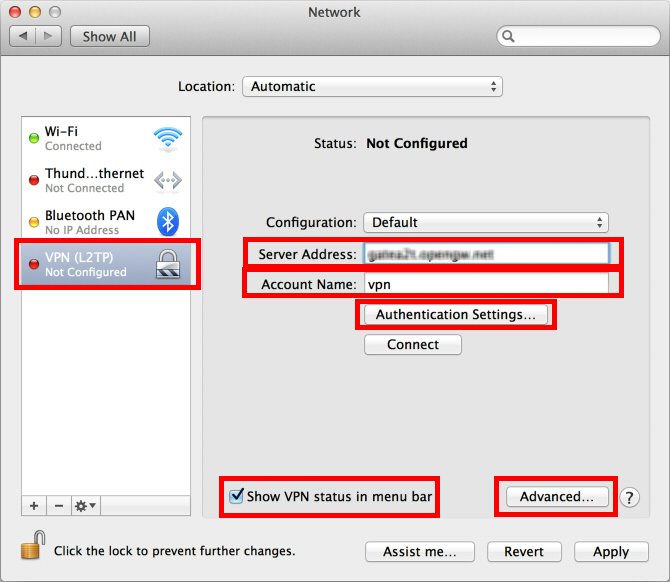
When the VPN server
Virtual private network
A virtual private network extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running on a computing device, e.g. …
Full Answer
How do I authenticate a remote access VPN connection?
You can use certificates installed on the client device to authenticate remote access VPN connections. When using client certificates, you can still configure a secondary identity source, fallback source, and authorization and accounting servers. These are AAA options; for details, see Configure AAA for a Connection Profile .
Can the Cisco rescue VPN client be used with CAG or rescue?
The CISCO RESCUE VPN Client is only for use on VA Government Furnished Equipment (GFE) and is installed on all GFE laptops. Users would still need to request remote access and have their remote access accounts enabled for use with either CAG or RESCUE.
Can I create a custom certificate template for a VPN certificate?
You're welcome. That process is actually for the certificate used by the remote access (RA) SSL VPN. If you're using Microsoft's standard Windows Certificate Authority there's no need to create a custom template - the "Web Server" one works fine. 07-22-2020 05:55 AM
What are the certificate requirements for a VPN client?
In addition, the certificate must include the Server Authentication EKU (1.3.6.1.5.5.7.3.1and the IP security IKE intermediate EKU (1.3.6.1.5.5.8.2.2). Client certificate requirements vary depending on the type of VPN tunnel and authentication method being used.
Does VPN need certificate?
Certificates can be used for authenticating VPN gateways and the Stonesoft VPN Client. In site-to-site VPNs, you can use both pre-shared keys and certificates as the authentication method. In mobile VPNs, certificates are always needed when the Stonesoft VPN Client is involved.
Is VPN considered remote access?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
How does remote access work with VPN?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I get a VPN certificate?
Navigate to Microsoft Windows Certificate Enrollment page: http:///CertSrv.When prompted for authentication, enter username and password of a Domain User.Click Request a certificate.Click advanced certificate request.Select Administrator or User under Certificate Template.More items...
What is the difference between site to site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
Which VPN is best for remote access?
Best Remote Access VPNs for business.Perimeter 81 – Best all-round business VPN.GoodAccess – Security Strategy Options.ExpressVPN – Lightning Fast VPN.Windscribe – VPN with Enterprise-Friendly Features.VyprVPN – Secure VPN with Business Packages.NordVPN – Security-first VPN.More items...•
What do you need for remote access?
Remote computer access requires a reliable internet connection. You'll need to activate or install software on the device you want to access, as well as on the device — or devices — you want to use to get that access.
What are the disadvantages of using a VPN?
The 10 biggest VPN disadvantages are:A VPN won't give you complete anonymity: Read more.Your privacy isn't always guaranteed: Read more.Using a VPN is illegal in some countries: Read more.A safe, top-quality VPN will cost you money: Read more.VPNs almost always slow your connection speed: Read more.More items...•
Is VPN safer than Remote Desktop?
Security. Although both VPN and RDP are encrypted through internet connection, a VPN connection is less accessible to threats than a remote desktop connection. For this reason, VPN is often considered more secure than RDP.
How do I check if my VPN certificate is valid?
