The compliance of Secure Remote Access (both Remote Support and Privileged Remote Access) with FIPS 140-2 is ensured by the use of exclusively FIPS 140-2 compliant, third-party cryptographic algorithms, and using the algorithms as the only providers of cryptographic services as applicable for product operation.
What is FIPS-compliant secure remote Linux development?
FIPS-compliant secure remote Linux development is available in Visual Studio 2019 version 16.5 and later. Federal Information Processing Standard (FIPS) Publication 140-2 is a U.S. government standard for cryptographic modules. Implementations of the standard are validated by NIST.
How do I enable FIPS compliance on my Network?
Click the “Security” tab in the network properties window. Click the “Advanced settings” button. Toggle the “Enable Federal Information Processing Standards (FIPS) compliance for this network” option under 802.11 settings.
What is the difference between FIPS compliant and FIPS validated?
On the other hand, FIPS compliant means that some, but not all of the product, has been FIPS validated. Therefore, you can have products on the market that might have some third-party FIPS validated software and components, but the entire product is itself not FIPS validated.
What host key algorithms are FIPS compliant?
ssh-rsa is the only FIPS compliant host key algorithm VS supports. The aes*-ctr algorithms are also FIPS compliant, but the implementation in Visual Studio isn't approved.
What IT means to be FIPS compliant?
To be FIPS compliant means an organization adheres to the Federal Information Processing Standards (FIPS) in order to act in accordance with the Federal Information Security Management Act of 2002 (FISMA) and the Federal Information Security Modernization Act of 2014 (FISMA2014).
Is bomgar FIPS compliant?
Bomgar has received the National Institute of Standards and Technology's (NIST) FIPS 140-2 Level 2 validation for its B200 and B300 appliances and version 13.1.
How do I SSH with FIPS enabled?
Prepare a FIPS-compliant connectionOn the Linux system, install and start the OpenSSH server: ... If you'd like the ssh server to start automatically when the system boots, enable it using systemctl : ... Open /etc/ssh/sshd_config as root.More items...•
Is BeyondTrust FIPS compliant?
BeyondTrust is the only Secure Remote Access provider that meets the rigorous requirements of Federal Information Processing Standard Publication (FIPS) 140-2 Level 1 validation.
Is OpenSSH FIPS compliant?
The openssh implementation of Secure Shell is a consumer of the OpenSSL FIPS 140-2 module. If your system must comply with FIPS 140-2 requirements, you need to configure and use the FIPS 140-2 options. OpenSSH in Oracle Solaris sets FIPS 140-2 mode dynamically.
How do I turn off FIPS mode?
Log in to Administration Console. Click Settings > Core System Settings > Configurations. Select Enable FIPS to enable FIPS mode or deselect it to disable FIPS mode. Click OK and restart the application server.
What is FIPS mode Linux?
fips - Run Linux in FIPS mode In Federal Information Processing Standard (FIPS) mode, the kernel enforces FIPS 140-2 security standards. For example, in FIPS mode only FIPS 140-2 approved encryption algorithms can be used. Note: Enabling FIPS mode is not sufficient to make your kernel certified according to FIPS 140-2.
Is Splashtop FIPS compliant?
Splashtop uses the FIPS validated/certified OpenSSL module, which is the unmodified certified source code, for this configuration to be FIPS compliant.
Who owns Dameware?
SolarWinds IncThe Austin software maker reported a second-quarter profit of $19.4 million on $64 million in revenue compared to a profit of $13 million on $45.8 million revenue during the same three months last year. A division of software maker SolarWinds Inc.
What is FIPS modules Dameware?
FIPS (Federal Information Processing Standards) are a set of standards that describe document processing, encryption algorithms and other information technology standards for use within non-military government agencies and by government contractors and vendors who work with the agencies.
How secure is bomgar?
Bomgar is still the most secure remote support software in the world. Now called BeyondTrust Remote Support, it's trusted by more customers than ever before. Sign-up for a free trial.
Does Bomgar use RDP?
This competitive document details the key advantages Bomgar provides over Windows' built-in remote access tools, including the ability to run RDP sessions securely through the Bomgar Box.
