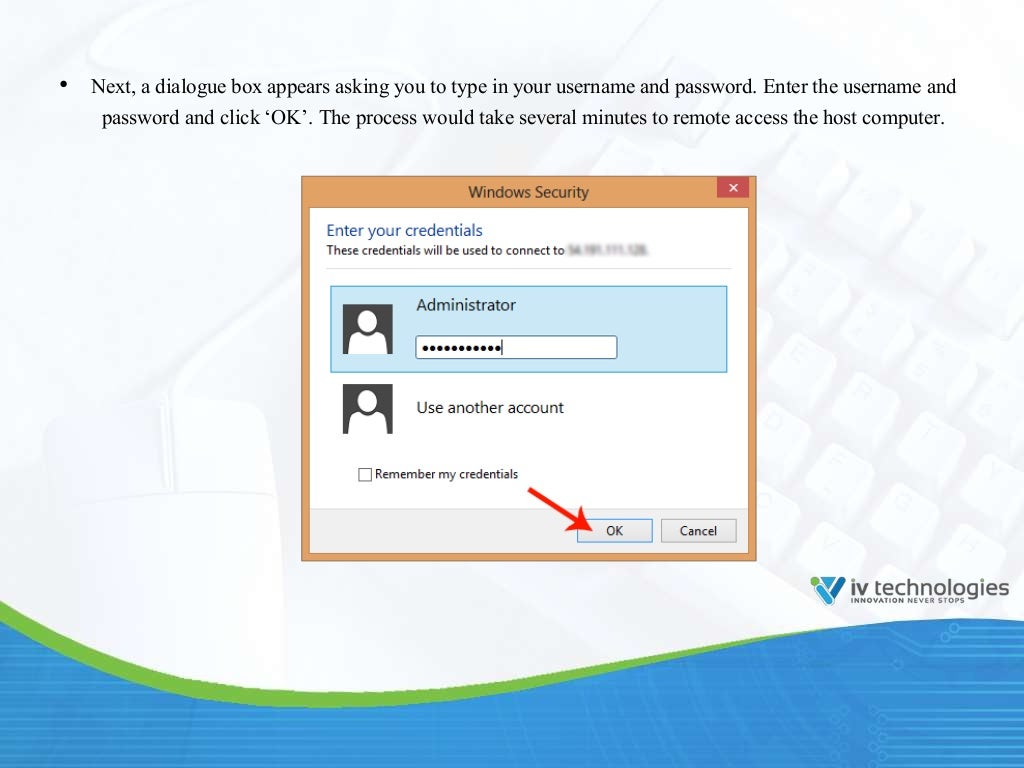
What is the best free Remote Access Software for Windows?
Remote Utilities is a free remote access program with some really great features. It works by pairing two remote computers together with an Internet ID. Control a total of 10 computers with this program. Install Host on a Windows computer to gain permanent access to it.
How to remotely access a computer for free?
AeroAdmin is probably the easiest program to use for free remote access. There are hardly any settings, and everything is quick and to the point, which is perfect for spontaneous support. Just open the portable program and share your IP address or the given ID with someone else. This is how the client computer will know how to connect to the host.
How do I use showmypc remote access?
ShowMyPC is a portable and free remote access program that's similar to some of these other programs but uses a password to make a connection instead of an IP address. Host Side Run the ShowMyPC software on any computer and then choose Show My PC to get a unique ID number called a Share Password .
What is illegal remote access (hacking)?
#2) Illegal remote access (hacking) refers to the unintended manipulation of data or files on your computer. If you have any malicious software such as Trojan on your system, then it is an open invitation to the hacker to get access to it. Hacker can add, delete or modify your files without your consent on his own.

How can I tell if someone has remote access to my computer?
How to Know If Someone is Accessing My Computer Remotely?Way 1: Disconnect Your Computer From the Internet.Way 2. ... Way 3: Check Your Browser History on The Computer.Way 4: Check Recently Modified Files.Way 5: Check Your computer's Login Events.Way 6: Use the Task Manager to Detect Remote Access.More items...•
How do I hide remote access?
Windows 8 and 7 InstructionsClick the Start button and then Control Panel.Open System and Security.Choose System in the right panel.Select Remote Settings from the left pane to open the System Properties dialog box for the Remote tab.Click Don't Allow Connections to This Computer and then click OK.More items...•
Can someone access my PC remotely without me knowing?
