How do I set up AnyConnect with firepower threat defense?
Download AnyConnect if it is not installed already and connect to the VPN. The AnyConnect client installs itself. On successful authentication, you will be connected to the Firepower Threat Defense remote access VPN gateway. The applicable identity or QoS policy is enforced according to your remote access VPN policy configuration.
Why can't I move a firepower threat defense device to another domain?
Moving a Firepower Threat Defense device from one domain to another domain is not possible if a remote access VPN policy is assigned to that device. Firepower 9300 and 4100 series in cluster mode do not support remote access VPN configuration. Remote access VPN connectivity could fail if there is an FTD NAT rule is misconfigured.
What version of firepower threat defense (FTD) does Ra VPN support?
Remote Access VPN (RA VPN) is available in Firepower Threat Defense (FTD) 6.2.1 for 2100 Platforms. For all other Platforms it will be supported on version 6.2.2. RA VPN Client software is AnyConnect 4.x available for Windows, Mac, Linux, Andorid and iOS.
How do I set up a VPN on firepower Management Center?
On your Firepower Management Center web interface, choose Devices > VPN > Remote Access. Existing remote access policies are listed. Select a remote access VPN policy and click Edit . Click Add and specify the following in the Add Connection Profile window: Connection Profile —Provide a name that the remote users will use for VPN connections.
Does Cisco FTD support VPN?
VPN Topology The Firepower Management Center configures site-to-site VPNs on FTD devices only. You can select from three types of topologies, containing one or more VPN tunnels: • Point-to-point (PTP) deployments establish a VPN tunnel between two endpoints.
Does Cisco firepower support route based VPN?
In November 2020 Cisco released the Firepower Threat Defence (FTD) and Firepower Management Centre (FMC) version 6.7. Supported from this version is the long-awaited Virtual Tunnel Interface (VTI) for route-based site-to-site VPNs.
What is Cisco remote access VPN?
This allows remote users to connect to the ASA and access the remote network through an IPsec encrypted tunnel. The remote user requires the Cisco VPN client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network.
How can I check Cisco firepower VPN status?
The simplest place to check the status of your VPN is in FMC. Browse to System -> Health -> Events. Then click on VPN Status. The remaining verification takes place on the FTD CLI.
What is the difference between policy based VPN and route-based VPN?
In a policy-based VPN configuration, the action must be permit and must include a tunnel. Route-based VPNs support the exchange of dynamic routing information through VPN tunnels. You can enable an instance of a dynamic routing protocol, such as OSPF, on an st0 interface that is bound to a VPN tunnel.
What is route-based VPN?
A route-based VPN is a configuration in which an IPsec VPN tunnel created between two end points is referenced by a route that determines which traffic is sent through the tunnel based on a destination IP address.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
Is Cisco AnyConnect SSL or IPsec?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
How do I check my FTD VPN tunnel?
In order to monitor the tunnel status, navigate to the CLI of the FTD or ASA. From the FTD CLI, verify phase-1 and phase-2 with the command show crypto ikev2 sa. This section provides information you can use in order to troubleshoot your configuration.
What is FMC in Cisco?
Cisco Secure Firewall Management Center (formerly Firepower Management Center) Data Sheet - Cisco.
Does Palo Alto support policy-based VPN?
Palo Alto Network firewalls do not support policy-based VPNs. The policy-based VPNs have specific security rules/policies or access-lists (source addresses, destination addresses and ports) configured for permitting the interesting traffic through IPSec tunnels.
What VPN types are supported by ASA?
For VPN Services, the ASA 5500 Series provides a complete remote-access VPN solution that supports numerous connectivity options, including Cisco VPN Client for IP Security (IPSec), Cisco Clientless SSL VPN, network-aware site-to-site VPN connectivity, and Cisco AnyConnect VPN client.
Does FTD support VTI?
VTI is not supported on an FTD Cluster.
How do I check my IPSec tunnel status in FTD?
In order to monitor the tunnel status, navigate to the CLI of the FTD or ASA. From the FTD CLI, verify phase-1 and phase-2 with the command show crypto ikev2 sa. This section provides information you can use in order to troubleshoot your configuration.
What is Firepower Threat Defense?
The Firepower Threat Defense device supports applying user authorization attributes (also called user entitlements or permissions) to VPN connections from the external RADIUS server that are configured for authentication and/or authorization in the remote access VPN policy.
What is remote access VPN?
Remote Access VPN policy contains the connection profiles targeted for specific devices. These policies pertain to creating the tunnel itself, such as, how AAA is accomplished, and how addresses are assigned (DHCP or Address Pools) to VPN clients. They also include user attributes, which are identified in group policies configured on the Firepower Threat Defense device or obtained from a AAA server. A device also provides a default connection profile named DefaultWEBVPNGroup. The connection profile that is configured using the wizard appears in the list.
What is AnyConnect profile?
