
The rule is actually quite simple: encryption prevents access to the encrypted data unless you have the key. Let’s say you have an encrypted file on your hard disk.
Full Answer
How to protect your network from remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly. Adopting two-factor authentication for remote access through VPN further boosts your network security.
Should I encrypt my solid-state drive?
Some solid-state drives advertise support for “hardware encryption.” If you’re using such a drive in your system and enable BitLocker, Windows will trust your drive to do the job and not perform its usual encryption techniques. After all, if the drive can do the work in hardware, that should be faster.
How does IPsec protect data transmission?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
How to increase security of remote remote access?
Security is further boosted by the enforcement of antivirus and firewall policies. A company should go for IPSec VPN remote access if it has a strong networking department with the ability to configure each employee’s hardware device individually (installing client software, enforcing security policies etc.).
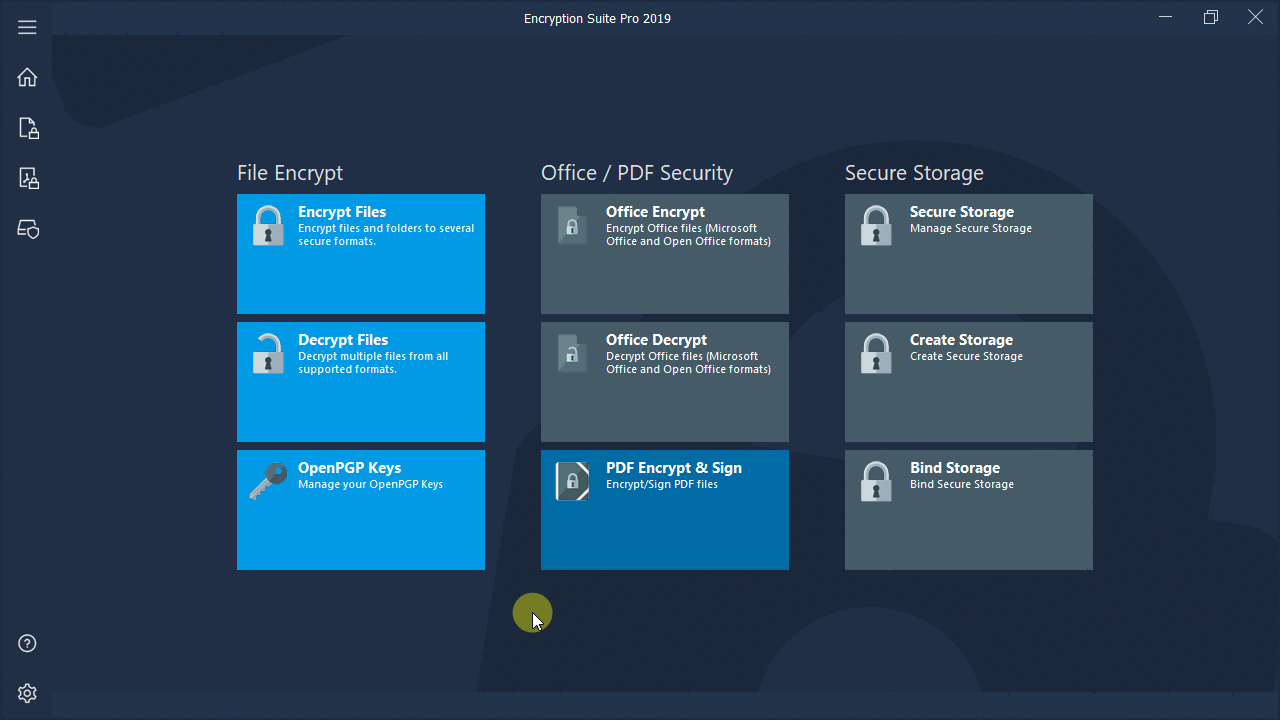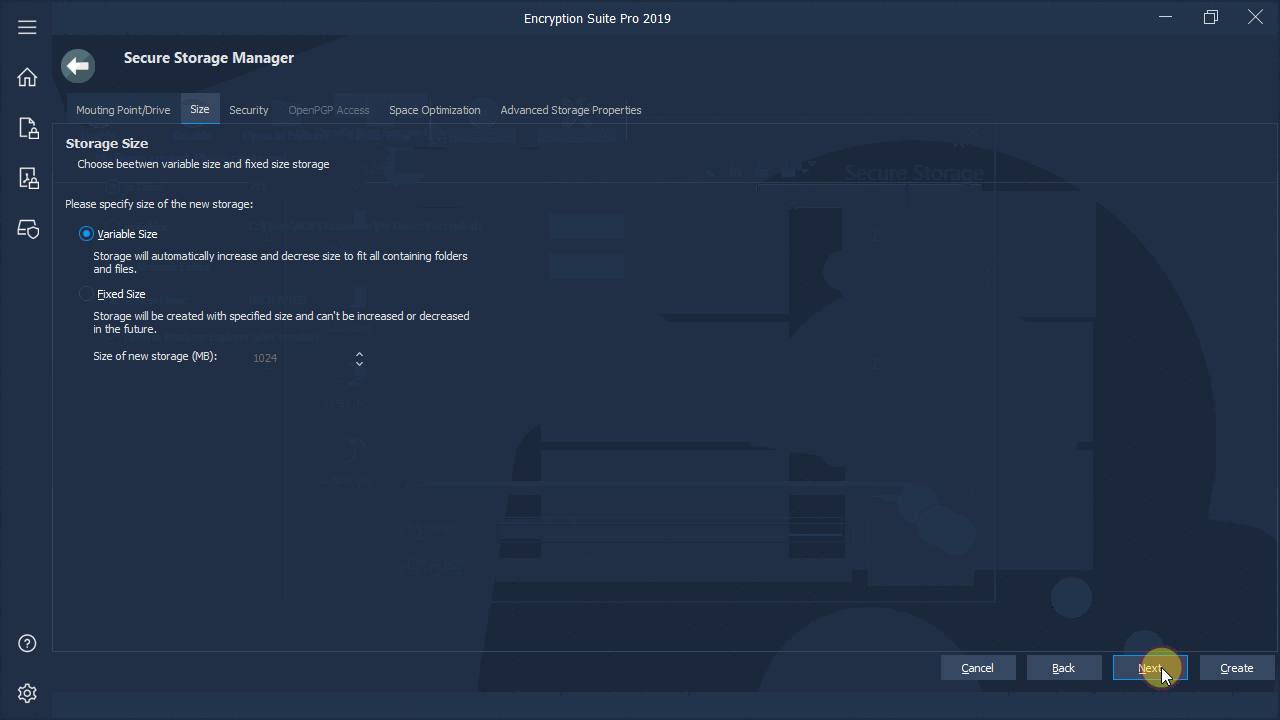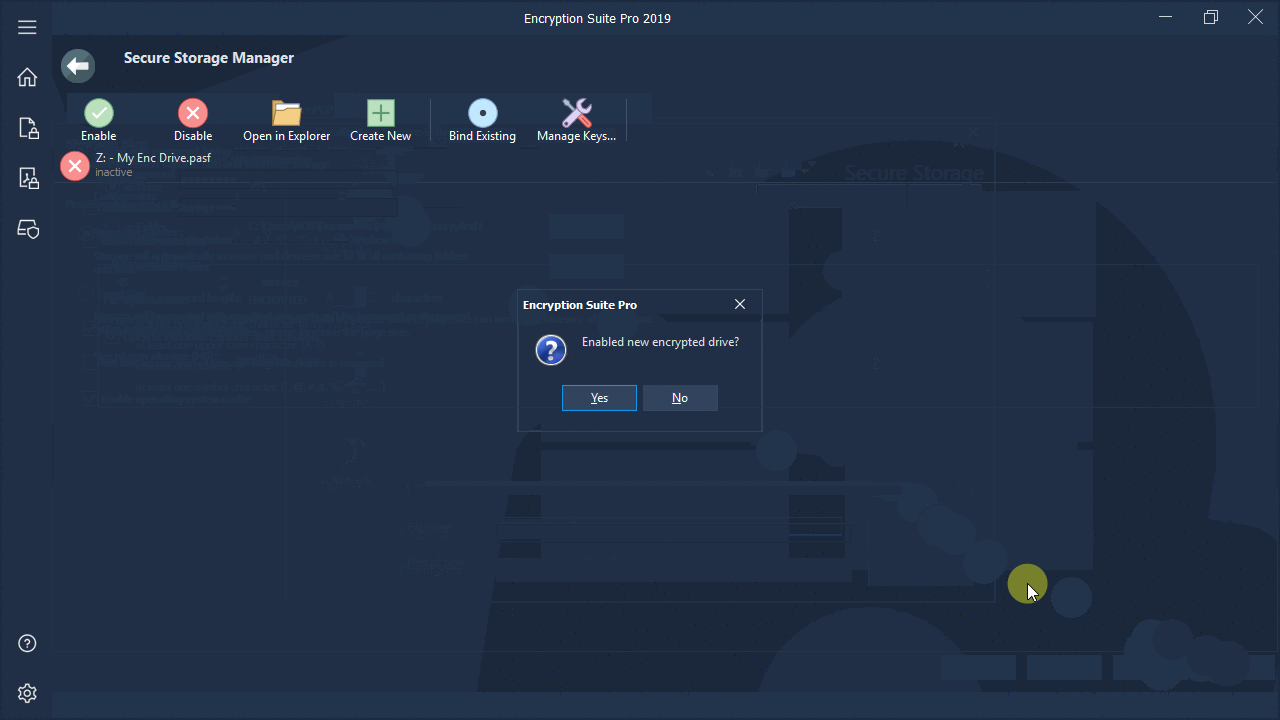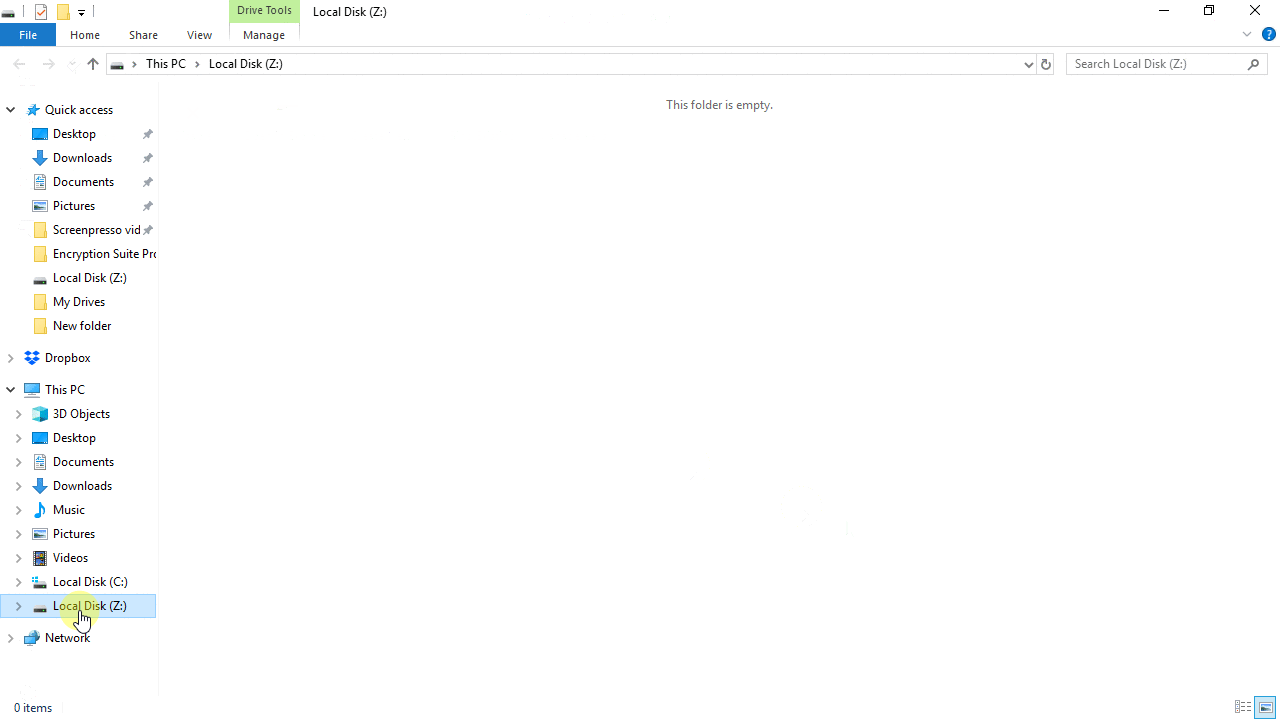
What does disk encryption protect against?
Full Disk Encryption (FDE) or whole disk encryption protects the entire volume and all files on the drive against unauthorized access. In contrast to FDE, File-Level Encryption (FLE) is an encryption method, which takes place on the file system level, enabling the encryption of data in individual files and directories.
Can encrypted hard drives be hacked?
Encrypted data can be hacked or decrypted with enough time and computing resources, revealing the original content. Hackers prefer to steal encryption keys or intercept data before encryption or after decryption. The most common way to hack encrypted data is to add an encryption layer using an attacker's key.
Why is drive encryption important?
