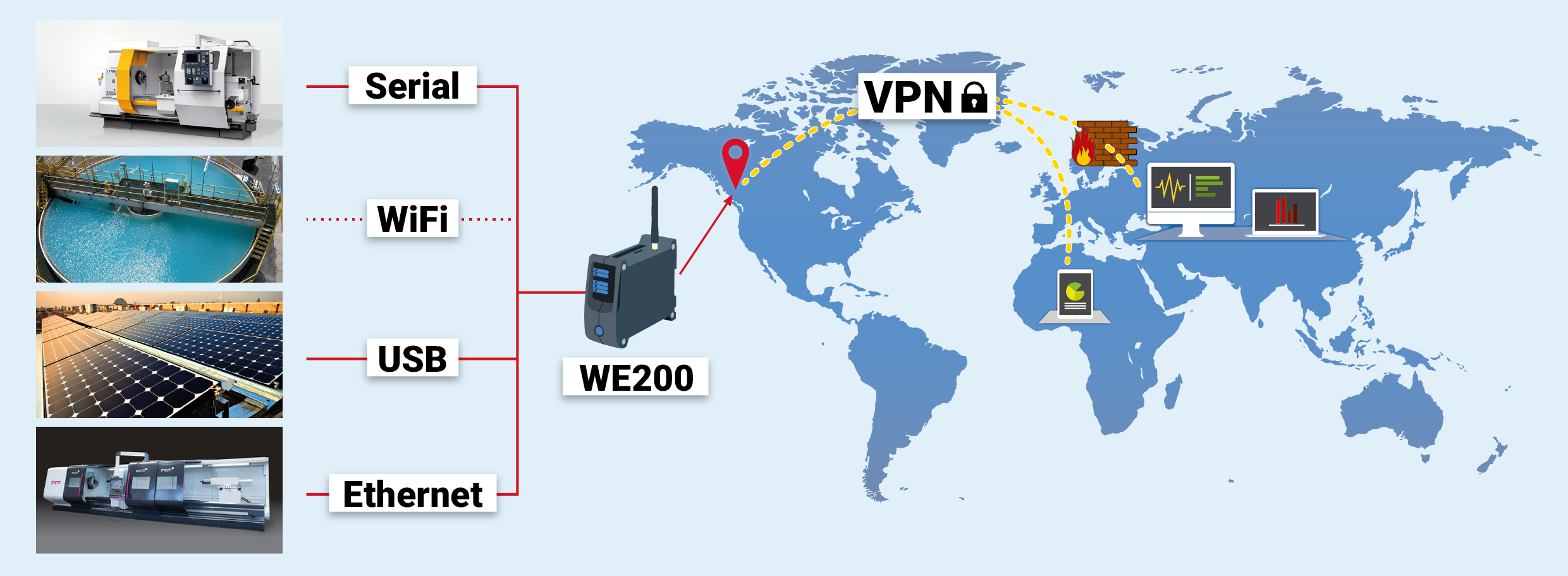
Does the R81 support IPsec VPN and mobile access?
These features are supported when connected to an R81 gateway that has IPsec VPN or Mobile Access enabled. See the R81 Mobile Access Administration Guide or the R81 Remote Access VPN Administration Guide for details.
What versions of Windows does the R81 remote access support?
See the R81 Mobile Access Administration Guide or the R81 Remote Access VPN Administration Guide for details. In this table, Windows 7 support is true for Ultimate, Professional, and Enterprise editions. Windows 8 support is true for Pro and Enterprise editions. All the marked consoles and clients support Windows 32-bit and 64-bit.
Can I have different versions of the VPN client on Security Gateway?
You can have packages for different versions of the VPN client for Windows and Mac OS X on your Security Gateway at the same time. For example, you can have E80.60 for Mac and E80.62 for Windows at the same time. To set up a gateway to automatically install client upgrades:
What is the fastest VPN for Linux?
ExpressVPN is a consistently fast VPN for Linux. It must be used with a command line client, but it offers great set up guides on its site, or opt for the browser extension instead.
How do I install Checkpoint VPN client in Linux?
Downloading the Shell ScriptsLogin.Click on “Settings” button.Click on “Download Installation for Linux” for both SSL Network Extender and Check Point Mobile Access Portal Agent.
What is Checkpoint VPN client?
Provide users with secure, seamless remote access to corporate networks and resources when traveling or working remotely. Privacy and integrity of sensitive information is ensured through multi-factor authentication, endpoint system compliance scanning and encryption of all transmitted data.
