Recommended Level: Another way you can hack into someone's computer is by installing or getting the users to install TeamViewer software. This software gives you the ability to literally take over a computer and control it from your device which is acting as a remote control, giving you access to all the data on the target computer.
Full Answer
How can hackers gain access to a network remotely?
There are several ways hackers can gain access to a network remotely using this software: lack of governance for installing remote access software and weak remote access account passwords.
How can you hack into someone's computer?
Recommend Level: Another way you can hack into someone's computer is by installing or getting the users to install TeamViewer software, this software gives you the ability to literally take over a computer and control it from your device which is acting as a remote control, giving you access to all the data on the target computer.
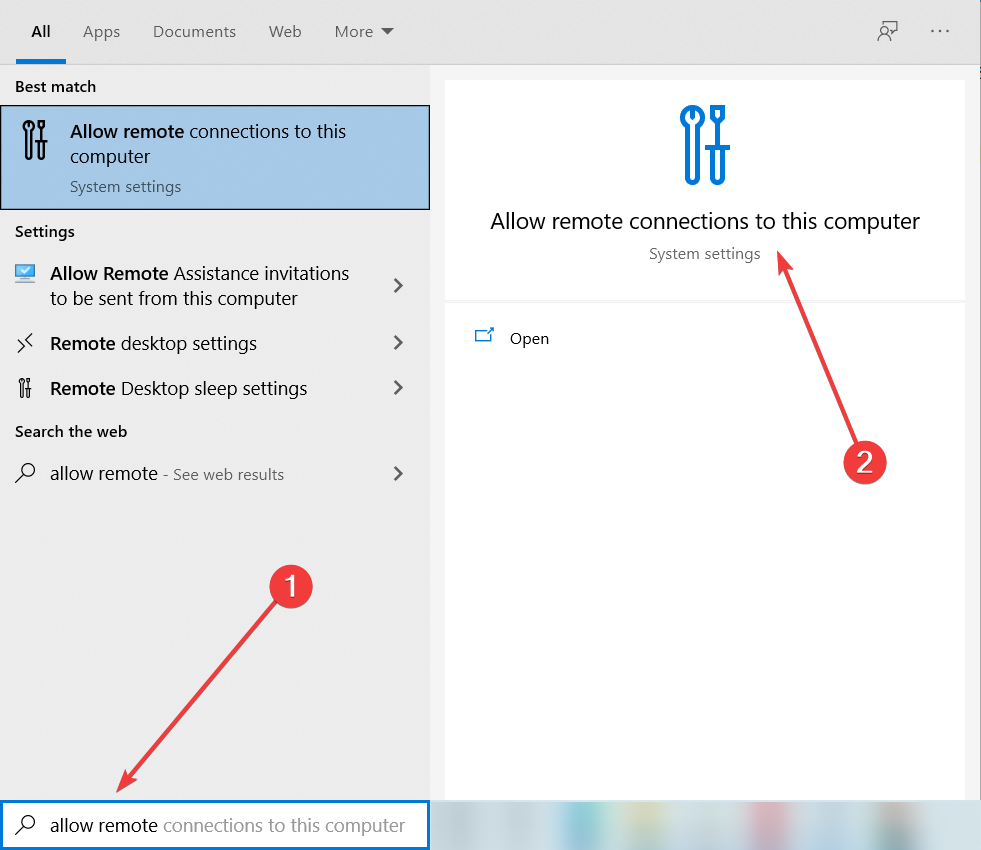
How do I enable remote access to a Windows 10 computer?
1 From “Control Panel”, go to “System and Security”. 2 Click on “Allow Remote Access” under “System”. 3 From the “Remote” tab, select the radio button present near “Allow remote connections to this computer”.
Can you remotely control another computer without any tool?
With Remote access, one can easily control everything on another computer, like managing files, troubleshoot things, etc. There are plenty of remote access tools available out there like Ammy, Teamviewer, etc. However, what if I tell you that you can remotely control another computer without using any tool? Yes, it’s absolutely possible.
How do I Remotely Access Another Computer without Permission?
What is a virus that attaches itself to a downloadable file or a link within a?
Can you hack a computer if you are not an administrator?
Can you hack someone's computer with Monivisor?
