What is SCW and how is it used?
Microsoft Security Configuration Wizard (SCW) is a software program that allows administrators to easily change a server's default security settings. SCW consists of three main components: a wizard interface, a command-line interface and a Security Configuration Database.
Can SCW apply security policies to multiple servers at a time?
To apply SCW security policies in Windows domain environments, I recommend transforming the SCW policy into GPO settings and applying the security policies through the GPO. Doing so will enable you to apply the SCW policy to multiple servers at one time.
How do I create a security policy in SCW?
Launch Server Manager using the icon on the desktop taskbar or from the Start screen. In Server Manager, select Security Configuration Wizard from the Tools menu. Click Next on the welcome screen of the wizard. On the Configuration Action screen, select Create a new security policy and click Next.
What is RPC firewall?
The RPC firewall is a free and open-source tool, which enables you to audit and block remote RPC calls.
What is the fundamental The requirement for applications that use IP protocol and ports when you run SCW?
All applications that use the IP protocol and ports must be running on the server when you run SCW. In some cases, you must be connected to the Internet to use the links in the SCW Help.
How do I open Local Security Policy in Windows Server 2016?
To open Local Security Policy, on the Start screen, type, secpol. msc. Under Security Settings of the console tree, do one of the following: Click Account Policies to edit the Password Policy or Account Lockout Policy.
What is NAP capable?
When a NAP-capable client computer contacts a NAP enforcement point, it submits its current health state. The NAP enforcement point sends the NAP client's health state to the NAP health policy server for evaluation using the RADIUS protocol.
How do I run security configuration wizard?
Launch Server Manager using the icon on the desktop taskbar or from the Start screen. In Server Manager, select Security Configuration Wizard from the Tools menu. Click Next on the welcome screen of the wizard. On the Configuration Action screen, select Create a new security policy and click Next.
What is security configuration wizard?
The Security Configuration Wizard (SCW) is a handy tool that was released as a part of the tool suite for Windows 2003 SP1. Its purpose is to allow you to create role-based security policies that can then be applied to any server in your organization.
What ports does RPC use?
By default, RPC uses the port range of 1024 to 5000 for allocating ports for endpoints.
How do I enable RPC in firewall?
To allow inbound remote procedure call (RPC) network traffic, use the Windows Defender Firewall with Advanced Security node in the Group Policy Management console to create two firewall rules. The first rule allows incoming network packets on TCP port 135 to the RPC Endpoint Mapper service.
How can I tell if RPC port is open?
The PortQry command-line utility can be used to test connectivity from the client to the server and determine which ports are open on the server. It includes support for RPC and can be used to determine which services have dynamic ports that are registered with RPC and which specific ports they use.
How do you create a security policy?
10 steps to a successful security policyIdentify your risks. What are your risks from inappropriate use? ... Learn from others. ... Make sure the policy conforms to legal requirements. ... Level of security = level of risk. ... Include staff in policy development. ... Train your employees. ... Get it in writing. ... Set clear penalties and enforce them.More items...•
How do you implement a security policy?
To implement a security policy, do the complete the following actions:Enter the data types that you identified into Secure Perspective as Resources.Enter the roles that you identified into Secure Perspective as Actors.Enter the data interactions that you identified into Secure Perspective as Actions.
How do you develop information security policies?
How to: Information security policy developmentStart with an assessment. Often, organizations will want to begin with a risk assessment. ... Consider applicable laws and guidelines. ... Include all appropriate elements. ... Learn from others. ... Develop an implementation and communication plan. ... Conduct regular security training.
How do you write information security policy?
Provide information security direction for your organisation; Include information security objectives; Include information on how you will meet business, contractual, legal or regulatory requirements; and. Contain a commitment to continually improve your ISMS (information security management system).
What is SCW in Windows Server 2003?
The Security Configuration Wizard (SCW) first appeared in Windows Server 2003 Service Pack 1. It helps organizations reduce the attack surface on production servers.
Why is SCW important?
Despite the vastly improved security of Windows Server since SCW was first included in the OS, it can still be used to improve security and ensure that servers are configured using an identical security policy.
What port is used for remote desktop?
The Windows Firewall rules allow any device to connect to Remote Desktop Services on TCP port 3389. Although Microsoft Azure uses random ports for Remote Desktop by default, no special rule to accommodate this is required on Azure VMs so the default firewall rules that use port 3389 will work properly.
How to create a security policy in Windows 10?
On the Configuration Action screen, select Create a new security policy and click Next.
What is the network security rules screen?
