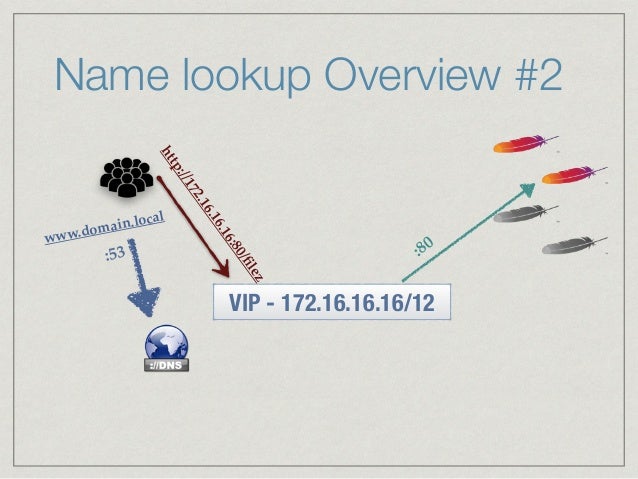
Enterprises of all sizes may use RDP to access servers, collaborate with other employees, and remotely access desktops to perform tasks similar to how they would with a physical office presence. The most common RDP use cases, include: Provide a bastion host with applications into an environment that mimics local resources.
Full Answer
Is unattended access the key to remote support success?
As many businesses around the world have recently transitioned to higher levels of remote working, the need for efficient remote support tools increased, and so has the need for scalability and fast, unattended support. During the coronavirus pandemic, unattended access played a key role in adhering to social distancing initiatives.
What are the use cases for a virtual desktop?
Relevant use cases. Most demand for enterprise virtual desktop solutions comes from: Security and regulation applications like financial services, healthcare, and government. Elastic workforce needs like remote work, mergers and acquisition, short-term employees, contractors, and partner access.
What is privileged remote access and how does it work?
Privileged Remote Access enables security professionals to control, monitor, and manage privileged access to critical systems. Privileged Remote Access eliminates the need for privileged users to remember or share credentials for the systems they need to access. Passwords can be stored in the on-appliance vault.
What are the benefits of a remote access management system?
Provide vendors and remote workers a secure method to access their workstations, internal and cloud infrastructure, and web/thick applications from wherever. Simplify the access process by providing one tool that facilitates all unattended access for remote systems and endpoints.

Is BeyondTrust remote support spying?
To start a session, BeyondTrust Remote Support retrieves a credential from the vault and automatically injects it into the session, without ever revealing it to end users. Every session is monitored (i.e. screen and audio recording, logging, etc.)
How do I secure remote access to enterprise network?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
What is BeyondTrust remote support?
BeyondTrust Remote Support Software enables support organizations to access and support nearly any remote computer or mobile device. Troubleshoot PCs and servers, provide remote assistance, train remote employees, or perform system maintenance . . . all with the highest levels of security.
What is remote access technologies?
Remote access technology refers to any IT toolset used to connect to, access, and control devices, resources, and data stored on a local network from a remote geographic location.
What is the main purpose of a RAS server?
A remote access server (RAS) is a type of server that provides a suite of services to remotely connected users over a network or the Internet. It operates as a remote gateway or central server that connects remote users with an organization's internal local area network (LAN).
Why RDP is not secure?
The problem is that the same password is often used for RDP remote logins as well. Companies do not typically manage these passwords to ensure their strength, and they often leave these remote connections open to brute force or credential stuffing attacks. Unrestricted port access.
What is BeyondTrust used for?
BeyondTrust is the worldwide leader in Privileged Access Management, offering the most seamless approach to preventing data breaches related to stolen credentials, misused privileges, and compromised remote access.
What is BeyondTrust session monitoring?
Session monitoring records the actions of a user while they access your password-protected managed systems. The actions are recorded in real time with the ability to bypass inactivity in the session. This allows you to view only the actions of the user.
What is privileged remote access?
Privileged remote access is about ensuring employees, third-party vendors, and other insiders don't have free access to systems while accessing the network remotely. You're able to define who has permissions, when they have it, and the appropriate level of access each role needs to complete their work.
What is remote access examples?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What is the greatest benefit of remote access to an organization?
Flexibility. By allowing your staff to perform tasks outside the office using remote access, you can facilitate more flexible work arrangements and help employees create a better work/life balance.
How can you ensure your network remains secure when you have clients with remote access?
Utilise VPNs Any remote connection between a computer and the corporate network should always be secured via a virtual private network (VPN) connection. The private network eliminates the need for a physical connection between integrated devices so that employees can remotely and securely access the office's servers.
