- On your computer, open Chrome.
- In the address bar, enter remotedesktop.google.com/access .
- Under “Set up Remote Access,” click Download .
- Follow the onscreen directions to download and install Chrome Remote Desktop.
How do I Turn on remote access on my computer?
Windows 10 Fall Creator Update (1709) or later
- On the device you want to connect to, select Start and then click the Settings icon on the left.
- Select the System group followed by the Remote Desktop item.
- Use the slider to enable Remote Desktop.
- It is also recommended to keep the PC awake and discoverable to facilitate connections. ...
How do I setup my computer for remote access?
To enable remote connections on Windows 10, use these steps:
- Open Control Panel.
- Click on System and Security.
- Under the “System” section, click the Allow remote access option ...
- Click the Remote tab.
- Under the “Remote Desktop” section, check the Allow remote connections to this computer option.
How to remotely access another computer from your computer?
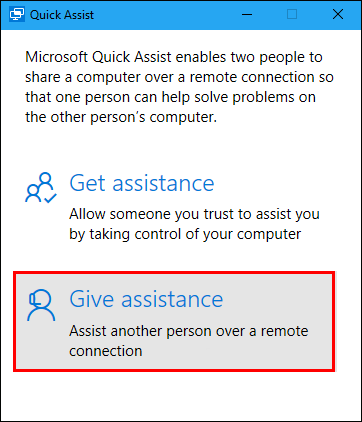
Using Quick Assist
- First of all, head to the Start Menu > Windows Accessories > Quick Assist.
- To remote into another computer, click on the ‘Give Assistance’ option.
- Now you will be asked to sign in with the Microsoft account and will receive a security code.
- Now the other person needs to open the Quick Assist tool and click on the ‘Get Assistance’ button.
How can Someone remotely access my computer?
How to remote access and control your Mac remotely from your iPhone
- Using Mac Screen Sharing. With the built-in Mac Screen Sharing tool enacted in macOS, it's possible to access a Mac anywhere with an internet connection.
- Using SharePlay with FaceTime. One of the newest ways to share your Mac screen is by using FaceTime's SharePlay feature. ...
- Use iCloud Drive. ...
- Limitations exist. ...

Can someone get into my computer remotely?
Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular. Remote desktop servers connect directly to the Internet when you forward ports on your router. Hackers and malware may be able to attack a weakness in those routers.
How can I remotely access someones laptop?
0:232:38How To Access Any PC or Laptop Remotely At Your Home Using IP ...YouTubeStart of suggested clipEnd of suggested clipSo at first you need to enable remote desktop on you computer. So for that you have to go to your myMoreSo at first you need to enable remote desktop on you computer. So for that you have to go to your my computer first and after that you have to right click over there and go to the properties. So if
How can I remotely access another computer outside my network?
Use a VPN. If you connect to your local area network by using a virtual private network (VPN), you don't have to open your PC to the public internet. Instead, when you connect to the VPN, your RD client acts like it's part of the same network and be able to access your PC.
How can I remotely access another computer over the internet for free?
10 Best Free Remote Desktop Tools You Should KnowTeamViewer. Available in premium and free versions, TeamViewer is quite an impressive online collaboration tool used for virtual meetings and sharing presentations. ... Splashtop. ... Chrome Remote Desktop. ... Microsoft Remote Desktop. ... TightVNC. ... Mikogo. ... LogMeIn. ... pcAnywhere.More items...
What is remote computer access?
Many people take their laptops with them to do things like finish a business presentation while waiting for a flight at the airport. But a lot of those laptops may not have bigger, important files on them. You might leave those files at work or at home on your desktop computer.
How to protect your computer when using remote access?
Here are some steps you can take to help protect your computer and data while relying on remote access. Maintain strong passwords.
How does TeamViewer work?
Here’s how it works. You’ll need to create an account, and then download and install TeamViewer software onto both your home computer and your remote computer or device. TeamViewer can be installed on Windows, Mac OS, Linux, and Chrome OS. It also has apps for Windows Phone, Blackberry, iOS, and Android. LogMeIn.
How to protect remote desktop from hackers?
Use a secure Virtual Private Network (VPN). If you set up a VPN, your remote desktop server won’t be connected directly to the internet. It will only be exposed on your local network, which could leave it less vulnerable to hackers.
How to protect your network from remote access?
You should set up firewalls to restrict access using software or hardware or both.
What is remote access software?
