The process:
- A VPN client installed on the remote user’s desktop recognizes the destination network as a part of remote VPN encryption network.
- This client then begins to negotiate with a remote gateway (firewall) to build a secure VPN tunnel.
- This negotiation process involves encryption schemes and methods to be adopted while establishing a VPN tunnel.
How to access remote computer via VPN?
Knowledge How do I remote into my computer at work from home using the VPN?
- Enable remote connection on your work computer. ...
- See How do I download and install the Cisco AnyConnect VPN client? ...
- Reboot your home computer
- After the reboot, go to your home computer's Windows Start Menu, search for Cisco AnyConnect VPN Client and open the program
- The AnyConnect window will come up and indicate that the VPN is "Ready to connect". ...
Why use a VPN for remote access in the cloud?
Why is a VPN Needed?
- Reduces Risk. A Clark School study is one of the first to quantify the near-constant rate of hacker attacks on computers with Internet access—every 39 seconds on average—and the non-secure ...
- Secures & Extends Private Network Services. ...
- Leverages Existing Security Investments. ...
- Increases Employee Productivity. ...
What is the difference between a VPN and remote control?
- Can access work-related assets
- Cheap
- Provides physical-level access to work computers
- Full encryption to protect against MITM attacks
- Stops prying eyes from your ISP or elsewhere
- Allows the employee to access geo-restricted content
What services can I access with VPN?
- Library databases (without logging in)
- All the information contained in PeopleFinder (without logging in)
- The MESA shared drive
- Remote into your office computer on campus
- Any other systems or resources your school or department restricts
- mason.gmu.edu server

Is remote access the same as VPN?
While having some similarities, VPN and remote desktop are functionally different things. A VPN will give you access to a network while remote desktop (or RDP) will give you control of an entire computer.
Do you need VPN for remote access?
No, but they serve a similar function. A VPN lets you access a secure network. RDP lets you remotely access a specific computer. Both will (usually) encrypt your traffic in one way or another, and both will grant you private access to a server or device that might be thousands of miles away.
What are the disadvantages of using a VPN?
The 10 biggest VPN disadvantages are:A VPN won't give you complete anonymity: Read more.Your privacy isn't always guaranteed: Read more.Using a VPN is illegal in some countries: Read more.A safe, top-quality VPN will cost you money: Read more.VPNs almost always slow your connection speed: Read more.More items...•
How do I setup a VPN remote access?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
What do you need for remote access?
Remote computer access requires a reliable internet connection. You'll need to activate or install software on the device you want to access, as well as on the device — or devices — you want to use to get that access.
How do I access my work network remotely?
The best solution that will allow organizations to access files remotely is to set-up a virtual private network (VPN). A VPN provides a cable-like connection via the Internet between a remote PC and your office's server.
Why is remote access VPN important?
It also ensures to protect your online privacy. Remote access VPNs restrict user access to just one, which signifies the fact that it is designed for personal use. Nevertheless, if you are a digital nomad that remotely communicates with your organization’s network, remote access VPN could be the pick of the litter.
Which VPN supports remote access?
2) SSL VPN – Also known as mobile access VPN, SSL VPN supports only remote access connections. While both the blades offer an equal amount of data confidentiality, integrity and authenticity, let’s see the other features that differentiate each other. IPSec VPN. SSL VPN. Supports both TCP and UDP.
What is VPN client?
A VPN client installed on the remote user’s desktop recognizes the destination network as a part of remote VPN encryption network.
What is VPN encryption?
In other words, your information that travels through the internet gets encrypted and encapsulated by a secure VPN gateway. This encryption technique plays a vital role in communicating your information to the remote destination. It scrambles your data and keeps it out of reach from notorious third parties like hackers and snoopers.
Why do businesses use VPN?
Hence every organization aims at offering comprehensive resource accessibility, even to its remote workers. That’s when a remote access VPN comes into the picture. It shares your organization’s responsibility of granting secure access to the business resources.
Is VPN clientless?