What is a common way to help protect devices connected to the company network?
What is a common way to help protect devices connected to the company network? A. Only use laptops and other mobile devices with full-disk encryption. This is correct!
Which option creates a secure connection for remote workers?
The only way to secure your remote workforce is a secure VPN. Employees must connect from their laptops, desktops and mobile devices over a VPN connection. It's the secure, private method for virtually entering the corporate office, so to speak.
How do I control remote access?
Set up remote access to your computerOn your computer, open Chrome.In the address bar, enter remotedesktop.google.com/access .Under “Set up Remote Access,” click Download .Follow the onscreen directions to download and install Chrome Remote Desktop.
How is Remote Access Helpful?
The ability of help desk personnel to access a remote system means there is less need for a lay person to try to explain something he or she does not understand, such as an error message.
When is Remote Access Used?
Help desks often use remote access when they need to inspect the system configuration of a computer, try to duplicate an error message, install software onto a system without the need for the regular user to download the files, or when they have to make regular system updates to many computers at once.
Why do organizations need remote users?
Organizations need to provide remote users with more than just a secure connection back to the core network or datacenter resources they are used to be remotely connecting to. An increasing number of applications are also being hosted in the cloud, and rather than backhauling those applications through the core network, ...
What is a Fortigate VM?
FortiGate-VM next-generation firewalls (NGFWs) offer the flexibility to be deployed as NGFWs and/or VPN gateways in the cloud. They enable high-performance VPN connections across multiple on-premises and cloud environments, and protect data in motion: within clouds, across multiple clouds, and between clouds and on-premises data centers. Learn more.
What is unattended remote support?
Unattended remote support can be defined as instances when an IT technician remote controls an endpoint in the absence of any end user on the endpoint. Unattended access solutions are primarily used to perform routine maintenance, troubleshoot, and conduct health checks for devices, including laptops, desktops, servers, smartphones, IoT, operation technology (OT), and more.
What Features & Capabilities to Look for in Unattended Access Solutions?
Many organizations use several or more tools for remote support use cases. This usually happens for a couple main reasons:
Can remote support be deployed?
Unattended remote support can be deployed multiple ways. Once installed, the solution should allow the endpoint to be grouped, sorted, or organized based on the granular actions the support technician wants to occur and who can access these systems. The technician should be able to securely remote any endpoint or device remotely for which they have been granted access to at any time, from anywhere, with an internet connection.
Insider Threat Monitoring – Excessive Permissions
With users suddenly working from home, a lot of sensitive data is exposed through channels that it has not been before. Due to the sudden nature of the change, security teams have had a very limited time, if any, to evaluate and deploy strong security controls.
Insider Threat Monitoring – Data Exfiltration
With a newly remote work force and data being exposed through new channels, the risk of data compromise has increased significantly. This can lead to intentional or accidental compromise.
Insider Threat Monitoring – Credential Sharing
In a remote work environment, it is possible that certain users may not have the permissions they had before. In this scenario, users may resort to sharing credentials. This in turn may lead to security challenges related to unauthorized access, separation of duties (SoD) violations, and more.
Monitoring for Phishing and Fake Alert Email Campaigns
The current crisis has gotten people more curious than ever before. The bad guys are looking to cash in with fake email alerts and impersonation campaigns. We have been seeing organizations getting an average of 350 emails daily on this topic. While some emails are legitimate, others are not.
Monitoring for Suspicious Logins and Account Compromise
With a huge surge in remote logins, user accounts are more vulnerable to attacks than before. The bad guys are looking for any weakness in the authentication process that they can exploit. This includes weak passwords, weak multi-factor authentication, or weak detection of brute force attacks.
Security Monitoring of Cloud Applications
A large percentage of enterprises today utilize the cloud for both critical and non-critical applications. With a remote workforce it is important to monitor activities within the applications in order to detect any patterns of misuse or compromise.
Security Monitoring of VPN and Remote Authentication Devices
With a remote workforce, remote authentication and VPN devices can be a single point of failure and result in significant business disruption if unavailable.
What are the concerns of remote work?
With a remote work setup, one of the concerns for organisations that do not have the work from home culture , is the drop in the productivity. Organisations are looking for ways to monitor productivity based on login and activity patterns and SIEM can help support this to be able to detect the session time and duration and able to report on employees that do not meet a certain threshold
What is superman use case?
