
What is remote web access for Windows Server Essentials?
Remote Web Access helps you stay connected to your Windows Server Essentials network when you are away.
What is remote web access and how does it work?
Remote Web Access is a feature of Windows Servers Essentials that enables you to access file/folders and computers on your network via a web browser from anywhere with Internet connectivity. Remote Web Access helps you stay connected to your Windows Server Essentials network when you are away.
How do I access resources on my server using remote web access?
When you log on to Remote Web Access from a local or remote computer, you can access resources on your server running Windows Server Essentials and computers on your network. Open a Web browser, type https://<YourServerName>/remote in the address bar, and then press Enter. Make sure that you include the s in https.
Which topics can help me access my server resources remotely?
The following topics can help you access your server resources remotely: For information about configuring Anywhere Access on your server, see Manage Anywhere Access. Remote Web Access helps you stay connected to your Windows Server Essentials network when you are away. For more information, see the topic Use Remote Web Access.
 - Remote Control Access.png)
What is required for remote access?
Remote computer access requires a reliable internet connection. You'll need to activate or install software on the device you want to access, as well as on the device — or devices — you want to use to get that access.
What is remote access function?
The most common function of remote access is to enable employees who are traveling or telecommuting to connect to the company network and access resources such as internal applications, intranet, mail services, and file sharing. In the past, remote access was a service that companies provided through dial-up modems.
What are the three main types of remote connections?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
What are the different types of remote access methods?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What is remote access examples?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
How do companies do remote access?
You have two main options here – a VPN or the cloud. VPN – Virtual Private Network – You can restrict access so that employees must exclusively connect through a VPN, providing a direct, encrypted connection between their remote device and the main office server.
Which protocol is essential for internet remote login?
Remote Desktop Protocol (RDP)The Remote Desktop Protocol (RDP) is a protocol, or technical standard, for using a desktop computer remotely. Remote desktop software can use several different protocols, including RDP, Independent Computing Architecture (ICA), and virtual network computing (VNC), but RDP is the most commonly used protocol.
What is remote access and its advantages?
Remote access technology gives users the ability to access a computer, device or network from a remote location. Remote access is now commonly used for corporate networks that give their employees the ability to remote access a computer and perform their tasks even without being physically present in the office.
What is the greatest benefit of remote access to an organization?
Flexibility. By allowing your staff to perform tasks outside the office using remote access, you can facilitate more flexible work arrangements and help employees create a better work/life balance.
What types of connections are there?
There are two possible types of connections: point-to-point and multipoint. A point-to-point connection provides a dedicated link between two devices.
What are the types of connections in network?
Generally there are two types of network connections: Peer-to-Peer and Network Shared environment.
What are the 4 types of networks?
A computer network is mainly of four types:LAN(Local Area Network)PAN(Personal Area Network)MAN(Metropolitan Area Network)WAN(Wide Area Network)
What are the different types of connections in data communication?
There are two possible types of connections:Point-to-Point Connection.Multipoint Connection.
Use Remote Web Access in Windows Server Essentials
Remote Web Access helps you stay connected to your Windows Server Essentials network when you are away. For more information, see the topic Use Rem...
Use VPN to Connect to Windows Server Essentials
If you have a client computer that is set up with network accounts that can be used to connect to a hosted server running Windows Server Essentials...
Use The My Server App to Connect to Windows Server Essentials
The My Server app lets you connect to resources and perform light administrative tasks on your Windows Server Essentials server from your Windows-b...
Use The My Server App For Windows Phone
The My Server Windows app for Windows Phone (for Windows Server 2012) and the My Server 2012 R2 app for Windows Phone (for Windows Server Essential...
Use Microsoft Office 365 With Windows Server Essentials
Office 365 is an easy-to-use set of web-enabled tools that let you access your email, important documents, contacts, and calendar from almost anywh...
What is remote web access?
Remote Web Access helps you stay connected to your Windows Server Essentials network when you are away. For more information, see the topic Use Remote Web Access.
How to use VPN on Windows Server Essentials?
To use VPN to remotely access server resources. Press Ctrl + Alt + Delete on the client computer. Click Switch User on the logon screen. Click the network logon icon on the bottom right corner of the screen. Log on to the Windows Server Essentials network by using your network user name and password.