How do I connect to Checkpoint VPN?
Configuration - Check Point security gatewayOpen SmartConsole > Security Policies > Access Tools > VPN Communities.Click Star Community. ... Enter an Object Name for the VPN Community.In the Center Gateways area, click the plus sign to add a Check Point Security Gateway object for the center of the community.More items...•
How does Checkpoint VPN Work?
The Check Point VPN solution uses these secure VPN protocols to manage encryption keys, and send encrypted packets. IKE (Internet Key Exchange) is a standard key management protocol that is used to create the VPN tunnels.
What is remote VPN?
A remote access Virtual Private Network (VPN) allows users working remotely to access and use applications and data residing in the corporate data center,headquarter offices, and cloud locations, often encrypting all user traffic.
Who makes Checkpoint VPN?
Check Point Software Technologies Ltd. (www.checkpoint.com) is a leading provider of cyber security solutions to governments and corporate enterprises globally. Its solutions protect customers from 5th generation cyber-attacks with an industry leading catch rate of malware, ransomware and other types of attacks.
What type of VPN is Check Point?
The Check Point secured VPN implementation is based on IPSec (IP Security). IPSec is a commonly used set of protocols that was developed to support the secure exchange of packets at the IP layer between gateways that are connected over a public network (such as the Internet), and to create VPNs.
How do I configure site to site VPN in Check Point?
Getting Started with Site-to-Site VPNCreate the Security Gateway. Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. ... Create the Trusted Communication (SIC. ... Enable the IPsec VPN Software Blade. ... Click OK.
What is Check Point Endpoint Connect?
Endpoint Connect is Check Point's new lightweight remote access client. Providing seamless, secure (IPSec) VPN connectivity to corporate resources, the client works transparently with VPN-1 and Connectra gateways.
What are the 3 types of VPN?
The Three Main Types of VPNs VPNs can be divided into three main categories – remote access, intranet-based site-to-site, and extranet-based site-to-site. Individual users are most likely to encounter remote access VPNs, whereas big businesses often implement site-to-site VPNs for corporate purposes.
What are 2 types of VPN?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
What is the difference between site-to-site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
What is Check Point Endpoint Security?
Check Point Endpoint Security™ is the first single agent for total endpoint security that combines the highest-rated firewall, network access control (NAC), program control, antivirus, anti-spyware, data security, and remote access.
What is endpoint security used for?
Endpoint security is the process of protecting devices like desktops, laptops, mobile phones, and tablets from malicious threats and cyberattacks. Endpoint security software enables businesses to protect devices that employees use for work purposes either on a network or in the cloud from cyber threats.
What is Checkpoint Endpoint Connect?
Endpoint Connect is Check Point's new lightweight remote access client. Providing seamless, secure (IPSec) VPN connectivity to corporate resources, the client works transparently with VPN-1 and Connectra gateways.
How do I download Checkpoint VPN?
Installation InstructionsStep 1: Download Checkpoint VPN E84.30. Download and save the VPN client installation file from this link. ... Step 2: Remove currently installed version. To uninstall the currently installed version of Check Point VPN Client: ... Step 3: Install new version.
Remote Access VPN Products
Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser.
What is Remote Access VPN?
Remote Access VPN ensures that the connections between corporate networks and remote and mobile devices are secure and can be accessed virtually anywhere users are located. A secure remote access solution promotes collaboration by connecting global virtual teams at headquarters, branch offices, remote locations, or mobile users on the go.
Technical Resources
The place to discuss all of Check Point’s Remote Access VPN solutions, including Mobile Access Software Blade, Endpoint Remote Access VPN, SNX, Capsule Connect, and more!
Our Customers Love Us
Versatile Security Protection –Like A Swiss Army Knife For Security Checkpoint Next Generation Firewall proves to be a great solution for our small business infrastructure. R80 Security Management has allowed our company to easily (and significantly) improve our protections over time. read more >
Quantum is powered by ThreatCloud
ThreatCloud, the brain behind all of Check Point’s products, combines the latest AI technologies with big data threat intelligence to prevent the most advanced attacks, while reducing false positives.
Which VPN protocol is best for NSA?
You might be wondering which protocol to go with if you're relatively new to VPNs. However, we'd always recommend sticking with OpenVPN. OpenVPN may not be the most efficient VPN protocol, mind you, but it is the only protocol known to be secure against the NSA when strong privacy settings are used (most notably perfect forward secrecy).
Why should I use a VPN for Linux?
