- PPTP. Point-to-Point Tunneling Protocol is one of the oldest VPN protocols in existence. ...
- L2TP/IPSec. Layer 2 Tunnel Protocol is a replacement of the PPTP VPN protocol. ...
- OpenVPN. ...
- SSTP. ...
- IKEv2.
What are the 3 types of VPN?
The Three Main Types of VPNs VPNs can be divided into three main categories – remote access, intranet-based site-to-site, and extranet-based site-to-site. Individual users are most likely to encounter remote access VPNs, whereas big businesses often implement site-to-site VPNs for corporate purposes.
What are the different kinds of VPN?
The four main types of VPN are:Remote access VPNs.Personal VPN services.Mobile VPNs.Site-to-site VPNs.
Which VPN is best for remote access?
Best Remote Access VPNs for business.Perimeter 81 – Best all-round business VPN.GoodAccess – Security Strategy Options.ExpressVPN – Lightning Fast VPN.Windscribe – VPN with Enterprise-Friendly Features.VyprVPN – Secure VPN with Business Packages.NordVPN – Security-first VPN.More items...•
What are the two types of VPN access?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
How does remote access VPN Work?
The remote access VPN does this by creating a tunnel between an organization's network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
Which type of VPN is best?
The Best VPN Service for 2022NordVPN - Best VPN for Privacy.Surfshark - Best VPN for Security.Private Internet Access VPN - Best VPN for Windows.IPVanish - Best VPN for Android.Ivacy - Most Affordable.Atlas VPN - Best Data Breach Monitoring.ExpressVPN - Best Encryption.PureVPN - Best Server Base.More items...
What is the difference between site to site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
How do I remotely access a VPN computer?
Simply go to Start -> Accessories -> Remote Desktop Connection and enter the IP address of the other Windows computer. desktop software. From HOME Mac to OFFICE Windows: Connect with VPN, then use Remote Desktop Client. From HOME Windows to OFFICE Mac: Connect with VPN, then use VNC client.
Which VPN has the most servers?
Here's a quick rundown of the number of countries supported by three of the best subscription-based VPNs: ExpressVPN boasts over 3,000 servers across 94 countries. CyberGhost has 7,000+ servers, though in slightly fewer countries (91 in total). NordVPN offers over 5,400 servers, though spread across just 58 countries.
How many types of VPN protocols are there?
Here are five common VPN protocols and their primary benefits. PPTP. Point-to-Point Tunneling Protocol is one of the oldest VPN protocols in existence. ... L2TP/IPSec. Layer 2 Tunnel Protocol is a replacement of the PPTP VPN protocol. ... OpenVPN. ... SSTP. ... IKEv2.
What is L2TP IPSec VPN?
About L2TP over IPsec/IKEv1 VPN Layer 2 Tunneling Protocol (L2TP) is a VPN tunneling protocol that allows remote clients to use the public IP network to securely communicate with private corporate network servers. L2TP uses PPP over UDP (port 1701) to tunnel the data. L2TP protocol is based on the client/server model.
Can I use NordVPN for remote desktop?
Unfortunately, you will not be able to use a remote desktop with NordVPN. Remote desktop service requires specific open ports and port-forwarding. Currently, we do not allow port-forwarding due to security reasons.
Is VPN required for remote desktop?
The search for secure remote access doesn't have to stop with VPNs and RDP. Check the security of your remote connections with this remote access security checklist or seek out solutions designed to manage third-party access that act as superior alternatives to VPNs and RDP software.
Does ExpressVPN allow remote access?
To use VPN with a remote desktop, simply: Sign up for ExpressVPN and its blazing-fast and ultra-secure service. Connect to a server in a location that's closest to your remote desktop. Launch your remote desktop software and begin working!
What is a B2B VPN tunnel?
A cost-effective way to setup these connections is to create a business to business virtual private network also known as a B2B VPN. VPN is a technology that allows for two geographically separate networks to connect and share data across insecure networks like the Internet.
What are the different types of VPNs?
Virtual Private Network (VPN) services fall into four main types: personal VPNs, remote access VPNs, mobile VPNs, and site-to-site VPNs. In this guide, we explain how each of these VPN types work and when to use them.
How to use remote access VPN?
To use a remote access VPN on your device you typically need to install client software or configure your device’s operating system to connect to the VPN. There also needs to be a VPN server on the network end of the connection.
What is a VPN service?
A personal VPN service connects you to a VPN server, which then acts as a middleman between your device and the online services you want to access.
Why use mobile VPN?
Mobile VPNs tend to be used to ensure consistent availability for mobile workers, or for the convenience of having a VPN that tolerates connection changes. For example:
What is intranet VPN?
Intranet-Based VPN: When the networks being connected belong to a single company, the combined VPN is known as an intranet-based VPN. This enables a company to establish a single wide area network (WAN) that spans two or more of its offices. Users in the company can access resources from other sites as easily as if they were on their own site.
How many types of VPN are there?
The four types of VPN outlined here have different applications, making it easy to choose between them.
How many ways can a VPN be implemented?
There are three main ways a site-to-site VPN can be implemented:
What is VPN in the internet?
Virtual Private Network (VPN) is basically of 2 types: Remote Access VPN permits a user to connect to a private network and access all its services and resources remotely. The connection between the user and the private network occurs through the Internet and the connection is secure and private.
What is site to site VPN?