Remote computer access software lets you access networks and computers remotely. It can enable file sharing. It’s like having a remote control for a computer or system that isn’t near you. You’ll be able to remotely download files and applications from your desktop or another person’s computer onto your laptop or your cell phone. Remote access also gives you control over that remote device
Why is it important to limit the number of users who can log in?
Remote computer access can help businesses, individuals, and families in a variety of ways. But it’s important to make remote access secure .
How to gain remote access to a computer?
There are several ways a person can gain remote access. 1. The user downloads a virus through a file or pic of an unknown sender. 2. Through remote assistance ( this has to be verified by the owner of the computer first.
What is a link to a virus?
Any link to or advocacy of virus, spyware, malware, or phishing sites. Any other inappropriate content or behavior as defined by the Terms of Use or Code of Conduct. Any image, link, or discussion related to child pornography, child nudity, or other child abuse or exploitation.
What are threats in the community?
Threats include any threat of suicide, violence, or harm to another. Any content of an adult theme or inappropriate to a community web site. Any image, link, or discussion of nudity. Any behavior that is insulting, rude, vulgar, desecrating, or showing disrespect.
What is remote assistance on Windows 10?
Windows has two remote assistance tools built in to the operating system: Quick Assist, which is new in Windows 10, and Windows Remote Assistance, which is available on Windows 7, 8, and 10. If both you and your friend are using Windows 10, you'll want to use Quick Assist.
How to help someone on Microsoft?
In the window that appears, click the Assist Another Person button under Give Assistance. Sign in with your Microsoft account (you need a Microsoft account to help, but your friend or relative does not), and you'll be given a six-digit code that expires in 10 minutes.
How to control zoom screen?
To request control, click the View Options drop-down menu while in a call and select Request Remote Control. The meeting host can then grant you control.
How to connect to a friend's computer using Windows 7?
If your friend or family member is still using Windows 7 or 8, you will need to use the older Remote Assistance tool . The tool is similar to Quick Assist, but it’s far clunkier to use. They should head to the Control Panel and search for Invite Someone to Connect to Your PC . They will need to send you a file over email that initiates the connection, then tell you the password that appears (preferably over the phone) so you can access their machine.
How many digits are needed to access a friend's computer?
That will produce a 12-digit access code you'll need to gain access to their computer. On your PC, from the Remote Desktop site, type in that code under Connect to Another Computer. Your friend will then need to grant you permission, after which you can control their computer and help them solve their problem.
How to share screen control in teams?
You can do the same in Microsoft Teams. Take control of someone's screen by clicking Request control while they are sharing their screen. If you're sharing the screen, select Give control in the sharing toolbar and select the person in order to share control with them.
Can you control someone else's screen?
If you absolutely need to control someone else's screen, your best bet is Chrome Remote Desktop, which doesn't come with the security issues that remote access tools like TeamViewer have had in the past few years.
How to access remote computer?
There are a couple of ways to access the remote computer. If you logged in to your account in the host program, then you have permanent access which means you can visit the link below to log in to the same account in a web browser to access the other computer.
How to enable remote desktop access to a computer?
To enable connections to a computer with Windows Remote Desktop, you must open the System Properties settings (accessible via Settings (W11) or Control Panel) and allow remote connections via a particular Windows user.
How to connect to a host browser?
To connect to the host browser, sign on to Chrome Remote Desktop through another web browser using the same Google credentials or using a temporary access code generated by the host computer.
How does remote utility work?
It works by pairing two remote computers together with an Internet ID. Control a total of 10 computers with Remote Utilities.
What is the other program in a host?
The other program, called Viewer, is installed for the client to connect to the host. Once the host computer has produced an ID, the client should enter it from the Connect by ID option in the Connection menu to establish a remote connection to the other computer.
What is the easiest program to use for remote access?
AeroAdmin is probably the easiest program to use for free remote access. There are hardly any settings, and everything is quick and to the point, which is perfect for spontaneous support.
What is the name of the program that allows you to access a Windows computer without installing anything?
Install a portion of Remote Utilities called Host on a Windows computer to gain permanent access to it. Or o just run Agent, which provides spontaneous support without installing anything—it can even be launched from a flash drive.
How to stop someone from accessing my computer?
This includes removing any Ethernet cables and turning off your Wi-Fi connections.
How to install antivirus on another computer?
If you don't have an antivirus, download an installer on another computer and transfer it to your computer via USB. Install the antivirus and then run a scan with it.
What to do if your computer is compromised?
