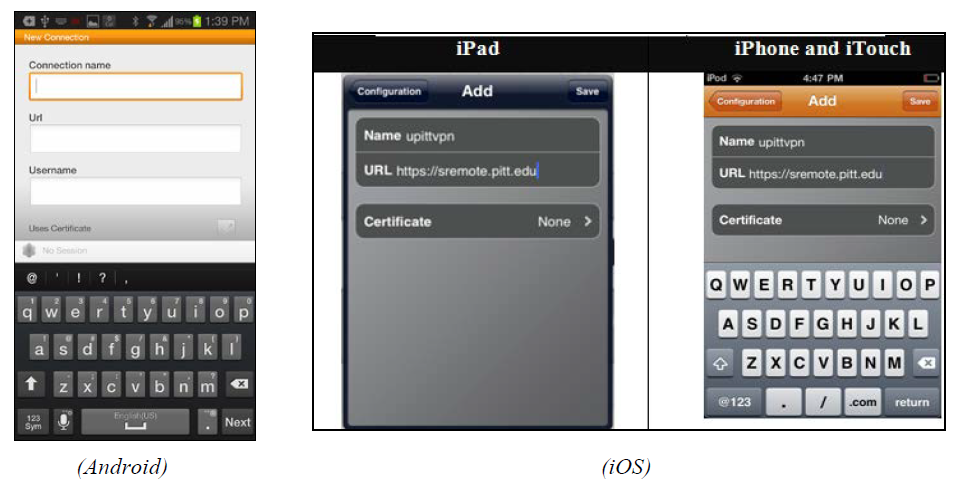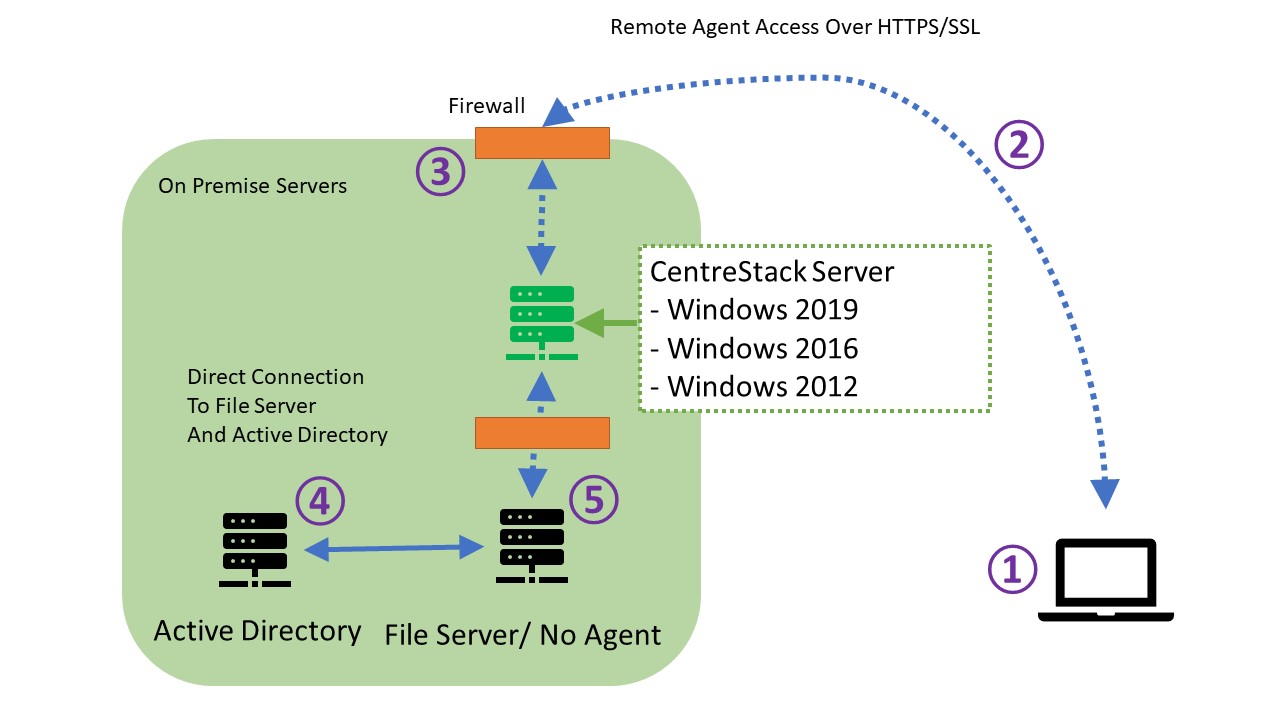
Full Answer
What is the best remote access for PC?
What is the Best Remote Desktop Software?