A Site-to-Site VPN is also called as Router-to-Router VPN and is commonly used in the large companies. Companies or organizations, with branch offices in different locations, use Site-to-site VPN to connect the network of one office location to the network at another office location.
What is intranet VPN?
Intranet based VPN: When several offices of the same company are connected using Site-to-Site VPN type, it is called as Intranet based V PN. Extranet based VPN: When companies use Site-to-site VPN type to connect to the office of another company, it is called as Extranet based VPN. Basically, Site-to-site VPN create a imaginary bridge between ...
How does a VPN work?
Basically, Site-to-site VPN create a imaginary bridge between the networks at geographically distant offices and connect them through the Internet and sustain a secure and private communication between the networks. In Site-to-site VPN one router acts as a VPN Client and another router as a VPN Server as it is based on Router-to-Router ...
What is VPN for employees?
An employee of a company, while he/she is out of station, uses a VPN to connect to his/her company’s private network and remotely access files and resources on the private network. Private users or home users of VPN, primarily use VPN services to bypass regional restrictions on the Internet and access blocked websites.
What is IP security?
Internet Protocol Security (IPSec):#N#Internet Protocol Security, known as IPSec, is used to secure Internet communication across an IP network. IPSec secures Internet Protocol communication by verifying the session and encrypts each data packet during the connection.#N#IPSec runs in 2 modes:#N#(i) Transport mode#N#(ii) Tunneling mode#N#The work of transport mode is to encrypt the message in the data packet and the tunneling mode encrypts the whole data packet. IPSec can also be used with other security protocols to improve the security system. 1 (i) Transport mode 2 (ii) Tunneling mode
What is VPN technology?
VPN technology is the technology used to create secure and private communication channels between the user's device and the destination by utilizing various VPN protocols.
What is a trusted VPN?
Trusted VPNs move traffic over a set of paths with specified properties. The paths are usually controlled by one ISP or a group of trusted ISPs. This allows users to handle their own routing and implement their own private IP addressing schemes. In addition, the users trust the ISPs not to change any of the VPN paths or insert their own traffic on the VPN.
Why is VPN important?
This is because a secure VPN encrypts all the traffic to such a level that if anyone replicates the traffic, they won't access or read its contents.
What layer of VPN is used in trusted VPN?
Technologies used in a trusted VPN can be separated into Layer 2 and Layer 3 VPNs.
Why use multiple EVPNs?
Multiple EVPNs can be deployed within a single service provider network to provide network connectivity to customers while maintaining the privacy of traffic shared within the network . In addition, EVPNs use the BGP control plane infrastructure to provide greater scale and the ability to separate devices from each other.
Can a VPN provider modify a path?
Only the trusted VPN provider can create or modify a path in the VPN.
Is software VPN better than hardware VPN?
Software VPNs are cheaper, easier to set up, and have better scalability compared to hardware VPNs. They don't require an expert to set up, and the network administrator can easily add more instances. All a user needs to do is install the VPN client application if it's not already installed on their device.
What is remote access VPN?
What is a remote access VPN? Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What are the advantages of remote access VPN?
Another advantage of remote access VPNs is that they provide companies with an affordable way to secure data sent by offsite employees. The initial investment needed to set up a remote access VPN is minimal and they can easily be scaled as a company grows and this is especially true if a VPN service provider is used.
Why is VPN important for business?
The most important benefit though is data security. When an offsite employee sends data through a VPN, it is encrypted, so even if a hacker is able to intercept that data, they won’t be able to use it. This is particularly important if an employee accesses their companies’ network using public Wi-Fi while traveling because traffic sent over these networks is usually not encrypted.
What is a network access server?
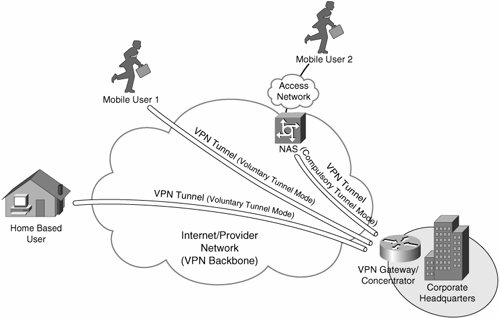
A network access server could be a dedicated server or it might be a software application running on a shared server. Users connect to the NAS over the internet in order to use a remote access VPN. In order to sign in to the VPN, the NAS requires that users provide valid credentials. To authenticate these credentials, the NAS uses either its own authentication process or a separate authentication server running on the network.
Why do businesses use VPNs?
Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What is site to site VPN?
A site-to-site VPN uses a secure gateway to connect a network at one location to one or more networks at another location. This type of VPN doesn’t require each device at the end location to have a VPN client installed because the gateway handles the traffic.
Is it good to work remotely?
The ability to work remotely is one of the perks that many businesses offer employees to help sweeten the deal. The recent coronavirus outbreak has only exacerbated that, leading many more organizations to allow their employees to work remotely. While this is good news for employees, it could end up causing a great deal of disruption to organizations that aren’t prepared and one way to do so is to look into remote access VPN solutions.
What is remote access VPN?
Remote access VPN. 1. In site to site VPN, IPsec security method is used to create an encrypted tunnel from one customer network to remote site of the customer. In remote access VPN, Individual users are connected to the private network. 2.
What is site to site VPN?
Site-to-Site VPN is also known as Router-to-Router VPN. In site to site VPN, IPsec security method is used to create an encrypted tunnel from one customer network to remote site of the customer. Multiple users are not allowed in Site-to-Site VPN.