SECURING DATA FROM HACKERS Volume level disk encryption helps protect you and your customers from data theft or accidental loss, by rendering data stored on hard drives unreadable when an unauthorized user tries to gain access. Hard disk encryption software makes it very for data to be accessed or stolen by hackers.
What encrypts data for remote transmission?
You can use a Communication Support Module (CSM) to encrypt data transmissions, including distributed queries, over the network, or Secure Sockets Layer (SSL) communications to encrypt data in end-to-end, secure TCP/IP and DRDA connections between two points over a network.
Should you encrypt your hard drive?
Keeping things secure Encrypting your hard drive is a great way to protect your personal data from prying eyes. Of course, if you're not careful, it might also protect your data from you. Unlike with an unencrypted computer, if you lose your password there is not an easy way to retrieve your data.
Can police break BitLocker?
Can government agencies break disk encryption? Without a warrant or probable cause, no. With a warrant, if your question is: "Can the encryption implemented by e.g., TrueCrypt be broken?" then the answer is that the TrueCrypt is believed to be secure.
What are the disadvantages of encrypting a whole drive to protect data?
DisadvantagesNot Protect Data in Transit. Yet, full disk encryption still has its own drawbacks. ... Slow down Computer. Moreover, in case of full disk encryption, the entire drive is encrypted. ... Complicate Data Recovery.
What is the reason for encrypting hard drives on laptop computers?
Full disk encryption protects the entire hard drive while your system is off. You cannot start Windows at all without first entering the correct password in a pre-boot authentication screen. Also, if someone removes the hard drive, they cannot read it from another system, because all the data remains encrypted.
How do I encrypt my external hard drive?
Most modern operating systems such as Windows, macOS, and Linux have built-in tools for encrypting your external hard drives or USB peripherals. For instance, you can use BitLocker for Windows, FileVault for Mac, and LUKS (Linux Unified Key Setup-on-disk-format) for Linux to encrypt your USB drives.
How can you protect data from transmission?
