Remote access scams (also known as technical support scams) usually involve scammers contacting people over the phone to get access to their computers and to steal their money. If you have doubts about any caller who says they represent a business or organisation, hang up and call the business back using contact details from an independent source.
Full Answer
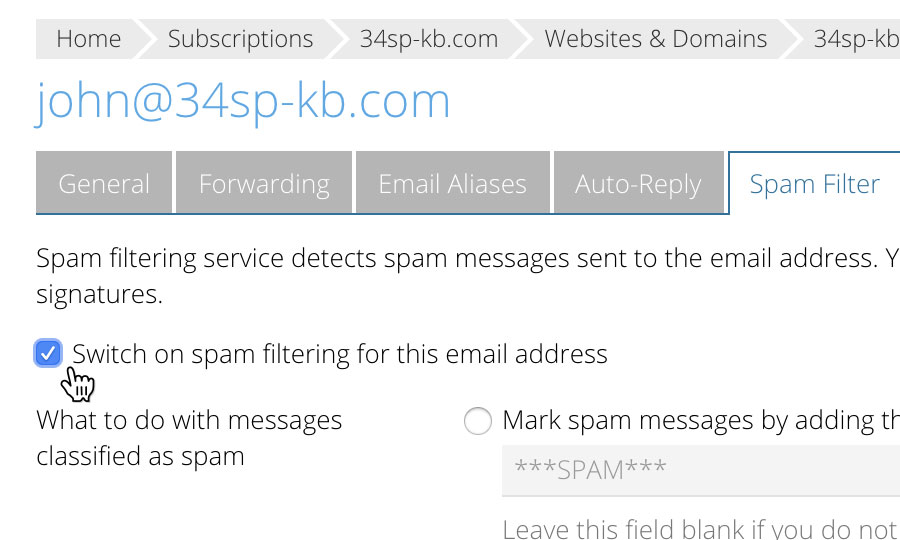
How do spammers get my email address?
How do spammers get my email address? Crawling the web for the @ sign. Spammers and cybercriminals use sophisticated tools to scan the web and harvest email addresses. If you publicly post your email address online, a spammer will find it.
How do you catch a computer scammer?
The first and easiest is when the scammer uses TeamViewer and you connect to their machine. TeamViewer allows the controlling PC to view/copy/move/etc. files without the other PC knowing, especially if you black out their screen. You have to be quick and play dumb though because sometimes the scammer catches on and unplugs the machine.
How to detect a remote access to my computer?
How to Detect a Remote Access to My Computer. 1. Disconnect your computer from the internet. If you believe someone is accessing your computer remotely, disconnect the computer from the internet. 2. Check the list of recently accessed files and apps. Both Windows PCs and Macs make it easy to view a ...
How do scammers target your personal information?
Scammers can target your personal information using unsecured wireless networks and software vulnerabilities. Be wary of public Wi-Fi networks.

What can a scammer do with AnyDesk?
AnyDesk is used legitimately by millions of IT professionals worldwide, to remotely connect to their clients' devices to help with technical issues. However, scammers can try to misuse AnyDesk (or any other remote access software) to connect to your computer and steal data, access codes, and even money.
What happens if you give a scammer access to your phone?
By having your cell number, a scammer could trick caller ID systems and get into your financial accounts or call financial institutions that use your phone number to identify you. Once the scammer convinces your carrier to port out your number, you may never get it back. Scam porting is a big problem for phone owners.
How do spammers get my address?
Spammers and cybercriminals use sophisticated tools to scan the web and harvest email addresses. If you publicly post your email address online, a spammer will find it. Making good guesses… and lots of them. Cybercriminals use tools to generate common user names and pair them with common domains.
What's the worst someone can do with your phone number?
If someone steals your phone number, they become you — for all intents and purposes. With your phone number, a hacker can start hijacking your accounts one by one by having a password reset sent to your phone. They can trick automated systems — like your bank — into thinking they're you when you call customer service.
