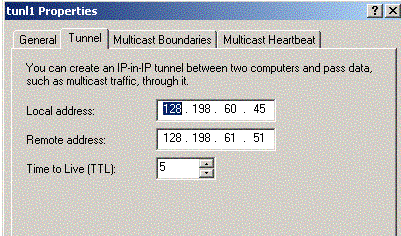
How do I Tunnel a database through SSH?
[remote host] the remote instance your tunnel will connect to the database through. This can be the database instance itself, or any instance within the database environment. The tunneling command opens an SSH session with the [remote host] specified. The tunnel will work as long as that SSH session is active.
How do I set up a remote access connection?
In order to establish a remote access connection via the GUI, as an Admin user, complete these steps: Navigate to Help and Support > Remote Access (for ESA, SMA), Support and Help > Remote Access (for WSA) Ensure that you check the Initiate connection via secure tunnel check box and specify the port number for connection
How do I Tunnel a database instance?
This can be the database instance itself, or any instance within the database environment. The tunneling command opens an SSH session with the [remote host] specified. The tunnel will work as long as that SSH session is active.
How to Access MySQL server remotely using SSH tunneling?
In this tutorial, we are going to use MySQL shell to access the remote MySQL server through SSH tunneling. Once the SSH session is connected, you can open your Windows command prompt and go to your MySQL shell directory and run the following command as if you are accessing from the same server.

What is FMC in Cisco?
Cisco Secure Firewall Management Center (formerly Firepower Management Center) Data Sheet - Cisco.
What is Cisco ASA WebVPN?
Previous page. WebVPN is an evolving method to establish remote-access VPN tunnels without having to install the Cisco VPN Client. A VPN user establishes the secure connection to the Cisco ASA by using a web browser such as Internet Explorer, Netscape, or FireFox.
How do I set up AnyConnect on ASA?
Configure AnyConnect ConnectionsConfigure the ASA to Web-Deploy the Client.Enable Permanent Client Installation.Configure DTLS.Prompt Remote Users.Enable AnyConnect Client Profile Downloads.Enable AnyConnect Client Deferred Upgrade.Enable DSCP Preservation.Enable Additional AnyConnect Client Features.More items...•
How can I check Cisco firepower VPN status?
The simplest place to check the status of your VPN is in FMC. Browse to System -> Health -> Events. Then click on VPN Status. The remaining verification takes place on the FTD CLI.
How do I access my Cisco ASA remotely?
There are eight basic steps in setting up remote access for users with the Cisco ASA.Configure an Identity Certificate.Upload the SSL VPN Client Image to the ASA.Enable AnyConnect VPN Access.Create a Group Policy.Configure Access List Bypass.Create a Connection Profile and Tunnel Group.Configure NAT Exemption.More items...•
Is Cisco AnyConnect SSL or IPsec?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN.
Is AnyConnect a VPN?
Cisco AnyConnect Client helps us to make secure , safe and reliable VPN connection to our organization's private network with multiple security services to safe and protect company's data. It gives freedom to employees to get connected from anywhere anytime, thus making life easier for remote workers.
What type of VPN is AnyConnect?
Cisco AnyConnect VPNs utilize TLS to authenticate and configure routing, then DTLS to efficiently encrypt and transport the tunneled VPN traffic, and can fall back to TLS-based transport where firewalls block UDP-based traffic.
How does AnyConnect VPN Work?
Remote and mobile users use the Cisco AnyConnect Secure VPN client to establish VPN sessions with the adaptive security appliance. The adaptive security appliance sends web traffic to the Web Security appliance along with information identifying the user by IP address and user name.
How do I check my FTD VPN tunnel?
In order to monitor the tunnel status, navigate to the CLI of the FTD or ASA. From the FTD CLI, verify phase-1 and phase-2 with the command show crypto ikev2 sa. This section provides information you can use in order to troubleshoot your configuration.
What is Cisco clientless SSL VPN?
Remote access VPNs include clientless SSL VPN using a web browser, SSL or Ipsec VPN using Cisco AnyConnect client, or Ipsec VPN remote access. A clientless SSL VPN is a browser-based VPN that allows a remote user to securely access the corporate resources.
What is SSL VPN Cisco?
“Cisco” is the brand name of the VPN appliance (hardware). The “SSL VPN” stands for Secure Sockets Layer Virtual Private Network. SSL VPN is a service that allows the user to connect securely to the internet via AnyConnect, Web Applications, Telnet/SSH server, Virtual Network Computing (VNC), and Terminal Servers.
How does SSL VPN Work?
An SSL tunnel VPN allows a web browser to securely access multiple network services that are not just web-based via a tunnel that is under SSL. These services could be proprietary networks or software built for corporate use only that cannot be accessed directly via the internet.
What is clientless SSL VPN?
Clientless SSL VPN creates a secure, remote-access VPN tunnel to an ASA using a web browser without requiring a software or hardware client. It provides secure and easy access to a broad range of web resources and both web-enabled and legacy applications from almost any device that can connect to the Internet via HTTP.