Can you hack a computer if it is not locked?
Is It Possible to Hack Into Someone's Computer Remotely?
See 1 more

Can hackers get remote access to your computer?
Using remote access software outside of a local network can also enable hackers to execute brute force attacks by trying to decode weak passwords and codes. Once they gain access to your system, they'll be able to acquire information that can result in a major security incident.
How can I remotely control someone else's computer?
Chrome Remote Desktop is available on the web on your computer. To use your mobile device for remote access, you need to download the Chrome Remote Desktop app....Access a computer remotelyOn your Android phone or tablet, open the Chrome Remote Desktop app. ... Tap the computer you want to access from the list.More items...
How can I remotely log into someone else's computer for free?
10 Best Free Remote Desktop Tools You Should KnowTeamViewer. Available in premium and free versions, TeamViewer is quite an impressive online collaboration tool used for virtual meetings and sharing presentations. ... Splashtop. ... Chrome Remote Desktop. ... Microsoft Remote Desktop. ... TightVNC. ... Mikogo. ... LogMeIn. ... pcAnywhere.More items...
How do hackers hack remotely?
Remote hackers use various malware deployment methods; the most common (and probably the easiest) way for hackers to reach unsuspecting victims is through phishing campaigns. In this scenario, hackers will send emails with links or files, which unsuspecting recipients may click on.
How can I remotely access another computer using IP address?
Once you've set up the target PC to allow access and have the IP address, you can move to the remote computer. On it, open the Start Menu, start typing “Remote Desktop” and select Remote Desktop Connection when it appears in the search results. Then in the box that appears type the IP address and click Connect.
How can I remotely access someones laptop?
0:582:38How To Access Any PC or Laptop Remotely At Your Home Using IP ...YouTubeStart of suggested clipEnd of suggested clipSo after that you have to open run box on your computer just pressing windows + R button together.MoreSo after that you have to open run box on your computer just pressing windows + R button together. And after that you have to type over there CMD. Now press Enter from your keyboard. And after that
Can hackers use TeamViewer?
The FBI alert doesn't specifically tell organizations to uninstall TeamViewer or any other type of desktop sharing software but warns that TeamViewer and other similar software can be abused if attackers gain access to employee account credentials or if remote access accounts (such as those used for Windows RDP access) ...
Do hackers use AnyDesk?
Sophos discovered that the AvosLocker attackers installed AnyDesk so it works in Safe Mode, tried to disable the components of security solutions that run in Safe Mode, and then ran the ransomware in Safe Mode.
Can hackers hack without Internet?
Can an Offline Computer be Hacked? Technically — as of right now — the answer is no. If you never connect your computer, you are 100 percent safe from hackers on the internet. There is no way someone can hack and retrieve, alter or monitor information without physical access.
Is there a free LogMeIn version?
Try LogMeIn's work-from-anywhere products for free.
Is Microsoft Remote Desktop free?
Microsoft Remote Desktop With the platform—which Microsoft provides for free—you can remotely access Windows PCs from other Windows computers, mobile, devices, and Macs.
Is AnyDesk free for personal use?
AnyDesk offers an easy-to-use Remote Desktop Software including all basic features that is free for personal use.
Is TeamViewer free for private use?
TeamViewer is free for personal use, which means any tasks within your personal life for which you are not being paid. Connections between personal devices at home or helping friends and family remotely qualify as personal use. To learn more, see this article from the TeamViewer Community.
How can Hackers Exploit Remote Access Software?
Hackers have several ways of exploiting the vulnerabilities of remote access software in hopes of causing a security incident to a private network or system. If there’s a poor protocol for installing remote access software, then there’s a high chance for hackers to gain unwanted access to your system.
Why is it important to secure remote access?
By securing remote access software, you’ll be able to have a safe environment away from security threats and risks that come with the utilization of remote access.
What is Remote Access Software?
Remote access software is a type of program that allows a computer to be accessed and control remotely while its screen is being displayed on a client’s computing device. Most of today’s businesses use this technology to effectively manage business operations in and out of the country, conduct remote meetings and conferences, and allow employees to access their files even outside of a corporate space. For small businesses, remote access software acts as a tool that allows them to outsource IT services and maintenance.
How do cybercriminals attack?