What do I dial to see if my phone has been hacked?
Use the code *#21# to see if hackers track your phone with malicious intent. You can also use this code to verify if your calls, messages, or other data are being diverted. It also shows your diverted information's status and the number to which the information is transferred.
How does a spam caller know my name?
Spammers often release information-gathering programs called “bots” to collect the names and e-mail addresses of people who post to specific newsgroups. Bots can get this information from both recent and old posts.
How do spammers get my email password?
Scammers then use the email addresses and password combinations that were obtained during the data breach to send a wave of spam emails. This is why the password you see in the email might be a password you have since changed - they only have access to the data that was available at the time of the breach.
How do spammers get email on purpose?
0:000:56How to Get Junk Mail for Spam - YouTubeYouTubeStart of suggested clipEnd of suggested clipAnd go to mail for spam com. Mail. For spam allows you to use an email address without registering.MoreAnd go to mail for spam com. Mail. For spam allows you to use an email address without registering. You can use it for the purpose of receiving junk mails newsletters.
Can scammer hack my phone through phone call?
Can hackers hack your phone by calling you? No, not directly. A hacker can call you, pretending to be someone official, and so gain access to your personal details. Armed with that information, they could begin hacking your online accounts.
What can a scammer do with my phone number and email address?
Once they have your number, the bad guys can clean out your financial accounts, confiscate your email, delete your data and take over your social media profiles.
What kind of information can someone get from your phone number?
The information found through these sites includes your address, bankruptcies, criminal records, and family members' names and addresses. All of this can be used for blackmail, stalking, doxxing, social media hacking, or identity theft.
Should I change my phone number after being scammed?
If you've experienced identity theft, you should probably change your phone number. It's a massive inconvenience, but the pros will outweigh the cons. Let's understand why. Most people upgrade their smartphone every two years — especially if they're on a contract plan.
Can spammers buy lists?
Spammers can purchase lists legally and illegally. When you sign up for a website or a service, make sure you read the privacy policy carefully to find out what the site plans to do with your email address.
Is it better to keep your email private?
It pays to keep your email address as private as possible, but sometimes it seems like there’s nothing you can do to keep it out of the hands of spammers. For this reason you have to combine smart privacy practices with strong email filters.
What are the two ways scammers target your phone number?
There are two common ways that scammers target your phone number: robocall scams and phone number theft.
Where to file a report if you suspect a scam?
If you suspect your personal information was stolen by scammers, file a report with the FTC at identitytheft.gov .
What to do if you get a call from a number you don't recognize?
If you get a call from a number you don’t recognize, don’t answer. That’s the best way to ensure you don’t get caught up in a phone scam. And know that government agencies like Social Security and the IRS won’t call you out of the blue seeking your personal information.
How to protect yourself from insecure Wi-Fi?
To protect yourself from inadvertently using insecure Wi-Fi networks, adjust your phone settings to avoid auto-connecting to Wi-Fi.
How to keep data safe on a phone?
To keep that data safe, start by understanding the threats you face. Your phone has three main areas of vulnerability: its hardware, its software and your phone number. Each carries a risk, and there are steps you can take to mitigate them.
Can a phone number be used as a security key?
Because phone numbers are often used as security keys, hackers may be able to get into many other accounts once they have access to your phone account. Make it harder to penetrate by avoiding common security questions, Davis says. “When you set up your security questions and answers, make sure you’re using really challenging questions that are going to be hard to figure out.”
Can scammers target your personal information?
Scammers can target your personal information using unsecured wireless networks and software vulnerabilities. Be wary of public Wi-Fi networks.
How to run JRT as administrator?
Run the tool by double-clicking it. If you are using Windows Vista, 7, or 8; instead of double-clicking, right-mouse click JRT.exe and select "Run as Administrator". The tool will open and start scanning your system. Please be patient as this can take a while to complete depending on your system's specifications.
How to save a scan log?
While still on the Scan tab, click the link for View detailed log, and in the window that opens click the Export button, select Text file (*.txt), and save the log to your Desktop.
