
robust remote access solution that supports HIPAA
Health Insurance Portability and Accountability Act
The Health Insurance Portability and Accountability Act of 1996 was enacted by the 104th United States Congress and signed by President Bill Clinton in 1996. It was created primarily to modernize the flow of healthcare information, stipulate how Personally Identifiable Information maintained by the healthcare and healthcare insurance industries should be protected from fraud and theft, and address lim…
Is working remotely a HIPAA compliance risk?
While there are several advantages of working remotely, there’s a monstrous risk for those that are obligated to comply with HIPAA: keeping clients’ protected health information (PHI) safe. Not convinced it’s a big deal?
What is the security rule under HIPAA?
Summary of the HIPAA Security Rule. The Security Rule operationalizes the protections contained in the Privacy Rule by addressing the technical and non-technical safeguards that organizations called “covered entities” must put in place to secure individuals’ “electronic protected health information” (e-PHI).
Do the HIPAA rules require a business associate to keep ePHI?
No, the HIPAA Rules generally do not require a business associate to maintain electronic protected health information (ePHI) beyond the time it provides services to a covered entity or business associate.
What is protected health information under HIPAA?
What Information is Protected. Electronic Protected Health Information. The HIPAA Privacy Rule protects the privacy of individually identifiable health information, called protected health information (PHI), as explained in the Privacy Rule and here - PDF.

Is Remote Desktop HIPAA compliant?
Many organizations allow users to access their PCs via windows remote desktop connections by opening a port on the firewall and allowing the user to directly access their office computer from home. This practice is not secure, and is definitely not HIPAA compliant.
What are the 3 HIPAA implementation requirements?
Broadly speaking, the HIPAA Security Rule requires implementation of three types of safeguards: 1) administrative, 2) physical, and 3) technical.
What are the 3 exceptions to HIPAA?
The Three Exceptions to a HIPAA BreachUnintentional Acquisition, Access, or Use. ... Inadvertent Disclosure to an Authorized Person. ... Inability to Retain PHI.
Does HIPAA require VPN?
HIPAA requires healthcare entities, and their business associates, to have safeguards in place to secure protected health information (PHI). Implementing VPN in healthcare provides many of the protections necessary to be HIPAA compliant.
What are the 4 main rules of HIPAA?
The HIPAA Security Rule Standards and Implementation Specifications has four major sections, created to identify relevant security safeguards that help achieve compliance: 1) Physical; 2) Administrative; 3) Technical, and 4) Policies, Procedures, and Documentation Requirements.
What are HIPAA security requirements?
The HIPAA Security Rule requires physicians to protect patients' electronically stored, protected health information (known as “ePHI”) by using appropriate administrative, physical and technical safeguards to ensure the confidentiality, integrity and security of this information.
What information can be shared without violating HIPAA?
Health information such as diagnoses, treatment information, medical test results, and prescription information are considered protected health information under HIPAA, as are national identification numbers and demographic information such as birth dates, gender, ethnicity, and contact and emergency contact ...
What isn't covered by HIPAA?
Here are just a few examples of those who aren't covered under HIPAA but may handle health information: life and long-term insurance companies. workers' compensation insurers, administrative agencies, or employers (unless they are otherwise considered covered entities)
What is not covered by HIPAA privacy Rule?
The Privacy Rule excludes from protected health information employment records that a covered entity maintains in its capacity as an employer and education and certain other records subject to, or defined in, the Family Educational Rights and Privacy Act, 20 U.S.C. §1232g. De-Identified Health Information.
Is Norton VPN HIPAA compliant?
Yes, Norton Antivirus could be an effective tool to support HIPAA compliance. Pairing Norton Antivirus with other security measures creates the privacy that covered entities need for protected health information (PHI).
How do certificates work in the context of a VPN?
All certificates issued by a trusted CA are accepted as valid, so certificates can be added, renewed, and changed without affecting the VPN as long as the actual identity information is correct. The same certificate can be used for any number of VPNs with any number of gateways and VPN clients.
How do SSL VPNs work?
An SSL tunnel VPN allows a web browser to securely access multiple network services that are not just web-based via a tunnel that is under SSL. These services could be proprietary networks or software built for corporate use only that cannot be accessed directly via the internet.
What are the two types of implementation specifications of the HIPAA security Rule?