It is clientless and just requires a browser. Seamless to use. Not seamless, requires multilevel authentication. Other than the data security it offers, setting up a remote access VPN is cost-effective. With multiple VPN providers offering competitive business VPN plans, it also easy to upgrade your subscription plan as your business grows.
Why is VPN remote access?
The remote access VPN does this by creating a tunnel between an organization’s network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
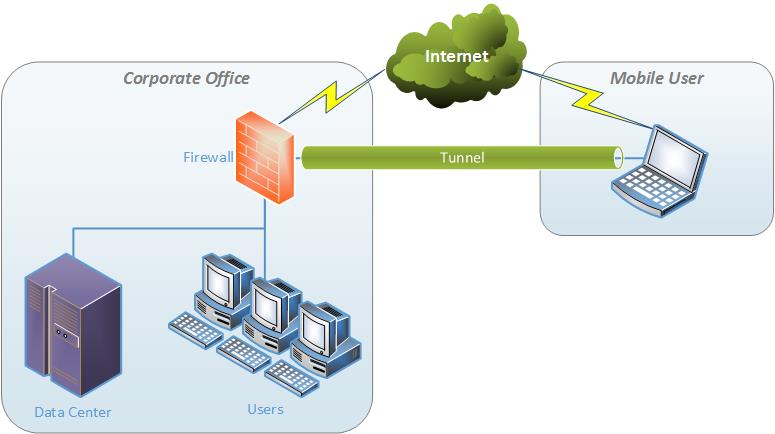
What is remote access VPN?
What Is a Remote Access VPN? A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive. The remote access VPN does this by creating a tunnel between an ...
Does SASE require a VPN?
Using SASE, an organization does not have to maintain a separate stand-alone proxy or VPN. Rather, users connect to a SASE solution (which provides access to the cloud and data center) with consistent security. Some advantages of using a SASE are that it allows companies to:
What is remote access VPN?
A remote-access VPN extends almost any data, voice, or video application to a remote device, also known as an "endpoint" or a host. Advanced VPN technology allows for security checks to be conducted on endpoints to make sure that they meet a certain posture before they can connect to the network.
Why do organizations use VPNs?
Organizations use site-to-site VPNs when distance makes it impractical to have direct network connections between these sites. Establishing and maintaining site-to-site VPN connections requires dedicated equipment.
What is a VPN topology?
A VPN topology specifies the peers and networks that are part of the VPN and how they connect to one another. Here is a quick overview of the three main types of topologies: Hub-and-spoke. In this VPN topology, multiple remote devices (spokes) communicate securely with a central device (hub).
What is SSL VPN?
Secure Sockets Layer (SSL) VPN and IP security (IPsec) are tunnels and authentication technologies. Businesses can use SSL VPN, IPsec, or both to deploy a remote-access VPN, depending on deployment requirements. SSL VPN and IPsec protect data traversing the VPN from unauthorized access.
Why is SSL VPN used?
SSL VPN uses SSL protocol and its successor, Transport Layer Security (TLS), to provide a secure connection between remote users and internal network resources. Because most web browsers now have SSL/TLS, users do not typically need to install client software to use SSL VPN. That's why SSL VPN is also known as "clientless VPN" or "web VPN."
What is VPN in business?
A virtual private network (VPN) extends a company's network, allowing secure remote user access through encrypted connections over the Internet. This allows VPN traffic to remain private as it travels between devices and the network. As a VPN user browses the web, their device contacts websites through the encrypted VPN connection.
What is secure remote access?
Secure remote access is a method for connecting remote users and devices securely to a corporate network. It includes VPN technology, which authenticates users or devices, confirming that they meet certain requirements—also known as "posture"—before they can connect to the network remotely.
How does a VPN work?
How a VPN Works. A VPN works by routing a device's internet connection through a private service rather than the user's regular internet service provider (ISP). The VPN acts as an intermediary between the user getting online and connecting to the internet by hiding their IP address. Using a VPN creates a private, ...
Why do people use VPN?