How to scan for rootkits?
Click the Settings tab at the top, and then in the left column, select Detections and Protections, and if not already checked place a checkmark in the selection box for Scan for rootkits. Click the Scan tab at the top of the program window, select Threat Scan and click the Scan Now button.
What is a BleepingComputer?
Welcome to BleepingComputer, a free community where people like yourself come together to discuss and learn how to use their computers. Using the site is easy and fun. As a guest, you can browse and view the various discussions in the forums, but can not create a new topic or reply to an existing one unless you are logged in. Other benefits of registering an account are subscribing to topics and forums, creating a blog, and having no ads shown anywhere on the site.
How Can Someone Hack My Phone Remotely?
It's not a secret that hackers don't need to have your phone in their hands to steal your personal information. They can target any of the data stored there remotely. Passwords, SSNs, bank account details, text messages, photos—almost anything can get into the hands of the bad guys if you aren't careful enough and well-protected.
What are some ways hackers can get access to your phone?
Cybercriminals create fake Wi-Fi networks, and when you connect to it with your phone, they redirect you to malicious sites. SIM swaps. Hackers transfer your phone number to their device and gain access to your account. Phishing emails or texts.
What is phishing email?
Phishing emails or texts. Hackers send you an email with a malicious link and try to trick you into clicking it. Such emails or texts may look very real, and sometimes it may be complicated to distinguish between a malicious site and a legitimate one.
How to prevent your phone from getting hacked?
Make sure that your device and the apps installed on it are up-to-date. Don't jailbreak your phone. This can increase the chances of your smartphone getting hacked later on. Use two-factor authentication. An extra layer of security for your apps will ensure that you're the only one who can access them.
Why turn off hotspot?
Turn off your hotspot in crowded places. It makes it easier for the hacker to get access to your device when it is turned on. And if you're using this feature, then make sure you have a strong password set.
How to prevent malware from using your phone?
If your phone also has such features as Touch ID or Face ID, then set it up as well. Don't turn on mobile data or Wi-Fi unless you need to use them. This can prevent malicious software from using your data.
What to do if you notice suspicious apps?
If you notice any suspicious apps, uninstall them immediately. Never click on suspicious links. If you've received a strange text message from your friend telling you to click on a link to open some random site, think twice before you do it. There can be malware in disguise.
How to stop someone from accessing my computer?
This includes removing any Ethernet cables and turning off your Wi-Fi connections.
What to do if your computer is compromised?
Change all of your passwords . If your computer was compromised, then there’s a possibility that all of your passwords have been recorded with a keylogger. If you’re sure the infection is gone, change the passwords for all of your various accounts. You should avoid using the same password for multiple services.
How to know if malware has been removed?
Monitor your computer after removing any malware. If your antivirus and/or Anti-Malware found malicious programs, you may have successfully removed the infection, but you'll need to keep a close eye on your computer to ensure that the infection hasn't remained hidden.
How to install antivirus on another computer?
If you don't have an antivirus, download an installer on another computer and transfer it to your computer via USB. Install the antivirus and then run a scan with it.
How to scan for malware on Windows 10?
If you're using Windows 10, you can use the built-in scanning tools in Settings > Update & Security > Windows Security to check for rogue applications. If you're using a Mac, check out How to Scan a Mac for Malware to learn how to use Mac-based scanning tools.
Why is public Wi-Fi so dangerous?
Try to avoid public Wi-Fi spots. Public Wi-Fi spots are risky because you have zero control over the network. You can't know if someone else using the spot is monitoring traffic to and from your computer. By doing this, they could gain access to your open browser session or worse. You can mitigate this risk by using a VPN whenever you are connected to a public Wi-Fi spot, which will encrypt your transfers.
What to do if you can't get rid of intrusion?
If you're still experiencing intrusions, or are concerned that you may still be infected, the only way to be sure is to completely wipe your system and reinstall your operating system.