What is EA Play?
EA Play is the ultimate game destination for anyone who loves EA titles. Membership gives you more of your favorite Electronic Arts games – more rewards, more exclusive trials, and more discounts. Unlock exclusive rewards and member-only content. Play select new-release EA games for up to 10 hours.
How long can you play EA games?
Play select new-release EA games for up to 10 hours.
Does EA Play only apply to one platform?
The EA Play membership will only apply to a single platform. *Conditions, limitations and exclusions apply. See <a href="https://tos.ea.com/legalapp/eaplay/US/en/PC/">EA Play terms</a> for details.
Why does the remote access not work on the SMA?
Remote access may not enable on an SMA if the SMA is placed in the local network without direct access to the Internet. For this instance, remote access can be enabled on an ESA or WSA, and SSH access can be enabled on the SMA. This allows Cisco Support to first connect via remote access to the ESA/WSA, and then from the ESA/WSA to the SMA via SSH. This will require connectivity between the ESA/WSA and the SMA on port 22.
What to do if your IronPort is not able to connect to the remote?
If the appliance is not able to enabled remote access and connect to upgrades.ironport.com via one of the ports listed, you will need to run a packet capture directly from the appliance to review what is causing the outbound connection to fail.
What is remote access Cisco?
Remote access is a Secure Shell (SSH) connection that is enabled from a Cisco Content Security appliance to a secure host at Cisco. Only Cisco Customer Assistance can access the appliance once a remote session is enabled. Remote access allows Cisco Customer Support to analyze an appliance. Support accesses the appliance through an SSH tunnel that this procedure creates between the appliance and the upgrades.ironport.com server.
When a remote access connection initiates, the appliance opens a secure, random, high-source port via an?
When a remote access connection initiates, the appliance opens a secure, random, high-source port via an SSH connection on the appliance to the configured/selected port one of the following Cisco Content Security servers:
Does a Cisco firewall allow outbound connections?
It is important to note that a customer firewall may need to be configured to allow outbound connections to one of the above listed servers. If your firewall has SMTP protocol inspection enabled, the tunnel will not establish. Ports that Cisco will accept connections from the appliance for the remote access are:
What is tunneling command?
The tunneling command opens an SSH session with the [remote host] specified. The tunnel will work as long as that SSH session is active. If the session window is consuming valuable workspace we recommend minimizing it as running tunnels in the background can lead to multiple tunnels and port conflicts.
What is SSH tunnel?
An SSH tunnel links a port on your local machine to a port on a remote host. When these ports are linked, anything communicated to the local port is passed through SSH to the remote port; likewise, any communication to the remote port is passed back through SSH to the local port.
Why is my database not accessible from outside?
This is a good thing because a database cannot reliably maintain the security and patch levels like SSH can. However, it means that to access your database from an external database tool, such as pgAdmin, MySQL Workbench, or SQLyog, you need to create an SSH tunnel to your database host/instance.
Can you use SSH tunnels for offsite replication?
You can also use SSH tunnels to set up offsite replication.
What is SSH tunneling?
SSH tunneling is also known as SSH port forwarding, which means we can route our traffic through SSH secure connection. It allows us to use the established SSH connection to set up a new “secure” connection from your computer to the remote server. There are three types of SSH port forwarding.
How to add a database to PuTTY?
On the left side navigation tree in PuTTY, click on Connection > SSH > Tunnels. Enter the database server (MySQL, PostgreSQL, etc) port under the “Source port”. Then in the destination box type “127.0.0.1:3306” and finally click on Add.
Do you need to create a new session for tunneling?
In the future, you do not need to create a new session for tunneling, you can simply load the saved session. Now, we can click on the Load button and you will be asked for your SSH login credentials.
What is a tunnel group?
Group policy assigned by the Connection Profile (called tunnel-group in the CLI)—The Connection Profile has the preliminary settings for the connection, and includes a default group policy applied to the user before authentication.
What does ASA do during authentication?
During authentication, the ASA retrieves the value of physicalDeliveryOfficeName from the server, maps the value to the Cisco attribute Banner1, and displays the banner to the user.
How to enforce a banner on LDAP?
To enforce a simple banner for a user who is configured on an AD LDAP server use the Office field in the General tab to enter the banner text. This field uses the attribute named physicalDeliveryOfficeName. On the ASA, create an attribute map that maps physicalDeliveryOfficeName to the Cisco attribute Banner1.
Can you use anyconnect before logon?
Because multiple certificate authentication requires a machine certificate and a user certificate (or two user certificates), you cannot use AnyConnect start before logon (SBL) with this feature.
Is IPsec and L2TP supported simultaneously?
1 (1) IPsec and L2TP over IPsec are not supported simultaneously. Therefore, the values 4 and 8 are mutually exclusive.
Can you map LDAP to VSA?