Let's look at some of the best methods to secure the transmission of confidential or sensitive data.Email Encryption. ... Website Encryption. ... File Transfer Protocol (FTP) and Secure File Transfer Protocol (SFTP) ... Secure HyperText Transfer Protocol. ... Off the Record Messaging. ... Cloud Services. ... Peer to Peer (P2P) Communication.More items...•
What type of encryption does VPN use?
public-key encryptionVPNs use public-key encryption to protect the transfer of AES keys. The server uses the public key of the VPN client to encrypt the key and then sends it to the client. The client program on your computer than decrypts that message using its own private key.
How strong is VPN encryption?
It's the same encryption standard adopted by the U.S. government and trusted by security experts worldwide to protect classified information. 256-bit keys means 2^256 or 1.1 x 10^77 possible combinations.
Can encryption be broken?
The simple answer is yes, encrypted data can be hacked.
Can encrypted data be decrypted?
Encrypted data can only be read or processed after it has been decrypted, using a decryption key or password. Only the sender and the recipient of the data should have access to the decryption key.
Can End to end encryption be decrypted?
End-to-end encryption (E2EE) is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system or device to another. In E2EE, the data is encrypted on the sender's system or device, and only the intended recipient can decrypt it.
How secure is encryption?
Encryption only protects whatever is encrypted, such as your internet connection, email or files, but it does nothing to protect you from other online threats. For example, you could use a VPN to encrypt your internet connection, but your online accounts could still get hacked.
What is the first thing that’s required to ensure smooth remote access via a VPN?
The first thing that’s required to ensure smooth remote access via a VPN is to plan out a comprehensive network security policy.
What is the line of defense for remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly.
Why is IPSEC used?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
What are the implications of IPSec connections for corporations?
What are the implications of IPSec connections for corporations, considering the very nature of this connection? Well, your employee will only be able to access the network from a single, authorized device. Security is further boosted by the enforcement of antivirus and firewall policies.
What is IPSEC encryption?
IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect data flows between hosts and security gateways.
Why use two factor authentication for VPN?
Adopting two-factor authentication for remote access through VPN further boosts your network security. Now let’s take a look at why you should choose a particular VPN type as a secure connection methodology instead of the alternatives.
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
Why is it important to enforce access based on user identity?
Recommendation: It’s critical that companies enforce access based on user identity, allowing specific groups access to only what they need to get their jobs done, and expanding access from there on an as-needed basis.
What should security teams do if on-premises network and email security mechanisms are no longer available?
Recommendation: If some on-premises network and email security mechanisms are no longer available, security teams should double down on educating users to identify phishing attempts and to choose strong, unique passwords, encouraging the use of a password manager. They should also implement client certificates and multi-factor authentication in order to prevent attackers from gaining access through unsecured devices.
What is XDR in security?
Recommendation: Rather than invest in point solutions, consider security platforms that maximize integration between systems, limiting the amount of switching between tools and providing visibility into all data – including remote user activity. Extended detection and response (XDR) not only protects endpoints, but also applies analytics across all your data to find threats like unusual access or lateral movement, and simplifies investigations by stitching together data and identifying the root cause.
Do passwords need to be stored in browsers?
This habit will cost you, if you become victim of such attacks. An alternative is to use password manager (though they are also not immune to attacks), which is advisable, but if you absolutely don’t want to get out of your old habit , a master password gives one more layer of protection.
Can you run TeamViewer on RDP?
Many popular remote apps, including TeamViewer, have an option to run the app instead of installing. So if you want to remote control for just one time it’s wise to just run the app. If you are not using any app and instead using RDP, then remember to disable RDP access after you are done.
Why is encryption important?
That’s the whole point of encryption—to stop a thief who stole your laptop or someone from gaining access to your desktop PC from viewing your files without your permission.
What is Bitlocker encryption?
