What is remote access trojan RAT?
A Remote Access Trojan (RAT) infects a computer with a virus that gives cyberattackers unrestricted access to the data on the PC by using the victim’s access permissions. A RAT can include backdoors into the computer system, which can be used to create a botnet and spread to other devices as well. 1. what is the best remote access trojan?
How can I create a Trojan?
There are several tools available like DrakComet, Cyber gate, ProRAT which you can use to create a trojan with several modifications like which message to display when the victim clicks on the .exe file that has been created by the attacker, changing the icon etc.
What is the rat Trojan used for?
Answer Wiki. RAT is used to remotely connect and manage single or multiple computers. RAT is one of the most dangerous Trojan because it compromises features of all types of Trojans. It provides an attacker with nearly unlimited access to host computer along with Screen Capture, File management, shell control and device drivers control.
What is a Trojan Horse on a computer?
Trojan horses are malicious programs that look legitimate, but can take control of your computer if they are installed on your computer. In general, a Trojan is designed to damage, disrupt, steal, or in general cause some other harm to your data or network. What Is The Best Remote Access Tool?

Are remote access Trojans illegal?
Law enforcement officials say that simply possessing a remote-access tool isn't illegal. In fact, remote-access tools are often used for IT support purposes in corporate environments.
How are remote access Trojans delivered?
A remote access Trojan (RAT) is a malware program that includes a back door for administrative control over the target computer. RATs are usually downloaded invisibly with a user-requested program -- such as a game -- or sent as an email attachment.
What are the variant of remote access Trojan?
There are a large number of Remote Access Trojans. Some are more well-known than others. SubSeven, Back Orifice, ProRat, Turkojan, and Poison-Ivy are established programs. Others, such as CyberGate, DarkComet, Optix, Shark, and VorteX Rat have a smaller distribution and utilization.
Can Norton detect RATs?
Antivirus software like Bitdefender, Kaspersky, Webroot, or Norton, can detect RATs and other types of malware if they infect your devices.
Is TeamViewer a RAT?
The JS script then launches the malware, which installs a version of TeamViewer, a remote administration tool (RAT), modified by the attackers. As in earlier attacks, the attackers use a malicious DLL library to hide the graphical user interface in order to control the infected system without the user's knowledge.
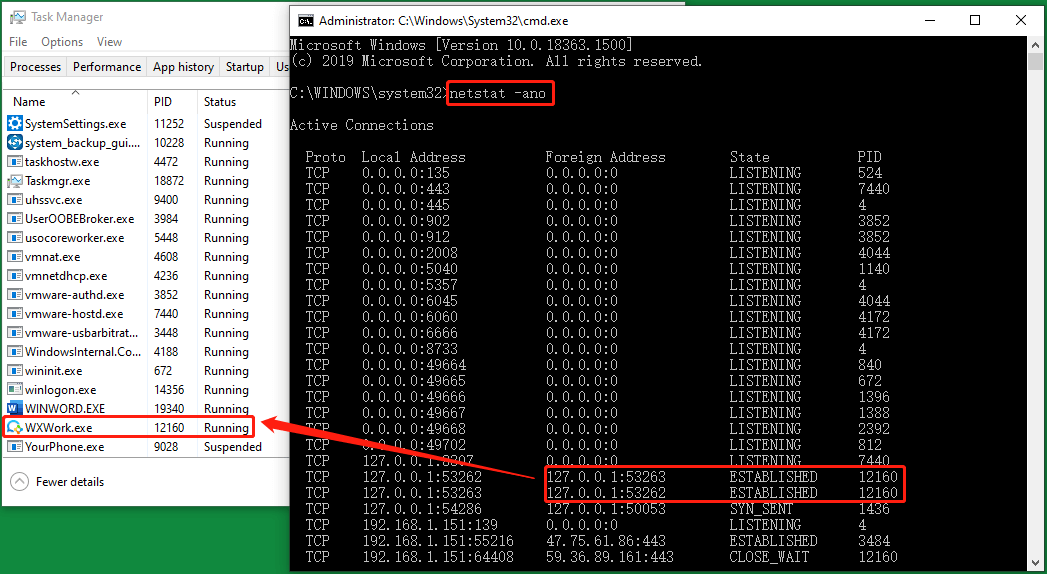
How do I know if someone is accessing my computer remotely?