Change all of your passwords . If your computer was compromised, then there’s a possibility that all of your passwords have been recorded with a keylogger. If you’re sure the infection is gone, change the passwords for all of your various accounts. You should avoid using the same password for multiple services.
Why is public Wi-Fi so dangerous?
Try to avoid public Wi-Fi spots. Public Wi-Fi spots are risky because you have zero control over the network. You can't know if someone else using the spot is monitoring traffic to and from your computer. By doing this, they could gain access to your open browser session or worse. You can mitigate this risk by using a VPN whenever you are connected to a public Wi-Fi spot, which will encrypt your transfers.
What to do if you can't get rid of intrusion?
If you're still experiencing intrusions, or are concerned that you may still be infected, the only way to be sure is to completely wipe your system and reinstall your operating system.
Why does my computer turn on without my input?
If your computer appears to turn on without your input when you're not using it, it is likely waking from Sleep mode to install updates .
How to find out what is running on my computer?
Open your Task Manager or Activity Monitor. These utilities can help you determine what is currently running on your computer.
How to remotely control one computer with another?
1. Install Chrome Remote Desktop on both computers. This is a free tool from Google that lets you remotely control one computer with another. The tool requires using Google Chrome as your web browser, so if you don't have Chrome installed, you'll need to get it from https://www.google.com/chrome. Complete the following steps on both computers: ...
How to get to the Windows key on a host computer?
on the host PC. Click the Windows logo in the bottom-left corner of the screen, or press the Windows key.
How long is Chrome Remote Desktop valid?
The code will only be valid for 5 minutes from creation, so you'll want to do this right before you're ready to make the connection. Here's how to generate the code on the computer receiving the connection:
How to download TeamViewer?
Scroll down and click Download TeamViewer. It's a green button near the top of the page. Doing so prompts the TeamViewer setup file to begin downloading to your computer.
How many digits is a remote desktop pin?
Enter and confirm a 6-digit PIN. Once confirmed, Remote Desktop will start.
Where is the computer name on a PC?
Note your computer's name. It's at the top of the page, right next to the "PC name" heading. You'll need this to connect the second computer to this one.
Where is Advanced System Settings?
Click Advanced system settings. It's in the upper-left side of the System window.
How do I Remotely Access Another Computer without Permission?
you will need to either know how to using some technical techniques or you will have to install a hacking app on the target device to get around knowing how to hack someone's computer remotely.
Can you monitor activity from dashboard?
The installation and configuration process is seamless and convenient and you can start monitoring activity from your dashboard right away! What makes this solution unique from others is that it does all this while remaining invisible on the target computer, meaning that the target will never know they have been hacked!
Can you hack a computer if you are not an administrator?
However, if you are not an administrator, it is still possible to gain access but you will need to use professional hacking steps to do so.
Can you hack someone's computer with Monivisor?
After reading the introduction and the steps on how to hack someone's computer with MoniVisor, we can know that this is an App suitable for everyone. Indeed, there are other 2 ways to hack a computer without the help of such ind of professional software, but you have to be equipped with good basis of technology. Check these ways below.
Can you hack a computer if it is not locked?
This method, however, can prove to backfire if the user catches onto what is happening, as the software is clearly visible on the target computer, they can clearly know what are you doing if the screen is not locked. You also need to have the same version and a stable and fast connection on both sides in order for this method to work effectively, a stable internet connection is not possible all the time making hacking and monitoring limited to only when the target computer is connected to LAN or Wi-Fi.
Is It Possible to Hack Into Someone's Computer Remotely?
Although not necessarily easy, it is definitely possible to remotely enter into someone's computer. To break into someone's system, you must gain their permission to do so, and it is important they do not realize that they have given it to you. A virus, which attaches itself to a downloadable file or a link within a phishing email, unravels the road into someone's personal computer, letting you attain access to the contents contained within it. A much simpler and safer method, though, is to simply use an invisible third-party hacking tool such as MoniVisor by ClevGuard in order to not get caught or waste too much time.
What is the most basic method by which to can access someone’s phone without their knowledge?
Password peeking is the most basic method by which to can access someone’s phone without their knowledge. This involves watching when they unlock their phone or asking them to open their phone for some reason while making sure you can view their password.
Is It Possible To Spy On A Cell Phone Without Having It?
The only time it is legal to spy on a cell phone is with the phone owner’s knowledge. In the case of spy apps like PhoneSpector, you can spy on a cell phone with their knowledge. This is specifically true for parents tracking their child’s phone use and businesses tracking company-owned devices.
