Log in the the device > Go to enable mode > Go to configuration mode > Enable Telnet and set a password. Router0> enable Router0# conf terminal Enter configuration commands, one per line. End with CNTL/Z. Router0 (config)# line vty 0 4 Router0 (config-line)# transport input telnet Router0 (config-line)# password P@ssword123
Full Answer
How to configure remote access VPN on Cisco routers?
One of the easiest ways to configure simple remote access VPN functionality for your remote users is by configuring PPTP. This is supported on Cisco routers and will work with Windows OS flawlessly. PPTP (Point to Point Tunneling Protocol) is a quick and easy solution to offer remote access to users.
How do I configure a Cisco switch for remote management?
To accomplish this, the following will be done: (i) Assign IP addresses, subnetmask and default gateways. Implementation. The following configuration commands will the required to configure a Cisco switch for remote management. The commands used here a for the lab represented in the network topology used here.
How do I set up remote access from within a network?
The primary method of remote access from within a network is setting up a port to connect to the Management VLAN. This could be a routed port or use a VLAN interface if the device has a switch module of several types.
How to configure the remote access radio button?
In the Remote Access field, select a desired radio button corresponding to the type of Remote Access protocol. The protocol will be used to connect devices from a remote Wide Area Network (WAN) directly to the router. HTTPS is more secure than HTTP and is the recommended option. The available options are defined as follows.
How do I configure my router for remote access?
All you need to do is type the router IP or default gateway address in the web browser. Next, enter your username and password. Now, once you are in the router's web portal, look for the Remote Management option. Some routers called it Remote Access and it's usually found under Advanced Settings.
What do you need to configure on a switch to allow remote management?
To prepare a switch for remote management access, the switch must be configured with an IP address and a subnet mask. Keep in mind that to manage the switch from a remote network, the switch must be configured with a default gateway. This is very similar to configuring the IP address information on host devices.
How do I setup a VPN on my Cisco router?
Let us examine each of the above steps.Step 1: Creating Extended ACL. Next step is to create an access-list and define the traffic we would like the router to pass through the VPN tunnel. ... Step 2: Create IPSec Transform (ISAKMP Phase 2 policy) ... Step 3: Create Crypto Map. ... Step 4: Apply Crypto Map to the Public Interface.
What is remote web management in router?
Remote Management allows the administrators to login remotely to the system and access the web interface. It allows to access the network from a remote Wide Area Network (WAN). By default Remote Management is disabled. NOTE: When Remote Management is enabled the router can be accessed by anyone who know its IP address.
How do I remotely control a Cisco switch?
0:2112:19Cisco router and switch configure remote access (telnet/ssh) - YouTubeYouTubeStart of suggested clipEnd of suggested clipFor telnet in the way we need to do that is we edit the vty lines Pete definitely BTY stands forMoreFor telnet in the way we need to do that is we edit the vty lines Pete definitely BTY stands for virtual terminal 0 to 15. And then we need to tell it we want set a password we'll set that to Cisco.
How do I configure a Cisco Managed switch?
Step 1: Inspect your hardware. Check the model number of your shiny new switch. ... Step 2: Set up management IP. ... Step 3: Check VTP revision number. ... Step 4: Configure access ports. ... Step 5: Configure trunk ports. ... Step 6: Configure access ports. ... Step 7: Set up VTY line config.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What is IPsec configuration?
Internet Protocol Security (IPsec) is a set of security protocols used to transfer IP packets confidentially across the Internet. IPsec is mandatory for all IPv6 implementations and optional for IPv4.
WHAT IS GET VPN in Cisco?
Cisco GET VPN eliminates the need for compromise between network intelligence and data privacy in private WAN environments.
Can a router be remotely managed?
Remote Management is a feature that allows you to access, view, or change your Router Settings over the Internet. You need your router's WAN IP address, username, and password to show this on your device. If Remote Management is necessary, set rules to allow Remote Management for known IP addresses only.
What is remote config management?
What is remote config? Remote config (short for "remote configuration") is a software development technique for mobile apps where the behavior or features of an app can be changed remotely without having to publish an app update.
How do I manage my router?
Tap on the network name. Look for a 'gateway', 'router' or other entry in the list....Find router IP address on Android or iOSTap on Wi-Fi.Make sure your phone is connected to your router's Wi-Fi network.Tap the 'i' to the right of the network name.Your router's IP address is shown next to 'Router'
Which protocol should be used to manage a switch remotely?
Secure Shell (SSH) is a protocol that provides a secure (encrypted) management connection to a remote device.
Which of the following tools allow remote management of servers?
