How many firewalls should I put around the it DMZ?
What we learn at reputable training such as SANS, is that in theory the best practice for implementing an IT/OT DMZ is to put two firewalls around the DMZ as is depicted the IT DMZ model: one between the OT network and DMZ network, the other between the DMZ and the IT network.
What are DMZs and why are they important?
DMZs are in essence a network between networks, and in the industrial security context, an added network layer between the OT, ICS, or SCADA, network and the less-trusted IT or enterprise network.
Is it safe to place items in a DMZ?
Placing any item in a DMZ that has access to your network especially to a domain can be dangerous. I would suggest using a 3rd party software (VPN clients) over using RDP. RDP has security flaws that could expose the network to possible intrusion. If you absolutely have to use RDP please review these items: 1.
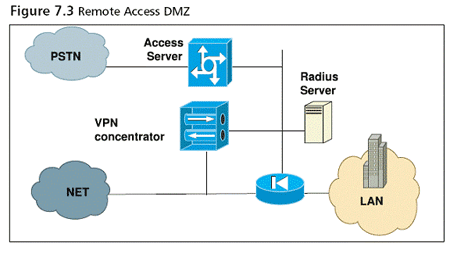
What happened to the patch management server in the DMZ?
The compromise of the patch management server in the DMZ allowed us to pivot via SMB connections to Microsoft Windows-based intermediary systems in the OT network. Lastly, we compromised Microsoft Windows server systems in the OT network to complete the objectives of the exercise.

What is DMZ and why it is used?
A DMZ Network is a perimeter network that protects and adds an extra layer of security to an organization's internal local-area network from untrusted traffic. A common DMZ is a subnetwork that sits between the public internet and private networks.
What is the difference between DMZ and VPN?
Servers that offer services to the public (e.g. Web servers, SMTP servers) are placed in the DMZ, while servers that offer services to internal users reside on the private network. The VPN provides remote users with access to private resources.
What is OT DMZ?
DMZs are in essence a network between networks, and in the industrial security context, an added network layer between the OT, ICS, or SCADA, network and the less-trusted IT or enterprise network.
Can DMZ be hacked?
Companies often place these services within a DMZ: Email servers: Users need internet access to send and receive email messages. But those documents can be extremely sensitive, and when hackers get them, they can sell the data on the dark web or ask for ransom.
Are DMZ still used?
While most organizations no longer need a DMZ to protect themselves from the outside world, the concept of separating valuable digital goodies from the rest of your network is still a potent security strategy. If you apply the DMZ mechanism on an entirely internal basis, then there are still use cases that makes sense.
What is the difference between DMZ and firewall?
Simply, a DMZ is portion of your network carved off and isolated from the rest of your network. A firewall is the appliance that creates that isolation, by restricting traffic both between the intranet and the DMZ and the DMZ and other networks it's exposed to.
Should DMZ be enabled?
DMZ should only be used if you have a computer/device that cannot run Internet applications properly from behind the router.
What devices should be in the DMZ?
Any service provided to users on the public internet should be placed in the DMZ network. External-facing servers, resources and services are usually located there. Some of the most common of these services include web, email, domain name system, File Transfer Protocol and proxy servers.
Where is a DMZ usually located?
demilitarized zone (DMZ), region on the Korean peninsula that demarcates North Korea from South Korea. It roughly follows latitude 38° N (the 38th parallel), the original demarcation line between North Korea and South Korea at the end of World War II.
What are the vulnerabilities to a DMZ?
DMZ resource vulnerabilities Remote access technologies such as VPN or RDP, for example, have become common targets of cyberattacks. Web or email servers that are not sufficiently locked down can let hackers move laterally through the DMZ and eventually into the protected network.
Are DMZ safe?
Hosts in the DMZ have tightly controlled access permissions to other services within the internal network, because the data passed through the DMZ is not as secure. On top of that, communications between hosts in the DMZ and the external network are also restricted to help increase the protected border zone.
How do I secure my DMZ server?
Four Tips for Securing a Network DMZPreserve isolation as much as possible. Keep the rules that allow traffic between the DMZ and an internal network as tight as possible. ... Practice good vulnerability management. ... Use application layer defenses for exposed services. ... Monitor, monitor, monitor.
What is DMZ in router settings?
The Demilitarized Zone (DMZ) is a feature that allows only one (1) local user to be exposed to the Internet for special purposes like Internet gaming or video conferencing.
What is DMZ Cold War?
3. The Demilitarized Zone (DMZ) is often referred to as the world's last remaining Cold War frontier. South Korean and US-led UN coalition forces fought to a standstill here with North Korean and Chinese troops during the 1950-53 Korean War.
What is DMZ Host IP?
A DMZ is a subnetwork that is open to the public but behind the firewall. A DMZ allows you to redirect packets going to your WAN port IP address to a particular IP address in your LAN. We recommended that you place hosts that must be exposed to the WAN (such as web or e-mail servers) in the DMZ network.
Which area is DMZ cybersecurity?
In computer security, a demilitarized zone (DMZ) or perimeter network is a network area (a subnetwork) that sits between an internal network and an external network.
What is a DMZ?
DMZs are in essence a network between networks, and in the industrial security context, an added network layer between the OT, ICS, or SCADA, network and the less-trusted IT or enterprise network. In theory, when correctly implemented, no TCP or any other connection exchanging messages should ever traverse a DMZ between IT and OT;
What is the purpose of a DMZ?
