What is the difference between VPN and remote access?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
How VPN works step by step?
A VPN masks your IP address by acting as an intermediary and rerouting your traffic. It also adds encryption, or a tunnel around your identity, as you connect. The combination of the VPN server and the encryption tunnel blocks your ISP, governments, hackers, and anyone else from spying on you as you navigate the web.
Does VPN allow you to access a computer remotely?
Overview VPN is a tool that enables you to access one computer from another. Typical uses for Pop Center members would be 1) access their pop center computer from a home computer or laptop 2) access HSPH Kresge computers from the pop center 3) access the HSPH network drives from a non-HSPH internet connection.
What are the disadvantages of using VPN?
VPN disadvantages#1: Not designed for continuous use. The use case for remote access VPN was never to connect an entire enterprise to the WAN. ... #2: Complexity impedes scalability. ... #3: Lack of granular security. ... #4: Unpredictable performance. ... #5: Unreliable availability.
Can you be tracked with a VPN?
A premium quality VPN encrypts data and hides your IP address by routing your activity through a VPN server; even if someone tries to monitor your traffic, all they'll see is the VPN server's IP and complete gibberish. Beyond that, you can only be tracked with information you provide to sites or services you log into.
How do I setup a VPN remote access?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
Is VPN safer than remote desktop?
Is a VPN more secure than a remote desktop? Security and privacy is a VPN's greatest advantage. RDPs don't have to offer robust encryption to work, but a VPN without powerful encryption isn't much of a VPN.
How can I remotely access my computer from anywhere?
Open the web app on the computer you want to access remotely, and click Remote Access in the top right on the first screen. That will take you to a page that says “Set up remote access.” Click Turn on, then give your computer a name and a PIN (you'll need that to access it).
What is VPN and how it works?
A VPN connection establishes a secure connection between you and the internet. Via the VPN, all your data traffic is routed through an encrypted virtual tunnel. This disguises your IP address when you use the internet, making its location invisible to everyone. A VPN connection is also secure against external attacks.
How do I setup a VPN?
If you haven't already, add a VPN.Open your phone's Settings app.Tap Network & internet. VPN. ... Next to the VPN you want to change, tap Settings .Turn Always-on VPN on or off. If you've set up a VPN through an app, you won't have the always-on option.If needed, tap Save.
How do I setup a VPN connection?
Head into Settings > Network & Internet > Advanced > VPN (you should see a little key icon). If you don't see Network & Internet in the Settings menu (which may happen depending on your Android overlay), then do a search within Settings for VPN. Press the Add button.
How does VPN work on mobile?
When you use a VPN app, certain data from your connected device or phone — like your browsing history or data from the apps you're using — is sent through servers owned by the company providing the VPN. Most VPN apps encrypt, or scramble, the data sent between your phone and the VPN server.
What is VPN client?
A VPN client installed on the remote user’s desktop recognizes the destination network as a part of remote VPN encryption network.
What is VPN encryption?
In other words, your information that travels through the internet gets encrypted and encapsulated by a secure VPN gateway. This encryption technique plays a vital role in communicating your information to the remote destination. It scrambles your data and keeps it out of reach from notorious third parties like hackers and snoopers.
What happens when a tunnel negotiation gets over?
Once the tunnel negotiation gets over, the client can exchange encrypted communication with the remote gateway.
Why is remote access VPN important?
It also ensures to protect your online privacy. Remote access VPNs restrict user access to just one, which signifies the fact that it is designed for personal use. Nevertheless, if you are a digital nomad that remotely communicates with your organization’s network, remote access VPN could be the pick of the litter.
Which VPN supports remote access?
2) SSL VPN – Also known as mobile access VPN, SSL VPN supports only remote access connections. While both the blades offer an equal amount of data confidentiality, integrity and authenticity, let’s see the other features that differentiate each other. IPSec VPN. SSL VPN. Supports both TCP and UDP.
Why do businesses use VPN?
Hence every organization aims at offering comprehensive resource accessibility, even to its remote workers. That’s when a remote access VPN comes into the picture. It shares your organization’s responsibility of granting secure access to the business resources.
Is VPN clientless?
It is clientless and just requires a browser. Seamless to use. Not seamless, requires multilevel authentication. Other than the data security it offers, setting up a remote access VPN is cost-effective. With multiple VPN providers offering competitive business VPN plans, it also easy to upgrade your subscription plan as your business grows.
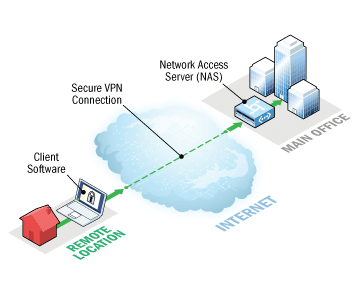
What is remote access VPN?
What Is a Remote Access VPN? A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive. The remote access VPN does this by creating a tunnel between an ...
Why is VPN remote access?
The remote access VPN does this by creating a tunnel between an organization’s network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
What are the advantages of using a SASE?
Some advantages of using a SASE are that it allows companies to: Apply security policies consistently across multiple locations and enforce least-privileged access. Simplify IT infrastructure and reduce costs by using a single cloud-based solution instead of having to buy and manage multiple point products.
Does SASE require a VPN?
Using SASE, an organization does not have to maintain a separate stand-alone proxy or VPN. Rather, users connect to a SASE solution (which provides access to the cloud and data center) with consistent security. Some advantages of using a SASE are that it allows companies to:
Remote Access VPN Explained
In the wake of the COVID-19 pandemic, your business may be accommodating more work from home (WFH) employees than ever before. If your teams often operate remotely, frequently travel for business, or use their own personal devices for work purposes, it’s vital that you offer them a safe way of connecting to your computer systems.
