
How to configure remote access policy for FTD devices?
Assign the name of the Remote Access policy and select an FTD device from the Available Devices. 3. Assign the Connection Profile Name (the Connection Profile Name is the tunnel-group name), select Authentication Server and Address Pools as shown in the image. 4. Select the + symbol in order to create Group Policy.
Is there a configuration example for remote access VPN on firepower threat defense?
This document provides a configuration example for remote access VPN on Firepower Threat Defense (FTD) on version 6.3, managed by Firepower Management Center (FMC). Cisco recommends that you have knowledge of these topics:
What is the ASA VPN DDoS vulnerability?
A vulnerability in the remote access SSL VPN features of Cisco Adaptive Security Appliance (ASA) Software and Cisco Firepower Threat Defense (FTD) Software could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition on an affected device.
How do I deploy the remote access VPN config with duo?
Select the FTD device (or devices) to which you want to push the new Remote Access VPN config with Duo. Click the Deploy button. Watch for the deployment to complete with the status "Deployment to device successful". Launch the AnyConnect client and select the VPN profile that now uses Duo RADIUS authentication.
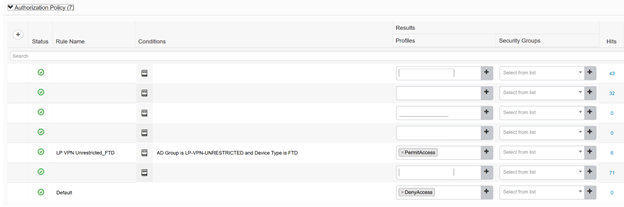
Does FTD support VPN?
VPN Topology The Firepower Management Center configures site-to-site VPNs on FTD devices only. You can select from three types of topologies, containing one or more VPN tunnels: • Point-to-point (PTP) deployments establish a VPN tunnel between two endpoints.
Can we configure FTD without FMC?
Yes correct. CDO relies on the FTD being configured to use local management via FDM. So you can continue to manage the FTD using FDM whether you continue to use CDO or not.
How do I enable syslog on FTD?
Enable a syslog device ID on the FTDs (Data Usage)...The Edit Syslog Configuration dialog box appears.In the Name field, enter a name for the new alert.In the Host field, enter the SecureTrack IP address.In the Facility field, select Syslog.Click Save.
Can I configure FTD from CLI?
With the FTDs being managed by FMC everything is now configured via GUI. There is no longer the option of configuring via CLI like the ASAs. You can still access the CLI but Cisco does not officially support configuration using the CLI.
How do I log into FTD command line?
ProcedureConnect to the FTD CLI, either from the console port or using SSH. You can SSH to the management interface of the FTD device. ... Log in with the admin username and password.At the CLI prompt (>), use any of the commands allowed by your level of command line access.(Optional) Access the diagnostic CLI:
How do I check my FTD logs?
Verify the FTD Syslog configuration in the FTD CLI. Log in to the management interface of the FTD, and enter the system support diagnostic-cli command in order to console into the diagnostic CLI. Ensure that the Syslog server is reachable from the FTD.
What is FTD in network?
+ Follow. Cisco Firepower Threat Defense (FTD) is an integrative software image combining CISCO ASA and FirePOWER feature into one hardware and software inclusive system. Cisco is a pioneer in the Next Generation Firewall Vendors, where competitors are limited to single platforms.
What is FMC in firewall?
Firewall Management Center (FMC) provides comprehensive information about the network users, applications, devices, threats and vulnerabilities and analyze your network constantly. FMC then provides tailored recommendations regarding security policies to implement, plus prioritization of security events to investigate.
What is difference between FTD and FMC?
2:056:23FMC vs FDM - YouTubeYouTubeStart of suggested clipEnd of suggested clipThis FMC can manage FTD five power defence on any of your hardware power platform. And it can manageMoreThis FMC can manage FTD five power defence on any of your hardware power platform. And it can manage FTD virtual form it can manage firepower on running on sound K and eight K series platform.
How do I add FTD to FMC?
Let's jump into this lab!Step 1: Verify the FTD management interface settings. ... Step 2: Add the FMC as the manager. ... Step 3: Log in to the FMC dashboard and go to Devices > Device Management.Step 4: Click on Add > Device.Step 5: Add the FTD device details. ... Step 6: Click Register to start adding the FTD device process.
How do I set up FTD management IP?
