In a remote access scam, a scammer attempts to persuade you into giving them remote control over your personal computer, which allows the scammer to con money out of you and steal your private information. Remote access scams are often related to tech support scams, (example: Dell Computer tech support) and typically starts on the phone with either a cold call from a fake tech support specialist telling you your computer is infected with malware, or a scary-looking pop-up ad that says there’s a problem with your computer and gives you a phone number to call for help. Scammers may also try to convince you to give them remote access by telling you they have money to give you that they can only deliver by connecting to your computer, as seen in the recent FTC refund scam that’s been making the rounds. Another very recent refund scam includes asking you to display your online bank account, and putting a fake deposit on your account statement. The scammers then lead you to believe that they made a typo on the fake refund issued and ask for a gift card as a refund to them.
Full Answer
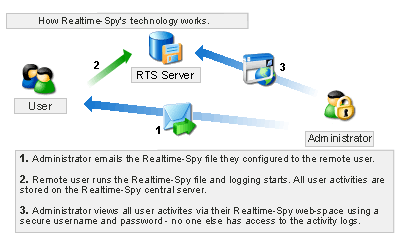
How do remote access scams work?
Remote access scams. Remote access scams try to convince you that you have a computer or internet problem and that you need to buy new software to fix the problem. The scammer will phone you and pretend to be a staff member from a large telecommunications or computer company, such as Telstra, the NBN or Microsoft.
How do you catch a computer scammer?
The first and easiest is when the scammer uses TeamViewer and you connect to their machine. TeamViewer allows the controlling PC to view/copy/move/etc. files without the other PC knowing, especially if you black out their screen. You have to be quick and play dumb though because sometimes the scammer catches on and unplugs the machine.
How do spammers get my email address?
How do spammers get my email address? Crawling the web for the @ sign. Spammers and cybercriminals use sophisticated tools to scan the web and harvest email addresses. If you publicly post your email address online, a spammer will find it.
How do I remotely access my computer?
Remote computer access requires a reliable internet connection. You’ll need to activate or install software on the device you want to access, as well as on the device — or devices — you want to use to get that access. For instance, you could install the software on your home computer and another device you’ll use remotely.

Can scammer access my computer remotely?
In a remote access scam, a scammer attempts to persuade you into giving them remote control over your personal computer, which allows the scammer to con money out of you and steal your private information.
Can someone remotely access my computer without my knowledge?
There are two ways someone can access your computer without your consent. Either a family member or work college is physically logging in to your computer or phone when you are not around, or someone is accessing your computer remotely.
How do I stop remote access to my computer?
How to Disable Remote Access in Windows 10Type “remote settings” into the Cortana search box. Select “Allow remote access to your computer”. ... Check “Don't Allow Remote Connections” to this Computer. You've now disabled remote access to your computer.
How do you tell if your computer is being monitored?
How to Check If Your Computer Is Being MonitoredLook for Suspicious Processes. Suspicious processes may indicate that your computer is being monitored. ... Run Antivirus Software. Antivirus software can reveal whether or not your computer is being monitored. ... Evaluate Ports. Another tip is to evaluate your network's ports.
How can I tell who is remoted into my computer?
RemotelyHold down the Windows Key, and press “R” to bring up the Run window.Type “CMD“, then press “Enter” to open a command prompt.At the command prompt, type the following then press “Enter“: query user /server:computername. ... The computer name or domain followed by the username is displayed.
Can you tell if someone is spying on your computer?
Check the Task Manager or Activity Monitor Spyware is subtle in comparison to other types of malware. It hides in your system, keeping track of every password you type, every video call you make and every email you send. While these pieces of software are sneaky, they do leave behind breadcrumbs.
What happens when someone hacks your computer?
If your computer is hacked, you might notice some of the following symptoms: Frequent pop-up windows, especially the ones that encourage you to visit unusual sites, or download antivirus or other software. Changes to your home page. Mass emails being sent from your email account.
What prevents someone from connecting to your computer remotely using your public IP?
If the firewall port is exposed to the public, it will allow any IP address to connect to it. Anyone located from different parts of the world can try to brute force their way into your computer. The computer can be infected with malware, ransomware, or data theft.
Is someone spying on my laptop?
To open the Activity Monitor, hit Command + Spacebar to open Spotlight Search. Then, type Activity Monitor and press Enter. Check over the list for anything you don't recognize. To close out a program or process, double click, then hit Quit.
Can someone listen to you through your computer?
Yes, there are people out there who can hack into your operating system and take over your microphone, using it to listen in on your conversations and record personal information.
What is remote access scam?
Remote access scams try to convince you that you have a computer or internet problem and that you need to buy new software to fix the problem.
How to protect your computer from spyware?