There are two ways someone can access your computer without your consent. Either a family member or work college is physically logging in to your computer or phone when you are not around, or someone is accessing your computer remotely.
What software is used to control someone else's computer screen?
Microsoft Remote Desktop Microsoft Remote Desktop is the native Windows screen-sharing solution. It uses the propriety Remote Desktop Protocol (RDP) technology.
Is my phone being remotely accessed?
How to Tell Someone Is Accessing Your Phone Remotely. Here are some signs that someone might have unauthorized access to your smartphone: Unknown apps are running in the background. Your phone has an increased closing time and is slower overall.
How do I disable Remote Assistance services?
Click the Remote tab. Under the "Remote Assistance" section, clear the Allow Remote Assistance connection to this computer option.
How can I tell if my computer is being monitored at work 2022?
Open task manager by right-clicking on the taskbar and choosing Task Manager. If there's a suspicious process, that's the monitoring app. Question: Can my company see what I do on my computer? Answer: Your company can see your device activities and track them if they provide you with that computer.
How do I know if someone is using TeamViewer on my computer?
Best Answer Just click in your TeamViewer on Extras --> Open Logfiles. In the same folder, there should be a file called connections_incoming. txt. In this file, you find the information you are looking for.
What is Remoteit?
What is remote.it? The remote.it Virtual Private Internet allows removal of global IP addresses and open ports, leaving a zero attack surface, while simultaneously solving the scarcity of global IPv4 addresses.
How can I remotely access someones computer?
Important: Make sure you're using the latest version of the Chrome Remote Desktop app.On your Android phone or tablet, open the Chrome Remote Desktop app. . ... Tap the computer you want to access from the list. If a computer is dimmed, it's offline or unavailable.You can control the computer in two different modes.
How do I access another computer on the same network?
Access other computersOpen File Explorer.In the Navigation pane on the left, click 'Network'.You will see all devices that are connected to the network. ... If prompted, enter the username and password that will grant you access to the system.You will see the Users folder and have access to select files.
How do I hide TeamViewer when connected?
Under the TeamViewer Options, Advanced, enable "Automatically minimize local TeamViewer Panel".
How do I hide the remote desktop bar in Chrome?
0:010:52How to hide the connection bar in Remote Desktop on Windows 10YouTubeStart of suggested clipEnd of suggested clipSo what we're going to do is go to the show options before we connect to our remote desktopMoreSo what we're going to do is go to the show options before we connect to our remote desktop connection go to display.
How do I hide the remote utility icon?
You cannot hide the tray icon itself, it's always there. This is because Remote Utilities is legitimate software for remote administration and support and must reveal itself in the system for the remote user. Otherwise, antivirus/security software may erroneously detect and remove it.
How do I hide my IP address on Remote Desktop?
0:312:08Hide Your Remote Desktop Session Names | MSTSC /public - YouTubeYouTubeStart of suggested clipEnd of suggested clipAnd it won't have like your dynamic DNS or your IP address or whatever so the way to do this youMoreAnd it won't have like your dynamic DNS or your IP address or whatever so the way to do this you just go to start type in MS TSC. Space which public.
How to access remote computer?
There are a couple of ways to access the remote computer. If you logged in to your account in the host program, then you have permanent access which means you can visit the link below to log in to the same account in a web browser to access the other computer.
How to enable remote desktop access to a computer?
To enable connections to a computer with Windows Remote Desktop, you must open the System Properties settings (accessible via Settings (W11) or Control Panel) and allow remote connections via a particular Windows user.
What is Zoho Assist?
Zoho Assist is yet another remote access tool that has a free edition for both personal and commercial use. You can share screens and files, and chat remotely with the other user through a unique session ID and password.
How to connect to a host browser?
To connect to the host browser, sign on to Chrome Remote Desktop through another web browser using the same Google credentials or using a temporary access code generated by the host computer.
How does remote utility work?
It works by pairing two remote computers together with an Internet ID. Control a total of 10 computers with Remote Utilities.
What is the other program in a host?
The other program, called Viewer, is installed for the client to connect to the host. Once the host computer has produced an ID, the client should enter it from the Connect by ID option in the Connection menu to establish a remote connection to the other computer.
