
DIAL-UP CONNECTIVITY
| PROTOCOL | WHEN USED | NOTES |
| Point-to-Point Protocol (PPP) | PPP is almost always the protocol of cho ... | Supports TCP/IP as well as other LAN pro ... |
| Serial Line Internet Protocol (SLIP) | SLIP is used as a client in NT or Win2K ... | Allows TCP/IP connections only and does ... |
| Asynchronous NetBEUI (AsyBEUI) | This is a Microsoft proprietary remote a ... | Supports only the NetBEUI LAN protocol. |
How to properly secure remote access?
- Windows or Mac login when connecting remotely
- Request permission to connect to the user’s computer
- Automatically blank the remote screen when connected
- Automatically lock remote computer when disconnected
- Lock the remote computer’s keyboard and mouse while in session
- Lock the streamer settings using Splashtop admin credentials
What is the best remote access for PC?
What is the Best Remote Desktop Software?
- GoToMyPC. GoToMyPC is the best remote desktop software on this list. ...
- AnyDesk. AnyDesk is one of the most popular remote desktop software platforms, used by over 100 million users globally.
- LogMeIn. ...
- Parallels. ...
- Splashtop Business Access. ...
- Zoho Assist. ...
- ConnectWise Control. ...
- RemotePC. ...
- TeamViewer. ...
- Remote Utilities for Windows. ...
How do you connect to your computer remotely?
To set up it:
- Go to Menu > System Preferences > Sharing
- Select Remote Management - it should appear as a checkbox.
- Now you can select who has remote desktop access. Either select, All Users, which means any other device on your network, or Mac you own, can access and connect, or ...
How to enable remote access for remote management?
To set up remote management:
- Launch a web browser from a computer or mobile device that is connected to your router’s network.
- Enter http://www.routerlogin.net. ...
- Enter the router user name and password. ...
- Select ADVANCED > Advanced Setup > Remote Management. ...
- Select the Turn Remote Management On check box.

What is a remote access protocol?
A remote access protocol is responsible for managing the connection between a remote access server and a remote computer. It's necessary for desktop sharing and remote access for help desk activities.
What is remote access explain with example?
Remote access refers to the ability to access a computer, such as a home computer or an office network computer, from a remote location. This allows employees to work offsite, such as at home or in another location, while still having access to a distant computer or network, such as the office network.
What are some protocols that can be used for remote access?
The Remote Desktop Protocol (RDP) is a protocol, or technical standard, for using a desktop computer remotely. Remote desktop software can use several different protocols, including RDP, Independent Computing Architecture (ICA), and virtual network computing (VNC), but RDP is the most commonly used protocol.
Which of the remote is a secure remote access protocol?
Most Secure Remote Access Protocol | Remote Desktop (RDP)
What is remote access and its advantages?
With remote access, employees can safely work from any device, platform, or network at their home office or abroad. Remote desktop functions allow them to remotely access important files and share their screen for meetings and troubleshooting.
What is the most secure remote access?
Best for Team Collaboration TeamViewer TeamViewer lets users access remote computers and devices running Windows, Mac OS, Linux, Android, and iOS. It also offers drag-and-drop file transfer, remote printing, and secure unattended access using two-factor authentication and 256-bit AES encryption.
What is secure remote access VPN?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
What is secure remote communications?
Secure Remote Working is a combination of multiple technologies and procedures comprising: Virtual Private Network (VPN) – Facilitates secure access to on-premises applications and services. VPNs also provide secure internet access for employees on public wireless or third-party corporate networks.
What is remote access protocol?
In addition to an IP address, you need a remote access protocol to connect to the Internet. A remote access protocol is a communications standard that allows your computer to talk to the remote network. If you ever intend to work from home, you will appreciate this service. After all, it enables telecommuting. There are three common remote access protocols used today: PPP, PPTP, and SLIP.
What is PPP protocol?
Point-to-Point Protocol (PPP) is the data link protocol emerging as the de facto choice of remote access protocols. PPP is the most common protocol used for dial-up access. In addition, to providing speed and reliability, PPP offers:
What is VPN in Microsoft?
Point-to-Point Tunneling Protocol (PPTP), now commonly referred to as VPN (Virtual Private Networking) is Microsoft's version of PPP that encapsulates packets from other protocols for transmission over an IP network. It is used to create a secure network utilizing public lines (the Internet). VPN essentially enables users access to a secure corporate network from remote locations (such as from a salesperson's portable computer located in a hotel room). Prior to VPN, a dedicated rented line was required from point-to-point to assure high levels of security.
