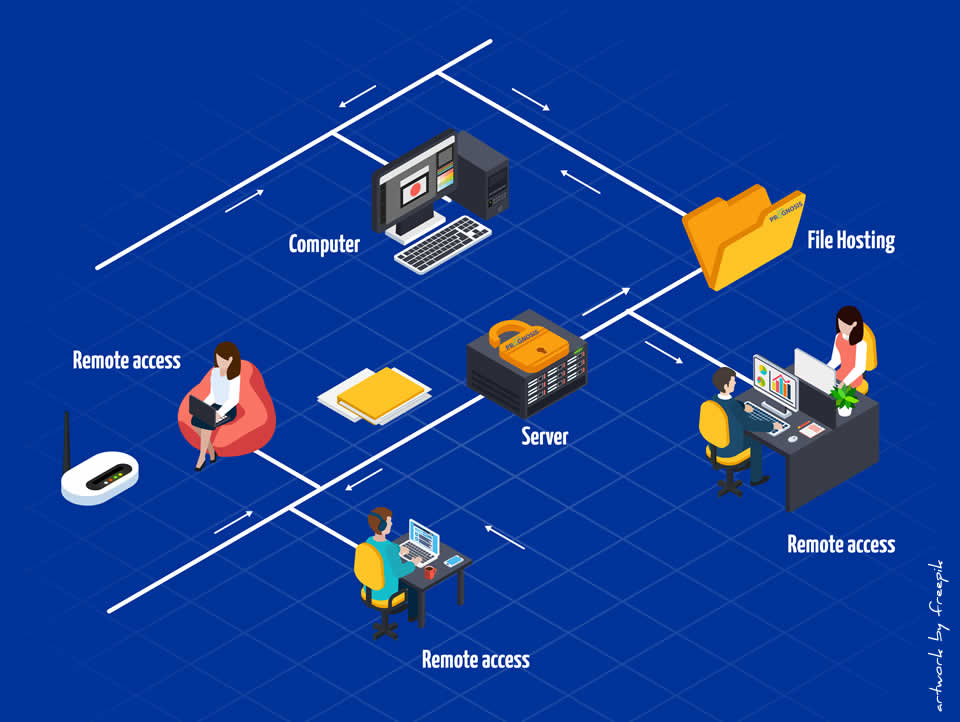
How to Keep Employees Safe with a Secure Remote Access Plan
- Issue Secure Equipment to Remote Employees. Small businesses and managers need to remember that their employees are not...
- Supply a VPN for Secure Remote Access. Organizations that utilize a Virtual Private Network (VPN) provide their remote...
- Empower Remote Employees through Education and Technology.
- Develop a Cybersecurity Policy For Remote Workers. ...
- Choose a Remote Access Software. ...
- Use Encryption. ...
- Implement a Password Management Software. ...
- Apply Two-factor Authentication. ...
- Employ the Principle of Least Privilege. ...
- Create Employee Cybersecurity Training.
What is securesecure remote access?
Secure remote access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization’s digital assets Skip to Main Content Global Search USAbout UsStore
How to protect your network from remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly. Adopting two-factor authentication for remote access through VPN further boosts your network security.
What is secure remote access (SRA)?
What is Secure Remote Access? - Definition | VMware Glossary Secure remote access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization’s digital assets Skip to Main Content Global Search
How to increase security of remote remote access?
Security is further boosted by the enforcement of antivirus and firewall policies. A company should go for IPSec VPN remote access if it has a strong networking department with the ability to configure each employee’s hardware device individually (installing client software, enforcing security policies etc.).

What is meant by secure remote access?
Secure Remote Access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization's digital assets and prevent the loss of sensitive data.
What can be used to support secure remote access?
The following technologies can contribute to secure remote access:VPNs;intrusion prevention systems and intrusion detection systems;Secure Access Service Edge (SASE) and software-defined perimeter;firewalls;cloud access security brokers;zero-trust network access;virtual desktop infrastructure; and.More items...•
Why is secure remote access important?
A secure remote access system protects your employees from web-based threats such as phishing attacks, ransomware and malware while they're logged in to your company's network. These cyber incidents can lead to unauthorized access and use of both the company's business data and the employee's personal data.
How do I keep my remote workers secure?
Here are a few security best practices your remote employees should follow.Run software updates regularly. ... Secure video meetings. ... Watch out for email phishing. ... Create strong passwords. ... Never leave your bag, briefcase or laptop unattended. ... Use caution with wireless networks. ... Keep your work separate.
What are potential risks associated with remote access?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
Which technology is used in remote access?
virtual private network (VPN) technologyRemote access software is usually accomplished using a virtual private network (VPN) technology. This type of method is more available compared to others since it is a more secure remote access software that connects the user and the enterprise's networks through an internet connection.
What are three examples of remote access locations?
What Is Remote Access?Queens College.Harvard University Extension School.
How many types of remote access are there?
Types of remote access: virtual private network. SaaS remote desktop tools. common remote service ports.
What is VPN for remote work?