What is the easiest program to use for remote access?
AeroAdmin is probably the easiest program to use for free remote access. There are hardly any settings, and everything is quick and to the point, which is perfect for spontaneous support.
How to stop someone from accessing my computer?
This includes removing any Ethernet cables and turning off your Wi-Fi connections.
How to install antivirus on another computer?
If you don't have an antivirus, download an installer on another computer and transfer it to your computer via USB. Install the antivirus and then run a scan with it.
How to know if malware has been removed?
Monitor your computer after removing any malware. If your antivirus and/or Anti-Malware found malicious programs, you may have successfully removed the infection, but you'll need to keep a close eye on your computer to ensure that the infection hasn't remained hidden.
What to do if your computer is compromised?
Change all of your passwords . If your computer was compromised, then there’s a possibility that all of your passwords have been recorded with a keylogger. If you’re sure the infection is gone, change the passwords for all of your various accounts. You should avoid using the same password for multiple services.
How to scan for malware on Windows 10?
If you're using Windows 10, you can use the built-in scanning tools in Settings > Update & Security > Windows Security to check for rogue applications. If you're using a Mac, check out How to Scan a Mac for Malware to learn how to use Mac-based scanning tools.
What to do if you can't get rid of intrusion?
If you're still experiencing intrusions, or are concerned that you may still be infected, the only way to be sure is to completely wipe your system and reinstall your operating system.
How to find out what is running on my computer?
Open your Task Manager or Activity Monitor. These utilities can help you determine what is currently running on your computer.
What Is Remote Access Software?
Remote access software lets one computer view or control another computer, not merely across a network, but from anywhere in the world. You might use it to log into your customers' computers and show them how to run a program, or sort out their technical troubles. Or you can even use it to invite friends or clients to view your desktop while you run a demo for them. You can use the screen as a temporary whiteboard, drawing lines and circles that help friends or clients understand what you're doing on your machine or theirs.
What is remote PC?
RemotePC is one of the best low-frills remote-access apps, offering identical features on PCs and Macs, fast performance, and a minimal, but intuitive, interface .
What is Logmein software?
LogMeIn is a solid, straightforward remote access and file-sharing software that's suitable for personal or corporate use .
What is GoToMyPC?
GoToMyPC is a mature, easy-to-use remote access software with the best available balance between features and ease of use. Unless you need support for Linux or enterprise-level operating systems, this is the app you want.
Is VNC Connect secure?
VNC Connect is solid, secure, and simple to use, once you get the hang of it. It has fewer features than other corporate-level remote access software, but it's also a lot less expensive.
Does GoToMyPC work with TeamViewer?
GoToMyPC and LogMeIn add the ability to drag and drop files between the local desktop and the viewer window that displays the desktop of the remote machine, but this feature works only when connecting to and from Windows computers. TeamViewer has a FileBox window into which you can drag files that will be accessible to both machines. LogMeIn, TeamViewer, and VNC Connect include whiteboard features for drawing lines in the viewer. For more on each remote access apps individual features, see the individual reviews, which are linked to below.
What is remote access?
Remote Access is the process of accessing your system from a remote location. When you are not physically near to a system to access it, then you can make use of remote administration to do so. In this process, the remote location may be in the next room, next building or anywhere worldwide.
What is remote administration service?
If the person is not at your place, he can make use of remote administration services to access your system by establishing a secure session between your system and the remote server. They are used to access multiple systems at a given team session to handle multiple tasks with multiple business entities.
What is Solarwinds Dameware Remote Support?
SolarWinds Dameware Remote Support is an easy-to-use package of remote control and systems management tools.
What is Cybergate spyware?
CyberGate is a fully configurable and Delphi coded spyware which is popular to crack your passwords. Using this software one can crack the user’s passwords and can view his screen. You can connect to several systems at the same time just by spreading the server file.
What is alienspy attack?
Alienspy uses phishing attack and sends payload link to the victim’s mailbox.
What is Supremo software?
Supremo is a software for remote desktop access, allowing connection and control of PCs and servers running on Windows, macOS, Linux and also available for mobile on Android and iOS. In terms of security, the data flow is encrypted, at each connection, a new random password is generated and you can also set up access to your PC from specific IDs ...
What is a remote access computer?