BitLocker, the encryption technology built into Windows, has taken some hits lately. A recent exploit demonstrated removing a computer’s TPM chip to extract its encryption keys, and many hard drives are breaking BitLocker. Here’s a guide to avoiding BitLocker’s pitfalls.
How can an attacker exploit a PC?
How an Attacker Can Exploit This: If an attacker has your PC, they can wake it and sign in. On Windows 10, they may have to enter a numeric PIN. With physical access to your PC, an attacker may also be able to use direct memory access (DMA) to grab the contents of your system’s RAM and get the BitLocker key.
Where is Bitlocker stored?
BitLocker stores your encryption key in your computer’s Trusted Platform Module (TPM,) which is a special piece of hardware that’s supposed to be tamper-resistant. Unfortunately, an attacker could use a $27 FPGA board and some open-source code to extract it from the TPM.
Does Crucial MX300 have Bitlocker?
There’s just one problem: Researchers have discovered that many SSDs don’t implement this properly. For example, the Crucial MX300 protects your encryption key with an empty password by default. Windows may say BitLocker is enabled, but it may not actually be doing much in the background. That’s scary: BitLocker shouldn’t be silently trusting SSDs ...
Does Bitlocker work on Windows 10?
Standard BitLocker Isn’t Available on Windows Home. While nearly all modern consumer operating systems ship with encryption by default, Windows 10 still doesn’t provide encryption on all PCs. Macs, Chromebooks, iPads, iPhones, and even Linux distributions offer encryption to all their users.
Can an attacker use an encryption key?
How an Attacker Can Exploit This: This is better than no encryption. However, this means that Microsoft could be forced to disclose your encryption key to the government with a warrant. Or, even worse, an attacker could theoretically abuse a Microsoft account’s recovery process to gain access to your account and access your encryption key. If the attacker had physical access to your PC or its hard drive, they could then use that recovery key to decrypt your files—without needing your password.
How to protect a domain controller?
When possible, domain controllers should be configured with Trusted Platform Module (T PM) chips and all volumes in the domain controller servers should be protected via BitLocker Drive Encryption. BitLocker generally adds performance overhead in single-digit percentages, but protects the directory against compromise even if disks are removed from the server. BitLocker can also help protect systems against attacks such as rootkits because the modification of boot files will cause the server to boot into recovery mode so that the original binaries can be loaded. If a domain controller is configured to use software RAID, serial-attached SCSI, SAN/NAS storage, or dynamic volumes, BitLocker cannot be implemented, so locally attached storage (with or without hardware RAID) should be used in domain controllers whenever possible.
What configurations can be used to prevent domain controllers from accessing the Internet?
You can use a combination of AppLocker configuration, "black hole" proxy configuration, and WFAS configuration to prevent domain controllers from accessing the Internet and to prevent the use of web browsers on domain controllers.
Why keep domain controllers current?
By keeping your domain controllers current and eliminating legacy domain controllers, you can often take advantage of new functionality and security that may not be available in domains or forests with domain controllers running legacy operating system. Note.
Why is a domain controller compromised?
Because domain controllers can read from and write to anything in the AD DS database, compromise of a domain controller means that your Active Directory forest can never be considered trustworthy again unless you are able to recover using a known good backup and to close the gaps that allowed the compromise in the process .
Why is it important to compromise a domain controller?
Compromising a domain controller can provide the most expedient path to wide scale propagation of access, or the most direct path to destruction of member servers, workstations, and Active Directory. Because of this, domain controllers should be secured separately and more stringently than the general Windows infrastructure.
What is the security configuration wizard?
As described earlier, you should use the Security Configuration Wizard to capture configuration settings for the Windows Firewall with Advanced Security on domain controllers. You should review the output of Security Configuration Wizard to ensure that the firewall configuration settings meet your organization's requirements, and then use GPOs to enforce configuration settings.
Can a domain controller be stored in a locked room?
If a domain controller cannot be stored in a locked room in branch locations , you should consider deploying RODCs in those locations.