Organizations that utilize a Virtual Private Network (VPN) provide their remote employees a very similar experience to working in brick and mortar locations. A VPN allows an end-user to establish a direct connection between their PC and the corporate network through a firewall. VPNs provide the much needed extra layer of security to ensure continued business productivity during and after this period of disruption. While remote desktop services and applications might suffice for a small office with only a few remote connections, a VPN will be needed to properly secure a business that requires multiple remote connections.
Is it safe to climb Mount Everest without crampons?
The prospect of trusting employees to ensure security protocols on personal devices is like climbing Mount Everest without crampons; the intentions are sound but you will inevitably fail due to lack of foresight and proper equipment. Being prepared with the right equipment for a steep ascent will ensure you are secure during your climb up the proverbial cybersecurity mountain.
How does secure remote access work?
Every remote worker needs a way to connect with remote desktop services and applications that won't slow down their workflows. At the same time, IT administrators must manage those connections to ensure they don't leave the network open to threats.
Why is secure remote access important to remote work security?
Secure remote access approaches are so vital because it’s now impossible to control security at the endpoint. Each user in a remote or hybrid workforce is connecting to the network from a different type of computer or smartphone, and they’re using a variety of internet connections to log in.
How to achieve maximum remote access security?
To achieve maximum remote access security, you should use and encourage your end users to employ a robust password manager. A password manager can help you keep track of your passwords, ensure they are strong, and enforce password updates when necessary.
Why is remote access important for MSPs?
By limiting access to only those who absolutely need it, MSPs can boost their overall security and help prevent loss of sensitive data.
What is risk prevention in cyber security?
Teaching risk prevention involves making every party aware of the reality of cyberthreats, the likelihood of them occurring, and how their actions can help prevent them.
What is remote desktop access?
Remote access is regularly used by managed services providers (MSPs) to assist customers experiencing IT issues without actually having to be present at a specific machine or device. However, it is important to remember that support via remote desktop access isn’t just about rectifying or troubleshooting issues—the experience needs to be quick ...
What is AES encryption?
To safeguard security, all connections and data transmissions should be fully encrypted. Advanced Encryption Standards (AES) 256 data encryption is preferable, and can help ensure that data is protected both in transit and at rest. 8. Implement idle sessions timeout control.
What is the first thing that’s required to ensure smooth remote access via a VPN?
The first thing that’s required to ensure smooth remote access via a VPN is to plan out a comprehensive network security policy.
What is the line of defense for remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly.
Why is IPSEC used?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
What are the implications of IPSec connections for corporations?
What are the implications of IPSec connections for corporations, considering the very nature of this connection? Well, your employee will only be able to access the network from a single, authorized device. Security is further boosted by the enforcement of antivirus and firewall policies.
What is IPSEC encryption?
IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect data flows between hosts and security gateways.
Why use two factor authentication for VPN?
Adopting two-factor authentication for remote access through VPN further boosts your network security. Now let’s take a look at why you should choose a particular VPN type as a secure connection methodology instead of the alternatives.
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
Why do organizations need remote access?
On a more granular level, organizations have several reasons for enabling remote access to their OT environments. Software Toolbox identified three such factors: 1 Empowering decision-makers with data access and visibility: Decision-makers need access to and visibility over data if they are to safeguard the organization’s interests. They need timely information to make the right decisions. 2 Centralizing access across geographically distributed systems: Many organizations that own or operate OT environments have assets that are scattered across different countries and continents. This makes it difficult for people like remote workers to monitor those devices all at once. Remote access solves this problem by enabling an authenticated user to access those systems from anywhere in the world. Alternatively, organizations can centralize these access sessions within a single operations center. 3 Streamlining work with third parties: Organizations that own or operate OT environments need to be able to work with their third-party vendors, contractors and suppliers. This can be difficult depending on the scope of the supply chain. As a result, organizations could use remote access to share key important data with third parties rather than grant them full access to their entire environments. 4 Facilitating the implementation of updates: Per Security Week, many industrial control systems come with a contract through which equipment manufacturers are responsible for providing remote maintenance. It’s therefore critical that organizations ensure there’s remote access available to these device manufacturers. Otherwise, they could risk those OT assets not receiving an important update or fix when it’s misbehaving, for example.
Why do decision makers need access to data?
Empowering decision-makers with data access and visibility: Decision-makers need access to and visibility over data if they are to safeguard the organization’s interests. They need timely information to make the right decisions.
Why do banks use OOBM?
A global bank uses OOBM solutions across thousands of ATMs to ensure uptime and security for this key part of its network infrastructure. Due to the large volume and remote locations of these sites and the critical nature of their function, the bank relies on OOBM to allow a centrally located IT team to manage, monitor and ultimately fix any problems that arise. This ensures maximum uptime, reduces the need for onsite ATM management and cuts engineering time.
Why use OOBM?
Uptime is critical for its data center operations worldwide, and with its senior staff often located offsite, it is important to ensure that they can remotely access and manage infrastructure at all times, in all situations. OOBM ensures secure remote control for maintenance and upkeep while maintaining a low resource overhead. It also gives its management and IT team peace of mind knowing they will have access in emergency situations.
