What is F5 remote access?
Clientless remote access is remote network access obtained without the installation of software on a user's device. Unlike IPsec VPNs, the F5 BIG-IP APM provides remote access without requiring pre-installed client software and configuration of the remote device.
What is a secure remote access?
Secure Remote Access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization's digital assets and prevent the loss of sensitive data.
Is F5 a VPN?
F5 Network's FirePass SSL VPN is an SSL VPN that provides broad application support, scalability, easy installation and use, and the highest standard of integrated end-point security.
What allows for secure remote console access?
You can enable remote access (dial-up or VPN), Network Address Translation (NAT), both VPN and NAT, a secure connection between two private networks (site-to-site VPN), or you can do a custom configuration to select any combination of these, as shown in Figure 14.25.
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
How do I create a secure remote access?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
How do I connect to F5 in access?
Connect to a profile to use the connections to your network supported by F5 Access.On your Windows system, select. Settings. VPN. . On Windows Mobile, select. Settings. Network & Wireless. VPN. ... Select the existing VPN profile. Additional options display.From the new options, select. Connect. .
How do I set up F5 in access?
Configuring a connectivity profile for F5 Access for AndroidOn the Main tab, click Access > Connectivity / VPN > Connectivity > Profiles . ... Select the connectivity profile that you want to update and click Edit Profile. ... From Mobile Client Settings in the left pane, select Android Edge Client.More items...
Is F5 VPN good?
An excellent VPN solution for companies. A good VPN solution for companies. Especially on Mac. No disconnection or connection problems.
How does a remote access work?
Remote access simply works by linking the remote user to the host computer over the internet. It does not require any additional hardware to do so. Instead, it requires remote access software to be downloaded and installed on both the local and remote computers.
What is remote access examples?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
Which protocol would be best to use to securely access the remote network devices?
Remote Desktop Protocol or RDP is a communications protocol designed to manage remote access to desktops, files, systems, and even private networks.
Why is secure remote access important?
A secure remote access system protects your employees from web-based threats such as phishing attacks, ransomware and malware while they're logged in to your company's network. These cyber incidents can lead to unauthorized access and use of both the company's business data and the employee's personal data.
Should I give remote access to my computer?
Remote access solutions could leave you vulnerable. If you don't have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data. Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular.
What is the main purpose of a RAS server?
A remote access server (RAS) is a type of server that provides a suite of services to remotely connected users over a network or the Internet. It operates as a remote gateway or central server that connects remote users with an organization's internal local area network (LAN).
Which is a more secure form of remote access over a network?
Virtual private network (VPN)Virtual private network (VPN) – The most common and well-known form of secure remote access, VPNs typically use the public Internet to connect to a private network resource through an encrypted tunnel.
What is SIEM in Azure?
Several options exist for logging events either locally, or remotely through a Security Information and Event Management (SIEM) solution, enabling off-box storage and processing of telemetry. A highly effective solution for monitoring Azure AD and SHA-specific activity, is to use Azure Monitor and Microsoft Sentinel, together offering:
Is APM a federation trust?
The integration is based on a standard federation trust between the APM and Azure AD, common to most SHA use cases that includes the SSL-VPN scenario. Security Assertion Markup Language (SAML), OAuth and Open ID Connect (OIDC) resources are no exception either, as they too can be secured for remote access. There could also be scenarios where a BIG-IP becomes a choke point for Zero Trust access to all services, including SaaS apps.
What is APM in remote desktop?
When you create a remote desktop resource, Access Policy Manager (APM) automatically creates an allow ACL for the IP addresses and ports specified in the resource. To disallow access to any other IP addresses and ports, you must create ACLs that deny access to them and assign the ACLs in the per-session policy. F5 recommends that you create an ACL that rejects access to all connections and put it last in the ACL order.
How to complete the process of remote desktop?
To complete the process, you must apply the access policy, and associate the access policy and connectivity profile with a virtual server so users can launch the remote desktop session.
What is APM webtop?
APM webtop supports native connections for Windows, Mac, and Linux clients. When this option is selected, a user on any compatible platform is presented with a simple interface to the Microsoft RDP server with reduced visual display features.