What are the two methods of remote access?
First, you need to consider two distinct methods of remote access, each of which uses different protocols: Dial-up. Virtual private networking (VPN) Within each method, there are three basic categories for protocols: Connectivity. Authentication.
How to make sense of all the protocol configuration options involved in setting up remote access servers?
To help make sense of all the protocol configuration options involved in setting up remote access servers, take a look at the categories of protocols and the advantages and disadvantages of the various protocols within each one.
What protocol is used for dial up encryption?
For data encryption in a dial-up session in a Windows network. In order to use MPPE, the authentication protocol for the dial-up session must be either EAP-TLS or MS-CHAP version 1 or 2. VPN protocols.
What is virtual private network?
Virtual private networking protocols encapsulate PPP frames (the data units at the data link layer of the OSI model) into IP datagrams at the network layer. These datagrams are then sent across an internetwork, which can be either a private network or, more commonly, the Internet. This encapsulation creates a “tunnel” that acts like a dedicated WAN link, even though it usually uses the Internet—thus, a “virtual” private network.
Why do you want to be encrypted in a remote session?
First, you want the best security you can provide for the remote session. You want authentication to be encrypted so that someone who is snooping cannot see it , and you want the data that is passed in the remote session to be encrypted for the same reason. Second, older systems and their associated protocols are less capable in terms ...
What is dial up modem?
Dial-up involves one modem connecting with another over the Public Switched Telephone Network (PSTN), creating a temporary, dedicated WAN link. There are three possible protocols for making the initial connection: Point-to-Point Protocol (PPP), Serial Line Internet Protocol (SLIP), and Asynchronous NetBEUI (AsyBEUI). Table A explains their differences.
How does dial up authentication work?
Authenticating the user. Part of the dial-up process involves authentication, usually by providing a password. Since that password can be intercepted and used to gain unauthorized access, it should be encrypted using the strongest possible method that is supported by both the server and the client.
What is a RAS modem?
Both Windows NT and Windows 2000 include technology to allow users to dial up a server and connect to not only that server, but also to that server’s host network. This technology is known as RAS. RAS is used in smaller networks where a dedicated dial-up router is not practical or possible. In a RAS setup, you can basically connect a modem to a Windows NT or Windows 2000 server and, by way of the RAS, configure that modem as dial-out only, dial-up only, or a combination.
What is PPTP in a network?
PPTP is the Microsoft-created protocol based on PPP. It is used to create virtual connections across the Internet using TCP/IP and PPP so that two networks can use the Internet as their WAN link and yet retain private network security. PPTP is both simple and secure.
How to use PPTP?
To use PPTP, you set up a PPP session between the client and server, typically over the Internet. Once the session is established, you create a second dial-up session that dials through the existing PPP session using PPTP. The PPTP session tunnels through the existing PPP connection, creating a secure session.
How to display destination address on PPP?
Select the connection to establish the PPP connection or choose not to dial an initial connection. Then click Next to display the Destination Address window.
What is PPP over Ethernet?
There is a version of PPP called PPP over Ethernet (PPPoE) that allows the authentication methods of PPP to be used over Ethernet and high-speed Internet connections so individual users can be authenticated for Internet access over a shared medium like Ethernet or DSL.
What is PPP used for?
PPP is used to implement TCP/IP; it is the protocol that establishes a connection over point-to point links (for example, dial-up and dedicated leased lines). It is most commonly used for remote connections to ISPs and LANs.
What is a SLIP connection?
SLIP is used today primarily to connect a workstation to the Internet or to another network running TCP/IP. Setting up SLIP for a remote connection requires a SLIP account on the host machine and usually a batch file or a script on the workstation.
What is RDP protocol?
This article describes the Remote Desktop Protocol (RDP) that's used for communication between the Terminal Server and the Terminal Server Client. RDP is encapsulated and encrypted within TCP.
Why is RDP used in Windows NT?
One reason that Microsoft decided to implement RDP for connectivity purposes within Windows NT Terminal Server is that it provides an extensible base to build many more capabilities. RDP provides 64,000 separate channels for data transmission. However, current transmission activities are only using a single channel (for keyboard, mouse, ...
Why use RDP?
One of the key points for application developers is that, in using RDP, Microsoft has abstracted away the complexities of dealing with the protocol stack. It allows them to write clean, well-designed, well-behaved 32-bit applications. Then the RDP stack implemented by the Terminal Server and its client connections takes care of the rest.
What is MCS in RDP?