StepsSelect Configuration, then browse to SD-WAN.Browse to Other Elements > Certificates > VPN Certificate Authorities.See the Expiration Date column for information about the CA's expiration date.More items...•
What is OpenVPN certificate?
OpenVPN supports bidirectional authentication based on certificates, meaning that the client must authenticate the server certificate, and the server must authenticate the client certificate before mutual trust is established.
Where are OpenVPN certificates?
After generating certificates and keys on the Command Window, you can find the certificates and keys in the %ProgramFiles%\OpenVPN\easy-rsa (e.g. D:\OpenVPN\easy-rsa). Diffie Hellman parameters. Note: If the KEY_SIZE in the vars.
How do I setup a VPN remote access?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
What is a remote internet connection?
Remote computer access is the ability to access another computer or network that isn't in your physical presence. Remote computer access allows an employee to access a computer desktop and its files from a remote location. This helps enable an employee who is working from home, for instance, to work effectively.
Which is better RDP or VPN?
Security. Although both VPN and RDP are encrypted through internet connection, a VPN connection is less accessible to threats than a remote desktop connection. For this reason, VPN is often considered more secure than RDP.
What are the disadvantages of using a VPN?
The 10 biggest VPN disadvantages are:A VPN won't give you complete anonymity: Read more.Your privacy isn't always guaranteed: Read more.Using a VPN is illegal in some countries: Read more.A safe, top-quality VPN will cost you money: Read more.VPNs almost always slow your connection speed: Read more.More items...•
How to install Remote Access Role in VPN?
On the VPN server, in Server Manager, select Manage and select Add Roles and Features. The Add Roles and Features Wizard opens. On the Before you begin page, select Next.
How many Ethernet adapters are needed for VPN?
Install two Ethernet network adapters in the physical server. If you are installing the VPN server on a VM, you must create two External virtual switches, one for each physical network adapter; and then create two virtual network adapters for the VM, with each network adapter connected to one virtual switch.
How to select a server from the server pool?
On the Select destination server page, select the Select a server from the server pool option. Under Server Pool, select the local computer and select Next. On the Select server roles page, in Roles, select Remote Access, then Next. On the Select features page, select Next. On the Remote Access page, select Next.
How to start remote access?
Select Start service to start Remote Access. In the Remote Access MMC, right-click the VPN server, then select Properties. In Properties, select the Security tab and do: a. Select Authentication provider and select RADIUS Authentication.
Can you assign a VPN to a pool?
Additionally, configure the server to assign addresses to VPN clients from a static address pool. You can feasibly assign addresses from either a pool or a DHCP server; however, using a DHCP server adds complexity to the design and delivers minimal benefits.
Is RRAS a router or a server?
RRAS is designed to perform well as both a router and a remote access server because it supports a wide array of features. For the purposes of this deployment, you require only a small subset of these features: support for IKEv2 VPN connections and LAN routing.
Where to install a server?
Install the server on your perimeter network between your edge and internal firewalls, with one network adapter connected to the External Perimeter Network, and one network adapter connected to the Internal Perimeter Network.
What is Cisco Secure Endpoint?
Cisco Secure Endpoint New packages fit for every organization Every Cisco Secure Endpoint (formerly AMP for Endpoints) package comes with Cisco SecureX built-in. It’s our cloud-native platform that integrates all your security solutions into one view wit... view more
How to browse to FQDN?
browse to the FQDN via https (or enter the device FQDN directly in AnyConnect VPN tile user interface)
Can a user access the Windows certicate store?
I am reasonably sure that a user cannot access the Windows computer/machine certicate store, unless the user is an administrator. A computer certificate would normally be used for the AnyConnect Management tunnel, which would be initiated automatically by the computer (when a user is not logged in).
Can I use a certificate on a VPN?
Yes, you are right. This process worked great for user certificate authentication. I enabled both AAA and certificate authentication on the FTD and was able to connect to the VPN after downloading a user certificate from my lab MS CA server.
What is VPN type?
VPN Type: SSTP (Secure Socket Tunneling Protocol) Click on Save. 37. Select VPN connection and click on Connect. 38. Specify a username and password to connect the VPN server. Click OK to connect. 39. Verify the VPN connection is successfully connected with the VPN server using SSTP protocol.
How to install Remote Access Server?