To sum it up, the core purpose of the IT/OT DMZ is two-fold: security and integration . In the industrial context, a DMZ must prevent arbitrary connections to act as attack channels from the internet straight into OT systems, not be an added layer of complexity for the security of control systems nor a funnel through which an attacker can access ICS.
Why are DMZs used?
Part of the reason for the confusion could be that for nearly three decades, digital network DMZs or “demilitarized zones” have been used as a data protection strategy in IT networks to broker access to information by external untrusted networks. This IT DMZ model and approach is well established, but is not necessarily an effective security measure when applied to OT networks. We’ll get to why that is a bit later.
What is unidirectional gateway?
The defining feature of a unidirectional gateway is that it is hardware-enforced: a combination of hardware and software that physically moves information in one direction only – meaning no messages whatsoever (including attacks) can enter the protected OT network from external sources, thus fulfilling the mission and purpose of implementing an IT/OT DMZ. The software element of unidirectional gateways replicates industrial servers and applications in two common scenarios with a Modern IT/OT DMZ:
What should go inside a DMZ?
For industrial purposes, what should go “inside” the DMZ is all of the applications and servers that have TCP connections out to the IT network. In practice, this can be a whole range of things; so when designing IT/OT network integration architectures, we at Waterfall generally see customers deploy an intermediate system to aggregate OT data which needs to be shared with the enterprise. The most common aggregator is one of the many process historians, or one of the many variants of OPC server.
How many ports does a firewall have?
In practice, we often see something much different. Most sites deploy only a single firewall with three ports – one connected to IT, one connected to OT and one to the DMZ network – meaning single vulnerabilities are again a concern. More fundamentally, modern attacks don’t exploit software vulnerabilities, modern attacks exploit permissions. From an attack perspective, exploiting vulnerabilities involves a lot of work and code writing – unless of course someone else has already done the work and released an attack tool to the public. Exploiting permissions, on the other hand, can be as easy as stealing the firewall password, or stealing a password on the IT network that the OT network then trusts or allows an attacker to go into a historian or other system in the DMZ right through the firewall.
What is a DMZ?
A DMZ, or de-militarized zone, is a network that is protected by access control mechanisms. Access control may be provided by a firewall device, a router, or a switch that provides port and address filtering capabilities. The purpose of the DMZ is to limit access to systems that are deployed within it. In the case of the B Series Appliance, the DMZ ...
Why is no firewall change required?
No firewall changes are required because the device and all of the endpoint clients are internal to the firewall. In environments where the remote systems are external to the firewall, BeyondTrust recommends this deployment location only in the event that a DMZ does not exist or when the B Series Appliance cannot be deployed externally. ...
Can a DMZ be deployed externally?
External Deployment:In situations where a DMZ does not exist and is not possible due to technical or business constraints, the B Series Appliance may be deployed external to the perimeter firewall.
The Problem: You Need Remote Access to Your Homelab
Unless your Homelab is hosted on “in the cloud,” it’s unlikely you already have remote access, at least without doing some “fancy” ssh or vnc tricks. Today we’ll look at how to setup remote access without having administrative access to your network’s router.
A Solution: Mesh Networks
I prefer this method because it means you don’t need administrative access to your network’s router (s). This route also means you just need an active network connection and everything’s ready to run – whereas Port Forwarding requires configuring your network router (unless you brought your own).
Enumerating Some Options
To get this running, you’ll have to setup your own Virtual Network. Tools I’ve used in the past are AlgoVPN, TincVPN, and ZeroTier.
Setting Up ZeroTier
Ensure you’ve installed ZeroTier One on all the devices you want in your Mesh Network. ZeroTier One is available on Windows, Android, iOS, most major Linux distributions and MacOS (I recommend using brew cask install zerotier-one ).
Where are network design documents and backup files for OT firewall configurations found?
Extract network design documents and backup files for OT firewall configurations found in the firewall management console
What is an actor who covertly performs internal reconnaissance and propagates to the OT network?
An actor who covertly performs internal reconnaissance and propagates to the OT network is already positioned to cause damage on mission critical assets and is unlikely to be discovered. Early detection of adversary activity before reaching critical OT systems will decrease the dwell time and the risk of an incident.
Why is internal reconnaissance and network propagation important?
Although specific capabilities such as malware and tooling vary amongst incidents, internal reconnaissance and network propagation are consistently needed for sophisticated adversaries to expand remote operations from external networks to OT systems. Focusing collection, detection, and hunting efforts on assets or information that are likely to be compromised during these phases presents defenders with strategic opportunities to hunt for and detect targeted adversary activity before it poses a risk to control systems.
What is OT defender?
OT defenders can prioritize collection and detection, alert triage, and incident response efforts by becoming familiar with the types of information and services that OT focused threat actors commonly search for during internal reconnaissance in IT networks and network propagation across OT intermediary systems.
What is the ideal scenario for an attacker targeting OT systems?
The ideal scenario for an attacker targeting OT systems is to achieve their objective while remaining undetected. Mandiant’s Red Team works with clients across critical infrastructure industries to simulate attack scenarios in which actors can accomplish this goal by gaining access to OT systems via compromise of external facing IT networks. During these engagements, we emulate real actor behaviors to learn about our target and to determine the best paths for IT/OT network propagation.
Is OT isolated from public networks?
However, there is a continued perception across critical infrastructure organizations that OT networks are isolated from public networks— such as the Internet. In Mandiant’s experience, the concept of an ‘air gap’ separating OT assets from external networks rarely holds true in practice.