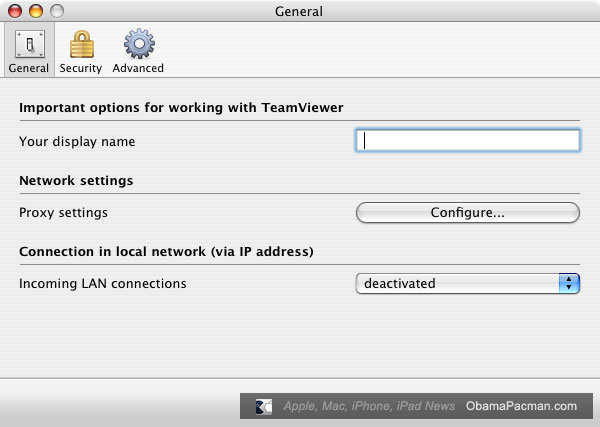
Most legitimate remote access programs are made for tech support and file sharing purposes, while RATs are made for spying on, hijacking, or destroying computers. Like most malware, RATs piggyback on legitimate-looking files. Hackers can attach a RAT to a document in an email, or within a large software package, like a video game.
Full Answer
What is remote access hacking and how does it work?
These remote hackers take advantage of remote working technologies like video conferencing tools, enterprise VPNs, and other remote access solutions that have become popular during the COVID-19 crisis. Here are ways bad actors can use remote access hacking opportunities to hack into remote access tools, steal sensitive data, and disrupt businesses.
Are hackers using VPNs to target remote employees?
While hackers are exploiting the vulnerabilities found in actual solutions like business VPNs and RDP to gain access to the company network, they are using traditional tactics to target remote employees.
How do bad actors use remote access hacking opportunities?
Here are ways bad actors can use remote access hacking opportunities to hack into remote access tools, steal sensitive data, and disrupt businesses. Companies and organizations that had to quickly mobilize for remote working environments have also had to deploy new networks such as VPNs.
How do hackers attack computers remotely?
Hackers typically sneak remotely into the networks of their victims by setting up phishing scams and duping users into downloading malware-ridden files, which are then executed to commence a cyberattack like ransomware. They may also look for vulnerabilities in computer systems to attempt to get into a network.

What is hacking and remote access?
Remote desktop hacks become a common way for hackers to access valuable password and system information on networks that rely on RDP to function. Malicious… Remote desktop hacks become a common way for hackers to access valuable password and system information on networks that rely on RDP to function.
Do hackers use remote access?
Remote Desktop Protocol (RDP) has been known since 2016 as a way to attack some computers and networks. Malicious cyber actors, hackers, have developed methods of identifying and exploiting vulnerable RDP sessions via the Internet to steal identities, login credentials and install and launch ransomeware attacks.
What are the 4 types of hacking?
4 different types of hackersScript Kiddies. When it comes to skill level, Script Kiddies are at the bottom of the totem pole and often use scripts or other automated tools they did not write themselves - hence the name. ... Hacktivist. ... Cyber Criminals. ... Insiders.
What is the difference between hacking and unauthorized access?
Hacking can be described as gaining unauthorised access to a computer system by improper means. Unauthorised access can be describes as gaining access to a computer system using usual means of access but without consent.
What can hackers do remotely?
And in fact, no industry is safe from remote hackers.4 Common Types of Remote Attacks. ... Domain Name System (DNS) Poisoning. ... Port Scanning. ... Password Spraying. ... Phishing. ... Virtual Private Network (VPN) Attacks. ... Remote Desktop Protocol (RDP) Hacks. ... Remote Access Trojans (RAT)
Can hackers take control of your PC?
Your computer can be used to attack other computers. Sometimes hackers will take over a computer, sometimes thousands of them, to launch an attack on a website they've targeted.
Who is the No 1 hacker in world?
Kevin Mitnick is the world's authority on hacking, social engineering, and security awareness training. In fact, the world's most used computer-based end-user security awareness training suite bears his name. Kevin's keynote presentations are one part magic show, one part education, and all parts entertaining.
Are hackers intelligent?
The simple answer is, yes, they are. The very definition of a hacker is that you find new and innovative ways to attack systems – their very job is to get smarter.
What is a professional hacker called?
An ethical hacker, also referred to as a white hat hacker, is an information security (infosec) expert who penetrates a computer system, network, application or other computing resource on behalf of its owners -- and with their authorization.
What's the difference between cracking and hacking?
Hackers are people who use their knowledge for a good purpose and do not damage the data, whereas a cracker is someone who breaks into the system with a malicious purpose and damages data intentionally.
What is the legal definition of hacking?
Hacking is broadly defined as the act of breaking into a computer system. Hacking isn't always a crime as "ethical hacking" occurs when a hacker is legally permitted to exploit security networks. In other words, it's when a hacker has the appropriate consent or authorization.
What is the difference between hacking and hacker?
Hacking is to gain unauthorized access to data, information, system, or resources. Hackers are people with technical skills who manipulate data to control networks with intention to breach and steal sensitive data.
Do hackers use AnyDesk?