The MCS is made up of two standards: It essentially abstracts the multiple RDP stacks into a single entity, from the perspective of the GCC. GCC is responsible for management of those multiple channels. The GCC allows the creation and deletion of session connections and controls resources provided by MCS.
How does RDP work?
Data from an application or service to be transmitted is passed down through the protocol stacks. It's sectioned, directed to a channel (through MCS), encrypted, wrapped, framed, packaged onto the network protocol, and finally addressed and sent over the wire to the client. The returned data works the same way only in reverse. The packet is stripped of its address, then unwrapped, decrypted, and so on. Finally the data is presented to the application for use. Key portions of the protocol stack modifications occur between the fourth and seventh layers, where the data is:
What is RDP in Microsoft?
highly encrypted data, such as keyboard, mouse activity. RDP is an extension of the core T.Share protocol. Several other capabilities are retained as part of the RDP, such as the architectural features necessary to support multipoint (multiparty sessions).
What is RDP in computer?
However, current transmission activities are only using a single channel (for keyboard, mouse, and presentation data). RDP is designed to support many different types of Network topologies, such as ISDN, POTS. RDP is also designed to support many LAN protocols, such as IPX, NetBIOS, TCP/IP.
How does remote access work?
Remote access is accomplished with a combination of software, hardware and network connectivity.
What are the types of remote access?
Traditionally, enterprises used modems and dial-up technologies to allow employees to connect to office networks via telephone networks connected to remote access servers. Devices connected to dial-up networks use analog modems to call assigned telephone numbers to make connections and send or receive messages.
What is remote access software?
A remote access software is a tool that allows you to access another computer from a remote location. From there, you can now access files, use apps, and even perform administrative tasks on the remote computer as if you’re in front of it.
Is VPN a security risk?
While a Virtual Private Network or VPN is one of the most sought-after remote access solutions at the moment, it can still pose a few security risks for your organization. A VPN can still be exposed to a bunch of security threats outside of a company’s network.
Can remote desktop access restrict access to sensitive data?
Remote Desktop Access software also can restrict users to access sensitive and confidential data. You can also disable file transfer features on remote access software when there’s no reason for your employees to do so.
Is remote access a target ground for hacking?
As remote access can be helpful to organizations these days, it can also be a target ground for modern hacking and online theft.
Can a VPN be exposed to a security threat?
A VPN can still be exposed to a bunch of security threats outside of a company’s network. A report from Trustwave found that the majority of the data breaches it investigated in 2011 were associated with a VPN connection. One alternative option for a VPN is remote access software. A remote access software is a tool that allows you ...
What is secure remote access?
Secure remote access refers to any security policy, solution, strategy or process that exists to prevent unauthorized access to your network, its resources, or any confidential or sensitive data. Essentially, secure remote access is a mix of security strategies and not necessarily one specific technology like a VPN.
What technologies are used for secure remote access?
Secure remote access is comprised of a multitude of security solutions and technologies. Some of the most prominent include the following:
Secure remote access solution
Enables employees with precise access to the applications and data required to do their job from anywhere.
Why is secure remote access important?
With the work from home shift in the workforce, endpoints are accessing corporate networks from multiple locations. Today, employees’ home networks are often the originating point for network connections, multiplying the risk on both home and corporate networks.
What are the benefits of secure remote access?
While the benefits of secure remote access are numerous, there are four key advantages in which to focus on:
Can secure remote access be achieved without VPN?
Yes. A robust cloud-based, highly secure remote access solution can provide unified protection for virtually all users against web-based threats — independent of a VPN connection.
How can AT&T help organizations with secure remote access?
AT&T Cybersecurity is uniquely positioned to help organizations address these immediate challenges with an eye toward the future by helping them balance connectivity, collaboration, and cybersecurity affordably.
What is the protocol used for remote desktop?
Remote desktop software can use several different protocols, including RDP , Independent Computing Architecture (ICA), and virtual network computing (VNC), but RDP is the most commonly used protocol.
What is the Remote Desktop Protocol (RDP)?
The Remote Desktop Protocol (RDP) is a protocol, or technical standard, for using a desktop computer remotely. Remote desktop software can use several different protocols, including RDP, Independent Computing Architecture (ICA), and virtual network computing (VNC), but RDP is the most commonly used protocol. RDP was initially released by Microsoft and is available for most Windows operating systems, but it can be used with Mac operating systems too.
What does 'remote desktop' mean?
