Event Viewer Access Remote Computer
- Log in to the local computer as an administrator.
- Start the Event Viewer. For example, on Windows 10 computer type Event Viewer in the search box ...
- You will be connected to the remote computer right away, but you may not have the rights to view the Event Viewer logs if you don’t connect to the remote ...
- Event Viewer cannot open the event log or custom view. Verify that Event Log service is running or query is too long ...
- Step 1: Open Event Viewer as Admin. Hit start and type event viewer to search for the event viewer. ...
- Step 2: Connect to Another Computer. ...
- Step 3: Enter the Remote Computer Name or IP. ...
- Step 4: Browse the Remote Computer Logs.
Where to find Windows Event Log?
View the security event log
- Open Event Viewer.
- In the console tree, expand Windows Logs, and then click Security. The results pane lists individual security events.
- If you want to see more details about a specific event, in the results pane, click the event.
How to use LogMeIn to access another computer remotely?
How to Use LogMeIn to Control Another Computer
- Open the LogMeIn Client App and sign in.
- Then click the other computer you want to access. You will only see this if the other computer accepted your invitation and clicked the link you sent them from the ...
- Then click the computer icon. ...
- Then enter the login credentials for the computer you want to access. ...
How to remotely access another computer from your computer?
Using Quick Assist
- First of all, head to the Start Menu > Windows Accessories > Quick Assist.
- To remote into another computer, click on the ‘Give Assistance’ option.
- Now you will be asked to sign in with the Microsoft account and will receive a security code.
- Now the other person needs to open the Quick Assist tool and click on the ‘Get Assistance’ button.
How to view LogMeIn event log files?
Logmein Control Panel Archives 2019
- Access the host preferences: From the host computer, open the LogMeIn Pro Control Panel and follow this path: Options > Preferences > Advanced From a client device, connect to the ...
- Under Event Logs, click the View Files button. ...
- On the list, double-click the file you want to view. ...
Is there a log file for RDP connections?
Outgoing RDP Connection Logs in Windows You can also view outgoing RDP connection logs on the client side. They are available in the following event log: Application and Services Logs -> Microsoft -> Windows -> TerminalServices-ClientActiveXCore -> Microsoft-Windows-TerminalServices-RDPClient -> Operational.
What is RDP event log?
Logon refers to an RDP logon to the system, an event that appears after a user has been successfully authenticated. It is an event with the EventID 21 (Remote Desktop Services: Session logon succeeded).
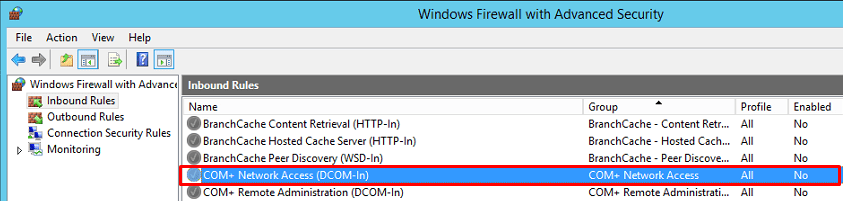
How do I enable remote view in Event Viewer?
In the Windows Control Panel, select Security and select Windows Firewall with Advanced Security. Select Inbound Rules and in the list, right-click Remote Event Log Management (RPC) and select Enable Rule.
Where is RDP history stored?
You can find information about RDP connection history in Event Viewer logs: Security; Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-RemoteConnectionManager -> Operational; TerminalServices-LocalSessionManager -> Admin.
Can you check Event Viewer remotely?
Accessing Remote Computer's Event Viewer Start the Event Viewer. For example, on Windows 10 computer type Event Viewer in the search box. You can also type EventVwr
How do I connect to another computer in Event Viewer?
To select computers in Event ViewerClick Start, and point to Programs.Point to Administrative Tools, and then click Event Viewer.Right-click Event Viewer (top level).Select Connect to another computer.Type the computer name on which to view Event Logs, and click OK.
How do I enable RPC remotely?
Method 1. Make sure the RPC services are runningOpen the search bar in your taskbar by clicking on the magnifying glass icon. ... Type in Services and click on the first search result.Scroll down and locate the Remote Procedure Call (RPC) service from the list. ... Ensure that the Startup type is set to Automatic.More items...
What is Event ID 40?
Event ID - 40 The event logging service encountered an error when attempting to apply one or more policy settings. Event Information. According to Microsoft : Cause. This event is logged when the event logging service encountered an error when attempting to apply one or more policy settings.
What is Qwinsta command?
