What is the endpoint remote access VPN software blade?
The Endpoint Remote Access VPN Software Blade is integrated into the Software Blade Architecture. Endpoint Security Software Blades from Check Point bring unprecedented flexibility, control and efficiency to the management and deployment of endpoint security.
What is endpoint security client?
Complete Endpoint Security Client for any CPU (32bit or 64bit). This is a self-extracting executable EXE file with all components (Blades) to be used as Dynamic package with R80.50 and higher. Initial client is a very thin client without any blade used for software deployment purposes.
What is the build number of the endpoint security client?
Client Version Endpoint Security Client Build Number Remote Access VPN Stand-alone Client Bui ... E85.10 85.10.0572 98.61.3105 E85.00 85.00.0007 98.61.3000 E84.71 84.71.8708 98.61.2710 E84.70 84.70.8619 98.61.2705 59 more rows ...
What's new in endpoint client for Windows?
Endpoint Client now supports new Push Operations: creating and deleting a VPN site and registry key or value, collecting processes information from the client machine, and moving or deleting a file on the client machine. Endpoint Client now supports turning ON/OFF admin-enabled capabilities.
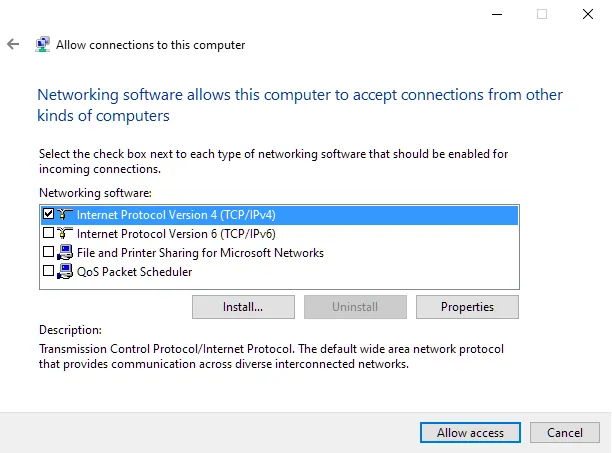
How do I install Checkpoint VPN?
Installation InstructionsStep 1: Download Checkpoint VPN E84.30. Download and save the VPN client installation file from this link. ... Step 2: Remove currently installed version. To uninstall the currently installed version of Check Point VPN Client: ... Step 3: Install new version.
How do I update my Checkpoint VPN?
Instructions for UserValidate if your Check Point VPN/EndPoint Client version is one of the following: ... If your client version is: Check Point Endpoint VPN E80. ... Reboot your machine.Click on EPPatcher_for_users.exe to install the patch. ... Within a few seconds you will get “Fix has been successfully deployed” pop-up.
What is Check Point Endpoint Security VPN?
Check Point endpoint security includes data security, network security, advanced threat prevention, forensics, endpoint detection and response (EDR), and remote access VPN solutions.
How do I install Checkpoint VPN client in Linux?
Downloading the Shell ScriptsLogin.Click on “Settings” button.Click on “Download Installation for Linux” for both SSL Network Extender and Check Point Mobile Access Portal Agent.
Is checkpoint a VPN?
The Check Point secured VPN implementation is based on IPSec (IP Security). IPSec is a commonly used set of protocols that was developed to support the secure exchange of packets at the IP layer between gateways that are connected over a public network (such as the Internet), and to create VPNs.
What is the difference between site-to-site VPN and remote access VPNs?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
How do I open Endpoint Security?
1. Right-click the Endpoint Security icon in your taskbar notification area and select Display Overview. The Endpoint Security Main Page opens.
What is a remote access VPN?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
Is Endpoint Security an antivirus?
Endpoint security is made up of antivirus, firewalls, intrusion detection, and anti-malware tools. This allows for the execution of more than just that of the antivirus, but data loss prevention, sandboxing, next-generation firewalls, and endpoint detection and response.
Is Cisco secure endpoint a VPN?
It not only provides VPN access through Secure Sockets Layer (SSL) and IPsec IKEv2 but also offers enhanced security through various built-in modules.
How does Checkpoint VPN Work?
The Check Point VPN solution uses these secure VPN protocols to manage encryption keys, and send encrypted packets. IKE (Internet Key Exchange) is a standard key management protocol that is used to create the VPN tunnels.
What is Checkpoint endpoint Connect?
Endpoint Connect is Check Point's new lightweight remote access client. Providing seamless, secure (IPSec) VPN connectivity to corporate resources, the client works transparently with VPN-1 and Connectra gateways.
How does Checkpoint VPN Work?
The Check Point VPN solution uses these secure VPN protocols to manage encryption keys, and send encrypted packets. IKE (Internet Key Exchange) is a standard key management protocol that is used to create the VPN tunnels.
What is Checkpoint Software used for?
(www.checkpoint.com) is a leading provider of cyber security solutions to governments and corporate enterprises globally. Its solutions protect customers from 5th generation cyber-attacks with an industry leading catch rate of malware, ransomware and other types of attacks.
What is Checkpoint endpoint Connect?
Endpoint Connect is Check Point's new lightweight remote access client. Providing seamless, secure (IPSec) VPN connectivity to corporate resources, the client works transparently with VPN-1 and Connectra gateways.
What is mobile checkpoint VPN?
Check Point Mobile VPN for Android devices is an L3 VPN client. It supplies secure connectivity and access to corporate resources using the L3 IPSec/SSL VPN Tunnel. The application is available in the Google Play Store: https://play.google.com/store/apps/details? id=com.checkpoint.VPN&hl=en.
Secure your remote workforce, fast
If you're looking to increase protection for your remote employees so they can work from any device, at any time, from any location, get started with the Cisco Secure Remote Worker solution.
Always-on protection for your business
Threats can occur through a variety of attack vectors. You need secure connectivity and always-on protection for your endpoints. Deploy Cisco endpoint security clients on Mac, PC, Linux, or mobile devices to give your employees protection on wired, wireless, or VPN.
Features and benefits
Empower employees to work from anywhere, on company laptops or personal mobile devices, at any time. Gain endpoint visibility across the extended enterprise. Protect employees on or off the network. Enforce posture for connected endpoints.
Services
Cisco Services help customers integrate a breadth of Cisco technology, migrate from other solutions, and optimize their existing security technologies.
Security that works for you
You don't have to be an expert in security to protect your business. A simple unified security platform can keep you humming along.