It’s a common practice for cybercriminals to launch attacks by tricking people through phishing scams and deceitful malware-mounted files. Hackers may also exploit the vulnerabilities of a private network or a system to steal confidential information and data. Though these types of malicious practices have become a norm in the field of modern hacking and online theft, another exploitable technology has also become a desirable prey for modern hackers – remote access software.
Why do you need to use two factor authentication?
Using two-factor authentication can help you strengthen your passwords even more. By combining two user identifications, hackers may have a difficult time decoding your passwords and breaking into your private system. You can also use unique passwords for each remote access account to ensure that security of your system against cybercriminals and hackers.
How did Russian hackers get into European embassies?
An article released by Sify Finance revealed that a group of Russian hackers were able to target a number of European embassies by using popular remote access software. These hackers sent out deceitful files that they disguised as a credible US government data to the targeted embassies in Kenya, Liberia, Nepal, Guyana, Italy, Bermuda, Lebanon, and others. Once viewed, these hackers were able to gain access to the targeted computer by unwillingly installing the said remote access software.
Should remote access be disabled?
Otherwise, all access should be disabled temporarily. Remote access policies should also be evaluated annually to assess the areas of improvement that need to be focused on.
How Do Hackers Gain Access?
There are several ways hackers can gain access to a network remotely using this software: lack of governance for installing remote access software and weak remote access account passwords. If a company’s employees are unaware that they’ve installed remote access software on company devices, then there is potential for abuse as it increases the risk of hackers finding a backdoor.
What is remote access software?
Remote access software allows a computer’s desktop environment to be run remotely on one system while being displayed on a separate client device. Many organizations find remote access software extremely useful.
Why is it important to choose a strong password for remote access?
It’s extremely important for businesses to choose a strong password for their remote access accounts. If the RDP is exposed to the Internet, a simple network engine can allow hackers to poke around the network and use various methods like brute force attacks to try and guess the password. Once inside the system, it’s only a matter of time before they acquire access information needed to infiltrate other critical systems.
What is fileless attack?
Previously, we discussed fileless attacks, an increasingly popular method used by hackers to spread ransomware that sometimes involves exploiting the macro functionality in Microsoft Office documents. Now, it appears that another exploitable entry point has been on the rise: remote access software.
Why were the WannaCry and NotPetya attacks successful?
Both the WannaCry and NotPetya attacks, for example, were successful because hackers used leaked NSA exploits to infect older computer operating systems.
What is RDP hacking?
Hackers are getting more and more creative in their hacking methods, and using the RDP is one way they can make their way into a company’s network. In fact, Naked Security recently reported on a growing trend of hackers spreading ransomware by accessing computer systems through the RDP.
How do hackers sneak into a network?
Hackers typically sneak remotely into the networks of their victims by setting up phishing scams and duping users into downloading malware-ridden files, which are then executed to commence a cyberattack like ransomware. They may also look for vulnerabilities in computer systems to attempt to get into a network.
How to enable remote desktop on Windows 10?
Step 1: From the Windows button, go to the “Start” menu. Step 2: Click on the gear icon which symbolizes the “Settings”. Step 3: Click on “System” and then on “Remote Desktop”. Step 4: Switch on “Enable Remote Desktop”. If you are using the older version of Windows, you need to follow the steps given below.
Can you access someone else's computer?
You can access others’ computer from almost any device with a stable internet connection.
Can you remotely control another computer?
Once you have followed the above steps, you can use cmd to remotely control on another computer to access their computer system. Here are the steps to know how to remotely access another computer without permission using cmd.
Can you key in your computer's IP address?
Instead of “computername” you can even key in your computer system’s public IP address. If you do not know the IP address of the target’s computer, you can search for “What’s my IP” on Google through target’s browser. 3. The Limitations of Using CMD To Hack a Computer.
Can you hack into a remote desktop?
1. If the target’s computer have not earlier configured a remote desktop computer system, you cannot hack into the system using this method. 2. For this method to work, the target’s computer needs to be on and not in sleep or hibernation mode. 3.
How to remotely access another computer?
Remotely Access Another Windows Computer: Step 1. First of all, in your Windows 10 got to your system settings by clicking on the Windows button on your keyboard and then entering ‘System .’ . Step 2. In a system setting, you need to select the Remote Settings on the left of the screen. Step 3. Now there enable the Allow remote connections ...