Displays information about sessions on a Remote Desktop Session Host server. The list includes information not only about active sessions but also about other sessions that the server runs. This command is the same as the query session command.
Step 1: Enable Setting in Registry and GPO
After adding above settings to the Sceregvl.inf in the %Windir%\Inf . Click File > Save.
Step 4: Enter SDDL for Event log Delegation
The above SDDL is to reinstate the permissions for the builtin users account in Windows eg: Server Operators etc.
What does the logs do on a RDP server?
Then you will get an event list with the history of all RDP connections to this server. As you can see, the logs provide a username, a domain (in this case the Network Level Authentication is used; if NLA is disabled, the event text looks differently) and the IP address of the computer, from which the RDP connection has been initiated.
How to check RDP logs?
You can check the RDP connection logs using Windows Event Viewer ( eventvwr.msc ). Windows logs contain a lot of data, and it is quite difficult to find the event you need. When a user remotely connects to the remote desktop of RDS (RDP), a whole number of events appears in the Windows Event Viewer. There are several different logs where you can find the information about Remote Desktop connections. We’ll look at the logs and events on the main stages of an RDP connection that may be of interest to the administrator:
What is logoff in Windows?
Logoff refers to the user logoff from the system. It is logged as the event with the EventID 23 ( Remote Desktop Services: Session logoff succeeded) in “Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-LocalSessionManager -> Operational”.
What is EventID 4778?
The event with the EventID 4778 in Windows -> Security log (A session was reconnected to a Window Station). A user has reconnected to an RDP session (a user is assigned a new LogonID).
What does event ID 21 mean?
The event with the EventID – 21 ( Remote Desktop Services: Shell start notification received) means that the Explorer shell has been successfully started (the desktop appears in the user’s RDP session).
What does the RDP session ID return?
The command returns the session ID (ID), the name of user (USERNAME) and the session state (Active/Disconnect). It is convenient to use this command when you need to get the ID of the user RDP session in case shadow connection is used.
Where is the RDP authentication log?
Authentication shows whether an RDP user has been successfully authenticated on the server or not. The log is located in “Windows -> Security”. So you may be interested in the events with the EventID 4624 ( An account was successfully logged on) or 4625 ( An account failed to log on ). Please, pay attention to the LogonType value in the event description. If the Remote Desktop service has been use to create new session during log on, LogonType = 10. If the LogonType = 7, it means that a user has reconnected to the existing RDP session.
Network Connection
This section covers the first indications of an RDP logon – the initial network connection to a machine.
Authentication
This section covers the authentication portion of the RDP connection – whether or not the logon is allowed based on success/failure of username/password combo.
Logon
This section covers the ensuing (post-authentication) events that occur upon successful authentication and logon to the system.
Logoff
This section covers the events that occur after a purposeful (Start -> Disconnect, Start -> Logoff) logoff.
Wrap-Up
Hopefully that provides a little better insight into some of the most common and (IME) most empirically useful RDP-related Event logs, when/where you might encounter them, what they mean, what they look like, and (most importantly) how they all fit together.
How to remotely collect Windows event logs?
There are multiple ways to remotely access and collect windows event logs.
How to collect log data?
Predominantly, there are two methods to collect log data—agent-based and agentless. Agent-based log collection requires installation of an agent in every machine that collects and forwards the log data from the device to the central server. When collecting log data from a secured network, agent-based log collection is employed. In other circumstances, this method is not preferred as it is difficult to administer. So, enterprises prefer native log forwarding and at times remote log collection.
How to collect syslogs remotely?
Collecting syslogs remotely is a fairly simple process involving two steps—configuring the remote server that will centrally collect all log data, and configuring the devices to send log data to the remote server.
What is WRM in domain?
Enabling domain computers to remote connection: Windows Remote Management (WRM) is a protocol that is used for exchanging information across systems in the domain. For remote log collection, you need to enable this protocol on each of the devices to facilitate log data exchange. To enable WRM protocol, login to the source computers as a local or domain administrator and execute the below command.
Why is it important to collect logs?
Every enterprise needs to collect and monitor log data from devices across their network to ensure security, troubleshoot operational issues, and conduct forensic analysis on security incidents. For this they might rely on either a log management tool or a SIEM solution. Irrespective of the tool used, collecting logs to a centralized location is more difficult than it appears. From configuring the devices to send log data to central server to ensure security of logs in transit, log collection is as important and tough as any other log management processes.
Why assign static IP address to remote server?
Assign a static IP address to the remote server. This helps the devices to contact and constantly send the log data to the remote server.
Can service account read logs?
The service account is now able to read all the logs from any part of the domain through Event Viewer UI. Just a few more steps now.