I would: Place the HA in maintenance to suspend them up. ( ... delete the manager from the FTD: configure manager delete. remove the device from FMC Devices > Device Management. change the IPs of the FTD: ... Add the manager back on FTD: configure manager add.More items...
How do you manage FTD?
Tips for Coping with FTDAcknowledge and manage your feelings. The FTD journey can be lonely and isolating. ... Don't take it personally. ... FTD isn't well known. ... There's a lot to learn. ... You are not alone. ... Tend to your grieving process. ... Trust yourself. ... Take care of yourself.
How to remote access VPN?
Based on the previous steps, the Remote Access Wizard can be followed accordingly. 1. Navigate to Devices > VPN > Remote Access. 2. Assign the name of the Remote Access policy and select an FTD device from the Available Devices. 3.
How to get a certificate for FTD appliance?
In order to get a certificate for the FTD appliance with the manual enrollment method , a CSR needs to be generated, sign it with a CA and then import the identity certificate.
What extension to save profile name?
Note: Save the profile with an easily identifiable name with a .xml extension.
Does FTD support manual enrollment?
If the CSR is generated in an external server (such as Windows Server or OpenSSL), the manual enrollment method is intended to fail, since FTD does not support manual key enrollment. A different method must be used such as PKCS12.
Is FTD supported by FMC?
On FTD devices managed by FMC, the local user database is not supported, another authentication method must be used, such as RADIUS or LDAP.
Does AnyConnect support RSA?
Certificates are essential when you configure AnyConnect. Only RSA based certificates are supported for SSL and IPSec.
Do you need to create a VPN pool before NAT?
A VPN pool object must be created before the NAT configuration.
The next release will be 6.2
The next release will be 6.2.2. I heard the beta is just wrapping up next week.
6.3.0 was never planned to be
6.3.0 was never planned to be released in Q2 CY17 as far as I know of. Like Marvin pointed out the next major update is 6.2.2 which will bring AnyConnect to all hardware platforms running FTD (not just FP2100). There will be some minor changes but I think it will be mostly bugfixes and AnyConnect.
Hmmmm... You are right -
Hmmmm... You are right - seems like I forgot this roadmap shift. The roadmap got updated a few months ago due to some priority adjustments, thats why 6.3 was pushed back to 2018.
Re: Hmmmm... You are right -
Can we have any updates on the release plan about 6.3 availability and features?
Re: Hmmmm... You are right -
Hi Team Can Cisco ISE help with the below? The proposed solution should be scalable to support more than 1million network-connected devices and manage Layer 2/ Layer 3 devices in non-dot1x mode2.Proposed solution should support uninterrupted, ou... view more
How to add VPN to FMC?
On FMC go to “Devices –> VPN –> Remote Access –> Add a new configuration ”. Assign the new VPN policy to the firewall and then click “Next”. On the next configuration menu you must select your Radius group that you have configured before and the IPv4 Address Pools, like the image below. After that you can click “Next”.
How to add Radius client to NPS?
You need to add a new Radius client on your NPS server, so right-click on “Radius Clients” and select “New”.
How to add a certificate to a FMC?
On FMC go to “Devices –> Certificates” and click on “Add Certificate”. On the tab that will be showed please select the FTD where you want to add the certificate and who is enrolling that certificate. In our guide we are using FMC as internal CA, that it’s a self signed certificate.
Do you need to specify a subnet for VPN?
You need to specify the subnet that will be used from a VPN client. In the field “ IPv4 Address Range” it ’s not necessary to specify a subnet but just a range of IP Address. At the end click the save button.
What is a wizard VPN?
The wizard is really easy to use for the creation of a remote access VPN policy. Just make sure that all requirements are met and the required information is available beforehand.
How many steps are needed for VPN configuration?
Once the wizard is started, five steps are needed for the VPN configuration
Can I use anyconnect for FTD?
Remote Access VPN for FTD is based on the anyconnect images, so it is possible to do IKEv2 and SSL VPN tunnels. In this blog, I’ll only configure the anyconnect SSL features, as this has become my most common deployment configuration.
Is AnyConnect supported by FTD?
Although anyconnect is now supported, not all featurs common to anyconnect on the ASA are available. So there are some requirements, restrictions that need to be followed: Smart Licenses. With FTD, only smart licenses are supported.
Can you use FTD to create remote access?
