
A VPN works by rerouting your internet traffic through a remote server and encrypting it in the process. That way, the VPN server
Virtual private network
A virtual private network extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running on a computing device, e.g. …
What is a remote access VPN?
What is a remote access VPN? Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What is a virtual private network (VPN)?
A virtual private network (VPN) extends a company's network, allowing secure remote user access through encrypted connections over the Internet. This allows VPN traffic to remain private as it travels between devices and the network.
What is VPN and how does VPN work?
VPN services are usually provided by a third-party. You install a small application on your device or your home router that creates a secure connection between that device and the VPN server. Nobody outside can see what you are doing or gain access to it.
How does a VPN tunnel work?
A VPN tunnel takes that data packet and slips it inside another data packet. This new packet is encrypted and only has a single possible destination, your VPN server. Once it gets to that destination, the VPN hardware at the end strips off most of that second packet and sends the original on its way.
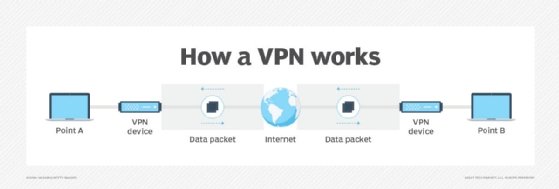
How does VPN work for remote access?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What is the difference between site to site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
Does VPN block remote access?
Because internet traffic and user identity are protected with encryption, VPN is technically a security solution, although it does enable remote network access, whether users are working from home, a coffee shop, or an airport.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
What are 3 types of VPN tunnels?
We'll look at three of the most common: IPsec tunnels, Dynamic multi point VPNs, and MPLS-based L3VPNs.IPsec Tunnels. In principle, a network-based VPN tunnel is no different from a client-based IPsec tunnel. ... Dynamic Multi point VPN (DMVPN) ... MPLS-based L3VPN.
Why do we need a site to site VPN?
A site-to-site virtual private network (VPN) is a connection between two or more networks, such as a corporate network and a branch office network. Many organizations use site-to-site VPNs to leverage an internet connection for private traffic as an alternative to using private MPLS circuits.
Which is more secure VPN or remote desktop?
Security. Although both VPN and RDP are encrypted through internet connection, a VPN connection is less accessible to threats than a remote desktop connection. For this reason, VPN is often considered more secure than RDP.
Which VPN is best for remote desktop?
Best Remote Access VPNs for business.Perimeter 81 – Best all-round business VPN.GoodAccess – Security Strategy Options.ExpressVPN – Lightning Fast VPN.Windscribe – VPN with Enterprise-Friendly Features.VyprVPN – Secure VPN with Business Packages.NordVPN – Security-first VPN.More items...•
Does remote desktop work with VPN?
If you create a virtual private network (VPN), you won't have to expose the Remote Desktop server directly to the Internet. Instead, when you're away from home, you can connect to the VPN, and your computer will act like it's part of the same local network as the computer at home, running the Remote Desktop server.
How do I connect VPN outside of network?
How does it work?Download your firewall's VPN client software - usually available for free from the vendors website (SonicWall, Checkpoint, WatchGuard, Meraki, etc).Install the software.Enter your organisation's public IP address.Enter your username and password and connect.
How can I access a private network remotely?
The best solution that will allow organizations to access files remotely is to set-up a virtual private network (VPN). A VPN provides a cable-like connection via the Internet between a remote PC and your office's server.
What is meant by site-to-site VPN?
A site-to-site virtual private network (VPN) refers to a connection set up between multiple networks. This could be a corporate network where multiple offices work in conjunction with each other or a branch office network with a central office and multiple branch locations.
What is site-to-site VPN in AWS?
AWS Site-to-Site VPN is a fully-managed service that creates a secure connection between your data center or branch office and your AWS resources using IP Security (IPSec) tunnels.
How many servers does PureVPN have?
PureVPN offers a global network of 6,500+ servers having a strong presence in over 140+ countries along with a huge pool of 300,000+ IPs, 100% Zero Log Policy (Audited and Verified), and a 31-day money-back guarantee. PureVPN offers apps for Windows, Mac, Android, iOS, Android TV, Firestick, and even your router.