The Network Security Rules screen shows a list of firewall rules required for the roles and features installed on the server.
What is auditing section in Windows Server?
The auditing section of the wizard allows you to increase the auditing level over what is configured as standard in Windows Server.
What happens if you change your security settings?
In the worst case scenario, you could lose access to a remote server. This would be especially catastrophic if it is located in a remote datacenter with no Integrated Lights Out facility.
How Firewall Rules Works?
As we have seen, the firewall rules are for traffic filtration. While we are adding any firewall rules, the rules entry will be made in the firewall config. When any network traffic comes, then the files will check the set of rules available. As per the rules, the firewall will take the decision.
Conclusion
We have seen the uncut concept of the “firewall rules” with the proper example, explanation and command with different outputs. It helps to filter the inbound network traffic as well as the outbound network traffic. The firewall is working on the TCP layer at level 7.
Recommended Articles
This is a guide to Firewall Rules. Here we discuss the introduction, how firewall rules works? And examples, respectively. You may also have a look at the following articles to learn more –
What is port forwarding on a router?
Port Forwarding or “opening ports” is a way for your router to allow traffic on certain ports. In our case it’s the DVR or NVRs specific ports.#N#Ports 80 (Web), 8000 (Apps), 554 (Video) should be forwarded to both TCP and UDP on your router.#N#Unfortunately because there are hundreds of router manufacturers and and thousands of different routers there is no unified way to guide you on how to forward up your ports.#N#Port Forward Tutorials#N#This website may be helpful. Select your router manufacturer and model number, a list of programs will pop up. Find “ Security Camera Warehouse Recorder” and Follow the step by step guide to open the ports.#N#We recommend referencing your router’s user manual in order to help forward ports.
Do most home users have static IP?
Most home users will have a dynamic IP unless specifically requested. Schools, businesses, or government facilities, etc should contact their technical staff or internet provider to determine their IP situation. Static IPs are typical with business level internet.
Can static IPs change?
The first step is to determine if your external IP is static or dynamic. Static IPs are addresses that don’t change, while dynamic IPs can change.
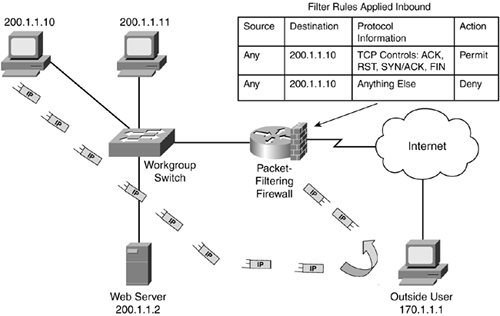
What are firewall rules?
The Windows Firewall uses rules and rule groups to establish its configuration. Each rule or rule group is associated with a particular program or service, and that program or service might modify or delete that rule without your knowledge. For example, the rule groups World Wide Web Services (HTTP) and World Wide Web Services (HTTPS) are associated with IIS. Enabling those rules will open ports 80 and 443, and SQL Server features that depend on ports 80 and 443 will function if those rules are enabled. However, administrators configuring IIS might modify or disable those rules. If you're using port 80 or port 443 for SQL Server, you should create your own rule or rule group that maintains your preferred port configuration independently of the other IIS rules.
What happens when you turn on the firewall?
Turning on the firewall will affect other programs that access this computer, such as file and print sharing, and remote desktop connections. Administrators should consider all applications that are running on the computer before adjusting the firewall settings.
What port is used for SQL Server reporting services?
By default, the typical ports used by SQL Server Reporting Services and associated services are: TCP 80, 443. The table below explains these ports in greater detail.
Why do we need a firewall?
Firewall systems help prevent unauthorized access to computer resources. If a firewall is turned on but not correctly configured, attempts to connect to SQL Server might be blocked. To access an instance of the SQL Server through a firewall, you must configure the firewall on the computer that is running SQL Server.
What is the first step in planning your firewall configuration?
The first step in planning your firewall configuration is to determine the current status of the firewall for your operating system. If the operating system was upgraded from a previous version, the earlier firewall settings may have been preserved. The Group Policy or Administrator can change the firewall settings in the domain.
How to open Windows Defender Firewall with Advanced Security?
From the start menu, type wf.msc. Press Enter or select the search result wf.msc to open Windows Defender Firewall with Advanced Security.
What is the net effect of port 80?
So if one rule allows traffic over port 80 from local subnet and one rule allows traffic from any address, the net effect is that all traffic to port 80 is independent of the source. To effectively manage access to SQL Server, administrators should periodically review all firewall rules enabled on the server.