There are two types of implementation specifications under the HIPAA Security Rule. Implementation specifications include required implementation specifications and addressable implementation specifications.
What is an implementation specification?
An implementation specification is a more detailed description of the method or approach covered entities can use to meet the requirements of a particular standard.
What are the 5 HIPAA standards?
HHS initiated 5 rules to enforce Administrative Simplification: (1) Privacy Rule, (2) Transactions and Code Sets Rule, (3) Security Rule, (4) Unique Identifiers Rule, and (5) Enforcement Rule.
What is HIPAA law?
Though most are very familiar with the Health Insurance Portability and Accountability Act (HIPAA) and its relation to third parties and remote access, we’re going to break it down a bit. HIPAA carries with it data privacy requirements for individuals, organizations, and entities working with patient information.
What should network managers know about patient access?
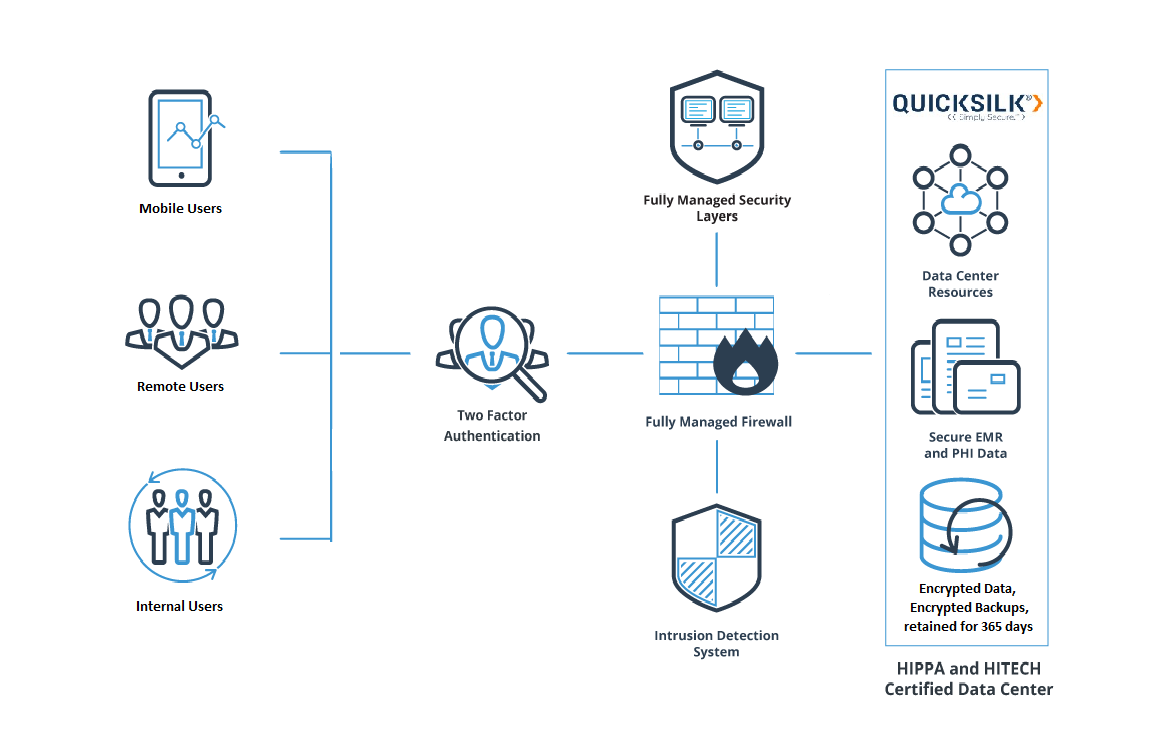
Network managers should always know who has access to patient information, the extent of that access, and how long it’s available. Third-party vendor access should have tight restrictions that limit time, scope and job function. In addition, every remote access session should begin with multi-factor authentication – then all activity must be logged, capturing a unique username and password tied to the individual.
Why is healthcare so heavily targeted for hackers?
The healthcare industry is still heavily targeted for hackers because of the wealth of information they can get. As someone that (I assume) has been to a doctor’s office of any sort, you know how many forms you have to fill out– all the information you have to give, all the releases you have to sign because of HIPAA/HITECH. When we, as patients, sign those papers and agree to hand over this information, we don’t think of all the vendors that might be also accessing that information. It’s imperative that healthcare systems that work with vendors ensure the security of PHI not only for HIPAA compliance, but for patient privacy too.