What is APM in RDP?
The configuration supports Microsoft RDP clients on Windows, Mac, iOS, and Android. When a user types the address or hostname of the gateway into an RDP client and specifies a particularly configured virtual server for it, APM authorizes the client. When the client requests connections to resources on backend servers, APM authorizes the access.
How many log settings can you add to an access profile?
You can assign up to three log settings that enable access system logging to an access profile. You can assign additional log settings to an access profile provided that they enable logging for URl request logging only.
Can Citrix remote desktop be used with ICA?
Citrix ® remote desktops are supported by Citrix XenApp ™ and ICA clients. With Access Policy Manager you can configure clients to access servers using Citrix terminal services. You provide a location from which a client can download and install a Citrix client for a Citrix ICA connection.
How to edit access profile?
The Access Profiles ( Per-Session Policies) screen opens. Click the name of the access profile for which you want to edit the access policy. The properties screen opens for the profile you want to edit. On the menu bar, click.
Secure Remote Access for Employees and Vendors
Traditional remote access methods, such as RDP, Virtual Private Networks, and legacy remote desktop tools lack granular access management controls. These processes enable easy exploits via stolen credentials and session hijacking. Extending remote access to your vendors makes matters even worse.
Privileged Remote Access: Use Cases
BeyondTrust Privileged Remote Access controls, manages, and audits remote privileged access to critical IT systems by authorized employees and third-party vendors. No VPN required.
Remote Support: Use Cases
BeyondTrust Remote Support allows help desk teams to securely access and fix any remote device on any platform, located anywhere in the world. All with the same solution.
Secure Remote Access and Remote Support Features
BeyondTrust Remote Support and Privileged Remote Access solutions work hand-in-hand to secure remote access points within the enterprise, including employees, vendors, third-parties, and more.
What is a client SSL forward proxy?
Creating a Client SSL forward proxy profile makes it possible for client and server authentication, while still allowing the BIG-IP system to perform data optimization, such as decryption and encryption. This profile applies to client-side SSL forward proxy traffic only.
What is SWG proxy?