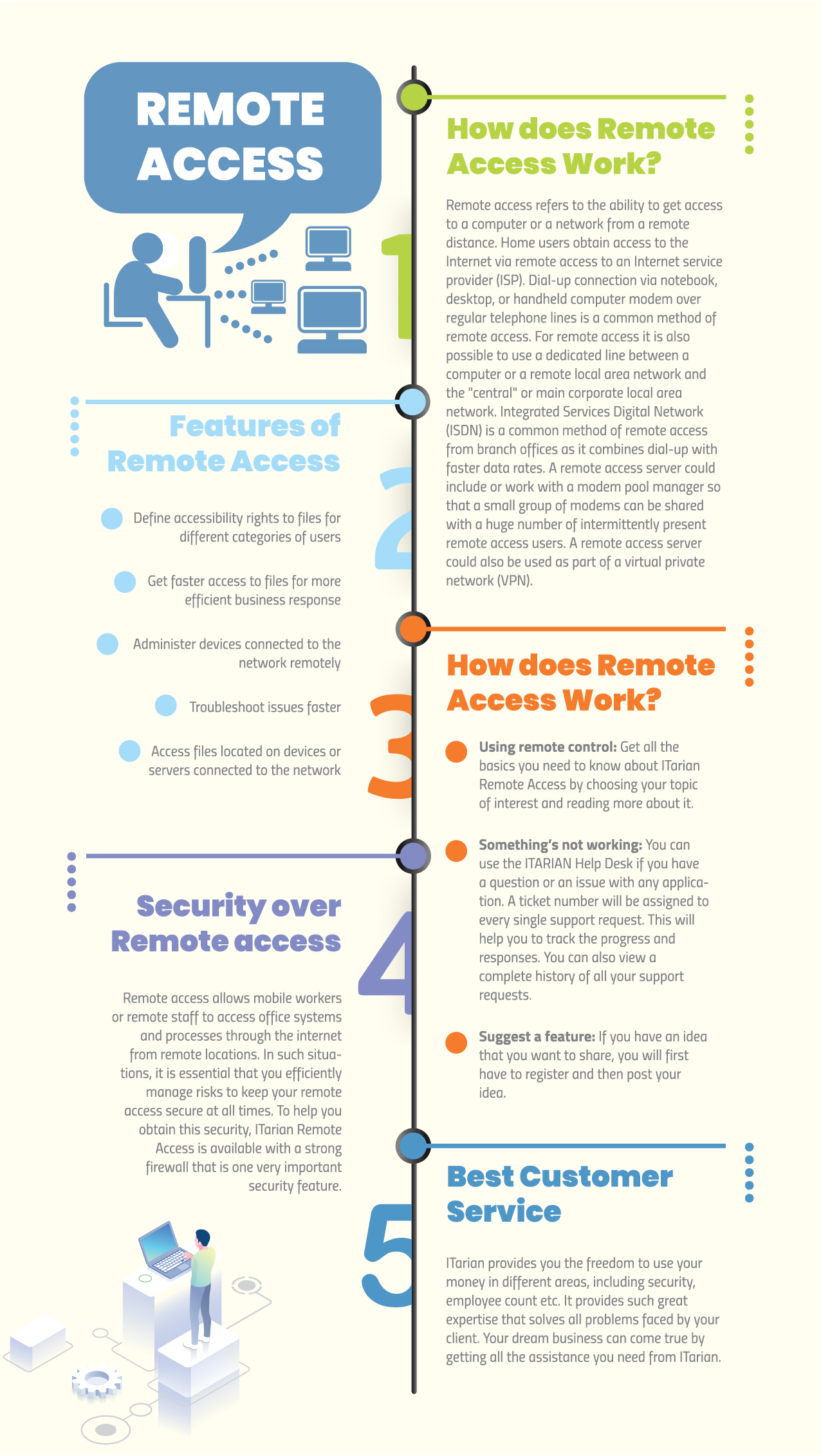
How does remote access work?
Remote access simply works by linking the remote user to the host computer over the internet. It does not require any additional hardware to do so. Instead, it requires remote access software to be downloaded and installed on both the local and remote computers. Once the software is installed, the local computer can access the remote computer and perform several tasks like running applications, managing updates, and even handling administrative tasks.
What is remote access?
Remote Access is simply reaching a remote machine, most often a computer, to carry out a particular task. In most cases, Remote Access is used to troubleshoot a target computer that is situated geographically at a different place.
Why do enterprises need remote access?
For businesses, remote access can maximize efficiency and boost employee productivity. By the year 2027, almost 50 percent of the US workforce is expected to be working remotely. With this many making the switch to remote work, it is essential to have a proper remote access solution in place to maintain business continuity.