Land speed analysis (aka superman use cases) – user logging in from two distinct locations at the same time when it is humanly impossible for him/her to be physically present at these locations
What is rare login?
Rare logins – user logins from a rare location for his/her profile, but the location happens to be normal baseline location for a peer within the organisation
Can remote users have permissions?
In the remote work environment, it is very likely that certain users may not have the permissions they had before. In this scenario, users may resort to sharing credentials, which in turn may lead to security challenges with unauthorised access, SOD violations, etc.
Is remote work a cybersecurity challenge?
This is not a usual cybersecurity challenge that would come to mind, but we are not in usual times either. With the shift to remote work setup, organisations are struggling to track and report on usage of licenses for various technologies that enable the remote setup.
Can remote authentication fail?
With the remote work from home setup, the remote Authentication and VPN devices can be single point of failure and result in significant business disruption if unavailable.
What is privileged remote access?
Privileged Remote Access gives you the ability to centrally secure and manage access across all of your environments, even sensitive systems in the Cloud.
What is advanced web access?
Advanced Web Access can be configured to work across any solution that leverages a web interface for management including; Amazon Web Services, Google Cloud, VMware vSphere, Citrix XenServer, Microsoft Hyper-V, Microsoft Azure, IBM Softlayer, and Rackspace.
Bring Your Own Device (BYOD)
Bring your own device (BYOD) is the new paradigm shift that companies have started following recently. Although it seems beneficial for both the company and employees, protection of business data along with availability of applications on different devices is difficult.
Vendor Risk Reduction
Companies work with external entities on a day-to-day basis for various projects. These can be one time or even ongoing engagement and will require the company to share different resources and assets. Keeping a track of these while adhering company guidelines is a big challenge.
Unmanaged Devices
Unmanaged devices such as laptops, desktops or smart phones can be a real source of security breaches on any network. Especially regulated industries such as – BFSI, Telecom, BPO
Secure Remote Access and Support
To run business processes smoothly, providing access to corporate data and infrastructure to partners or vendors is essential. For example, providing remote access to your specific servers to your IT support partner. In these situations, providing restricted on-demand access with complete visibility is a must.
Remote access & control
Secure remote access and control is a fundamental requirement for managing embedded devices throughout their lifecycles. In most cases, devices are deployed across different networks and physical locations with varying access rights and security measures.
Remote operations
The global pandemic has accelerated the need to connect, control, and securely access machines without sending personnel. TeamViewer IoT allows operations teams to perform many asset-related activities remotely.
Secure attended access
To resolve problems with equipment they manufacture, in many cases OEMs must ask their customers to send malfunctioning units back. Or, worse yet, they may need to send a service technician to the site.
Device management
TeamViewer provides an easy-to-use console for administering and managing devices. With an inventory of all connected devices, you can provision, authenticate, configure, and maintain them in bulk or by device group.
Components Microsoft manages
Microsoft manages the following Azure Virtual Desktop services, as part of Azure:
Personal and pooled desktops
Personal desktop solutions, sometimes called persistent desktops, allow users to always connect to the same specific session host. Users can typically modify their desktop experience to meet personal preferences, and save files in the desktop environment. Personal desktop solutions:
Windows servicing
There are several options for updating Azure Virtual Desktop instances. Deploying an updated image every month guarantees compliance and state.
Azure limitations
The Azure Virtual Desktop service is scalable to more than 10,000 session hosts per workspace. You can address some Azure platform and Azure Virtual Desktop control plane limitations in the design phase to avoid changes in the scaling phase.
VM sizing
Virtual machine sizing guidelines lists the maximum suggested number of users per virtual central processing unit (vCPU) and minimum VM configurations for different workloads. This data helps estimate the VMs you need in your host pool.
Pricing
Architect your Azure Virtual Desktop solution to realize cost savings. Here are five different options to help manage costs for enterprises:

Insider Threat Monitoring – Excessive Permissions
Insider Threat Monitoring – Data Exfiltration
Insider Threat Monitoring – Credential Sharing
Monitoring For Phishing and Fake Alert Email Campaigns
Monitoring For Suspicious Logins and Account Compromise
Security Monitoring of Cloud Applications
Security Monitoring of Vpn and Remote Authentication Devices
- With a remote workforce, remote authentication and VPN devices can be a single point of failure and result in significant business disruption if unavailable. SIEM use cases should monitor for threats to remote authentication and VPN devices. Securonix monitors activities on VPN and remote authentication devices in order to detect any suspicious beh...
Security Monitoring For Host Compromise
License and Compliance Monitoring
Productivity Monitoring