Make sure your computer is protected with regularly updated anti-virus and anti-spyware software, and a good firewall. Research first and only purchase software from a source that you know and trust.
What is malware scam?
Malware tricks you into installing software that allows scammers to access your files and track what you are doing, while ransomware demands payment to ‘unlock’ your computer or files.
What to do if you think you have provided your account details to a scammer?
If you think you have provided your account details to a scammer, contact your bank or financial institution immediately.
Can a scammer be abusive?
The scammer may initially sound professional and knowledgeable—however they will be very persistent and may become abusive if you don't do what they ask.
How to stop someone from accessing my computer?
This includes removing any Ethernet cables and turning off your Wi-Fi connections.
How to install antivirus on another computer?
If you don't have an antivirus, download an installer on another computer and transfer it to your computer via USB. Install the antivirus and then run a scan with it.
How to know if malware has been removed?
Monitor your computer after removing any malware. If your antivirus and/or Anti-Malware found malicious programs, you may have successfully removed the infection, but you'll need to keep a close eye on your computer to ensure that the infection hasn't remained hidden.
What to do if your computer is compromised?
Change all of your passwords . If your computer was compromised, then there’s a possibility that all of your passwords have been recorded with a keylogger. If you’re sure the infection is gone, change the passwords for all of your various accounts. You should avoid using the same password for multiple services.
How to scan for malware on Windows 10?
If you're using Windows 10, you can use the built-in scanning tools in Settings > Update & Security > Windows Security to check for rogue applications. If you're using a Mac, check out How to Scan a Mac for Malware to learn how to use Mac-based scanning tools.
Why is public Wi-Fi so dangerous?
Try to avoid public Wi-Fi spots. Public Wi-Fi spots are risky because you have zero control over the network. You can't know if someone else using the spot is monitoring traffic to and from your computer. By doing this, they could gain access to your open browser session or worse. You can mitigate this risk by using a VPN whenever you are connected to a public Wi-Fi spot, which will encrypt your transfers.
What to do if you can't get rid of intrusion?
If you're still experiencing intrusions, or are concerned that you may still be infected, the only way to be sure is to completely wipe your system and reinstall your operating system.
How to protect your computer when using remote access?
Here are some steps you can take to help protect your computer and data while relying on remote access. Maintain strong passwords.
How to protect remote desktop from hackers?
Use a secure Virtual Private Network (VPN). If you set up a VPN, your remote desktop server won’t be connected directly to the internet. It will only be exposed on your local network, which could leave it less vulnerable to hackers.
What is remote computer access?
Many people take their laptops with them to do things like finish a business presentation while waiting for a flight at the airport. But a lot of those laptops may not have bigger, important files on them. You might leave those files at work or at home on your desktop computer.
How does TeamViewer work?
Here’s how it works. You’ll need to create an account, and then download and install TeamViewer software onto both your home computer and your remote computer or device. TeamViewer can be installed on Windows, Mac OS, Linux, and Chrome OS. It also has apps for Windows Phone, Blackberry, iOS, and Android. LogMeIn.
How to protect your network from remote access?
You should set up firewalls to restrict access using software or hardware or both.
What is remote access software?
Remote computer access software lets you access networks and computers remotely. It can enable file sharing. It’s like having a remote control for a computer or system that isn’t near you. You’ll be able to remotely download files and applications from your desktop or another person’s computer onto your laptop or your cell phone. Remote access also gives you control over that remote device
Why is it important to lock your computer?
Set up an account lockout policy. To help guard against hackers implementing brute-force attacks with automated password-guessing tools, it’s important to set your computer to lock your accounts when someone enters an incorrect password a set number of times.
What does a scammer do when he has control of the victim's computer?
However, in at least some of these videos, the first thing the scammer does when he has control of the victim's computer is to install and run a different remote-control application and use it to connect to his own computer.
Is TeamViewer a scam?
TeamViewer has noticed that scammers often come from India (or other places where scams often originate), and so when you get an incoming connection from India TeamViewer will give you a warning saying that this could be a scam. If the scammer can get the victim to connect to the scammer's computer first and then reverse the connection (by clicking a button that says "switch sides with partner"), TeamViewer's warning is skipped and the victim still doesn't know it's a scammer. The scammers want to use TeamViewer because it has the ability to blacken the victims screen so the victim cannot see what the scammer is doing.
Can spammers buy lists?
Spammers can purchase lists legally and illegally. When you sign up for a website or a service, make sure you read the privacy policy carefully to find out what the site plans to do with your email address.
Is it better to keep your email private?
It pays to keep your email address as private as possible, but sometimes it seems like there’s nothing you can do to keep it out of the hands of spammers. For this reason you have to combine smart privacy practices with strong email filters.