Is HIPAA compliance required for remote access?
When hospital systems provide remote access to third-party vendors without comprehensive controls, this compliance – and their overall network security – can be jeopardized. A HIPAA-compliant remote access policy isn’t just essential in the healthcare industry, but it’s necessary.
Is remote access required for HIPAA?
A HIPAA compliant remote access policy isn’t just essential in the healthcare industry, but it’s necessary. It’s important to remember that you can’t be in compliance if your vendors (or anyone external who has access to your “stuff”) aren’t compliant, too.
What is the HIPAA Privacy Rule?
With limited exceptions, the HIPAA Privacy Rule (the Privacy Rule) provides individuals with a legal, enforceable right to see and receive copies upon request of the information in their medical and other health records maintained by their health care providers and health plans.
How long does a covered entity have to respond to a HIPAA request?
Under the HIPAA Privacy Rule, a covered entity must act on an individual’s request for access no later than 30 calendar days after receipt of the request. If the covered entity is not able to act within this timeframe, the entity may have up to an additional 30 calendar days, as long as it provides the individual – within that initial 30-day period – with a written statement of the reasons for the delay and the date by which the entity will complete its action on the request. See 45 CFR 164.524 (b) (2).
How long does it take to get a PHI denied?
If the covered entity denies access, in whole or in part, to PHI requested by the individual, the covered entity must provide a denial in writing to the individual no later than within 30 calendar days of the request (or no later than within 60 calendar days if the covered entity notified the individual of an extension). See 45 CFR 164.524 (b) (2). The denial must be in plain language and describe the basis for denial; if applicable, the individual’s right to have the decision reviewed and how to request such a review; and how the individual may submit a complaint to the covered entity or the HHS Office for Civil Rights. See 45 CFR 164.524 (d).
How long does it take to respond to a PHI request?
In providing access to the individual, a covered entity must provide access to the PHI requested, in whole, or in part (if certain access may be denied as explained below), no later than 30 calendar days from receiving the individual’s request. See 45 CFR 164.524 (b) (2). The 30 calendar days is an outer limit and covered entities are encouraged to respond as soon as possible. Indeed, a covered entity may have the capacity to provide individuals with almost instantaneous or very prompt electronic access to the PHI requested through personal health records, web portals, or similar electronic means. Further, individuals may reasonably expect a covered entity to be able to respond in a much faster timeframe when the covered entity is using health information technology in its day to day operations.
How long does it take to get access to a certified EHR?
While the Privacy Rule permits a covered entity to take up to 30 calendar days from receipt of a request to provide access (with one extension for up to an additional 30 calendar days when necessary), covered entities are strongly encouraged to provide individuals with access to their health information much sooner, and to take advantage of technologies that enable individuals to have faster or even immediate access to the information.
What is access requested?
The access requested is reasonably likely to cause substantial harm to a person (other than a health care provider) referenced in the PHI. The provision of access to a personal representative of the individual that requests such access is reasonably likely to cause substantial harm to the individual or another person.
What are the two categories of information that are expressly excluded from the right of access?
In addition, two categories of information are expressly excluded from the right of access: Psychotherapy notes , which are the personal notes of a mental health care provider documenting or analyzing the contents of a counseling session, that are maintained separate from the rest of the patient’s medical record.
What is the HIPAA Privacy and Security Rule?
1 To fulfill this requirement, HHS published what are commonly known as the HIPAA Privacy Rule and the HIPAA Security Rule. The Privacy Rule, or Standards for Privacy of Individually Identifiable Health Information, establishes national standards for the protection of certain health information. The Security Standards for the Protection of Electronic Protected Health Information (the Security Rule) establish a national set of security standards for protecting certain health information that is held or transferred in electronic form. The Security Rule operationalizes the protections contained in the Privacy Rule by addressing the technical and non-technical safeguards that organizations called “covered entities” must put in place to secure individuals’ “electronic protected health information” (e-PHI). Within HHS, the Office for Civil Rights (OCR) has responsibility for enforcing the Privacy and Security Rules with voluntary compliance activities and civil money penalties.
What is the summary of the HIPAA security rule?