You can configure Secure Web Gateway (SWG) explicit forward proxy and network access configurations so that SWG processes the Internet traffic from a network access client in the same way that it processes such traffic from a client in the enterprise.
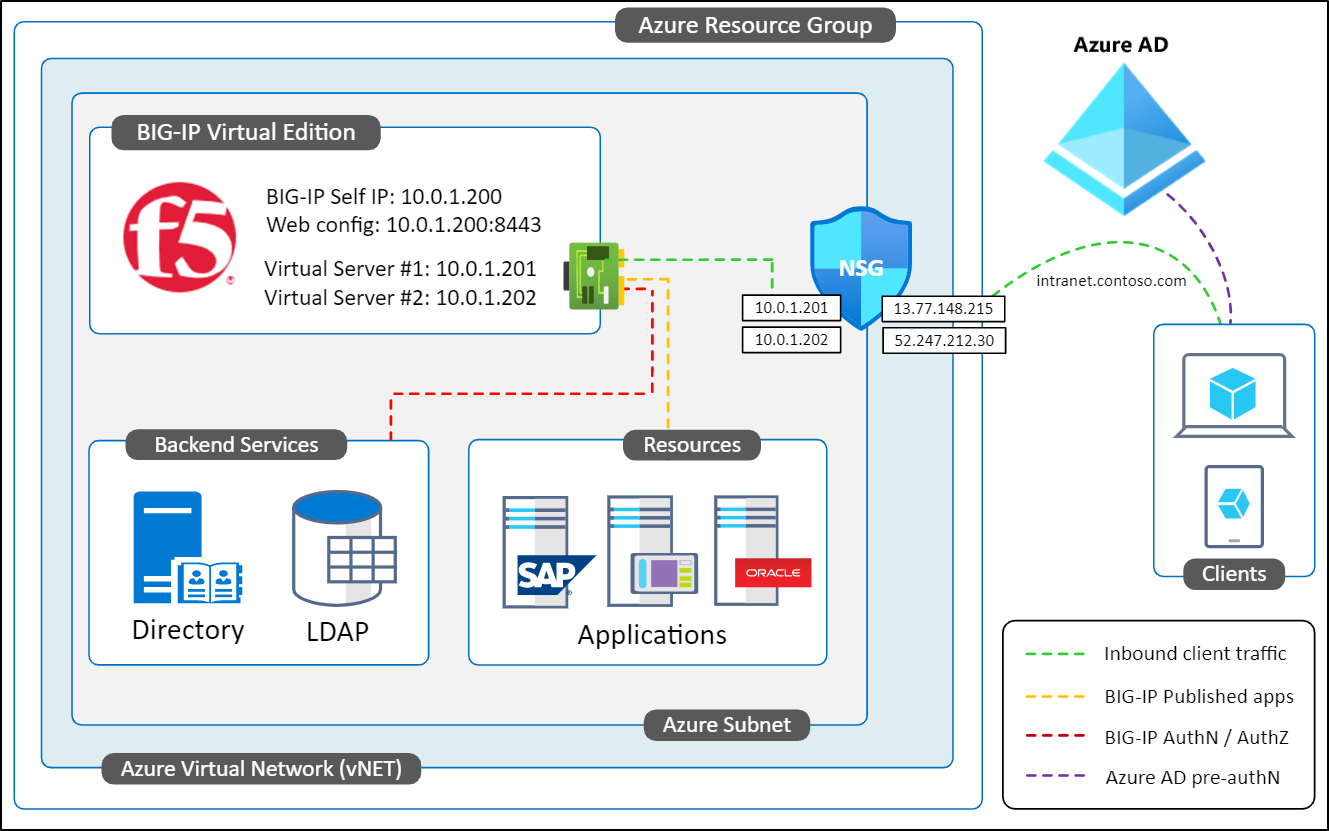
Scenario Description
User Experience
- Whether a direct employee, affiliate, or consumer, most users are already acquainted with the Office 365 login experience, so accessing BIG-IP services via SHA remains largely familiar. Users now find their BIG-IP published services consolidated in the Microsoft MyApps portal or O365 launchpadsalong with self-service capabilities to a broader set of services, no matter the type o…
Insights and Analytics
- A BIG-IP’s role is critical to any business, so deployed BIG-IP instances can be monitored to ensure published services are highly available, both at an SHA level and operationally too. Several options exist for logging events either locally, or remotely through a Security Information and Event Management (SIEM) solution, enabling off-box storage and processing of telemetry. A hig…
Prerequisites
- Integrating an F5 BIG-IP with Azure AD for SHA has the following pre-requisites: 1. An F5 BIG-IP instance running on either of the following platforms: 1.1. Physical appliance 1.2. Hypervisor Virtual Edition such as Microsoft Hyper-V, VMware ESXi, Linux KVM, and Citrix Hypervisor 1.3. Cloud Virtual Edition such as Azure, VMware, KVM, Community Xen,...
Configuration Scenarios
- Configuring a BIG-IP for SHA is achieved using any of the many available methods, including several template based options, or a manual configuration.The following tutorials provide detailed guidance on implementing some of the more common patterns for BIG-IP and Azure AD secure hybrid access. Advanced configuration The advanced approach provides a more elaborate, yet fl…
Azure Ad B2B Guest Access
- Azure AD B2B guest access to SHA protected applications is also possible, but some scenarios may require some additional steps not covered in the tutorials. One example is Kerberos SSO, where a BIG-IP will perform kerberos constrained delegation (KCD) to obtain a service ticket from domain contollers. Without a local representation of a guest user exisiting locally, a domain cont…
Next Steps
- Consider running a SHA Proof of concept (POC) using your existing BIG-IP infrastructure, or by Deploying a BIG-IP Virtual Edition (VE) VM into Azure. Deploying a VM in Azure takes approximately 30 minutes, at which point you'll have: 1. A fully secured platform to model a SHA pilot 2. A pre-production instance for testing new BIG-IP system updates and hotfixes You shoul…
Additional Resources