The main benefits of remote access VPNs are easy setups and hassle-free use. With the right software, this type of VPN can be easily accessible to newcomers and veterans alike, and is ideal for personal use. However, it may be unsuitable for (and even incompatible with) large-scale business needs.
- Secures the Cloud. ...
- Enables Remote Access. ...
- Encrypts Transmitted Data. ...
- Protect cloud environments, staging servers and company databases with total ease.
- Access and Security for BYOD Devices. ...
- International Quality Assurance Testing. ...
- Simple Automatic IP Whitelisting.
How do businesses use remote access VPN?
Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
How do I use a remote access VPN on a NAS?
Today most operating systems ship with built-in software which can connect to a remote access VPN, though some VPN services may require users to install a specific application instead. The client software sets up the tunnelled connection to the NAS and manages the encryption required to keep the connection secure.
What is the difference between a site-to-site VPN and remote access VPN?
A site-to-site VPN and a remote access VPN both offer similar benefits but they actually have different use cases. A site-to-site VPN uses a secure gateway to connect a network at one location to one or more networks at another location.
How secure is remote access to your network?
This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper. Remote users can securely access and use their organization’s network in much the same way as they would if they were physically in the office.
What are the features of VPN?
VPN Security Features: VPN ProtectionEncryption Types. Now we get to the real complicated stuff. ... VPN Protocols. A VPN protocol is like a secret language that the VPN uses to create a connection between its users and the internet. ... VPN Automation Features. ... Kill Switch. ... Leak Protection. ... Malware & Ad Blockers. ... IP Address Options.
What is a function of a remote access VPN?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
What is an important characteristic of remote access VPNs?
The VPN configuration is identical between the remote devices. Internal hosts have no knowledge of the VPN. Information required to establish the VPN must remain static.
What is the most common use of a remote access VPN?
A remote access VPN (virtual private network) is a solution that allows users to connect to a local private network from anywhere in the world. Companies mostly use this type of VPN to provide a way for employees to securely connect to their network from remote locations when working from home or traveling.
What are the benefits of having a VPN?
Pros of VPN: What are the advantages of using a VPN?Secure Your Network. The benefits of using a VPN are vast. ... Hide Your Private Information. ... Prevent Data Throttling. ... Avoid Bandwidth Throttling. ... Get Access to Geo-blocked Services. ... Network Scalability. ... Reduce Support Costs.
What is the difference between remote access and a VPN?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
What are the two VPN components?
Tunneling protocols There are two protocols that are used to manage tunnels and encapsulate private data: Point-to-Point Tunneling Protocol (PPTP), and Layer Two Transport Protocol (L2TP).
What feature allows remote access VPN users to access resources across a site to site VPN tunnel?
A VPN gives authenticated remote users and sites secured access to an organization's network and resources. A group of computers and networks connected to a VPN tunnel by one VPN gateway that handles encryption and protects the VPN Domain members. A named collection of VPN domains, each protected by a VPN gateway.
What are the different VPN types?
The four main types of VPN are:Remote access VPNs.Personal VPN services.Mobile VPNs.Site-to-site VPNs.
What are the advantages and disadvantages of VPN?
While not always ideal, the use of a VPN is often the most affordable and secure way to protect oneself online. VPN Disadvantages. Specific activities that require high bandwidth, such as gaming, might not be able to function using a VPN, but they are easily enabled and disabled.
What are the three types of VPNs?
The Three Main Types of VPNs VPNs can be divided into three main categories – remote access, intranet-based site-to-site, and extranet-based site-to-site. Individual users are most likely to encounter remote access VPNs, whereas big businesses often implement site-to-site VPNs for corporate purposes.
What is the main purpose of a RAS server?
A remote access server (RAS) is a type of server that provides a suite of services to remotely connected users over a network or the Internet. It operates as a remote gateway or central server that connects remote users with an organization's internal local area network (LAN).
What do you need for remote access?
Remote computer access requires a reliable internet connection. You'll need to activate or install software on the device you want to access, as well as on the device — or devices — you want to use to get that access.
Does VPN allow you to access a computer remotely?
While having some similarities, VPN and remote desktop are functionally different things. A VPN will give you access to a network while remote desktop (or RDP) will give you control of an entire computer. If you want to have full control over a local computer from a remote location, VPN won't let you achieve that.