- GoToMyPC. GoToMyPC is the best remote desktop software on this list. ...
- AnyDesk. AnyDesk is one of the most popular remote desktop software platforms, used by over 100 million users globally.
- LogMeIn. ...
- Parallels. ...
- Splashtop Business Access. ...
- Zoho Assist. ...
- ConnectWise Control. ...
- RemotePC. ...
- TeamViewer. ...
- Remote Utilities for Windows. ...
How do I find my Remote Desktop Connection?
You'll need this later.
- Make sure you have Windows 10 Pro. To check, go to Start > Settings > System > About and look for Edition . ...
- When you're ready, select Start > Settings > System > Remote Desktop, and turn on Enable Remote Desktop.
- Make note of the name of this PC under How to connect to this PC. You'll need this later.
How to set up windows for remote file access?
- Select Start.
- In your programs list, Expand Windows Accessories, then select Remote Desktop Connection. ...
- Enter your home computer's IP address, then select Connect.
- Enter your Home computer's username and password, then select OK.
- Your computer is not certified by a third party verification service. ...
Is rdweb secure?
Using Remote Web Access is fine but is less secure than a good VPN, especially if you don't take extra precautions to secure it, i.e. using an alternate server only for RWA, placing it in a DMZ, getting a valid 3rd party SSL cert, etc. Thanks for your feedback! This person is a verified professional.

Is remote access secure?
Remote access solutions could leave you vulnerable. If you don't have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data. Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular.
How do you secure remote access to a network?
Use virtual private networks (VPN) - Many remote users will want to connect from insecure Wi-Fi or other untrusted network connections. VPNs can eliminate that risk, however VPN endpoint software must also be kept up-to-date to avoid vulnerabilities that can occur from older versions of the software client.
Why is remote access not secure?
In many cases, servers with RDP publicly accessible to the internet have failed to enable multi-factor authentication (MFA). This means that an attacker who compromises a user account by exposing a weak or reused password through a brute force attack can easily gain access to a user's workstation via RDP.
Which method of remote access is the most secure?
Implement a Secure Connection for Remote Network AccessWired Connection: A wired connection is the most secure method for remote network access.Home Wi-Fi: The second most secure network connection is using a secured home Wi-Fi connection.More items...•
What are potential risks associated with remote access?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
What happens if you give someone remote access to your computer?
This can be even worse than just conning you out of money, as undetected malware can allow hackers to steal your identity, including your passwords and financial information, over and over again, even if you get new passwords and account numbers.
Which is more secure to use when connecting to a device virtually?
VPNs allow employees working remotely to connect to a corporate network by routing their activity through a secure server. VPN systems encrypt data transmitted over the network, so that data is unusable to an attacker eavesdropping on the connection.
Which is a more secure form of remote access over a network?
Virtual private network (VPN)Virtual private network (VPN) – The most common and well-known form of secure remote access, VPNs typically use the public Internet to connect to a private network resource through an encrypted tunnel.
Which protocol for remote access is more secure and why?
POINT-TO-POINT TUNNELING PROTOCOL (PPTP) It's used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network. PPTP is a great option because it's simple and secure.
Which is a more secure form of remote access over a network?
Virtual private network (VPN)Virtual private network (VPN) – The most common and well-known form of secure remote access, VPNs typically use the public Internet to connect to a private network resource through an encrypted tunnel.
Which option creates a secure connection for remote workers?
The only way to secure your remote workforce is a secure VPN. Employees must connect from their laptops, desktops and mobile devices over a VPN connection. It's the secure, private method for virtually entering the corporate office, so to speak.
What is secure remote access?
Secure remote access refers to any security policy, solution, strategy or process that exists to prevent unauthorized access to your network, its resources, or any confidential or sensitive data. Essentially, secure remote access is a mix of security strategies and not necessarily one specific technology like a VPN.
What technologies are used for secure remote access?
Secure remote access is comprised of a multitude of security solutions and technologies. Some of the most prominent include the following:
Secure remote access solution
Enables employees with precise access to the applications and data required to do their job from anywhere.
Why is secure remote access important?
With the work from home shift in the workforce, endpoints are accessing corporate networks from multiple locations. Today, employees’ home networks are often the originating point for network connections, multiplying the risk on both home and corporate networks.
What are the benefits of secure remote access?
While the benefits of secure remote access are numerous, there are four key advantages in which to focus on:
Can secure remote access be achieved without VPN?
Yes. A robust cloud-based, highly secure remote access solution can provide unified protection for virtually all users against web-based threats — independent of a VPN connection.
How can AT&T help organizations with secure remote access?
AT&T Cybersecurity is uniquely positioned to help organizations address these immediate challenges with an eye toward the future by helping them balance connectivity, collaboration, and cybersecurity affordably.