What is ManageEngine Remote Access Plus?
ManageEngine Remote Access Plus is a modern remote access solution that lets users access and troubleshoot Windows, Mac and Linux computers remotely in a secure manner. This way, employee productivity will be unhindered without having to compromise on data security. Here are some top-notch features that make Remote Access Plus the best fit for any enterprise.
When was remote access first released?
Although the concept of remote access has stood the test of time, with its initial release in the year 2006, the basic functionalities have remained the same: troubleshooting remote PCs and accessing files remotely. However, the way remote access has evolved is in how these functions are delivered. Modern remote access software offers basic remote access capabilities with a host of side features like extensive reports, chat support, and bolstered security.
Is Remote Access Plus secure?
This is why Remote Access Plus comes with data privacy and security as its core mantra, which is reflected in features like recording remote sessions, prompting user confirmation for each session, and idle session timeout.
Database
DDE Function DDEInitiate Function DDERequest Function DDESend Function Eval Function Partition Function
File Management
CurDir Function Dir Function FileAttr Function FileDateTime Function FileLen Function GetAttr Function
Miscellaneous
CallByName Function IMEStatus Function MacID Function MacScript Function QBColor Function RGB Function Spc Function Tab Function
Question
I'm setting up a new Server 2016 Essentials. When I run the wizard to create my domain, "myserver.remotewebaccess.com", I received an error message "The Set Up Anywhere Access wizard completed with errors" There is an error in your Remote Desktop Services settings"
Answers
I was able to run the repair remote access wizard. That completed successfully.
All replies
When enable Remote Web Access via build-in wizard, RD Gateway server role is automatically installed and configured.
1. Server deployment
You can install Essentials as a member server in a domain of any size. Previously, Windows Server 2012 Essentials could be installed as the only domain controller of a small office network. Now Windows Server 2012 R2 Essentials can be installed on a virtual server or physical server, and on a member server in an existing domain of any size.
2. Client deployment
You can connect computers to your domain from a remote location. In other words, you can domain join your users’ mobile computers even when they are not on your corporate network.
3. Pre-configured auto-VPN dialing
If you need access to on-premise network resources there is a pre-configured VPN client. Figure C shows the box that appears after connecting the computer to the network over the Internet. The user can optionally trigger auto-VPN dialing so they are always connected to the workplace.
4. Server storage
You can create shared folders such as user home folders on a secondary server on the network. Get an alert when a server folder grows beyond its defined quota.
5. Health Report
A really useful Health Report is integrated with Windows Server 2012 R2 Essentials and no longer needs to be installed as an add-in. Depending on your business needs, you can customize the system health reports to display items that you prefer to monitor. Figure D shows a daily health report viewed on a smartphone.
6. BranchCache
You can turn on BranchCache to improve data access if the server running Windows Server 2012 R2 Essentials is located offsite. BranchCache is a wide area network (WAN) bandwidth optimization technology that is included in some editions of the Windows Server Windows client operating systems.
7. Office 365 integration
The following functionalities are new in Office 365 integration with Windows Server 2012 R2 Essentials: SharePoint Libraries management and Office 365 Distribution Groups management.
What is respond function?
The Respond Function includes appropriate activities to take action regarding a detected cybersecurity incident. The Respond Function supports the ability to contain the impact of a potential cybersecurity incident.
What is the Protect Function?
The Protect Function outlines appropriate safeguards to ensure delivery of critical infrastructure services. The Protect Function supports the ability to limit or contain the impact of a potential cybersecurity event.
What is the identify function?
The Identify Function assists in developing an organizational understanding to managing cybersecurity risk to systems, people, assets, data, and capabilities. Understanding the business context, the resources that support critical functions, and the related cybersecurity risks enables an organization to focus and prioritize its efforts, consistent with its risk management strategy and business needs.
How many functions are there in the framework core?
The five Functions included in the Framework Core are:
What is the purpose of data security?
Establishing Data Security protection consistent with the organization’s risk strategy to protect the confidentiality, integrity, and availability of information
What are the functions of the Cybersecurity Framework?
This learning module takes a deeper look at the Cybersecurity Framework's five Functions: Identify, Protect, Detect, Respond, and Recover. The information presented here builds upon the material introduced in the Components of the Framework module. This module explores the value of the Functions within the Framework, and what is included in each Function.
What is the purpose of essential records?
