Clientless remote access is remote network access obtained without the installation of software on a user's device. Unlike IPsec VPNs, the F5 BIG-IP APM provides remote access without requiring pre-installed client software and configuration of the remote device. Neither client- nor server-side application changes are required.
Full Answer
What is the F5 deployment guide?
This F5 deployment guide shows administrators how to configure the BIG-IP GTM and APM v11.2 and later to provide high availability and secure remote access to corporate resources from anywhere in the world. In this solution, the BIG-IP GTM intelligently directs traffic to the closest available branch office to the user.
How do I apply an RDG policy to APM?
Without an RDG policy, APM denies access to each resource request. link to apply and activate the changes to the policy. To apply this access policy to network traffic, add the access profile to a virtual server.
What configuration objects can I use with APM as a gateway?
If you already have configured them, you can use existing configuration objects: a machine account, an NTLM authentication configuration, a VDI profile, a connectivity profile, and a client SSL profile. Supported Microsoft RDP clients can use APM as a gateway.
What is BIG-IP APM and GTM?
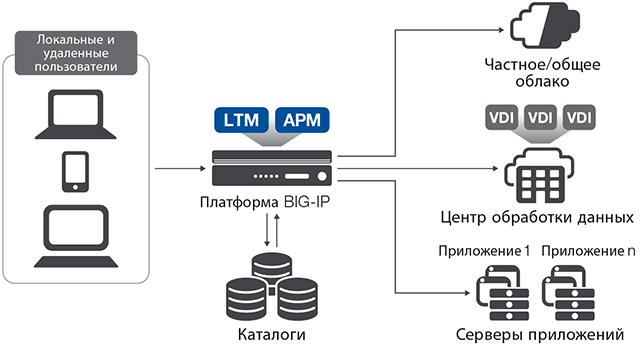
In this solution, the BIG-IP GTM intelligently directs traffic to the closest available branch office to the user. The BIG-IP APM uses one of several options to authenticate the user, and then creates a secure session between the user and the remote office.

What is F5 APM used for?
F5 BIG-IP Access Policy Manager (APM) secures, simplifies and centralizes access to apps, APIs and data, no matter where users and their apps are located.
What is APM in F5 load balancer?
F5® BIG-IP® Access Policy Manager® (APM) is a secure, flexible, high-performance access. management proxy solution managing global access to your network, the cloud, applications, and application programming interfaces (APIs).
What is APM network access?
F5® BIG-IP® Access Policy Manager® (APM) is a secure, flexible, high-performance access management proxy solution that delivers unified global access control for your users, devices, applications, and application programming interfaces (APIs).
What is Webtop F5?
A full webtop allows your users to connect and disconnect from a network access connection, portal access resources, SAML resources, app tunnels, remote desktops, and administrator-defined links. On the Main tab, click Access Policy > Webtops. Click Create to create a new webtop.
What is difference between APM and Pam in F5?
Hi, BigIP uses PAM to authenticate administrators on linux system. APM (Access Policy Manager) is an authentication module for connections going through virtual servers.
How do I find F5 APM logs?
APM Logs are generally found in: Access > Overview > Event Logs > Settings where they can be applied to specific APM profiles. There are 2 APM Log setting options located in: System > Logs > Configuration > Options that should not be used unless explicitly directed by F5 Support during an active Support Incident.
How do I set up F5 in access?
Configuring a connectivity profile for F5 Access for AndroidOn the Main tab, click Access > Connectivity / VPN > Connectivity > Profiles . ... Select the connectivity profile that you want to update and click Edit Profile. ... From Mobile Client Settings in the left pane, select Android Edge Client.More items...
How do I open the Big-IP Configuration Utility?
Use BIG-IP configuration utility tool to set management IP address¶Connect to the virtual machine by using the hypervisor's console.At the login prompt, type root .At the password prompt, type default . ... Type config and press Enter. ... Click OK.More items...
How do you see last changes in F5?
May 26, 2022 F5 has videos to help you upgrade or update your BIG-IP systems....To search the audit logs:In the BIG-IP UI, select System > Logs > Audit > List.In the text field, enter the word transaction.Select Search.Scroll to the time of the last configuration change.
How does f5 VPN Work?