You can try any of these for confirmation.Way 1: Disconnect Your Computer From the Internet.Way 2. ... Way 3: Check Your Browser History on The Computer.Way 4: Check Recently Modified Files.Way 5: Check Your computer's Login Events.Way 6: Use the Task Manager to Detect Remote Access.Way 7: Check Your Firewall Settings.More items...•
Which is the best remote access Trojan?
Blackshades is a Trojan which is widely used by hackers to gain access to any system remotely. This tool frequently attacks the Windows-based operating system for access.
How can I remotely access another computer over the Internet?
You can set up remote access to your Mac, Windows, or Linux computer.On your computer, open Chrome.In the address bar, enter remotedesktop.google.com/access .Under “Set up Remote Access,” click Download .Follow the onscreen directions to download and install Chrome Remote Desktop.
What is meant by logic bomb?
A logic bomb is a string of malicious code inserted intentionally into a program to harm a network when certain conditions are met.
Can antivirus detect Trojan?
An effective antivirus program searches for valid trust and app behavior, as well as trojan signatures in files in order to detect, isolate and then promptly remove them.
Does Norton find Trojans?
Resolution. Norton Antivirus detects and removes Trojan horses. Via LiveUpdate, administrators can download to a computer the latest virus definitions, which contain information that the scan engine needs to find existing and emerging threats on a system.
Can you get a RAT on your Iphone?
So someone would need direct physical access to your iOS device and a computer to install a RAT exploit into it. Even if you accessed a web site or email with a RAT package hidden in it, it cannot execute or do anything on a normal iOS installation.
What is a backdoor Trojan?
Backdoor malware is generally classified as a Trojan. A Trojan is a malicious computer program pretending to be something it's not for the purposes of delivering malware, stealing data, or opening up a backdoor on your system.
Are PUPs malware?
Type and source of infection. Detections categorized as PUPs are not considered as malicious as other forms of malware, and may even be regarded by some as useful. Malwarebytes detects potentially unwanted programs for several reasons, including: They may have been installed without the user's consent.
What is data sending Trojan?
A data-sending Trojan is a kind of Trojan virus that relays sensitive information back to its owner. This type of Trojan can be used to retrieve sensitive data, including credit card information, email addresses, passwords, instant messaging contact lists, log files and so on.
Is a backdoor malware?
A backdoor is a malware type that negates normal authentication procedures to access a system. As a result, remote access is granted to resources within an application, such as databases and file servers, giving perpetrators the ability to remotely issue system commands and update malware.
How Is A Remote Access Trojan Executed?
An attacker uses a Trojan to execute a program file on a system. Once the user attempts to open the file, the Trojan is executed, and some dangerous actions are taken. A remote access Trojan program uses a backdoor to control the target machine with administrative privileges.
What Is Remote Access Virus?
Remote access Trojan (RAT) programs are malware programs that allow the target computer to be controlled remotely. A user may download RATs invisibly with a program they request — such as a game — or send them as an email attachment. Viruses and other malware are distributed.
How Bad Is A Trojan Virus?
In addition to stealing your most personal information, Trojan viruses can also cause identity theft and other serious cybercrimes.
What Is The Purpose Of A Trojan Horse?
In general, a Trojan is designed to damage, disrupt, steal, or in general cause some other harm to your data or network.
Why Trojan Virus Is Bad?
As well, unlike viruses, Trojan horses are not self-replicating and are only spread by users who download them mistakenly, usually from an email attachment or by visiting an infected website.
What Is An Example Of A Trojan Virus?
A number of trojans are known to be malicious in government, including the Swiss MiniPanzer and MegaPanzer, as well as the German “state trojan” nicknamed R2D2. Governmentware in Germany exploits security gaps that are unknown to the general public and accesses smartphone data before it is encrypted.
Is Trojan Always Bad?