A VPN enables people to protect themselves from government surveillance by hiding their browsing history. As long as their VPN provider does not log browsing history, which some do, users can rest assured that their freedom on the internet is protected.
What is a VPN?
A virtual private network (VPN) is a secure network that enables internet users to hide their Internet Protocol (IP) address to securely browse the web and access content from other countries . A succinct description of what is VPN is it enables people to access the internet securely while remaining anonymous online.
What is VPN for medical?
A VPN enables users to keep search information—such as medical conditions, required surgery or treatment, travel plans, or even gift idea research—private and prevents their ISP and web browser from serving related ads.
What is VPN mask?
A VPN masks a user’s true location to the one they set their VPN to. This enables them to access content or websites typically restricted to that region. For example, a user in the U.S. can set their location to the United Kingdom and watch content from streaming websites aimed at British audiences. A U.S. citizen can also continue streaming their favorite shows even when they are away from the country on holiday.
What is VPN traffic?
All network traffic is sent through a secure connection via the VPN. This means that any data transmitted to the internet is redirected to the VPN rather than from the user’s computer. When the user connects to the web using their VPN, their computer submits information to websites through the encrypted connection created by the VPN. ...
Why do VPNs use encryption?
is a fair question, and anyone asking should know they do. VPNs use encryption to keep internet users secure and their data private. A VPN works based on encryption, which hides the true meaning of information. This ensures data cannot be read unless someone unlocks it with a password, known as an encryption key.
How Are Remote-Access VPNs Different to Consumer VPN Solutions?
You may be familiar with the term ‘VPN’ from the vast range of consumer VPN solutions available on the market, like NordVPN, ExpressVPN, and TunnelBear.
Why do people use VPN?
Personal, consumer VPN services are used by private individuals to encrypt their online traffic, protecting their online activity and their right to informational privacy. VPNs are often used to conceal or alter a device’s perceived geographic location.
What is a VPN?
You may be familiar with the term ‘VPN’ from the vast range of consumer VPN solutions available on the market, like NordVPN, ExpressVPN, and TunnelBear. Enterprise level remote-access VPNs use the same underlying technology but they are used very differently in practice.
What are the benefits of working remotely?
Giving your staff the option of working remotely has a number of benefits: 1 Flexibility – Remote working options give people the freedom to work whenever and wherever they like, providing a better work-life balance 2 Working Preferences – Some people find they’re more productive at home than in the busy office 3 Employees Without Borders – The ability to telecommute means that you can work with the best talent – wherever they are in the world 4 Eco-Friendly – The average UK commute takes almost an hour. Working from home means more productivity and a lower carbon footprint 5 Cost Reduction – Companies with home workers can have a smaller office with lower overheads 6 In Case of Emergency – Remote working options can help keep your business running when the unexpected occurs 7 Maximise Productivity – Remote working enables personnel to work productively even when they’re at a conference or meeting off-site.
What is the first option for a VPN?
The first option is to supply your workers with a PC/laptop with pre-configured VPN software.
Why is VPN traffic routed?
User traffic is routed through a VPN provider’s servers to preserve anonymity and privacy – creating a secure tunnel between the user’s device and whatever website or resource they’re trying to access. Consumers purchase a subscription to the service and manage connections and disconnections through software.
Why do remote workers use their own devices?
So when remote workers use their own devices to access company servers, files, and emails, their device could potentially bring cybersecurity vulnerabilities into the company’s network. The company also has no agency over the security measures employed on the networks that their workers use to access those resources.
What is SSTP in VPN?
SSTP is a Microsoft proprietary SSL-based solution that can penetrate firewalls since most firewalls open the outbound TCP port that 443 SSL uses. OpenVPN. OpenVPN is a SSL-based solution that can penetrate firewalls since most firewalls open the outbound TCP port that 443 SSL uses. IKEv2 VPN.
Is TLS 1.1 supported by Azure VPN?
Starting July 1, 2018, support is being removed for TLS 1.0 and 1.1 from Azure VPN Gateway. VPN Gateway will support only TLS 1.2. To maintain support, see the updates to enable support for TLS1.2.