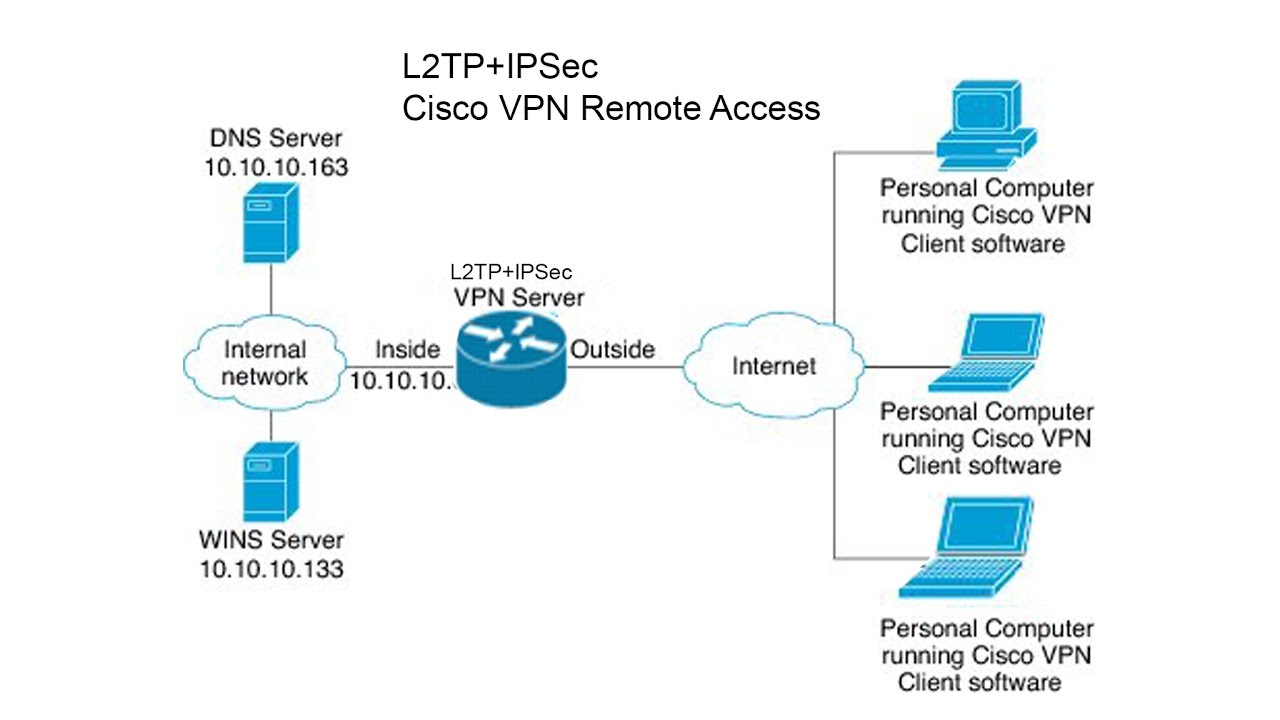
What is remote access VPN Cisco?
This allows remote users to connect to the ASA and access the remote network through an IPsec encrypted tunnel. The remote user requires the Cisco VPN client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network.
What is remote access VPN?
A remote access VPN has to guarantee confidentiality, integrity and availability of information and systems. NCP's remote access VPN solution guarantees this security. It sustainably protects your end devices and communication mediums from attacks by using seamlessly interacting security mechanisms. Security levels are not static but constantly changing. To meet those changing but current threats in time, all security features have to be upgraded to cutting edge technology. NCP's software components are inexpensive due to low cost updates or upgrades.
What is an APN?
The APN (Access Point Name) defines the access point of a mobile data connection at a provider. If the user changes provider, the system automatically takes APN data from the corresponding SIM card and uses it in client configuration. Through that, it is easy to use inexpensive, local providers abroad.
What port does NCP use?
This feature allows for remote access behind firewalls whose settings prevent IPsec based data traffic (Port 500 or UDP encapsulation not possible). With the help of the VPN Path Finder technology, the NCP Secure Client can use Port 443 of the firewall (Fallback IPsec / HTTPS). This allows for a holistic IPsec-based implementation of the security policy (prerequisite: NCP VPN gateway, starting with v 8.0, at the corporate headquarters).
What is seamless roaming?
You can call "seamless roaming" the logical advancement from "WiFi roaming". With "Seamless Roaming" the devices are able to automatically change between various networks, for example between LAN, WiFi and 3/4G. This further facilitates mobile computing and enables the state "always on" - meaning continuous and constant availability of applications of the mobile telework station. The client is able to automatically change the communication medium during a session and to dynamically redirect the VPN tunnel, while the user does not even notice this process.
What happens when a teleworker moves within the reception area of several access points using the same SSID?
If a teleworker moves within the reception area of several access points using the same SSID, the system automatically chooses the strongest access point available. Applications which communicate via a tunnel do not even "notice" this access point roaming.
Is remote access VPN good?