An AnyConnect client profile is a group of configuration parameters stored in an XML file that the client uses to configure its operation and appearance. These parameters (XML tags) include the names and addresses of host computers and settings to enable more client features.
What is Cisco AnyConnect Secure Mobility?
The Cisco AnyConnect Secure Mobility client provides secure SSL or IPsec (IKEv2) connections to the Firepower Threat Defense device for remote users with full VPN profiling to corporate resources. Without a previously-installed client, remote users can enter the IP address of an interface configured to accept clientless VPN connections in their browser to download and install the AnyConnect client. The Firepower Threat Defense device downloads the client that matches the operating system of the remote computer. After downloading, the client installs and establishes a secure connection. In case of a previously installed client, when the user authenticates, the Firepower Threat Defense device, examines the version of the client, and upgrades the client if necessary.
What is the only VPN client?
The only supported VPN client is the Cisco AnyConnect Secure Mobility Client. No other clients or native VPNs are supported. Clientless VPN is not supported for VPN connectivity; it is only used to deploy the AnyConnect client using a web browser.
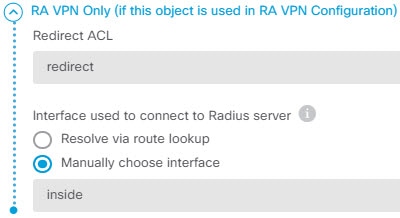
How many interfaces can be configured in a security zone?
Only one interface can be configured in the security zone or interface group if it is referred in a RADIUS Server.
Can Firepower Threat Defense resolve IP addresses?
Without DNS, the devices cannot resolve AAA server names, named URLs, and CA Servers with FQDN or Hostnames. It can only resolve IP addresses.
How to change VPN settings on Firepower?
On the Firepower Management Center web interface, choose Devices > VPN > Remote Access, choose and edit a listed RA VPN policy, then choose the Advanced tab.
What is the rule for remote access VPN?
Before deploying the remote access VPN policy, you must update the access control policy on the targeted Firepower Threat Defense device with a rule that allows VPN traffic. The rule must allow all traffic coming in from the outside interface , with source as the defined VPN pool networks and destination as the corporate network.
What is AnyConnect profile?
An AnyConnect client profile is a group of configuration parameters stored in an XML file that the client uses to configure its operation and appearance. These parameters (XML tags) include the names and addresses of host computers and settings to enable more client features.
What is Cisco AnyConnect Secure Mobility?
The Cisco AnyConnect Secure Mobility client provides secure SSL or IPsec (IKEv2) connections to the Firepower Threat Defense device for remote users with full VPN profiling to corporate resources. Without a previously-installed client, remote users can enter the IP address of an interface configured to accept clientless VPN connections in their browser to download and install the AnyConnect client. The Firepower Threat Defense device downloads the client that matches the operating system of the remote computer. After downloading, the client installs and establishes a secure connection. In case of a previously installed client, when the user authenticates, the Firepower Threat Defense device, examines the version of the client, and upgrades the client if necessary.
How to upload Cisco AnyConnect client image?
You can upload the Cisco AnyConnect Mobility client image to the Firepower Management Center by using the AnyConnect File object. For more information, see FTD File Objects. For more information about the client image, see Cisco AnyConnect Secure Mobility Client Image .
What is the only VPN client?
The only supported VPN client is the Cisco AnyConnect Secure Mobility Client. No other clients or native VPNs are supported. Clientless VPN is not supported for VPN connectivity; it is only used to deploy the AnyConnect client using a web browser.
How to add IPv4 to address pool?
Select the Add icon in the Address Pools window to add a new IPv4 or IPv6 address pool. When you choose the IPv4 pool, provide a starting and ending IP address. When you choose to include a new IPv6 address pool, enter Number of Addresses in the range 1-16384. Select the Allow Overrides option to avoid conflicts with IP address when objects are shared across many devices. For more information, see Address Pools .
What is a hub and spoke VPN?
In a Hub and Spoke VPN topology, a central endpoint (hub node) connects with multiple remote endpoints (spoke nodes). Each connection between the hub node and an individual spoke endpoint is a separate VPN tunnel. The hosts behind any of the spoke nodes can communicate with each other through the hub node.
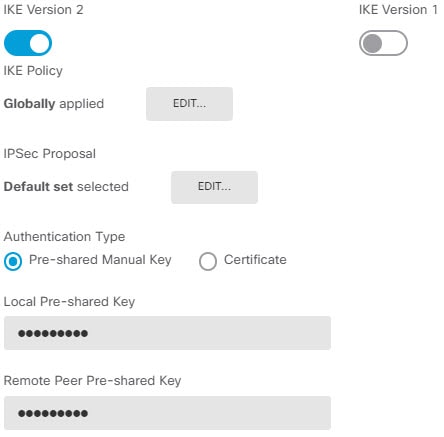
How Secure Should a VPN Connection Be?
