What is DSS mobile app?
DSS Mobile 2 is mobile surveillance software designed for security field. It has user-friendly UI and offers fluent video playing experience, supports multi-point touch and gesture recognition,enables real-time preview, playback,PTZ control and E-map management of IPCameras, IP Speed dome cameras,DVR and NVR.
How do I control access on my Iphone?
Follow these steps:Go to Settings and tap Screen Time.Tap Content & Privacy Restrictions and enter your Screen Time passcode.Tap Content Restrictions, then tap Web Content.Choose Unrestricted Access, Limit Adult Websites, or Allowed Websites Only.
How do I set up vivotek iViewer?
To establish a connection with VIVOTEK's embedded Linux-based NVR, you need to enable the connection on a web console via Network > Service. Select the "Allow CMS and iViewer connection" checkbox, and enter the same password as that you use for login to an NVR console.
How can I monitor my childs iPhone text messages?
Monitor text messages through iCloud If you use iOS 12 or a more recent version, you can use Apple's cloud message sync feature. By enabling iCloud syncing, you can access all data from your child's device. Make sure to enable message synching so you can read messages from your child's phone.
How can I get text messages without unlocking my iPhone?
Respond to text messages without unlocking your phone You can respond to texts directly from your lock screen by pulling down on the notification drawer and swiping over to the left on the text notification. You'll see a "Reply" option, and tapping it will let you type a response without having to unlock your iPhone.
How do I stop my iPhone from sharing data?
In your privacy settings you can go to Analytics and Improvements and toggle off data sharing here.
What's the best parental control app for iPhone?
The best parental control apps for iOS are Qustodio, Net Nanny and Mobicip. All offer the same sorts of features for a similar cost. Other parental control apps like Bark and Canopy are good too, but the available features are a little less extensive.
Can you lock settings on iPhone?
From the Home screen, launch Settings and then tap "General" and "Restrictions." Tap the "Enable Restrictions" button and create a four-digit passcode that will need to be entered before restricted settings can be modified.
Where is the Control Center on iPhone?
To open Control Center, swipe down from the top-right corner of your screen. To close Control Center, swipe up from the bottom of the screen or tap the screen.
Description
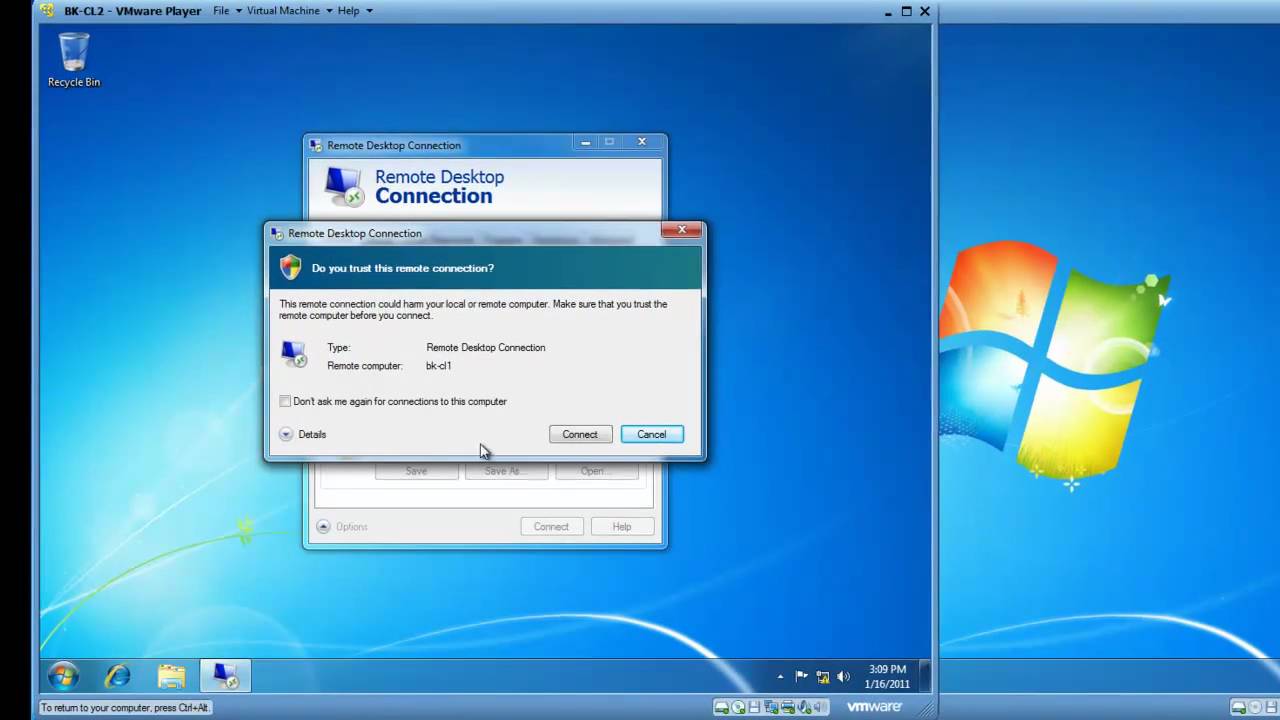
These instructions will show you how to setup your DSS Express server and network so you can remotely access the DSS Express server from the DSS Client or from the DSS Mobile App.
Forward Ports in Router or Modem
Please note the screenshots in this guide may not match identically to the modem/router being used with the DSS, but will be helpful as a reference in configuring the correct Port Forwarding rules.
Install personal firewall software on portable computing devices that access the CDE remotely
PCI DSS requirement 1.4 requires you to install personal firewall software or equivalent functionality on any portable computing device that connects to the Internet outside the network, such as laptop computers used by employees and is also used to access the CDE. Firewall or equivalent configurations should include the following requirements:
Monitor third-party remote accesses
PCI DSS requirement 8.1.5 requires you to manage identities used by third parties to access, support, or maintain system components via remote access as follows:
Use multi-factor authentication (MFA) controls
PCI DSS requirement 8.3.2 requires you to use multi-factor authentication for all remote network access from outside the organization’s network, including user, administrator, and third-party access for support or maintenance.
Use unique credentials for each customer, valid only for service providers
According to PCI DSS requirement 8.5.1, service providers with remote access to customer facilities for activities such as supporting POS systems or servers must use unique authentication information for each customer.
Establish usage policies for critical technologies, including remote access
Under PCI DSS requirement 12.3, you must develop usage policies for critical technologies and define the correct use of these technologies, including:
Automatically terminate remote access sessions after a specified time
PCI DSS requirement 12.3.8 requires automatic disconnection of sessions for remote access technologies after a specified period of inactivity.
Use remote accesses for third parties only when necessary
PCI DSS requirement 12.3.9 requires vendors and partners to enable remote access technologies only when needed by vendors and partners and be disabled immediately after use.