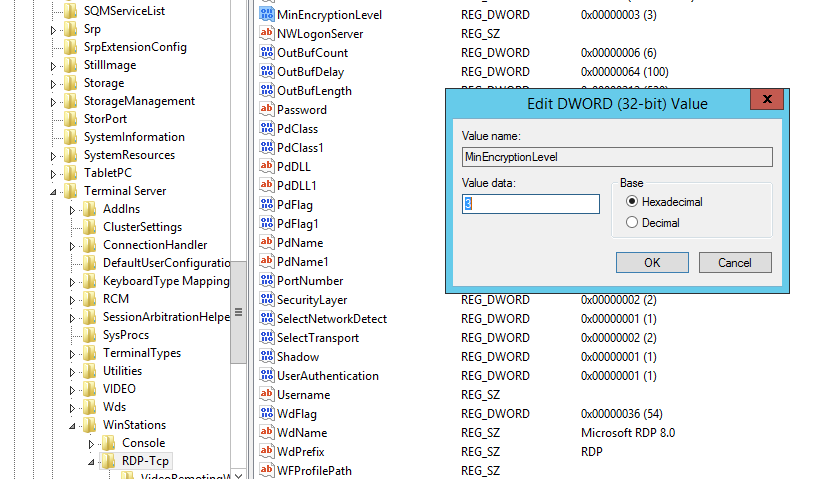
How to enable FIPS mode?
Optional: Enable or disable FIPS mode 1 To enable FIPS mode, press Windows+R to open the Run dialog, and then run gpedit.msc. 2 Expand Local Computer Policy > Computer Configuration > Windows Settings > Security Settings > Local Policies and select Security Options. 3 Under Policy, select System cryptography: Use FIPS-compliant algorithms for encryption, hashing, and signing, and then press Enter to open its dialog box. 4 In the Local Security Setting tab, select Enabled or Disabled, and then choose OK to save your changes.
What is FIPS 140-2?
Federal Information Processing Standard (FIPS) Publication 140-2 is a U.S. government standard for cryptographic modules. Implementations of the standard are validated by NIST. Windows has validated support for FIPS-compliant cryptographic modules. In Visual Studio 2019 version 16.5 and later, you can use a secure, ...
Can you configure ssh to use additional ciphers?
You're not limited to these options. You can configure ssh to use additional ciphers, host key algorithms, and so on. Some other relevant security options you may want to consider are PermitRootLogin, PasswordAuthentication, and PermitEmptyPasswords. For more information, see the man page for sshd_config or the article SSH Server Configuration.
Is ssh-rsa FIPS compliant?
ssh-rsa is the only FIPS compliant host key algorithm VS supports. The aes*-ctr algorithms are also FIPS compliant, but the implementation in Visual Studio isn't approved. The ecdh-* key exchange algorithms are FIPS compliant, but Visual Studio doesn't support them.
FIPS Certification Information and Resources
Learn more about the FIPS security standards for cryptographic modules.
What does FIPS Certification Mean?
A 6-9 month process, claims must be tested by a NIST accredited independent laboratory.
Is FIPS Compliant the same as FIPS Certified?
IT security solutions that are marketed as being FIPS compliant are making a claim that the product meets FIPS requirements. However, this is very different than if a NIST-approved laboratory validates that the product meets FIPS requirements.
What is Cisco FIPS?
Cisco FIPS-compliant VPN clients comply with Level 1 of the Federal Information Processing Standard (FIPS) 140-2, a U.S. government standard for specific security requirements for cryptographic modules. The FIPS 140-2 standard applies to all federal agencies that use cryptographic-based security systems to protect sensitive information in computer and telecommunication systems.
Does VPN license affect concurrent sessions?
The license does not affect the number of allowed concurrent VPN sessions. The following table shows the Product numbers (also called SKUs) of the licenses for each security appliance model: Note Each new security appliance model purchased after August 31st, 2009 requires a FIPS-compliant VPN client license.
Open source tools for controls, risk exception libraries and policy reviews, approvals and version management of all of the above
Looking for advice on alternatives to RSA archer or RSAM for any of you familiar with these compliance tools that help store controls and other daily metadata around policy reviews, annual policy scheduled reviews, exceptions, architecture reviews, etc. Hope I made sense here.
Am I wasting my time?
Most techy guy in a <10 employee manufacturer. Put in charge of becoming NIST 800-171 compliant. I've been doing my homework, identifying tools we would need, thinking about alternatives of how to become complaint, hardware research, software research, reading through documentation, etc etc. I'm not a cyber security expert, not even close.
Sub using Prime Contractor Assets for Self Assessment
If you are a sub contractor using a prime contractors laptop for contract support, how does the sub report their self assessment? Technically all contract work is being done on a complaint prime contract system and network.
800-53 Guidance
I'm just being introduced to the wonderful world that is security frameworks and compliance and feel quite overwhelmed and would like if someone could "point" me into the right direction. What i'm attempting to accomplish is something "minor" but slowly give me more experience.
SSP Nist 800-171
Hi guys I am writing an SSP for a windows domain environment to meet the NIST 800-171 110 controls
How to enable FIPS?