This is a summary of key elements of the Security Rule including who is covered, what information is protected, and what safeguards must be in place to ensure appropriate protection of electronic protected health information. Because it is an overview of the Security Rule, it does not address every detail ...
What is HIPAA protected health information?
The HIPAA Privacy Rule protects the privacy of individually identifiable health information, called protected health information (PHI), as explained in the Privacy Rule and here - PDF - PDF. The Security Rule protects a subset of information covered by the Privacy Rule, which is all individually identifiable ...
What is the HITECH Act?
The HITECH Act of 2009 expanded the responsibilities of business associates under the HIPAA Security Rule. HHS developed regulations to implement and clarify these changes. See additional guidance on business associates.
What is the Privacy Rule?
The Privacy Rule, or Standards for Privacy of Individually Identifiable Health Information, establishes national standards for the protection of certain health information. The Security Standards for the Protection of Electronic Protected Health Information (the Security Rule) establish a national set of security standards for protecting certain ...
What is the goal of the Security Rule?
A major goal of the Security Rule is to protect the privacy of individuals’ health information while allowing covered entities to adopt new technologies to improve the quality and efficiency of patient care.
Why are risk analysis and management provisions of the Security Rule addressed separately?
The risk analysis and management provisions of the Security Rule are addressed separately here because, by helping to determine which security measures are reasonable and appropriate for a particular covered entity, risk analysis affects the implementation of all of the safeguards contained in the Security Rule.
What devices can you use to access PHI?
Encrypt and password protect personal devices you may use to access PHI such as cell phones and tablets.
How to limit PHI?
Limit email transmissions of PHI to only those circumstances when the information cannot be sent another way. At a minimum, use encryption tools (most businesses provide tools to send encrypted emails).
Can you share PHI with others?
Lock your screens when walking away from your computer. Do not share sensitive PHI with others who shouldn’t have access, including co-workers and personal acquaintances. Only access a patient’s record if needed for work.
Can you print PHI?
Avoid printing PHI; however, if necessary, keep all PHI, such as patient paperwork, charts, and records, locked away and out of view.
Is HIPAA being waived?
Although certain HIPAA sanctions are being waived during the current health crisis, that does not excuse us from mishandling patients’ protected health information ( PHI ). We must take the same physical and security measures to safeguard the PHI we are trusted with in our work. Here are some best practices to follow:
What is required for covered entities to restrict access to only what is necessary?
In order to restrict access to only what is necessary, covered entities should make lists of all employees and specify what level of information each employee should have access to.
How to protect PHI from family?
Protect PHI from friends and family within your house by using a privacy screen on your computer, locking the screen when you walk away, restricting their access to the devices that contain PHI, and being careful not to say PHI aloud in a place where anyone could overhear.
Why should IT security teams monitor VPN limits?
Especially in light of widespread stay at home orders, IT security teams should monitor and test VPN limits to prepare for any increases in the number of users. Team members should also be aware of the potential need to make changes to adjust to their bandwidth requirements.
What is PHI in healthcare?
Access to Protected Health Information ( PHI) by unauthorized individuals
What is the best way to protect network access?
Ensure that laptops are equipped with firewalls and antivirus software to protect network access.
Is remote work HIPAA compliant?
While a remote work environment can provide many benefits to all of the parties involved, it also can present significant challenges for organizations that need to remain HIPAA compliant. There are many privacy and security measures that need to be implemented in order to address the concerns and risks of maintaining HIPAA compliance in ...
When do you need to sign confidentiality agreement?
Require all employees to sign a Confidentiality Agreement upon hiring before they begin to work.
What are the HIPAA rules?
The HIPAA Security and Privacy Rules require all covered entities to protect the EPHI that they use or disclose to business associates, trading partners or other entities. New standards and technologies have significantly simplified the way in which data is transmitted throughout the healthcare industry and created tremendous opportunities for improvements in the healthcare system. However, these technologies have also created complications and increased the risk of loss and unauthorized use and disclosure of this sensitive information.
What is the HIPAA security rule for laptops?
All covered entities are required to be in compliance with the HIPAA Security Rule1, which includes, among its requirements, reviewing and modifying, where necessary, security policies and procedures on a regular basis. This is particularly relevant for organizations that allow remote access to EPHI through portable devices or on external systems or hardware not owned or managed by the covered entity.