Because a VPN tunnel typically traverses a public network, most likely the Internet, you need to encrypt the connection to protect the traffic. You define the encryption and other security techniques to apply using IKE polices and IPsec proposals.
What is a trustpoint CA?
Once enrollment is complete, a trustpoint is created on the managed device. It is the object representation of a CA and associated certificates. A trustpoint includes the identity of the CA, CA-specific parameters, and an association with a single enrolled identity certificate.
What is a CA in VPN?
When you use Digital Certificates as the authentication method for VPN connections, peers are configured to obtain digital certificates from a Certificate Authority (CA). CAs are trusted authorities that “sign” certificates to verify their authenticity, thereby guaranteeing the identity of the device or user.
How does a VPN work point to point?
In a point-to-point VPN topology, two endpoints communicate directly with each other. You configure the two endpoints as peer devices, and either device can start the secured connection.
Why use PKI in VPN?
Using a PKI improves the manageability and scalability of your VPN since you do not have to configure pre-shared keys between all the encrypting devices. Instead, you individually enroll each participating device with a CA server, which is explicitly trusted to validate identities and create an identity certificate for the device. When this has been accomplished, each participating peer sends their identity certificate to the other peer to validate their identities and establish encrypted sessions with the public keys contained in the certificates. See Certificate Enrollment Objects for details on enrolling FTD devices.
Can FTD devices pass through access control?
On a FTD device, by default no traffic is allowed to pass through access-control without explicit permission. VPN tunnel traffic as well, is not relayed to the endpoints until it has passed through Snort. Incoming tunnel packets are decrypted before being sent to the Snort process. Snort processes outgoing packets before encryption.
How to create an IP pool in Firepower?
Also, you can create an IP pool in Firepower Management Center using the Objects > Object Management > Address Pools path. For more information, see Address Pools .
When a local realm is created and local users are added, can you add it to a remote access VPN to?
When a local realm is created and local users are added, you can add it to a remote access VPN to enable local user authentication.
What is AnyConnect profile?
An AnyConnect client profile is a group of configuration parameters stored in an XML file that the client uses to configure its operation and appearance. These parameters (XML tags) include the names and addresses of host computers and settings to enable more client features.
What is Cisco AnyConnect Secure Mobility?
The Cisco AnyConnect Secure Mobility client provides secure SSL or IPsec (IKEv2) connections to the Firepower Threat Defense device for remote users with full VPN profiling to corporate resources. Without a previously-installed client, remote users can enter the IP address of an interface configured to accept clientless VPN connections in their browser to download and install the AnyConnect client. The Firepower Threat Defense device downloads the client that matches the operating system of the remote computer. After downloading, the client installs and establishes a secure connection. In case of a previously installed client, when the user authenticates, the Firepower Threat Defense device, examines the version of the client, and upgrades the client if necessary.
What is the only VPN client?
The only supported VPN client is the Cisco AnyConnect Secure Mobility Client. No other clients or native VPNs are supported. Clientless VPN is not supported for VPN connectivity; it is only used to deploy the AnyConnect client using a web browser.
How to check VPN banner?
You can check the banner settings under Group Policy > General Settings> Banner. Edit the connect profile you have created for management VPN tunnel. Click Edit Group Policy> AnyConnect> Management Profile. Click the Management VPN Profiledrop-down and select the management profile file object you have created.
Can Firepower Threat Defense resolve IP addresses?
Without DNS, the devices cannot resolve AAA server names, named URLs, and CA Servers with FQDN or Hostnames. It can only resolve IP addresses.
How to integrate Duo with Cisco FTD?
To integrate Duo with your Cisco FTD SSL VPN, you will need to install a local Duo proxy service on a machine within your network. This Duo proxy server will receive incoming RADIUS requests from your Cisco FTD SSL VPN, contact your existing local LDAP/AD or RADIUS server to perform primary authentication, and then contact Duo's cloud service for secondary authentication.
What port is used for a RADIUS server?
The authentication port on your RADIUS server. Use port_2, port_3, etc. to specify ports for the backup servers.
What is a secret in authentication?
A secret to be shared between the Authentication Proxy and your existing RADIUS server. If you're on Windows and would like to encrypt this secret, see Encrypting Passwords in the full Authentication Proxy documentation.
How to use LDAP as primary authenticator?
To use Active Directory/LDAP as your primary authenticator, add an [ad_client] section to the top of your config file. Add the following properties to the section:
Does Firepower 6.7 have a duo?
The SAML VPN instructions for Firepower 6.7 and later feature inline enrollment and the interactive Duo Prompt for both web-based VPN logins and AnyConnect 4.6+ client logins. This deployment option features Duo Single Sign-On, our cloud-hosted SAML 2.0 identity provider. Primary and Duo secondary authentication occur at the identity provider, not at the ASA itself.