On Home versions of Windows, you can still enable or disable the FIPS setting via a registry setting. To check whether FIPS is enabled or disabled in the registry, follow the following steps: 1 Press Windows Key+R to open the Run dialog. 2 Type “regedit” into the Run dialog box (without the quotes) and press Enter. 3 Navigate to “HKEY_LOCAL_MACHINESystemCurrentControlSetControlLsaFipsAlgorithmPolicy”. 4 Look at the “Enabled” value in the right pane. If it’s set to “0”, FIPS mode is disabled. If it’s set to “1”, FIPS mode is enabled. To change the setting, double-click the “Enabled” value and set it to either “0” or “1”. 5 Restart the computer.
How to enable FIPS on a network?
Right-click the network you want to enable FIPS for and select “Status.”. Click the “Wireless Properties” button in the Wi-Fi Status window. Click the “Security” tab in the network properties window. Click the “Advanced settings” button. Toggle the “Enable Federal Information Processing Standards ...
What Is FIPS-compliant Encryption?
FIPS stands for “Federal Information Processing Standards.” It’s a set of government standards that define how certain things are used in the government–for example, encryption algorithm s. FIPS defines certain specific encryption methods that can be used, as well as methods for generating encryption keys. It’s published by the National Institute of Standards and Technology, or NIST.
Does.NET have FIPS?
Microsoft’s .NET framework will also block access to algorithms that aren’t FIPS-validated. The .NET framework offers several different algorithms for most cryptography algorithms, and not all of them have even been submitted for validation. As an example, Microsoft notes that there are three different versions of the SHA256 hashing algorithm in the .NET framework. The fastest one hasn’t been submitted for validation, but should be just as secure. So enabling FIPS mode will either break .NET applications that use the more efficient algorithm or force them to use the less efficient algorithm and be slower.
Does Microsoft recommend FIPS mode?
Microsoft only recommends you use FIPS mode if you have to. For example, if you’re using a US government computer, that computer is supposed to have “FIPS mode” enabled according to the government’s own regulations.
Does FIPS mode force anything else?
Aside from those two things, enabling FIPS mode recommends to applications that they use only FIPS-validated encryption, too. But it doesn’t force anything else. Traditional Windows desktop applications can choose to implement any encryption code they want–even horrifically vulnerable encryption–or no encryption at all. FIPS mode doesn’t do anything to other applications unless they obey this setting.
Does Windows use FIPS?
This setting does two things to Windows itself. It forces Windows and Windows services to use only FIPS-validated cryptography. For example, the Schannel service built into Windows won’t work with older SSL 2.0 and 3.0 protocols, and will require at least TLS 1.0 instead.
Why does Eaglesoft tell their practices to reboot their servers everyday?
Can someone explain to me why most of their offices told us that they need to reboot their servers everyday? This ended up causing syncing issues for a couple of the softwares it would integrate with.
When will HP stop allowing non authorized partners to buy?
So apparently HP is no longer allowing non Authorized Partners to buy ANY of their SKU's through Distribution as of July 2021?

Cisco Fips-Compliant Vpn Clients
- Cisco provides an end-to-end remote access security solution for our customers that require FIPS compliance. Our FIPS-compliant VPN clients and the FIPS-certified ASA 5500 Series Adaptive Security Appliance allow organizations to establish end-to-end, encrypted VPN tunnels for secure connectivity for mobile employees and telecommuters. The FIPS-com...
Information About FIPS
- Cisco FIPS-compliant VPN clients comply with Level 1 of the Federal Information Processing Standard (FIPS) 140-2, a U.S. government standard for specific security requirements for cryptographic modules. The FIPS 140-2 standard applies to all federal agencies that use cryptographic-based security systems to protect sensitive information in computer and telecom…
New Features For The Fips-Compliant Vpn Client
- The FIPS-compliant VPN client (IPsec) is a separate release of the client. The following are some of the new features added since the last release of the FIPS-compliant VPN client, Release 3.6.3: •A redesigned user interface for greater usability. •Windows Vista support. •Windows Vista Smartcard support. •A new virtual adapter improves performance of application requiring the cli…
Licensing Requirements For The Fips-Compliant Vpn Client
- The Cisco FIPS-compliant VPN clients are licensed based on the ASA 5500 Series Adaptive Security Appliance model. Each security appliance model requires a different license. The license does not affect the number of allowed concurrent VPN sessions. The following table shows the Product numbers (also called SKUs) of the licenses for each security appliance model: Note Eac…
Where to Go For Additional Information
- For more information about Cisco FIPS-compliant VPN clients, see the following documents: Release Notes for Cisco VPN Client, FIPS-Compliant Release 5.0.5-FIPS: http://www.cisco.com/en/US/docs/security/vpn_client/fips/release/notes/FIPS_51client.html Release Notes for Cisco VPN Client, Release 5.0.00 and Release 5.0.01: http://www.cisco.com/e…