What is secure remote access?
Secure remote access describes the ability to securely access networks, devices, and applications from a “remote” location, which means “off the network.”
Why are IPs never exposed to the internet?
IPs are never exposed to the internet, creating a “darknet” and making the network impossible to find. Apps segmentation ensures that once users are authorized, application access is granted on a one-to-one basis so that authorized users have access only to specific applications rather than full access to the network.
What is Zscaler private access?
Looking more closely, Zscaler Private Access (ZPA) service provides secure remote access to internal applications in the cloud without placing users on the corporate network. The cloud service requires no complex remote access VPN gateway appliances and uses cloud-hosted policies to authenticate access and route user traffic to the closest application location to them. ZPA is a true software-defined solution that can work in conjunction with direct access technology. It directly connects customer data centers with cloud service provider data centers.
How does a VPN work?
VPNs work by extending the internal network to external users so they can access resources on the network. Opening the network in this way enables it to be “found” by your remote users, but it also means it can be found by adversaries. They can (and do) exploit the VPN attack surface to infiltrate the network, deliver malware such as ransomware, launch denial-of-service attacks, and exfiltrate critical business data.
Why is VPN so bad?
Trust is inherent and often excessive for those inside the network. 2. There is a increased risk of external access to the network.
How does ZTNA improve security?
ZTNA improves your security posture by drastically reducing your attack surface. Application access is decoupled from network access. ZTNA moves away from network-centric security and instead focuses on securing the connection between user and application.
What is ZTNA security?
ZTNA takes a user-to-application approach rather than a network-centric approach to security . The network becomes deemphasized, and the internet becomes the new corporate network, leveraging end-to-end encrypted TLS micro-tunnels instead of MPLS.
How to protect your network from remote access?
You should set up firewalls to restrict access using software or hardware or both.
How to protect your computer when using remote access?
Here are some steps you can take to help protect your computer and data while relying on remote access. Maintain strong passwords.
What is remote computer access?
Many people take their laptops with them to do things like finish a business presentation while waiting for a flight at the airport. But a lot of those laptops may not have bigger, important files on them. You might leave those files at work or at home on your desktop computer.
How to protect remote desktop from hackers?
Use a secure Virtual Private Network (VPN). If you set up a VPN, your remote desktop server won’t be connected directly to the internet. It will only be exposed on your local network, which could leave it less vulnerable to hackers.
What is remote access software?
Remote computer access software lets you access networks and computers remotely. It can enable file sharing. It’s like having a remote control for a computer or system that isn’t near you. You’ll be able to remotely download files and applications from your desktop or another person’s computer onto your laptop or your cell phone. Remote access also gives you control over that remote device
Why is it important to limit the number of users who can log in?
Remote computer access can help businesses, individuals, and families in a variety of ways. But it’s important to make remote access secure .
Why is it important to lock your computer?
Set up an account lockout policy. To help guard against hackers implementing brute-force attacks with automated password-guessing tools, it’s important to set your computer to lock your accounts when someone enters an incorrect password a set number of times.
What should security teams do if on-premises network and email security mechanisms are no longer available?
Recommendation: If some on-premises network and email security mechanisms are no longer available, security teams should double down on educating users to identify phishing attempts and to choose strong, unique passwords, encouraging the use of a password manager. They should also implement client certificates and multi-factor authentication in order to prevent attackers from gaining access through unsecured devices.
Why is it important to enforce access based on user identity?
Recommendation: It’s critical that companies enforce access based on user identity, allowing specific groups access to only what they need to get their jobs done, and expanding access from there on an as-needed basis.
Why do companies use VPNs?
Historically, many companies deployed VPNs primarily for technical people needing access to critical technology assets. Not so much the case anymore – VPNs are often encouraged for all users as a more secure connection than home or public networks.
What are the risks of using a VPN?
Here are five top security risks that teams must deal with, as well as technology and user education best practices to keep users and data safe: 1. Weak remote access policies. Once attackers get access to a virtual private network (VPN), they can often penetrate the rest of the network like a hot knife through butter.
What is XDR in security?
Recommendation: Rather than invest in point solutions, consider security platforms that maximize integration between systems, limiting the amount of switching between tools and providing visibility into all data – including remote user activity. Extended detection and response (XDR) not only protects endpoints, but also applies analytics across all your data to find threats like unusual access or lateral movement, and simplifies investigations by stitching together data and identifying the root cause.
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
What is the first thing that’s required to ensure smooth remote access via a VPN?
The first thing that’s required to ensure smooth remote access via a VPN is to plan out a comprehensive network security policy.
Why is IPSEC used?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
What are the implications of IPSec connections for corporations?