1. Rollback the SCW
Rollback to the last applied security policy. This is given as one of the options on the first page of the Security configuration Wizard. To continue with this option requires at least one prior saved configuration, otherwise the error given is: The selected server does not have a rollback file.
2. Re-apply the SCW
Work your way through the Security Configuration Wizard, ensuring that the checkboxes concerned with Remote Desktop are turned on:
3. Check Firewall Setting
In the Windows firewall ensure that there are a pair of outgoing rules enabled for Remote Desktop, for TCP and UDP on the specified port. These are either the original pairing for port 3389. Or a more recent pairing, probably located near the top of the list. These will reflect the port number assigned to RDP.
4. Inbound Authentication Methods
On the SCW page Inbound Authentication Methods by default both options are checked.
5. Services
Check the service settings to ensure that Remote Desktop is active. Set it to automatic if set otherwise and if its not running manually start it.
6. Roles and Features
Reading on the Internet I found suggestions about adding Roles and Features associated with Remote Desktop. However, these were more associated with virtual hosts, including the brokerage service and licensing.
Why is the firewall GUI restricted?
To enhance the security of a network , in many environments access to the firewall GUI is limited by firewall rules. Restricting access to the management interface is the best practice , for reasons as to why, see the blog post Securely Managing Web-administered Devices.
What is an alias in a firewall?
1. Example alias for networks allowed to access management interface. 2. Example alias for ports allowed to access management interface. Now add a firewall rule allowing the sources defined in the management alias to the destination of the firewall, with the port used or alias created for those using multiple ports.
What is VPN in PfSense?
There are several VPN options available in pfSense software, such as. IPsec. OpenVPN. SSH tunneling. Once a VPN is in place, reach the GUI safely using a local address on the firewall, such as the LAN IP address. The exact details vary depending on the VPN configuration.
How to restrict webgui port?
If the webGUI port must be accessible to the Internet, restrict it by IP address/range as much as possible. Ideally, if there is a static IP address at the location to manage from, allow traffic from that IP address or subnet and nowhere else. Aliases also help, and they can include fully qualified domain names as well. If the remote management clients have a dynamic DNS address, add it to a management alias.
What is the best way to encrypt a GUI port?
The best practice is to always use HTTPS to encrypt access to the GUI port. Modern browsers may complain about the certificate, but an exception can usually be stored so it will only complain the first time.
What to do if a restrictive ruleset is in place on the LAN?
If a restrictive ruleset is in place on the LAN, make sure it permits access to the web interface before continuing.
Is moving the GUI to a non-standard port good?
Moving the GUI to a non-standard, random port is also beneficial. This does not improve the actual security of the GUI itself, but can potentially reduce the number of brute force attempts. The GUI can still be found by scanners unless the port is properly filtered.
What ports does RPC use?
Restart the server. All applications that use RPC dynamic port allocation use ports 5000 through 6000, inclusive.
What is the port range of a RPC?
For example, a single port may be represented by 5984, and a set of ports may be represented by 5000-5100. If any entries are outside the range of 0 to 65535, or if any string can't be interpreted, the RPC runtime treats the entire configuration as invalid.
What is the error code for RPC?
When there is a configuration error, the error code will be 87 (0x57) ERROR_INVALID_PARAMETER. This can affect Windows RPC servers as well, such as Netlogon. It will log event 5820 in this case:
What is RPC dynamic port allocation?
RPC dynamic port allocation is used by server applications and remote administration applications, such as Dynamic Host Configuration Protocol (DHCP) Manager, Windows Internet Name Service (WINS) Manager, and so on. RPC dynamic port allocation instructs the RPC program to use a particular random port in the range configured for TCP and UDP, based on the implementation of the operating system used. For more information, see references below.
Why are ports 5000 and 6000 selected?
In this example, ports 5000 through 6000 inclusive have been arbitrarily selected to help illustrate how the new registry key can be configured. It isn't a recommendation of a minimum number of ports needed for any particular system.
What is a string of IP ports?
Specifies a set of IP port ranges consisting of either all the ports available from the Internet or all the ports not available from the Internet. Each string represents a single port or an inclusive set of ports.
Can you use DCOM through firewalls?
You can't use DCOM through firewalls that do address translation. For example, a client connects to virtual address 198.252.145.1, which the firewall maps transparently to the server's actual address of, say, 192.100.81.101. DCOM stores raw IP addresses in the interface marshaling packets.
