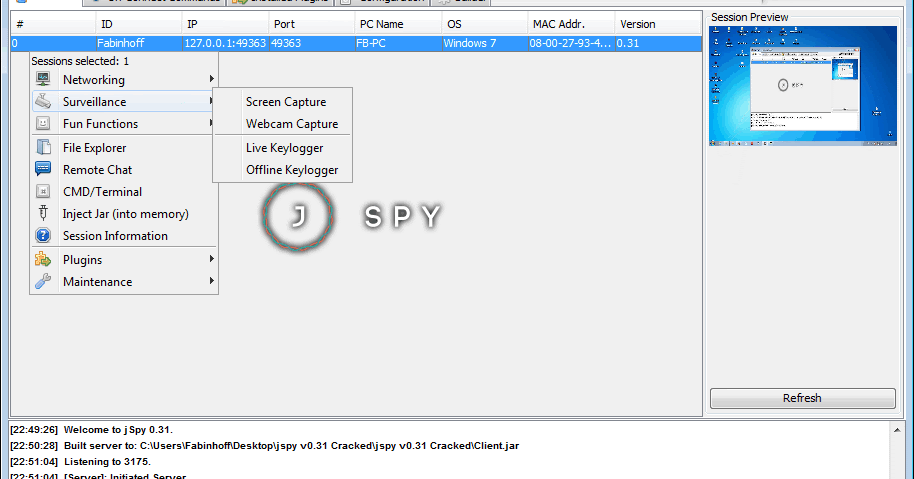
Well, the answer is YES, they can. In fact, infiltrating a computer through remote access is one of the common methods used by cybercriminals. Lately, hacking the PCs through remote access, spying, or stealing sensitive data has become common for cyberattackers.
Full Answer
How to stop remote hacking?
- Educate your employees. Like most things in life, it all begins with education. ...
- Make VPNs mandatory. A virtual private network, or VPN, establishes a protected connection even when you’re using a public network.
- Use shared documents. ...
- Implement two-factor authentication. ...
- Teach staff how to recognise hacking attempts. ...
- Enforce regular password changes. ...
How to block remote hackers?
Steps
- Follow forums. It is always a good idea to follow hacking forums as you will be able to pick up on all the latest methods being used.
- Change default passwords immediately. Some software has built-in passwords to allow the first login after installation; it is extremely unwise to leave it unchanged.
- Identify entry points. ...
How can I prevent remote access to my Windows PC?
Windows 8 and 7 Instructions
- Click the Start button and then Control Panel.
- Open System and Security.
- Choose System in the right panel.
- Select Remote Settings from the left pane to open the System Properties dialog box for the Remote tab.
- Click Don’t Allow Connections to This Computer and then click OK.
What is the best remote access for PC?
What is the Best Remote Desktop Software?
- GoToMyPC. GoToMyPC is the best remote desktop software on this list. ...
- AnyDesk. AnyDesk is one of the most popular remote desktop software platforms, used by over 100 million users globally.
- LogMeIn. ...
- Parallels. ...
- Splashtop Business Access. ...
- Zoho Assist. ...
- ConnectWise Control. ...
- RemotePC. ...
- TeamViewer. ...
- Remote Utilities for Windows. ...

Can a PC be hacked remotely?
Remote desktop hacks become a common way for hackers to access valuable password and system information on networks that rely on RDP to function. Malicious actors are constantly developing more and more creative ways to access private data and secure information that they can use as leverage for ransom payments.
How can I remotely access someones computer?
You can set up remote access to your Mac, Windows, or Linux computer.On your computer, open Chrome.In the address bar, enter remotedesktop.google.com/access .Under “Set up Remote Access,” click Download .Follow the onscreen directions to download and install Chrome Remote Desktop.
Is it possible to hack remotely?
Yes. Unfortunately, they can even hack a phone's camera. But you can also learn how to block hackers from your Android or iOS phone.
How do hackers use Remote Desktop?
Hackers use RDP to gain access to the host computer or network and then install ransomware on the system. Once installed, regular users lose access to their devices, data, and the larger network until payment is made.
Can someone access my computer remotely without me knowing?
"Can someone access my computer remotely without me knowing?" The answer is "Yes!". This could happen when you are connected to the internet on your device.
How can I remotely access another computer for free?