What are the implications of IPSec connections for corporations, considering the very nature of this connection? Well, your employee will only be able to access the network from a single, authorized device. Security is further boosted by the enforcement of antivirus and firewall policies.
What is IPSEC encryption?
IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect data flows between hosts and security gateways.
Why use two factor authentication for VPN?
Adopting two-factor authentication for remote access through VPN further boosts your network security. Now let’s take a look at why you should choose a particular VPN type as a secure connection methodology instead of the alternatives.
What is the line of defense for remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly.
Types of Tunneling and Encryption
Tunneling involves using protocols to encapsulate or encrypt data packets so that will pass through the Internet in a secure fashion. Think of encapsulation and tunneling like peas in a pod. The peas are the data packets (unencrypted) and the pod encapsulates or encrypts the peas so they cannot be seen.
Remote Access
Here is a high level example (Figure 1) of how a remote host can connect to an internal corporate network which can be referred to when reviewing the types of remote access solutions: Remote Access Service (RAS), Point-to-Point over Ethernet (PPPoE), Remote Desktop Protocol (RDP), Independent Computing Architecture (ICA), and Secure Shell (SSH).
Network Intrusion & Protection
An Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) are network security appliances that can be host-based, network-based or a combination of both.
Network Security Traps
A honeypot is a computer host that has been set up to attract hackers to learn what tactics they are using to infiltrate a network. It monitors their movements and gives a network administrator insight to where future attacks may come from.
Why is remote access important?
It is essential for these individuals to have safe, anytime, anywhere access to corporate networks and services.
What are the risks of remote access?
Many potential risks accompany vendor remote access —from introducing malware into your systems to technical and business dangers.
What percentage of Verizon network intrusions exploited weak or stolen credentials?
According to Verizon’s Data Breach Investigation Report, “76 percent of network intrusions exploited weak or stolen credentials.” Since vendors don’t need constant access to your network, they often use one remote access tool license and share generic logins and passwords across technicians. This makes the credentials easy for hackers to guess. What’s more, the vendor’s ex-employees often retain remote access to your systems.
How many factor authentication is required for a network?
For optimum protection and a clean audit trail, require everyone who accesses your network to use unique credentials and at least two-factor authentication. This will make it harder for a hacker to successfully use stolen vendor credentials.
What happens if you give access to an outsider?
Recognize that granting system access to an outsider lowers your security level to that of the external provider. If they lack strong security controls, they become your weakest link. If a hacker compromises their system, that partner can become a backdoor into your environment .
Why is reducing network entry points important?
By reducing network entry points to the least amount that are necessary, you increase your ability to monitor and block unwanted activity on your network.
Where should a server be placed?
Because of this, NIST recommends; in most cases, that a server should be placed at an enterprise's network perimeter so it serves as a single point of entry to the network and enforces the remote work security policy before any remote access traffic is permitted into the enterprise's internal networks.
How secure is a VPN?
Many VPN providers claim to be the best at protecting sensitive personal information when employees connect to public networks. And in some instances, the VPN client does work as promised. By providing a strong encrypted connection on IT-manged devices, these solutions focus on safeguarding private information and protecting VPN users’ personal data. Someone snooping for security flaws in a public WiFi hotspot would be unable to see internet activity—unlike the user who takes advantage of public internet access without protection.
Why is VPN not secure?
The reason? Unlike zero trust security solutions, traditional networking models put blind trust in users.
What does it mean to connect to a VPN server?
Connecting to a VPN server means all the traffic is backhauled to a datacenter. That obviously includes not only the business traffic, but personal traffic as well. With Citrix Workspace, employee data stays private because only corporate data is sent through the data center.
Why are VPNs so hard to scale?
VPNs are hard to scale and create a poor user experience. Most VPN services were deployed to serve a small percentage of a remote workforce. When most of the workforce is remote, VPNs become bottlenecks, especially when delivering traditional client-server applications that consume a lot of bandwidth.
What is Citrix Analytics for Security?
Citrix Analytics for Security uses machine learning to understand and monitor end user behavior across devices, data, networks, apps and virtual desktops. When it detects risky behavior, it can take proactive, automated action like session recording, logging the user out of their account or expiring links to shared documents.
How does VPN work?
VPN security works to shield online activity from hackers and Internet Service Providers when employees work remotely. Its sole job is to shield online activity from snoops and spies looking to steal sensitive data. What it doesn’t account for is all the ways your attack surface is expanding.
Why do companies use VPNs?
Remote work and business travel. Public WiFi networks and prying eyes. Data security and personal privacy. These are among the top reasons companies choose to use virtual private networks. But do VPNs really provide the protection you’ve been promised?