So yes, the wizard is very easy to create a Remote Access configuration, but FTD is more than just that. There is also a policy that needs to be configured. Of course you could use FlexConfig to setup “sysopt connection permit-vpn” or prefilter “trust” option to bypass all policies for your newly created VPN configuration. But in my opinion with the current cyber security requirements, that is not really a valid option anymore as usually these VPN’s are also used for contractors and external support suppliers for which you do not have control of the connecting endpoint.
Can I use local authentication with FTD?
Local authentication is not possible with FTD , you need to have a PKI, Radius server or AD server available for authentication purposes. This is a thing you really need to keep in mind for those pesky VPN setups used by IT staff in case of emergencies.. Public Access.
Can you use hairpin NAT on FTD?
It is possible to execute hairpin NAT on FTD. Just configure an auto-nat rule (because of troubleshooting, I’ve used a NAT rules after) with a source zone outside to zone outside to perform the PAT.
How to integrate Duo with Cisco FTD?
To integrate Duo with your Cisco FTD SSL VPN, you will need to install a local Duo proxy service on a machine within your network. This Duo proxy server will receive incoming RADIUS requests from your Cisco FTD SSL VPN, contact your existing local LDAP/AD or RADIUS server to perform primary authentication, and then contact Duo's cloud service for secondary authentication.
Where to download authentication proxy for Unix?
Download the most recent Authentication Proxy for Unix from https://dl.duosecurity.com/duoauthproxy-latest-src.tgz. Depending on your download method, the actual filename may reflect the version e.g. duoauthproxy-5.5.0-src.tgz. View checksums for Duo downloads here.
What is Duo MFA?
Duo MFA for Cisco Firepower Threat Defense (FTD) supports push, phone call, or passcode authentication for AnyConnect desktop and AnyConnect mobile client VPN connections that use SSL encryption. This configuration does not feature the interactive Duo Prompt for web-based logins, but does capture client IP information for use with Duo policies, such as geolocation and authorized networks.
What is a secret in authentication?
A secret to be shared between the Authentication Proxy and your existing RADIUS server. If you're on Windows and would like to encrypt this secret, see Encrypting Passwords in the full Authentication Proxy documentation.
How to use LDAP as primary authenticator?
To use Active Directory/LDAP as your primary authenticator, add an [ad_client] section to the top of your config file. Add the following properties to the section:
Where is the duo authentication proxy located?
The Duo Authentication Proxy configuration file is named authproxy.cfg, and is located in the conf subdirectory of the proxy installation. With default installation paths, the proxy configuration file will be located at:
How much RAM is needed for Duo authentication?
The Duo Authentication Proxy can be installed on a physical or virtual host. We recommend a system with at least 1 CPU, 200 MB disk space, and 4 GB RAM (although 1 GB RAM is usually sufficient).
Introduction
Prerequisites
- Requirements
Cisco recommends that you have knowledge of these topics: 1. Basic remote access VPN, Secure Sockets Layer (SSL) and Internet Key Exchange version 2 (IKEv2) knowledge 2. Basic Authentication, Authorization, and Accounting (AAA) and RADIUS knowledge 3. Basic FMC know… - Components Used
The information in this document is based on these software and hardware versions: 1. Cisco FMC 6.4 2. Cisco FTD 6.3 3. AnyConnect 4.7 The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with …
Background Information
- This document is intended to cover the configuration on FTD devices, if you seek for the ASA configuration example, please refer to the document: https://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/100918-asa-sslvpn-00.html Limitations: Currently, these features are unsup…
Nat Exemption and Hairpin
- Step 1. NAT Exemption Configuration
TheNAT exemptionis a preferred translation method used to prevent traffic to be routed to the internet when it is intended to flow over a VPN tunnel (Remote Access or Site-to-Site). This is needed when the traffic from your internal network is intended to flow over the tunnels without a… - Step 2. Hairpin Configuration
Also known as U-turn, this is a translation method that allows the traffic to flow over the same interface the traffic is received on. For example, when Anyconnect is configured with a Full tunnelsplit-tunnel policy, the internal resources are accessed as per the NAT Exemption policy. I…
Verify
- Use this section to confirm that your configuration works properly. Run these commands in the FTD's command line. 1. sh crypto ca certificates 2. show running-config ip local pool 3. show running-config webvpn 4. show running-config tunnel-group 5. show running-config group-policy 6. show running-config ssl 7. show running-config nat