What Are Remote-Access VPNs?
In a nutshell, remote-access virtual private networks enable safe and secure access for company employees who are working remotely to use applications and share company data. These VPNs actively encrypt all of the traffic that’s sent and received by users between their home locations and corporate data centers.
Why Remote-Access VPNs Are Essential to WFH Businesses
Utilising remote-access VPNs offers plenty of advantages for organisations. The key benefit is of course the security that you can deliver to your remote employees.
Applications of Remote-Access VPNs For Businesses
There are a number of different actions that remote-access VPNs perform for businesses to ensure a comprehensive level of security for employees and their organisations alike. Let’s take a deeper look at some of the different ways in which remote-access VPNs can benefit businesses:
What is a Business VPN?
A Virtual Private Network (VPN) provides your business with a securely encrypted connection to your network over the public Internet. It adds an important piece of layered security, which is essential to protect your data. Using a VPN gives you the ability to remotely access important network resources and connect your company's branches and locations worldwide.
Are all VPNs the same?
No, the first notable difference is between consumer and business VPNs.
What is the difference between a Proxy Server and a VPN?
A proxy server is similar to a VPN in that it is a type of gateway to the Internet. Businesses set up proxy servers to protect their network from the dangers of the open Internet. It can provide anonymity, protection against malicious traffic, not allowing outgoing traffic to known malicious sites, and Internet logging, which could help you track down something like a malware infection. While a proxy can provide these safeguards, it does not protect data being transmitted. Many businesses combine VPNs and Proxy Servers, and you can read details here about layering network security.
What is encryption?
Encryption is the conversion of information into a cryptographic encoding that can't be read without a key. Encrypted data looks meaningless and is extremely difficult for unauthorized parties to decrypt without the correct key.
What is tunneling?
Tunneling involves protecting data by repackaging it into a different form. There are different kinds of tunneling that will affect the end-user. We recommend split-tunneling for remote access.
What is needed? What hardware/software?
It depends on the VPN. OpenVPN Access Server is completely virtual in the sense that it's purely a software solution. You won't need modems or routers or cables to get started; it's software-based.
Why can't I just run my own VPN?
You can. OpenVPN is open source, so we have an entire community of people who build their own VPNs using our OS code.
What is a VPN?
A virtual private network (VPN) is a secure network that enables internet users to hide their Internet Protocol (IP) address to securely browse the web and access content from other countries . A succinct description of what is VPN is it enables people to access the internet securely while remaining anonymous online.
What is VPN for medical?
A VPN enables users to keep search information—such as medical conditions, required surgery or treatment, travel plans, or even gift idea research—private and prevents their ISP and web browser from serving related ads.
What is VPN mask?
A VPN masks a user’s true location to the one they set their VPN to. This enables them to access content or websites typically restricted to that region. For example, a user in the U.S. can set their location to the United Kingdom and watch content from streaming websites aimed at British audiences. A U.S. citizen can also continue streaming their favorite shows even when they are away from the country on holiday.
What is VPN traffic?
All network traffic is sent through a secure connection via the VPN. This means that any data transmitted to the internet is redirected to the VPN rather than from the user’s computer. When the user connects to the web using their VPN, their computer submits information to websites through the encrypted connection created by the VPN. ...
Why do VPNs use encryption?
is a fair question, and anyone asking should know they do. VPNs use encryption to keep internet users secure and their data private. A VPN works based on encryption, which hides the true meaning of information. This ensures data cannot be read unless someone unlocks it with a password, known as an encryption key.
Why do people use VPN?
A VPN enables people to protect themselves from government surveillance by hiding their browsing history. As long as their VPN provider does not log browsing history, which some do, users can rest assured that their freedom on the internet is protected.
How does a VPN work?
How a VPN Works. A VPN works by routing a device's internet connection through a private service rather than the user's regular internet service provider (ISP). The VPN acts as an intermediary between the user getting online and connecting to the internet by hiding their IP address. Using a VPN creates a private, ...
What is a VPN topology?
A VPN topology specifies the peers and networks that are part of the VPN and how they connect to one another. Here is a quick overview of the three main types of topologies: Hub-and-spoke. In this VPN topology, multiple remote devices (spokes) communicate securely with a central device (hub).
What is SSL VPN?
Secure Sockets Layer (SSL) VPN and IP security (IPsec) are tunnels and authentication technologies. Businesses can use SSL VPN, IPsec, or both to deploy a remote-access VPN, depending on deployment requirements. SSL VPN and IPsec protect data traversing the VPN from unauthorized access.
Why is SSL VPN used?
SSL VPN uses SSL protocol and its successor, Transport Layer Security (TLS), to provide a secure connection between remote users and internal network resources. Because most web browsers now have SSL/TLS, users do not typically need to install client software to use SSL VPN. That's why SSL VPN is also known as "clientless VPN" or "web VPN."
What is IPsec policy?
An IPsec policy defines the characteristics of the site-to-site VPN, such as the security protocols and algorithms used to secure traffic in an IPsec tunnel. After an organization creates a VPN topology, it can configure the IPsec policies it applies to that topology, depending on the assigned IPsec technology.
What is VPN in business?
A virtual private network (VPN) extends a company's network, allowing secure remote user access through encrypted connections over the Internet. This allows VPN traffic to remain private as it travels between devices and the network. As a VPN user browses the web, their device contacts websites through the encrypted VPN connection.
What is secure remote access?
Secure remote access is a method for connecting remote users and devices securely to a corporate network. It includes VPN technology, which authenticates users or devices, confirming that they meet certain requirements—also known as "posture"—before they can connect to the network remotely.
What is a partial mesh VPN?
This is a network in which some devices are organized in a full mesh topology, and other devices form either a hub-and-spoke or a point-to-point connection to some of the fully meshed devices.