Does Radius support OpenVPN?
RADIUS authentication is supported for the OpenVPN protocol only through PowerShell.
Does Azure support P2S VPN?
Azure supports Windows, Mac, and Linux for P2S VPN.
Does VPN reestablish automatically?
By default, the client computer will not reestablish the VPN connection automatically.
Do you need a VPN for a resource manager?
Yes. For the Resource Manager deployment model , you must have a RouteBased VPN type for your gateway. For the classic deployment model, you need a dynamic gateway. We do not support Point-to-Site for static routing VPN gateways or PolicyBased VPN gateways.
Can a point to site client connect to a VNet?
Yes, Point-to-Site client connections to a virtual network gateway that is deployed in a VNet which is peered with other VNets may have access to other peered VNets. Point-to-Site clients will be able to connect to peered VNets as long as the peered VNets are using the UseRemoteGateway / AllowGatewayTransit features.
What is remote computer access?
Many people take their laptops with them to do things like finish a business presentation while waiting for a flight at the airport. But a lot of those laptops may not have bigger, important files on them. You might leave those files at work or at home on your desktop computer.
Why is remote access important?
Remote access software is helpful when you’re in a meeting at another office with your laptop — or telecommuting — and need an important file that’s on your office computer. Remote computer access can help you assist someone in your personal life who might be far away.
How does TeamViewer work?
Here’s how it works. You’ll need to create an account, and then download and install TeamViewer software onto both your home computer and your remote computer or device. TeamViewer can be installed on Windows, Mac OS, Linux, and Chrome OS. It also has apps for Windows Phone, Blackberry, iOS, and Android. LogMeIn.
How to protect remote desktop from hackers?
Use a secure Virtual Private Network (VPN). If you set up a VPN, your remote desktop server won’t be connected directly to the internet. It will only be exposed on your local network, which could leave it less vulnerable to hackers.
How to protect your network from remote access?
You should set up firewalls to restrict access using software or hardware or both.
What is remote access software?
Remote computer access software lets you access networks and computers remotely. It can enable file sharing. It’s like having a remote control for a computer or system that isn’t near you. You’ll be able to remotely download files and applications from your desktop or another person’s computer onto your laptop or your cell phone. Remote access also gives you control over that remote device
How to protect your computer when using remote access?
Here are some steps you can take to help protect your computer and data while relying on remote access. Maintain strong passwords.
What is remote access VPN?
Remote Access: A remote access VPN means your employees can log on to your company network from anywhere that has access to the Internet. Whether they are in the coffee shop, traveling, or (hopefully) social isolating at home, a VPN allows your employees to access all the resources they need to get the job done.
How does a VPN work?
The only way in is through a device with VPN client software installed and configured to connect to your VPN server (s).
What is a Business VPN?
A Virtual Private Network (VPN) provides your business with a securely encrypted connection to your network over the public Internet. It adds an important piece of layered security, which is essential to protect your data. Using a VPN gives you the ability to remotely access important network resources and connect your company's branches and locations worldwide.
What is the difference between a Proxy Server and a VPN?
A proxy server is similar to a VPN in that it is a type of gateway to the Internet. Businesses set up proxy servers to protect their network from the dangers of the open Internet. It can provide anonymity, protection against malicious traffic, not allowing outgoing traffic to known malicious sites, and Internet logging, which could help you track down something like a malware infection. While a proxy can provide these safeguards, it does not protect data being transmitted. Many businesses combine VPNs and Proxy Servers, and you can read details here about layering network security.
What is encryption?
Encryption is the conversion of information into a cryptographic encoding that can't be read without a key. Encrypted data looks meaningless and is extremely difficult for unauthorized parties to decrypt without the correct key.
Why can't I just run my own VPN?
You can. OpenVPN is open source, so we have an entire community of people who build their own VPNs using our OS code.
What is a VPN app?
The OpenVPN Connect App enables mobile users to have access to Enterprise-grade security, reliability, and scalability features offered by OpenVPN Access Server Software or their VPN provider.