A remote access VPN solution is only as good as the sum of its components' (client and server) features. This, however, does not only include a simple evaluation of technical aspects.
What is site to site VPN?
Site-to-Site VPN- also referred to as “branch office VPN”, this encrypted connection is between a main corporate network or headquarters and remote branch office networks. The VPN tunnel is established between two VPN network devices, such as VPN routers. This setup is most relevant for organizations that need to securely connect entire office ...
What is VPN solution?
What are Virtual Private Network (VPN) Solutions? A virtual private network (VPN) is a service that securely connects an end user directly to a remote private network and its assets. The VPN hides the end user's IP address providing anonymity and privacy.
How to compare VPNs?
When comparing different virtual private networks, consider these factors: 1 Reliability: Consider how reliable each VPN is, especially at scale. For example, will the VPN impact your traffic or connectivity? VPNs, if not properly deployed/managed, can interfere with permissions set in other systems. Some may also restrict bandwidth or throttle traffic speeds given the lagtime to encrypt/decrypt traffic within a VPN and resourcing to send data across the network itself. 2 Data Privacy: Some vendors retain the right to sell user data to third parties. For sensitive or personal data transmission, ensure that each vendor does not sell users’ data.
What is VPN software?
Virtual Private Network software’s core definition is a service that provides an encrypted tunnel between a main network and an “end user.” There are a variety of VPN setups and protocols, VPNs most commonly work in one of two ways:
How much does a VPN cost?
Standalone pricing is usually per device per month, with a floor around $5-10 per device.
Why is VPN important?
The main benefit to organizations is the ability to securely send data from endpoint to endpoint since the encrypted data can only be decrypted by the recipient on the VPN.
What is secure remote connection?
Secure remote connections to, or transfers of, data, communications, etc, such as remote workers using sensitive company data
What is remote access VPN?
What Is a Remote Access VPN? A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive. The remote access VPN does this by creating a tunnel between an ...
Why is VPN remote access?
The remote access VPN does this by creating a tunnel between an organization’s network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
What are the advantages of using a SASE?
Some advantages of using a SASE are that it allows companies to: Apply security policies consistently across multiple locations and enforce least-privileged access. Simplify IT infrastructure and reduce costs by using a single cloud-based solution instead of having to buy and manage multiple point products.
Does SASE require a VPN?
Using SASE, an organization does not have to maintain a separate stand-alone proxy or VPN. Rather, users connect to a SASE solution (which provides access to the cloud and data center) with consistent security. Some advantages of using a SASE are that it allows companies to:
Additional layer of authentication
Accessing organizational resources through remote access -- particularly through devices that aren't controlled by the organization (e.g., BYOD devices, partner devices) -- generally increases the risk for an organization when compared to accessing the same resources from an internal organization network.
Security health checks
SSL VPN products typically offer the ability to do security health checks on each device before granting remote access to organizational resources. These health checks can involve a wide variety of security characteristics.
Centralized access control
Another beneficial feature of SSL VPN products is that they provide centralized access control for a variety of organizational resources.
Benefits of SSL VPN products
SSL VPN products are able to protect the confidentiality and integrity of network communications for remote access users, but they are able to do much more than that. Supported on desktops, laptops, smartphones and tablets, SSL VPNs typically provide an additional layer of authentication, enabling multifactor authentication for remote access users.
What Are Virtual Private Network (Vpn) Solutions?
Types of Virtual Private Networks
- Virtual Private Network software’s core definition is a service that provides an encrypted tunnel between a main network and an “end user.” There are a variety of VPN setups and protocols, VPNs most commonly work in one of two ways: 1. Remote Access VPN- a remote access VPN is an encrypted tunnel between an individual using a device, such as a lapt...
Free VPNs
- There are a number of theoretically “free” VPN products available. These are usually targeted towards small scale or personal use. However, these VPNs are able to sell the data that users send over the VPN. Free options will also offer less reliability and bandwidth, and they will likely have fewer global server options. B2B users, especially businesses with more than a few employ…
Vpn Comparison
- When comparing different virtual private networks, consider these factors: 1. Reliability:Consider how reliable each VPN is, especially at scale. For example, will the VPN impact your traffic or connectivity? VPNs, if not properly deployed/managed, can interfere with permissions set in other systems. Some may also restrict bandwidth or throttle traffic speeds given the lagtime to encryp…
Pricing Information
- VPN pricing can vary depending on whether vendors offer it as a standalone product or part of a broader security package, like a firewall product. Standalone pricing is usually per device per month, with a floor around $5-10 per device. There are some free virtual private network products available for very small businesses. However, free VPNs are primarily designed for individual us…