10 Best Free Remote Desktop Tools You Should KnowTeamViewer. Available in premium and free versions, TeamViewer is quite an impressive online collaboration tool used for virtual meetings and sharing presentations. ... Splashtop. ... Chrome Remote Desktop. ... Microsoft Remote Desktop. ... TightVNC. ... Mikogo. ... LogMeIn. ... pcAnywhere.More items...
What remote access methods could an attacker exploit?
Common remote access attacks An attacker could breach a system via remote access by: Scanning the Internet for vulnerable IP addresses. Running a password-cracking tool. Simulating a remote access session with cracked username and password information.
Can someone hack my phone by texting me?
Android phones can get infected by merely receiving a picture via text message, according to research published Monday. This is likely the biggest smartphone flaw ever discovered.
What is remotely hacked?
Remote desktop hacking is defined as when an attacker takes control of your computer from a remote location using a vulnerable Remote Desktop Protocol (RDP). RDP is usually used as a way to give administrators or collaborators remote access to a device when they are not in the same office.
Can hackers use TeamViewer?
The FBI alert doesn't specifically tell organizations to uninstall TeamViewer or any other type of desktop sharing software but warns that TeamViewer and other similar software can be abused if attackers gain access to employee account credentials or if remote access accounts (such as those used for Windows RDP access) ...
Can someone hack my phone remotely?
remotely. Skilled hackers can take over a hacked smartphone and do everything from making overseas phone calls, sending texts, and using your phone's browser to shop on the Internet. Since they're not paying your smartphone bill, they don't care about exceeding your data limits.
Can someone control my phone remotely?
The truth is that someone can spy on your phone without physically touching it. People can remotely install spying software and track your phone without your knowledge. Remote access to any device connected to the internet is possible in some way.
Can hackers see you through your phone camera?
On top of that, popular app developers aren't immune to accusations of watching you through your phone's camera. Generally, however, a stalker would need to install spyware on your device in order to compromise it. Hackers can gain access to your phone physically, through apps, media files, and even emojis.
Is my phone being remotely accessed?
How to Tell Someone Is Accessing Your Phone Remotely. Here are some signs that someone might have unauthorized access to your smartphone: Unknown apps are running in the background. Your phone has an increased closing time and is slower overall.
How do I Remotely Access Another Computer without Permission?
you will need to either know how to using some technical techniques or you will have to install a hacking app on the target device to get around knowing how to hack someone's computer remotely.
What is a virus that attaches itself to a downloadable file or a link within a?
A virus, which attaches itself to a downloadable file or a link within a phishing email , unravels the road into someone's personal computer, letting you attain access to the contents contained within it.
Can you hack a computer if you are not an administrator?
However, if you are not an administrator, it is still possible to gain access but you will need to use professional hacking steps to do so.
Can you hack someone's computer with Monivisor?
After reading the introduction and the steps on how to hack someone's computer with MoniVisor, we can know that this is an App suitable for everyone. Indeed, there are other 2 ways to hack a computer without the help of such ind of professional software, but you have to be equipped with good basis of technology. Check these ways below.
Can you hack a computer if it is not locked?
This method, however, can prove to backfire if the user catches onto what is happening, as the software is clearly visible on the target computer, they can clearly know what are you doing if the screen is not locked. You also need to have the same version and a stable and fast connection on both sides in order for this method to work effectively, a stable internet connection is not possible all the time making hacking and monitoring limited to only when the target computer is connected to LAN or Wi-Fi.
Is It Possible to Hack Into Someone's Computer Remotely?
Although not necessarily easy, it is definitely possible to remotely enter into someone's computer. To break into someone's system, you must gain their permission to do so, and it is important they do not realize that they have given it to you. A virus, which attaches itself to a downloadable file or a link within a phishing email, unravels the road into someone's personal computer, letting you attain access to the contents contained within it. A much simpler and safer method, though, is to simply use an invisible third-party hacking tool such as MoniVisor by ClevGuard in order to not get caught or waste too much time.
How to gain access to someone's computer?