Sophos discovered that the AvosLocker attackers installed AnyDesk so it works in Safe Mode, tried to disable the components of security solutions that run in Safe Mode, and then ran the ransomware in Safe Mode.
How do hackers get access to your computer?
Access to a corporate or public wifi network allows hackers to carry out various operations such as sniffing users' credentials, executing a man-in-the-middle attack, and even redirecting victims to malicious websites for further compromise. People often associate computer hacking with compromising a system remotely.
What is hacking
Hacking is the act of compromising digital devices and networks by gaining unauthorized access to an account or computer system.
What are the seven types of hackers?
There are many different types of hackers, the most common of which are black, grey, and white hat hackers. Black hat hackers are the bad guys—the...
What is the biggest hack in history?
The biggest hack in history is thought to be the data breach against Yahoo! The 2013 attack compromised around 3 billion people, and the company re...
What is remote access software?
Remote access software allows a computer’s desktop environment to be run remotely on one system while being displayed on a separate client device. Many organizations find remote access software extremely useful.
Why is it important to choose a strong password for remote access?
It’s extremely important for businesses to choose a strong password for their remote access accounts. If the RDP is exposed to the Internet, a simple network engine can allow hackers to poke around the network and use various methods like brute force attacks to try and guess the password. Once inside the system, it’s only a matter of time before they acquire access information needed to infiltrate other critical systems.
How Do Hackers Gain Access?
There are several ways hackers can gain access to a network remotely using this software: lack of governance for installing remote access software and weak remote access account passwords. If a company’s employees are unaware that they’ve installed remote access software on company devices, then there is potential for abuse as it increases the risk of hackers finding a backdoor.
What is fileless attack?
Previously, we discussed fileless attacks, an increasingly popular method used by hackers to spread ransomware that sometimes involves exploiting the macro functionality in Microsoft Office documents. Now, it appears that another exploitable entry point has been on the rise: remote access software.
Why were the WannaCry and NotPetya attacks successful?
Both the WannaCry and NotPetya attacks, for example, were successful because hackers used leaked NSA exploits to infect older computer operating systems.
What is RDP hacking?
Hackers are getting more and more creative in their hacking methods, and using the RDP is one way they can make their way into a company’s network. In fact, Naked Security recently reported on a growing trend of hackers spreading ransomware by accessing computer systems through the RDP.
How do hackers sneak into a network?
Hackers typically sneak remotely into the networks of their victims by setting up phishing scams and duping users into downloading malware-ridden files, which are then executed to commence a cyberattack like ransomware. They may also look for vulnerabilities in computer systems to attempt to get into a network.
What are the dangers of car computers?
These ECUs connect to one another and to the Internet, making car computers as vulnerable to the same digital dangers widely known among PCs and other networked devices: viruses, Trojans, denial-of-service attacks and more.
Is it dangerous to hack a car?
Although most experts agree there isn't an immediate risk, vehicle hacking is something that bears watching.
Can a hacker disable a vehicle?
A malicious hacker could, in theory, disable the vehicles, re-route GPS signals or otherwise put employees, customers and the company as a whole in danger. Consumers are getting worried about the safety and privacy risks that come with today's connected cars, according to a Harris Interactive poll released last week.
What is hacking in computer terms?
Hacking refers to the misuse of devices like computers, smartphones, tablets, and networks to cause damage to or corrupt systems, gather information on users, steal data and documents, or disrupt data-related activity. A traditional view of hackers is a lone rogue programmer who is highly skilled in coding and modifying computer software ...
What is a hacker?
A traditional view of hackers is a lone rogue programmer who is highly skilled in coding and modifying computer software and hardware systems. But this narrow view does not cover the true technical nature of hacking. Hackers are increasingly growing in sophistication, using stealthy attack methods designed to go completely unnoticed by cybersecurity software and IT teams. They are also highly skilled in creating attack vectors that trick users into opening malicious attachments or links and freely giving up their sensitive personal data.
What is Ethical Hacking? How Legal is Ethical Hacking?
Using these technical skills for ethical hacking purposes is legal, provided the individual has written permission from the system or network owner, protects the organization’s privacy, and reports all weaknesses they find to the organization and its vendors.
Why are webcams a target for hackers?
Webcams built into computers are a common hacking target, mainly because hacking them is a simple process. Hackers typically gain access to a computer using a Remote Access Trojan (RAT) in rootkit malware, which allows them to not only spy on users but also read their messages, see their browsing activity, take screenshots, and hijack their webcam.
What is a hacker router?
Hacking routers enables an attacker to gain access to data sent and received across them and networks that are accessed on them. Hackers can also hijack a router to carry out wider malicious acts such as distributed denial-of-service (DDoS) attacks, Domain Name System (DNS) spoofing, or cryptomining.
What is the act of compromising digital devices and networks by gaining unauthorized access to an account or computer system?
Hacking is the act of compromising digital devices and networks by gaining unauthorized access to an account or computer system.
What does it mean to jailbreak a phone?
Jailbreaking a phone means removing restrictions imposed on its operating system to enable the user to install applications or other software not available through its official app store. Aside from being a violation of the end-user’s license agreement with the phone developer, jailbreaking exposes many vulnerabilities. Hackers can target jailbroken phones, which allows them to steal any data on the device but also extend their attack to connected networks and systems.