Virtual network computing (VNC) is another method you can use to access a remote computer, but it’s definitely not the most user-friendly option. Unlike TeamViewer or Chrome, VNC requires a fair amount of setup. You have to configure ports, set up a static IP or use dynamic DNS, and deal with the security implications of not using encryption.
How to remotely access a machine?
Remote access requires that you install an “agent” on the machine you want to control. You have to do this bit in person, so you’ll have to set this up before you leave the office or wherever the machine to which you want to remotely connect is located.
How to get TeamViewer on my computer?
To get started, download the TeamViewer app on the computer you want to access. For ease of use, it’s best to set up a TeamViewer account and log in. In the main client window, click “Set up unattended access,” and then follow the steps to finalize it. You might want to check the “Start TeamViewer with System” box just in case your machine restarts.
Why use Anydesk over TeamViewer?
The main reason to choose AnyDesk over TeamViewer is its focus on slower connections. The app uses a proprietary codec that AnyDesk promises “ensures low lag, even at high screen resolutions or bandwidths of just 100 kB/s.”
How to access remote desktop?
For this to work, you have to use the Chrome browser on both computers and be logged in to a Google account. You’ll also need to set up the Remote Access extension on any computers you want to access.
How to access my computer remotely from Chrome?
To access your remote machine, head over to remotedesktop.google.com/access, and then click the machine in question.
How long does it take to set up a remote desktop?
Remote-access tools allow you to use a computer that’s located elsewhere as if you were sitting in front of it. Most remote desktop solutions only take a few minutes to set up. Plus, as long as the remote computer remains online, the connection should work indefinitely.
What Is Windows Spy Software?
SPYERA Windows spy software is an application that you install onto a PC to supervise the processes and activities that take place on a particular machine or computer network.
What is the only undetectable monitoring software for Windows?
SPYERA is the only completely undetectable monitoring software for Windows. We design, develop and support all our products since 1999.
What is a Windows monitoring software?
Windows computer monitoring software is an application that you install on to a Windows PC to supervise the processes and activities that take place on a particular machine or computer network without any evidence. GET STARTED. eye-slash.
Does Spyera run in the background?
SPYERA gives you the option to run the software visible or hidden mode. No other software gives you this options. SPYERA runs in the background without any evidence. It is the only 100% invisible Windows Spy Software on the market. It does not harm performance or battery drain.
What can a hacker do with a RAT?
A hacker with a RAT can command power stations, telephone networks, nuclear facilities, or gas pipelines. RATs not only represent a corporate network security risk, but they can also enable belligerent nations to cripple an enemy country.
What is SIEM in security?
This dual capability gives you a full Security Information and Event Management (SIEM) service. This means that you can watch Snort-captured events live and also examine cross-packet intrusion signatures identified through log file records.
What is intrusion detection?
Intrusion detection systems are important tools for blocking software intrusion that can evade detection by antivirus software and firewall utilities. The SolarWinds Security Event Manager is a Host-based Intrusion Detection System. However, there is a section of the tool that works as a Network-based Intrusion Detection System. This is the Snort Log Analyzer. You can read more about Snort below, however, you should know here that it is a widely used packet sniffer. By employing Snort as a data collector to feed into the Snort Log Analyzer, you get both real-time and historic data analysis out of the Security Event Manager.
How to get rid of a RAT?
Sometimes, the only solution to rid your computer of a RAT is to wipe out all of your software and reinstall the operating system. RAT prevention systems are rare because the RAT software can only be identified once it is operating on your system.
Where is the server software stored?
The server software is stored in C:WindowsBifrostserver.exe or C:Program Files Bifrostserver.exe. This directory and file are hidden and so some anti-virus system checks fail to detect Bifrost.
Can antivirus be used to get rid of a RAT?
Antivirus systems don’t do very well against RATs. Often the infection of a computer or network goes undetected for years. The obfuscation methods used by parallel programs to cloak the RAT procedures make them very difficult to spot. Persistence modules that use rootkit techniques mean that RATs are very difficult to get rid of. Sometimes, the only solution to rid your computer of a RAT is to wipe out all of your software and reinstall the operating system.
Can a hacker use your internet address?
The hacker might also be using your internet address as a front for illegal activities, impersonating you, and attacking other computers. Viruses downloaded through RAT will infect other computers, while also causing damage to your system by erasing or encryption essential software.