What is remote access?
Remote computer access is a method in the computer world to control another computer remotely over the internet. Technicians and business owners mostly use remote Computer Access to guide their clients and employees. With Remote access, one can easily control everything on another computer, like managing files, troubleshoot things, etc.
What is Quick Assist?
Well, Quick Assist is a part of the Windows 10 operating system now, and it can be used remotely to troubleshoot a friend’s Windows PC without installing any extra software. Let’s check out how to use Quick Assist to remove access to another computer.
How to hack a webcam?
For a person to know “How to hack someone’s webcam”, first it is important to find out how to hack someone’s computer because webcam itself is part of the computer and we need to gain access to the software first. For this purpose, there are several programs that can be downloaded remotely on your computer which are actually some sorts of viruses. Some of them are:
How to protect yourself from hacked webcams?
It is always better for users to adopt safety measures on their own in order to protect themselves from hacking. Some of the measures that can be taken are as follows:
How to find out IP address?
Internet Protocol (IP) address is a distinct form of identification in numbers that are allocated to every device that is connected to a network and uses the Internet for communication. IP addresses can be used for numerous reasons, both good and bad. The good reasons include the identification of users by different companies in order to place them in separate categories.
What is Hacking?
Before we head into the detailed guide of “How to hack laptop camera using IP address”? first, we have to find out what actually hacking is? In simple words, hacking is to gain unauthorized access to a computer or network. Once a hacker gains this access, then the data can be stolen and misused for various purposes. This may be just for fun, for example hacking a friend’s Facebook account to prove that someone has more technical knowledge than his peers but it can range up to high profile hacking in which data of national importance may be stolen and used for malicious purposes.
Why do people hack webcams?
The main reason is to blackmail the users because the hacker can gain access to compromising photos or videos of them while they are in front of the webcam. This is common with females as men use this tactic to blackmail them for money. Another reason is to find out more about a person or his belongings and residence.
What is hacking in cybercrime?
Hacking is one of the parts of cybercrime which is a collective term used for describing unethical activities done in the digital space. With the development of Internet, webcam and social media applications, people are interested in learning about new forms of hacking such as “how to hack webcam”? and “how to hack IP address”?
How much money did a hacker lose in 2000?
In 2000, a 15 year old hacked high profile websites like Amazon and CNN, eBay and Yahoo which resulted in a loss of almost $1 billion dollars for the companies.
How do I Remotely Access Another Computer without Permission?
you will need to either know how to using some technical techniques or you will have to install a hacking app on the target device to get around knowing how to hack someone's computer remotely.
What is a virus that attaches itself to a downloadable file or a link within a?
A virus, which attaches itself to a downloadable file or a link within a phishing email , unravels the road into someone's personal computer, letting you attain access to the contents contained within it.
Can you hack a computer if you are not an administrator?
However, if you are not an administrator, it is still possible to gain access but you will need to use professional hacking steps to do so.
Can you hack someone's computer with Monivisor?
After reading the introduction and the steps on how to hack someone's computer with MoniVisor, we can know that this is an App suitable for everyone. Indeed, there are other 2 ways to hack a computer without the help of such ind of professional software, but you have to be equipped with good basis of technology. Check these ways below.
Can you hack a computer if it is not locked?
This method, however, can prove to backfire if the user catches onto what is happening, as the software is clearly visible on the target computer, they can clearly know what are you doing if the screen is not locked. You also need to have the same version and a stable and fast connection on both sides in order for this method to work effectively, a stable internet connection is not possible all the time making hacking and monitoring limited to only when the target computer is connected to LAN or Wi-Fi.
Is It Possible to Hack Into Someone's Computer Remotely?
Although not necessarily easy, it is definitely possible to remotely enter into someone's computer. To break into someone's system, you must gain their permission to do so, and it is important they do not realize that they have given it to you. A virus, which attaches itself to a downloadable file or a link within a phishing email, unravels the road into someone's personal computer, letting you attain access to the contents contained within it. A much simpler and safer method, though, is to simply use an invisible third-party hacking tool such as MoniVisor by ClevGuard in order to not get caught or waste too much time.