“Essential records” refers to information systems technology, applications and infrastructure, electronic and hardcopy documents, references, and records needed to support the continued performance of essential functions during a continuity activation . The National Institute of Standards and Technology (NIST) develops and issues standards, guidelines, and other publications to assist Federal agencies in implementing the Federal Information Security Management Act (FISMA) of 2002 and in managing cost-effective programs to protect their information and information systems. NIST has issued guidance for Federal information system contingency planning. Contingency planning refers to interim measures to recover information system services after a disruption. For more information please refer to:
What is the purpose of communication processes in emergency management?
Establish communication processes to notify emergency employees and non-emergency employees of the activation of the agency’s emergency plan and the agency operating status during the emergency.
How to ensure successful use of telework in the event of an emergency?
To ensure successful use of telework in the event of an emergency each Federal agency should: Establish a policy under which eligible employees, both ERG and non-ERG personnel, are authorized to telework during a continuity event. Notify all employees of their eligibility to telework during a continuity activation.
What is telework enhanced?
The Telework Enhancement Act states that “each Executive agency shall incorporate telework into the continuity of operations plan of that agency.” Incorporating telework into continuity plans means that these plans identify ways for an organization’s staff to perform the duties and responsibilities necessary to continue the organization’s essential functions during any type of threat or emergency from a telework location. The U.S. Department of Homeland Security's Federal Continuity Directive 1 (FCD 1), Federal Executive Branch National Continuity Program and Requirements (January 2017) defines Continuity of Operations (COOP) as “an effort within the Executive Office of the President and individual Departments and Agencies to ensure that essential functions continue to be performed during disruption of normal operations.” Requirements for organizations as it relates to incorporating telework into an agency’s continuity plans are found in Annex G of FCD 1.
What is the importance of the identification, protection, and ready availability of essential records, databases, and hardcopy documents?
The identification, protection, and ready availability of essential records, databases, and hardcopy documents needed to support essential functions under the full spectrum of all-hazards emergencies are critical elements of a successful continuity plan and program. Requirements for organizations as it relates to essential records management in a continuity event are found in Annex I of the Federal Continuity Directive (FCD) 1 . Additionally the National Archives & Records Management provides guidance to agencies and their employees that applies to Federal records in a telework environment on NARA's FAQs about Telework.
What should a manager do in an emergency?
Specifically, managers should: Understand the agency's emergency plans (continuity plan, pandemic plan, etc.) and management roles in executing the plan. Implement telework to the greatest extent possible so systems are in place to support successful telework in an emergency.
How can telework help?
Telework can be used to help slow the spread of disease by keeping face-to-face contact to a minimum (often referred to as "social distancing") while maintaining operations as close to normal as possible . Therefore, Federal agencies must plan to deal with the potential implications for human resources management.
Defining network security
The simple definition of network security is any combination of hardware and software products that operate in Layers 3 and 4 -- the network and transport layers -- of the OSI stack, with the primary function to manage access to the corporate network and network-embedded resources.
1. Network firewall
Firewalls are the first line of defense in network security. These network applications or devices monitor and control the flow of incoming and outgoing network traffic between a trusted internal network and untrusted external networks.
2. Intrusion prevention system
Network IPSes are software products that provide continuous monitoring of the network or system activities and analyze them for signs of policy violations, deviations from standard security practices or malicious activity. They log, alert and react to discovered issues.
3. Unified threat management
A UTM product integrates multiple networking and network security functions into a single appliance, while offering consolidated management. UTM devices must include network routing, firewalling, network intrusion prevention and gateway antivirus.
4. Advanced network threat prevention
Advanced network threat prevention products perform signatureless malware discovery at the network layer to detect cyber threats and attacks that employ advanced malware and persistent remote access. These products employ heuristics, code analysis, statistical analysis, emulation and machine learning to flag and sandbox suspicious files.
5. Network access control
NAC is an approach to network management and security that supports network visibility and access management. It consists of policies, procedures, protocols, tools and applications that define, restrict and regulate what an individual or component can or cannot do on a network.
6. Cloud access security broker
CASBs are on-premises or cloud-based security policy enforcement points for cloud application access and data usage.
Overview
Arrays
Conversion
Database
Date/Time
Domain Aggregate
File Input/Output
File Management
Financial
Inspection
Math
Miscellaneous
Program Flow
SQL Aggregate
Text
- Format Function
InStr Function - InStrRev Function
LCase Function
Functions (alphabetical)