What does covered entity need to do to protect EPHI?
Covered entities must develop and implement policies and procedures to protect EPHI that is stored on remote or portable devices, or on potentially transportable media (particularly backups).
What is the HIPAA Privacy Rule for EPHI?
It is important that only those workforce members who have been trained and have proper authorization are granted access to EPHI.
What is the procedure for a covered entity to lose EPHI?
Should a covered entity experience loss of EPHI via portable media, the entity’s security incident procedures must specify the actions workforce members must take to manage harmful effects of the loss. Procedures may include securing and preserving evidence; managing the harmful effects of improper use or disclosure; and notification to affected parties. Needless to say, such incidents should be evaluated as part of the entity’s ongoing risk management initiatives.
Can a CSP be a HIPAA compliant business associate?
Yes, provided the covered entity or business associate enters into a HIPAA-compliant business associate contract or agreement (BAA) with the C SP that will be creating, receiving, maintaining, or transmitting electronic protected health information (ePHI) on its behalf, and otherwise complies with the HIPAA Rules.
Does encryption protect EPHI?
While encryption protects ePHI by significantly reducing the risk of the information being viewed by unauthorized persons, such protections alone cannot adequately safeguard the confidentiality, integrity, and availability of ePHI as required by the Security Rule. Encryption does not maintain the integrity and availability of the ePHI, such as ensuring that the information is not corrupted by malware, or ensuring through contingency planning that the data remains available to authorized persons even during emergency or disaster situations. Further, encryption does not address other safeguards that are also important to maintaining confidentiality, such as administrative safeguards to analyze risks to the ePHI or physical safeguards for systems and servers that may house the ePHI.
Can a health care provider access a cloud?
Yes. Health care providers, other covered entities, and business associates may use mobile devices to access electronic protected health information (ePHI) in a cloud as long as appropriate physical, administrative, and technical safeguards are in place to protect the confidentiality, integrity, and availability of the ePHI on the mobile device and in the cloud, and appropriate BAAs are in place with any third party service providers for the device and/or the cloud that will have access to the e-PHI. The HIPAA Rules do not endorse or require specific types of technology, but rather establish the standards for how covered entities and business associates may use or disclose ePHI through certain technology while protecting the security of the ePHI by requiring analysis of the risks to the ePHI posed by such technology and implementation of reasonable and appropriate administrative, technical, and physical safeguards to address such risks. OCR and ONC have issued guidance on the use of mobile devices and tips for securing ePHI on mobile devices. [18]
Is a covered entity in violation of HIPAA?
If a covered entity (or business associate) uses a CSP to maintain (e.g., to process or store) electronic protected health information (ePHI) without entering into a BAA with the CSP, the covered entity (or business associate) is in violation of the HIPAA Rules. 45 C.F.R §§164.308 (b) (1) and §164.502 (e). OCR has entered into a resolution agreement and corrective action plan with a covered entity that OCR determined stored ePHI of over 3,000 individuals on a cloud-based server without entering into a BAA with the CSP. [15]
Can a CSP view EPHI?
Generally, no. CSPs that provide cloud services to a covered entity or business associate that involve creating, receiving, or maintaining (e.g., to process and/or store) electronic protected health information (ePHI) meet the definition of a business associate, even if the CSP cannot view the ePHI because it is encrypted and the CSP does not have the decryption key.
Is a CSP exempt from HIPAA?
As a business associate, a CSP providing no-view services is not exempt from any otherwise applicable requirements of the HIPAA Rules. However, the requirements of the Rules are flexible and scalable to take into account the no-view nature of the services provided by the CSP.
More and More Employees Are Working Remotely
Real Life Examples
- Cancer Care Group agreed to a settlement of $750,000, after a remote employee lost a laptopand backup drive to car theft. The laptop contained more than 50,000 patients’ PHI. OCR determined that prior to the breach, Cancer Care Group was in widespread non-compliance with the HIPAA Security Rule. They failed to conduct an enterprise-wide risk analysis when the breach originally …
How to Protect Your Clients’ Phi When Working Remotely
- What can you do to safeguard your organization from HIPAA violations? We compiled a list of documentation requirementsand preventative actions you need to observe to protect you and your clients. First and foremost, if you have remote employees, you must set rules for them in your Security Policies and Procedures. Use the following checklistas a guide for what to inclu…