Why is Hacker’s Door an Important Issue and Why Should I be Concerned?
Hacker’s Door is a good example of “commoditized” malware – being sold in private markets by the original author and providing updates so that the malware can continue to run.
What is hacker door?
Hacker’s Door is a remote access trojan that has been around for many years. However, it has resurfaced and Cylance employees discovered it as part of recent compromise assessment engagement.
What is remote access in Linux?
Remote access is defined as gaining access via the network (for example, a listening service) or other communication channel. Local access is defined as having an actual command shell or login to the system. Local access attacks are also referred to as privilege escalation attacks. It is important to understand the relationship between remote and local access. Attackers follow a logical progression, remotely exploiting a vulnerability in a listening service and then gaining local shell access. Once shell access is obtained, the attackers are considered to be local on the system. We try to logically break out the types of attacks that are used to gain remote access and provide relevant examples. Once remote access is obtained, we explain common ways attackers escalate their local privileges to root. Finally, we explain information-gathering techniques that allow attackers to garner information about the local system so that it can be used as a staging point for additional attacks. It is important to remember that this chapter is not a comprehensive book on UNIX security. For that we refer you to Practical UNIX & Internet Security , by Simson Garfinkel and Gene Spafford (O'Reilly, 2003). Additionally, this chapter cannot cover every conceivable UNIX exploit and flavor of UNIX. That would be a book in itself. In fact, an entire book has been dedicated to hacking Linux Hacking Linux Exposed , by Brian Hatch, James Lee, and George Kurtz (Osborne/McGraw-Hill, 2001). Rather, we aim to categorize these attacks and to explain the theory behind them. Thus, when a new attack is discovered , it will be easy for you to understand how it works, even though it was not specifically covered. We take the "teach a man to fish and feed him for life" approach rather than the "feed him for a day" approach.
What is local access?
Local access is defined as having an actual command shell or login to the system. Local access attacks are also referred to as privilege escalation attacks. It is important to understand the relationship between remote and local access.
Who wrote the book Hacking Linux Exposed?
In fact, an entire book has been dedicated to hacking Linux Hacking Linux Exposed , by Brian Hatch, James Lee, and George Kurtz (Osborne/McGraw-Hill, 2001). Rather, we aim to categorize these attacks and to explain the theory behind them.
What is the logical progression of an attacker?
Attackers follow a logical progression, remotely exploiting a vulnerability in a listening service and then gaining local shell access. Once shell access is obtained, the attackers are considered to be local on the system.
How does the RDP is exploited?
Generally, the RDP hack happens because of the victim’s lack of awareness and loosely configured RDP on its system. If the system is connected to the internet and is listening for an RDP signal, it will respond if a remote user asks it is active. The remote user will then be provided a login screen of the victim’s desktop without letting the victim know anything about it. The attacker would be asked to enter the password for getting remote access through RDP. If the victim’s RDP is poorly configured, i.e., no strong password is enabled, then it would be easy for the intruder to get remote access to the system.
How to stop RDP exploitation?
You just have to disable the remote access when not in use and limit the users.
What is remote access tool?
Remote Access Tool is a piece of software used to remotely access or control a computer. This tool can be used legitimately by system administrators for accessing the client computers. Remote Access tools, when used for malicious purposes, are known as a Remote Access Trojan (RAT). They can be used by a malicious user to control the system without the knowledge of the victim. Most of the popular RATs are capable of performing key logging, screen and camera capture, file access, code execution, registry management, password sniffing etc.
How can an attacker remotely control a system?
An attacker can remotely control the system by gaining the key logs, webcam feeds, audio footage, screen captures, etc . RATs normally obfuscate their presence by changing the name, size, and often their behavior or encryption methods. By doing this they evade from AV, firewalls, IDS, IPS and security defense systems.
What is Bandook RAT?
Bandook RAT has the ability of process injection, API unhooking, bypass the Windows firewall etc. In this, the client has the ability to extend the functionality of the server by sending plugin code to it. The server has capability to hide it by creating a process using the default browser settings.
What is B02K client interface?
B02K client interface has a list of servers that displays the list of compromised servers and this server has its name, IP address, and connection information. Several commands can be used to gather data from victim machine and this command can be executed using the attacker machine by giving the intended parameters. The responses can be seen using the Server Response window.
How is malware delivered?
The malware is delivered via spear phishing emails, or drive-by downloads. The attackers are also embedding the malware in other applications such as the L517 Word List Generator; the malware is compressed and obfuscated by a number of tools in order to avoid detection by security software.
What is B02K configuration?
B02K has a configuration interface, which can be used to setup the functionality of the program. The configuration interface can be used to setup the Server file, network protocol including TCP or UDP, Port number, encryption mechanism, and password encryption key.
What is network based detection?
In network based detection method, the network communication protocols can be monitored to check whether if any deviation is there in the behavior of network usage. Ports can be monitored for exceptional behavior, and can analyze protocol headers of packet among the systems. The network traffic can be analyzed and the RAT behavior patterns can distinguished among other legitimate traffic.