This example displays a simple banner to the user, showing how you can map any standard LDAP attribute to a well-known Vendor-Specific Attribute (VSA), and you can map one or more LDAP attribute (s) to one or more Cisco LDAP attributes. It applies to any connection type, including the IPsec VPN client, AnyConnect SSL VPN client, or clientless SSL VPN.
What is remote access VPN?
What is a remote access VPN? Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What are the advantages of remote access VPN?
Another advantage of remote access VPNs is that they provide companies with an affordable way to secure data sent by offsite employees. The initial investment needed to set up a remote access VPN is minimal and they can easily be scaled as a company grows and this is especially true if a VPN service provider is used.
How does a NAS work?
Users connect to the NAS over the internet in order to use a remote access VPN. In order to sign in to the VPN, the NAS requires that users provide valid credentials. To authenticate these credentials, the NAS uses either its own authentication process or a separate authentication server running on the network .
What is a network access server?
A network access server could be a dedicated server or it might be a software application running on a shared server. Users connect to the NAS over the internet in order to use a remote access VPN. In order to sign in to the VPN, the NAS requires that users provide valid credentials. To authenticate these credentials, the NAS uses either its own authentication process or a separate authentication server running on the network.
Is it good to work remotely?
The ability to work remotely is one of the perks that many businesses offer employees to help sweeten the deal. The recent coronavirus outbreak has only exacerbated that, leading many more organizations to allow their employees to work remotely. While this is good news for employees, it could end up causing a great deal of disruption to organizations that aren’t prepared and one way to do so is to look into remote access VPN solutions.
Can VPNs be used remotely?
While VPNs have grown increasingly popular among users looking to protect their data and privacy online, using the right type of VPN can make all the difference when working remotely. In this article, we’ll be taking a closer look at remote access VPNs, who offers them ( like Perimeter 81, our top ranked business VPN) and the benefits they can bring to organizations looking to mobilize a remote workforce quickly.
What is a VPN tunnel?
The device tunnel is designed to allow the client device to establish an Always On VPN connection before the user logs on. This enables important scenarios such as logging on without cached credentials. This feature is crucial for organizations who expect users to log on to devices the first time remotely. The device tunnel can also be helpful for remote support, allowing administrators to manage remotely connected Always On VPN clients without having a user logged on. In addition, the device tunnel can alleviate some of the pain caused by administrators resetting remote worker’s passwords, or by users initiating a Self-Service Password Reset (SSPR).
When can a device tunnel be safely deployed?
The device tunnel can be safely deployed in conjunction with the user tunnel whenever its functionality is required.
What is a host route?
An alternative to using traffic filters to limit access over the device tunnel is using host routes. Host routes are configured with a /32 prefix size and define a route to a specific individual host. The following is an example of host route configuration in ProfileXML.
Does Windows Server RRAS perform certificate revocation?
However, Windows Server RRAS does not perform certificate revocation checking for Windows 10 Always On VPN device tunnel connections by default.
Can you add a host route to a domain controller?
In this scenario it is recommended to add host routes only for the domain controllers that belong to the Active Directory site where the VPN server resides.
Can MFA be used with VPN?
For the record, it is possible to integrate MFA with Always On VPN when using either MSCHAPv2 and in some cases PEAP, depending on your MFA provider.
Can I disable IKE mobility?
Yes, you can disable IKE mobility on the endpoint itself by looking at advanced security properties on the VPN connection itself. You can change the outage time or simply disable it completely.
How to see web portal virtual desktop?
To see the web portal virtual desktop settings, right-click the SSL VPN Virtual Desktop icon in the taskbar and select Virtual Desktop Option. When you have finished working with the virtual desktop, right-click the SSL VPN Virtual Desktop icon in the taskbar and select Exit. Select Yes to confirm.
Where is the Logout button on the web portal?
When you have finished using the web portal, select the Logout button in the top right corner of the portal window.
What is a web portal?
A web portal defines SSL VPN user access to network resources. The portal configuration determines what SSL VPN users see when they log in to the unit. Both the Fortinet administrator and the SSL VPN user have the ability to customize the web portal settings. Portal settings are configured in VPN > SSL-VPN Portals.
What is the Fortinet portal configuration?
The portal configuration determines what the user sees when they log in to the portal. Both the system administrator and the user have the ability to customize the SSL VPN portal.
How to use SSL VPN?
To use the SSL VPN virtual desktop, simply log in to an SSL VPN that requires the use of the virtual desktop. Wait for the virtual desktop to initialize and replace your desktop with the SSL VPN desktop, which has a Fortinet SSL VPN logo as wallpaper. Your web browser will open to the web portal page.
Why isn't the IP pool field used in VPN?
In this example, the IP Pools field on the VPN > SSL-VPN Settings page is not used because each web portal specifies its own tunnel IP address range.
How to send Ctrl Alt delete?
If you need to send Ctrl-Alt-Delete in your session, press F8, then select Send Ctrl-Alt-Delete from the pop-up menu.