The first step is the installation of the Remote Access Server role. Open Server Manager Console and start role and feature installation wizard. Select the Remote Access Server role. 2. On select role services, select DirectAccess and VPN (RAS) role service. Click Next and finish the installation. 3.
How to configure SSTP VPN?
To configure SSTP VPN, we need to set up specific settings in the VPN server’s properties section. 21. Right-click on the server name and click on Properties. 22. Click on the Security tab. Under SSL Certificate Binding, select the self-signed certificate that you just created earlier. 23.
How long is an IIS self signed certificate valid?
8. You now have an IIS Self Signed Certificate listed under Server Certificates. Double-click on Certificate. The validity of the Self Signed Certificate is one year.
How to request remote access VA?
You may request remote access by visiting the Remote Access Self Service Portal ( only available while on VA's internal network).
How to disable automatic server selection in VPN?
In the VPN tab of the setting screen, uncheck Enable automatic server selection. Close the settings.
What is Azure Virtual Desktop?
Azure Virtual Desktop (AVD) is designed for users with a Windows 10 (either VA-furnished or privately-owned) or personal Windows 11 computer. This is a good option for users who need access to a standardized VA desktop (PIV or eToken required).
How to enable TLS 1.1?
To enable TLS within Internet Explorer: Select ‘Tools’, then ‘Internet Options’, then the ‘Advanced’ tab. Enable the checkbox for ‘Use TL S 1.1’ (found towards the end of the list).
Is VA responsible for non-VA websites?
This page includes links to other websites outside our control and jurisdiction. VA is not responsible for the privacy practices or the content of non-VA Web sites. We encourage you to review the privacy policy or terms and conditions of those sites to fully understand what information is collected and how it is used.
Where does remote access VPN problem originate?
Remote access VPN connection issues can originate in the client or in the Firepower Threat Defense device configuration. The following topics cover the main troubleshooting problems you might encounter.
How to use a VPN on a computer?
Step 1. Using a web browser, open https://ravpn-address , where ravpn-address is the IP address or hostname of the outside interface on which you are allowing VPN connections. You identify this interface when you configure the remote access VPN. The system prompts the user to log in. Step 2.
How to see what session a VPN is on?
Use the show vpn-sessiondb anyconnect command to view detailed information about current AnyConnect VPN sessions.
How to complete a VPN connection?
To complete a VPN connection, your users must install the AnyConnect client software. You can use your existing software distribution methods to install the software directly. Or, you can have users install the AnyConnect client directly from the Firepower Threat Defense device.
Why create a VPN profile?
You can create a remote access VPN connection profile to allow your users to connect to your inside networks when they are on external networks, such as their home network . Create separate profiles to accommodate different authentication methods.
What is the primary authentication source for Duo?
You can configure the Duo RADIUS server as the primary authentication source. This approach uses the Duo RADIUS Authentication Proxy.
What is Cisco ISE?
Cisco ISE has a client posture agent that assesses an endpoint's compliance for criteria such as processes, files, registry entries, antivirus protection, antispyware protection, and firewall software installed on the host. Administrators can then restrict network access until the endpoint is in compliance or can elevate local user privileges so they can establish remediation practices. ISE Posture performs a client-side evaluation. The client receives the posture requirement policy from ISE, performs the posture data collection, compares the results against the policy, and sends the assessment results back to ISE.
What is the best practice for always on VPN?
Using certificate authentication for the user tunnel is the recommended best practice for Always On VPN deployments. A client certificate must be installed in the Current User/Personal store to support PEAP authentication with smart card or certificate authentication. The certificate must include the Client Authentication EKU (1.3.6.1.5.5.7.3.2).
What is IKEv2 VPN?
Internet Key Exchange version 2 (IKEv2) is one of the VPN protocols supported for Windows 10 Always On VPN deployments. When the VPN server is Windows Server 2016 with the Routing and Remote Access Service (RRAS) role configured, a computer certificate must first be installed on the server to support IKEv2. There are some unique requirements for this certificate, specifically regarding the subject name and Enhanced Key Usage (EKU) configuration. In addition, some deployment scenarios may require a certificate to be provisioned to the client to support IKEv2 VPN connections.
Where is IKEv2 certificate installed?
It must be installed in the Local Computer/Personal certificate store on the VPN server.