Is PureVPN a VPN?
PureVPN is a simplified, secure and easy-to-use virtual private network designed to give you an unparalleled VPN experience. With a suite of professionally designed software & apps, you can stay absolutely secure on public hotspots and Wi-Fi networks without worrying about your security & privacy.
What is remote access VPN?
What is a remote access VPN? Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What are the advantages of remote access VPN?
Another advantage of remote access VPNs is that they provide companies with an affordable way to secure data sent by offsite employees. The initial investment needed to set up a remote access VPN is minimal and they can easily be scaled as a company grows and this is especially true if a VPN service provider is used.
Why is VPN important for business?
The most important benefit though is data security. When an offsite employee sends data through a VPN, it is encrypted, so even if a hacker is able to intercept that data, they won’t be able to use it. This is particularly important if an employee accesses their companies’ network using public Wi-Fi while traveling because traffic sent over these networks is usually not encrypted.
How does a NAS work?
Users connect to the NAS over the internet in order to use a remote access VPN. In order to sign in to the VPN, the NAS requires that users provide valid credentials. To authenticate these credentials, the NAS uses either its own authentication process or a separate authentication server running on the network .
What is a network access server?
A network access server could be a dedicated server or it might be a software application running on a shared server. Users connect to the NAS over the internet in order to use a remote access VPN. In order to sign in to the VPN, the NAS requires that users provide valid credentials. To authenticate these credentials, the NAS uses either its own authentication process or a separate authentication server running on the network.
Why do businesses use VPNs?
Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What is site to site VPN?
A site-to-site VPN uses a secure gateway to connect a network at one location to one or more networks at another location. This type of VPN doesn’t require each device at the end location to have a VPN client installed because the gateway handles the traffic.
What is remote access VPN?
A remote-access VPN extends almost any data, voice, or video application to a remote device, also known as an "endpoint" or a host. Advanced VPN technology allows for security checks to be conducted on endpoints to make sure that they meet a certain posture before they can connect to the network.
Why do organizations use VPNs?
Organizations use site-to-site VPNs when distance makes it impractical to have direct network connections between these sites. Establishing and maintaining site-to-site VPN connections requires dedicated equipment.
What is a VPN topology?
A VPN topology specifies the peers and networks that are part of the VPN and how they connect to one another. Here is a quick overview of the three main types of topologies: Hub-and-spoke. In this VPN topology, multiple remote devices (spokes) communicate securely with a central device (hub).
What is SSL VPN?
Secure Sockets Layer (SSL) VPN and IP security (IPsec) are tunnels and authentication technologies. Businesses can use SSL VPN, IPsec, or both to deploy a remote-access VPN, depending on deployment requirements. SSL VPN and IPsec protect data traversing the VPN from unauthorized access.
Why is SSL VPN used?
SSL VPN uses SSL protocol and its successor, Transport Layer Security (TLS), to provide a secure connection between remote users and internal network resources. Because most web browsers now have SSL/TLS, users do not typically need to install client software to use SSL VPN. That's why SSL VPN is also known as "clientless VPN" or "web VPN."
What is VPN in business?
A virtual private network (VPN) extends a company's network, allowing secure remote user access through encrypted connections over the Internet. This allows VPN traffic to remain private as it travels between devices and the network. As a VPN user browses the web, their device contacts websites through the encrypted VPN connection.
What is secure remote access?
Secure remote access is a method for connecting remote users and devices securely to a corporate network. It includes VPN technology, which authenticates users or devices, confirming that they meet certain requirements—also known as "posture"—before they can connect to the network remotely.
What can a VPN do for you?
A VPN is a secure encrypted connection between your computer and the VPN server. It keeps you safe and secure while online.
How do VPNs work?
The usual type of VPN home users utilize is called a remote access VPN. Your device establishes a secure tunnel with a remote network provided by the VPN company. That connection is referred to as a tunnel and is encrypted and secured, usually by SSH.
What is publicly visible when you use a VPN?
If your ISP now has carte blanche to track your every move while online, what do they see if you use a VPN? Not a lot actually. They will see you are using their service but not what you’re doing. All they will see is a series of encrypted data packets being sent from your device to the VPN server. That’s it.