The term “Trojan horse” refers to a type of malicious software that infects computers and mobile devices. Trojan horses are usually disguised as benign or useful software that you download from the Internet, but they actually contain malicious code that can harm you.
How many parts does a Trojan have?
A Trojan generally has two parts Client and Server or Master and Slave. We can say Server is Slave and Client is Master. So a server side is installed on a remote host and the attacker manipulates it with client software.
Why is RAT the most dangerous Trojan?
RAT is one of the most dangerous Trojan because it compromises features of all types of Trojans.
How to download Cerberus RAT?
Type “Download Cerberus RAT” in Google search and download Cerberus RAT. Execute Cerberus file and launch program. Accept EULA and following interface will be launched in front of you.
What portal does the bad guy come from?
this realm is your computer the portal the bad guy comes from is your REMOTE ACCESS TROJAN and his computer is the Realm where all they think off is taking over earth, now this portal (REMOTE ACCESS TROJAN) gives the bad guy (Hacker) access to your world (PC) And believe me when i say he can do ANYTHING with your computer when he gains this access. steal saved passwords, keylogging, put on your camera, steal banking credentials, lock your computer and ask for ransom, the list is endless. catch my drift???
How to listen to client Cerberus?
Configuring To Listen On Client: To configure Cerberus to listen on specific port select options and put “Connection Password” and “Connection Ports” that were specified in Server. Wait for victim to execute server and then just right click on listening server and play with options.
How to use C in a server?
Using c I would code both the server and client side code and establish simple message relays. After that all you need to do is send the code to the system (<command>); and send the output back to the socket descriptor.
Is a rat a Trojan?
They can hide themselves in process space of legitimate program and hence never appear in task manager or system monitors. A Trojan generally has two parts Client and Serve. Continue Reading. RAT is used to remotely connect and manage single or multiple computers. RAT is one of the most dangerous Trojan because it compromises features ...
Does an attacker need Internet access?
Of course — an attacker needs the infected workstation has Internet access. But I think it’s not a big deal for some reasons.
Can an attacker customize a RAT?
An attacker can customize the RAT (change an icon, add a certificate etc), then compile and send it as a phishing email attachment. What’s next? Anything!
How to protect yourself from remote access trojans?
Just like protecting yourself from other network malware threats, for remote access trojan protection, in general, you need to avoid downloading unknown items; keep antimalware and firewall up to date, change your usernames and passwords regularly; (for administrative perspective) block unused ports, turn off unused services, and monitor outgoing traffic.
What is a RAT trojan?
RAT trojan is typically installed on a computer without its owner’s knowledge and often as a trojan horse or payload. For example, it is usually downloaded invisibly with an email attachment, torrent files, weblinks, or a user-desired program like a game. While targeted attacks by a motivated attacker may deceive desired targets into installing RAT ...
How does RAT malware work?
Once get into the victim’s machine, RAT malware will hide its harmful operations from either the victim or the antivirus or firewall and use the infected host to spread itself to other vulnerable computers to build a botnet.
Why do RATs use a randomized filename?
It is kind of difficult. RATs are covert by nature and may make use of a randomized filename or file path structure to try to prevent identification of itself. Commonly, a RAT worm virus does not show up in the lists of running programs or tasks and its actions are similar to those of legal programs.
Is Sub 7 a trojan horse?
Typically, Sub 7 allows undetected and unauthorized access. So, it is usually regarded as a trojan horse by the security industry. Sub7 worked on the Windows 9x and Windows NT family of OSes, up to and including Windows 8.1. Sub7 has not been maintained since 2014. 4.
Who created DarkComet?
5. DarkComet. DarkComet is created by Jean-Pierre Lesueur, known as DarkCoderSc, an independent programmer and computer security coder from France. Although this RAT application was developed back in 2008, it began to proliferate at the start of 2012.
Can a RAT remote access trojan be used on a computer?
Since RAT remote access trojan will probably utilize the legitimate apps on your computer, you’d better upgrade those apps to their latest versions. Those programs include your browsers, chat apps, games, email servers, video/audio/photo/screenshot tools, work applications…