To gain access to someone's computer, you'll need their password. If you don't have it, but you have physical access to the computer, you can reset it to gain access. If you're using Windows, you can do this by creating a Windows installation drive or DVD and booting the target computer from that drive. When the computer boots up, you'll back up the Sticky Keys accessibility feature, and then replace Sticky Keys with the command prompt. After booting into Safe Mode from there, you can press Shift 5 times to open a command prompt (instead of Sticky Keys). Use the command prompt to create a new user account and add them to the administrator group. Then you can log in to the computer with your new administrator account.
How does a hacker use malware?
Although most modern hacking requires some form of physical access to the computer in question, some hacking techniques use malware sent via an email to create a vulnerability in the other computer.
How to connect to another computer?
Connect to the target computer from your computer. Enter the target computer's ID in the "Partner ID" text box, click CONNECT, enter the password when prompted, and click Log On. Doing so will allow you to access remotely the other computer whenever you like.
How to restart a Mac?
Click Restart. You'll find this option at the bottom of the screen. Clicking it prompts your Mac to begin restarting; when it completes, you'll be back at the login screen.
Can I hack a phone with Kali Linux?
It depends. On an Android, yes, but you would have to root your phone which would void any warranty. If you don't care about that, once the phone is rooted, you can install a variety of hacking tools via Kali Linux. There is a lot of messing around involved so I wouldn't recommend it to a beginner or someone who has never rooted a phone, as doing so incorrectly can brick the device.
Is it illegal to hack a computer without permission?
Hacking without explicit permission from the computer owner is illegal, and can result in anything from a school suspension to fines and jail time.
Can you reset your administrator password with sticky keys?
Understand what this will accomplish. This method covers manipulating the Sticky Keys accessibility feature of Windows, which allows you to reset the Windows administrator password. This should still work as of 2021. You'll need a Windows 10 installation DVD or USB drive, either of which you can create on a PC you do have access to.
What are remote hackers?
With the rise of a remote working population, “remote hackers” have been re-emerging as well. These remote hackers take advantage of remote working technologies like video conferencing tools, enterprise VPNs, and other remote access solutions that have become popular during the COVID-19 crisis.
How do remote hackers reach unsuspecting victims?
Remote hackers use various malware deployment methods; the most common (and probably the easiest) way for hackers to reach unsuspecting victims is through phishing campaigns.
What are hackers exploiting?
While hackers are exploiting the vulnerabilities found in actual solutions like business VPNs and RDP to gain access to the company network, they are using traditional tactics to target remote employees.
Why do VPNs run 24/7?
VPNs run 24/7, which means organizations are less likely to check for and apply security patches on a regular basis. This also makes VPNs vulnerable and susceptible to attacks by hackers. For instance, hackers may start a phishing campaign to target remote employees in order to steal their usernames and passwords that gives them access to the VPN, and by extension, your network.
Can malware be executed on a client?
The malware is then executed within the client — the victim’s device; the compromised device is left open to the hackers so they can access the private network directly. Hackers may also try to instill the use of macros within Excel or Word docs to execute malware and take over a PC.
Can hackers steal your credentials?
Hackers with stolen credentials in hand (acquired through brute force or other malicious ways) may exploit this port to gain access to the internal network of a company or organization. Just as hackers can steal the login credentials for corporate VPNs , hackers can also acquire the ID/PWs of RDP users too.
How to stop RDP exploitation?
You just have to disable the remote access when not in use and limit the users.
How does the RDP is exploited?
Generally, the RDP hack happens because of the victim’s lack of awareness and loosely configured RDP on its system. If the system is connected to the internet and is listening for an RDP signal, it will respond if a remote user asks it is active. The remote user will then be provided a login screen of the victim’s desktop without letting the victim know anything about it. The attacker would be asked to enter the password for getting remote access through RDP. If the victim’s RDP is poorly configured, i.e., no strong password is enabled, then it would be easy for the intruder to get remote access to the system.
How to check if you have RDP enabled?
First thing is to know if you have RDP enabled. That’s easy to check from your Control Panel under System > Remote Settings > Remote Desktop (under Windows 7, other operating systems vary).
What can RDP intruders do?
What can RDP intruders do? If you have administrative privileges assigned to the user they login as, they can take your computer for an unfettered spin around the block, ranging from turning it off, rebooting it, installing software (including malware), or just having a look around to find documents of files with your critical personal information in them like banking, accounting, or other information and then spirit them off across the network to their own computers for nefarious purposes.
What port is listening to RDP?