Using a VPN, then, would be the next logical step for Linux users in securing watertight online privacy.
How much does Mullvad VPN cost?
It has a VPN GUI for Linux users with all the features you get on Windows and Mac, including VPN through Tor. Pricing. From $5.50 - $5.60.
Where to find OpenVPN files?
You can import OpenVPN files from any convenient location (such as your Downloads folder). Once imported, they can usually be found in the /etc/openvpn/ folder
Where are OpenVPN logs?
OpenVPN logs are typically found in the syslog at /var/log/syslog – though bear in mind that this can vary by distro. OpenVPN config files are usually found in /etc/openvpn/
How many devices can you use PIA on?
Plus, this service will be compatible with your other devices (iOS, Android, macOS, etc) and it allows you to use it on up to 10 devices at once – with just a single subscription.
Is AirVPN good for Linux?
AirVPN is great for Linux users thanks to its strong reputation for respecting user privacy and for implementing the technology needed to protect it. Unfortunately, this is something of a double-edged sword, as AirVPN’s techie focus can make it difficult for beginners.
Does XenApp support Identity Agent?
Note - Identity Agent for Terminal Servers is also supported on XenApp 6.
Does a gateway have multiple authentication options?
This version supports multiple login options per gateway with multi-factor authentication schemes, for users of different clients and the Mobile Access Portal. For example, configure an option to authenticate with Personal Certificate and Password, or Password and DynamicID for SMS or email.
How to disconnect a session in OpenVPN?
It is also possible to use the D-Bus path to the session as well: openvpn3 session-manage --session-path /net/openvpn/v3/sessions/..... --disconnect. This command above will disconnect a running session. Once this operation has completed, it will be removed from the openvpn3 sessions-list overview. Important: you will be able to start a new session with this or another OpenVPN profile only after you have disconnected from the current session using the command in this step
How to install OpenVPN 3 on Linux?
Finally, the OpenVPN 3 Linux client can be installed by running the following command: sudo yum install openvpn3-client
How to check OpenVPN Cloud?
Run the command: sudo openvpn3 configs-list. It will show information about your active configurations. Check the name assigned to your active config. In this case, this is OpenVPN Cloud
How to install yum-plugin-copr?
You need to install the yum copr module first by running the following command: sudo yum install yum-plugin-copr. Note: Fedora releases usually have the yum/dnf copr module preinstalled.
How to import a VPN configuration file?
In order to import a configuration file for re-use and start a VPN session, type the following command into the Terminal: openvpn3 config-import --config $ {MY_CONFIGURATION_FILE}. Note: using this approach, an imported configuration file can be used several times, and access to the configuration file itself is not needed to start VPN tunnels. By default, configuration profiles imported are only available to the user who imported the configuration file. But OpenVPN 3 Linux also provides an Access Control List feature via openvpn3 config-acl to grant access to specific or all users on the system. Important: this loads the configuration profile and stores it in memory-only. That means, if the system is rebooted, the configuration profile is not preserved. If the –persistent argument is added to the command line above, the configuration profile will be saved to disk in a directory only accessible by the OpenVPN user. Whenever the Configuration Manager is started, configuration files imported with –persistent will be automatically loaded as well.
What is OpenVPN 3 Linux?
The OpenVPN 3 Linux project is a new client built on top of the OpenVPN 3 Core Library , which is also used in the various OpenVPN Connect clients and OpenVPN for Android (need to be enabled via the settings page in the app).
How to list all available configuration profiles?
To list all available configuration profiles, run this command: openvpn3 configs-list. Important: a configuration file typically contains generic options to be able to connect to a specific server, regardless of the device itself. OpenVPN 3 Linux also supports setting more host-specific settings on a configuration profile as well. This is handled via the `openvpn3 config-manage` interface. Any settings here will also be preserved across boots if the configuration profile was imported with the --persistent argument.
Installation and Configuration
Before you install this release, make sure that you have supported gateways.
Automatic Upgrade from the Gateway
You can configure your Security Gateway to automatically upgrade Remote Access VPN clients the next time that they connect. When this occurs, the Security Gateway downloads the applicable package to the client. Endpoint users must have administrator permissions to install an upgrade.
Endpoint Security and VPN Config Tool
Hi, I am trying to create a custom MSI package for installing the Remote Access Client but has run into a problem.
Re: Endpoint Security and VPN Config Tool
Did you ever get an answer on this? I found where it read "certificate" in the trac.defaults file, but I have no idea what to change it to.