Remote desktop is the ability to connect with and use a faraway desktop computer from a separate computer. Remote desktop users can access their desktop, open and edit files, and use applications as if they were actually sitting at their desktop computer. Employees often use remote desktop software to access their work computers when they are traveling or working from home.
What are the pros and cons of using RDP?
One advantage is that it does not require a VPN. It also keeps data stored securely on the user's desktop, instead of storing it on cloud servers or on the user's unsecured personal devices. Furthermore, RDP enables companies with a legacy on-premises IT setup to allow their employees to work from home.
How does RDP work?
Think of a remote-controlled drone or toy car. The user presses buttons and steers the drone or car from afar, and their commands are transmitted to the vehicle. Using RDP is somewhat like that: the user's mouse movements and keystrokes are transmitted to their desktop computer remotely, but over the Internet instead of over radio waves. The user's desktop is displayed on the computer they are connecting from, just as if they were sitting in front of it.
How is remote desktop different from cloud computing?
Remote desktop access is very different from cloud computing, even though both allow employees to work remotely. In cloud computing, users access files and applications that are stored in the cloud — specifically, in cloud servers. In contrast, when using remote desktop software, users are actually accessing their physical desktop computer, and can only use files and applications saved locally on that desktop. Cloud computing is sometimes easier to use and more efficient to implement for remote workforces, but many companies have not migrated to the cloud, or cannot for security or regulatory reasons.
How does Cloudflare help accelerate and secure RDP?
Cloudflare Spectrum reduces network latency associated with long-distance RDP connections and other network issues. Cloudflare decreases the connection time for sessions and helps reduce overall network latency for a more real-time user experience by using smart routing. Cloudflare also uses Argo Tunnel to prevent unauthorized port 3389 connections, making RDP more secure.
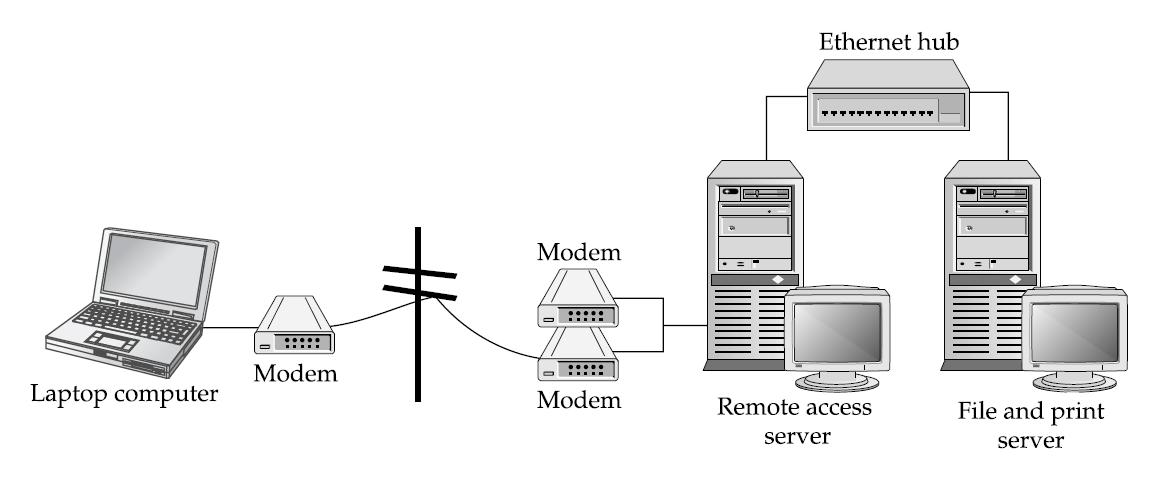
Serial Line Internet Protocol (Slip)`
Point-To-Point Tunneling Protocol
- PPTP is a remote access protocol, based on PPP, created by Microsoft. It’s used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network. PPTP is a great option because it’s simple and secure. To use PPTP, you’ll have to set up a PPP session be…
Windows Remote Access Services
- Windows 2000 and Windows NT let users dial up a server and connect to both the server and the server’s host network. This is referred to as RAS, which is used in smaller networks where a dedicated dial-up router would not be possible or practical. With a RAS setup, you can connect a modem to a Windows 2000 or Windows NT server and configure the modem as dial-out only, di…
Remote Desktop Protocol
- Finally, there is the RDP, which is very similar to the Independent Computing Architecture (ICA) protocol used by Citrix products. RDP is utilized to access Windows Terminal Services, which is a close relative of the product line provided by Citrix WinFrame. RDP offers the same core functions as ICA, although there are some limitations. RDP provides remote access for Windows clients o…