If your computer is “listening” for an RDP signal (typically over port TCP 3389), and it is connected to the Internet, it will respond when a remote user asks it if it’s alive.
Can a remote attacker access my computer as administrator?
When remote attackers come calling this could pose problems for an unwitting user who is logged in as Administrator. Very likely the bad guys will be looking to gain elevated access, and logging in as Administrator is a quick way to do that. If they can pair that valid User with an easy-to-guess password, they’ve got the keys to your computer’s crown jewels.
Can malware be installed via RDP?
Lately, we’ve seen an increase in reports of malware being installed via Remote Desktop Protocol (RDP). This is the powerful protocol which has been letting you view a Windows desktop “over the wire” on the other side of the globe (or back at your home from the office) for over a decade now. Sadly, while RDP can serve a variety of useful purposes ranging from remote “hands-on” support to configuring and running servers, in the wrong hands it can be a remote control weapon that enables bad actors to zombify your computer and have it do their bidding.
How to stop someone from accessing my computer?
This includes removing any Ethernet cables and turning off your Wi-Fi connections.
How to install antivirus on another computer?
If you don't have an antivirus, download an installer on another computer and transfer it to your computer via USB. Install the antivirus and then run a scan with it.
How to know if malware has been removed?
Monitor your computer after removing any malware. If your antivirus and/or Anti-Malware found malicious programs, you may have successfully removed the infection, but you'll need to keep a close eye on your computer to ensure that the infection hasn't remained hidden.
What to do if your computer is compromised?
Change all of your passwords . If your computer was compromised, then there’s a possibility that all of your passwords have been recorded with a keylogger. If you’re sure the infection is gone, change the passwords for all of your various accounts. You should avoid using the same password for multiple services.
How to scan for malware on Windows 10?
If you're using Windows 10, you can use the built-in scanning tools in Settings > Update & Security > Windows Security to check for rogue applications. If you're using a Mac, check out How to Scan a Mac for Malware to learn how to use Mac-based scanning tools.
Why is public Wi-Fi so dangerous?
Try to avoid public Wi-Fi spots. Public Wi-Fi spots are risky because you have zero control over the network. You can't know if someone else using the spot is monitoring traffic to and from your computer. By doing this, they could gain access to your open browser session or worse. You can mitigate this risk by using a VPN whenever you are connected to a public Wi-Fi spot, which will encrypt your transfers.
What to do if you can't get rid of intrusion?
If you're still experiencing intrusions, or are concerned that you may still be infected, the only way to be sure is to completely wipe your system and reinstall your operating system.
What is unauthorized access?
"Unauthorized access" entails approaching, trespassing within, communicating with, storing data in, retrieving data from, or otherwise intercepting and changing computer resources without consent. These laws relate to these and other actions that interfere with computers, systems, programs or networks.
What are the types of computer crimes?
Some state laws also directly address other specific types of computer crime, such as spyware, phishing, denial of service attacks, and ransomware, as shown below. Computer crime laws encompass a variety of actions that destroy or interfere with normal operation of a computer system. Computer trespass, unauthorized access (or access exceeding ...
What is ransomware 2021?
Ransomware is computer malware that is installed covertly on a victim's computer and preventing access to it, followed by demands for a ransom payment in exchange for returning access or not publishing or exposing data held on the computer.
What is the prohibition on ransomware?
Prohibits a person from knowingly possessing certain ransomware with the intent to use the ransomware for purposes of introduction into a computer, network or system of another person, alters and establishes certain penalties, authorizes a victim of a certain offense to bring a civil action for damages against a certain person. (2021 H.B. 425 / 2021 S.B. 623)
What is spyware on a computer?
Spyware, also sometimes called adware, is software that can track or collect the online activities or personal information of Web users, change settings on users’ computers, or cause advertising messages to pop up on users' computer screens. Web users are often unaware that spyware has been downloaded to their computers.
What is malware and virus?
Malware and viruses (viruses are a type of malware) are a set of computer instructions that are designed to modify, damage, destroy, record, or transmit information within a computer system or network without the permission of the owner. Generally, they are designed to infect other computer programs or computer data, consume resources, modify, ...
What is a computer virus?
Generally, they are designed to infect other computer programs or computer data, consume resources, modify, destroy, record or transmit data, and disrupt normal operation of a computer system.