IPsec VPN – Establishes a VPN over the public Internet using the standard IPsec mechanism. SSL VPN – Uses Secure Sockets Layer protocol, an authentication and encryption technology built into every web browser, to create a secure and encrypted connection over a less secure network, like the Internet.
How do I access Webtop?
A webtop provides a screen for your users to connect and disconnect from the portal access connection.On the Main tab, click Access Policy > Webtops.Click Create to create a new webtop.Type a name for the webtop you are creating.From the Type list, select Portal Access.More items...
How does F5 ASM work?
F5 BIG-IP® Application Security Manager™ (ASM) is a flexible web application firewall that secures web applications in traditional, virtual, and private cloud environments. BIG-IP ASM helps secure applications against unknown vulnerabilities, and enables compliance for key regulatory mandates.
What is Bigip?
The BIG-IP platform is a smart evolution of Application Delivery Controller (ADC) technology. Solutions built on this platform are load balancers. And they're full proxies that give visibility into, and the power to control—inspect and encrypt or decrypt—all the traffic that passes through your network.
What are the F5 modules?
BIG-IP Software Modules The Local Traffic Manager™ (LTM) and Global Traffic Manager™ (GTM) are the core modules F5 has built it's application delivery architecture on. F5 now offers a whole product suite that builds on those capabilities - making F5 the most comprehensive solution to deliver your applications.
What is virtual server in load balancer?
A Virtual Load Balancer provides more flexibility to balance the workload of a server by distributing traffic across multiple network servers. Virtual load balancing aims to mimic software-driven infrastructure through virtualization. It runs the software of a physical load balancing appliance on a virtual machine.
What is an APM?
Access Policy Manager (APM ®) can act as a gateway for Microsoft RDP clients, authorizing them on initial access and authorizing access to resources that they request after that. The APM configuration includes these elements.
What happens after APM authorizes a Microsoft RDP client?
After APM authorizes a Microsoft RDP client, subsequent resource requests are sent to APM.
What configuration objects can you use for NTLM?
If you already have configured them, you can use existing configuration objects: a machine account, an NTLM authentication configuration, a VDI profile, a connectivity profile, and a client SSL profile.
What is NTLM access policy?
This access policy runs when the RDP client initiates a session with the gateway (APM). Only NTLM authentication is supported. This access policy should verify that NTLM authentication is successful and must assign an additional access policy to use for resource authorization throughout the session.
Why do you create an access profile?
You create an access profile to provide the access policy configuration for a virtual server that establishes a secured session.
How long does an access policy timeout need to be?
field, type the number of seconds that should pass before the access profile times out because of inactivity. The timeout needs to be at least 15 minutes long because an RDP client sends a keepalive to the gateway every 15 minutes. To prevent a timeout, type.
When does an access policy run?
This access policy runs when the authorized RDP client requests access to a resource. The access policy must contain logic to determine whether to allow or deny access to the target server and port.
What is APM in RDP?
With proper BIG-IP ® system configuration, Microsoft RDP clients can use APM as a gateway. The configuration supports Microsoft RDP clients on Windows, Mac, iOS, and Android. When a user types the address or hostname of the gateway into an RDP client and specifies a particularly configured virtual server for it, APM authorizes the client. When the client requests connections to resources on backend servers, APM authorizes the access.
How to complete the process of remote desktop?
To complete the process, you must apply the access policy, and associate the access policy and connectivity profile with a virtual server so users can launch the remote desktop session.
What is Citrix remote desktop?
Citrix ® remote desktops are supported by Citrix XenApp™ and ICA clients. With Access Policy Manager ® you can configure clients to access servers using Citrix terminal services. You provide a location from which a client can download and install a Citrix client for a Citrix ICA connection.
What is RDP in Microsoft?
RDP is a protocol that provides a graphical interface to another computer on a network.
Is there a subset of access policy items?
Note: Only an applicable subset of access policy items is available for selection in the visual policy editor for any access profile type.
Description
Understand the APM + LTM use cases as well as Configure APM and LTM to work together for advanced application delivery
Instructor
Hey, I am a 5-year experienced Network Security Architect and have been in Network industry for more than 20 years. My main focus are designing flexible and scalable Data Centers network, Secured Edge and application solution.
Student feedback
Great simple explanation of the subject. Instructor is very detailed and not overly complex, keeps things simple. About time someone made a course for F5 APM. The price is fair and not over the top.