Which of the following tools allow for remote management of servers? Both Telnet and SSH are tools for remote management of servers.
Which service must be running in order to perform remote management in PowerShell?
On all other supported versions of Windows, you need to run the Enable-PSRemoting cmdlet to enable PowerShell remoting. The remoting features of PowerShell are supported by the WinRM service, which is the Microsoft implementation of the Web Services for Management (WS-Management) protocol.
How do I enable remote management in PowerShell?
PowerShell remoting is enabled by default on Windows Server platforms. You can use Enable-PSRemoting to enable PowerShell remoting on other supported versions of Windows and to re-enable remoting if it becomes disabled. You have to run this command only one time on each computer that will receive commands.
What is VPN on Cisco router?
This chapter explains the basic tasks for configuring an IP-based, remote access Virtual Private Network (VPN) on a Cisco 7200 series router. In the remote access VPN business scenario, a remote user running VPN client software on a PC establishes a connection to the headquarters Cisco 7200 series router.
How to verify that authentication proxy is successfully configured on the router?
To verify that the authentication proxy is successfully configured on the router, ask a user to initiate an HTTP connection through the router. The user must have authentication and authorization configured at the AAA server. If the user authentication is successful, the firewall completes the HTTP connection for the user. If the authentication is unsuccessful, check the access list and the AAA server configurations.
What command to use to verify PPTP?
After you complete a connection, enter the show vpdn tunnel command or the show vpdn session command to verify your PPTP and MPPE configuration.The following example contains typical output:
What is Cisco IOS firewall proxy?
Using the Cisco IOS firewall authentication proxy feature , network administrators can apply specific security policies on a per-user basis. Users can be identified and authorized on the basis of their per-user policy, and access privileges tailored on an individual basis are possible, in contrast with general policy applied across multiple users.
What is the radiusserverkey command?
Sets the authentication and encryption key for communications between the router and the AAA server. For RADIUS servers use the radiusserverkey command.
What is authentication proxy?
With the authentication proxy feature, users can log into the network or access the Internet via HTTP, and their specific access profiles are automatically retrieved and applied from an authentication server. The user profiles are active only when there is active traffic from the authenticated users.
How to display user authentication entries?
Display the user authentication entries using the show ip auth-proxy cache command in privileged EXEC mode. The authentication proxy cache lists the host IP address, the source port number, the timeout value for the authentication proxy, and the state of the connection. If the authentication proxy state is HTTP_ESTAB, the user authentication was successful.
How many steps are required to enable SSH on Cisco router?
There are four steps required to enable SSH support on a Cisco IOS router:
How to prevent non-SSH connections?
If you want to prevent non-SSH connections, add the transport input ssh command under the lines to limit the router to SSH connections only . Straight (non-SSH) Telnets are refused.
Why isn't the connect button enabled?
The Connect button is not enabled if you do not enter the host name and username. This screenshot shows that the login banner is displayed when Secure Shell connects to the router. Then, the login banner password prompt displays. The PuTTY client does not require the username to initiate the SSH connection to the router.
Can you test SSH for outbound reverse telnets?
If you need outbound SSH terminal-line authentication, you can configure and test SSH for outbound reverse Telnets through Carter , which acts as a comm server to Philly.
Is Cisco ASA Firewall Fundamentals self published?
He is a self-published author of two books ("Cisco ASA Firewall Fundamentals" and "Cisco VPN Configuration Guide") which are available at Amazon and on this website as well.
Does Cisco ASA support PPTP?
Cisco supports PPTP on its IOS routers. Cisco ASA firewalls do not support termination of PPTP on the firewall itself.
Can a remote user use PPTP?
Like other types of remote access solutions, a remote user can use PPTP to connect to a corporate network and be treated as directly connected to that internal network even if he/she is physically outside the network. PPTP is always implemented between a server (e.g a Cisco router) and a client (e.g a windows workstation).
Does PPTP work with IPSEC?
However, you should note that PPTP does not offer the strong encryption and security offered by IPSEC or SSL VPN remote access solutions. Although the Microsoft Point-to-Point Encryption (MPPE) supported by Cisco routers offers a good degree of security, PPTP remote access should not be used in situations where you need to provide access ...
What is Cisco Secure Endpoint?
Cisco Secure Endpoint New packages fit for every organization Every Cisco Secure Endpoint (formerly AMP for Endpoints) package comes with Cisco SecureX built-in. It’s our cloud-native platform that integrates all your security solutions into one view wit... view more
Do you need to set IP domain name for generating key?
Apart from those commands as sandeep stated here... you need to set ip domain-name as well for generating the key. Because you key will get generated based on your hostname... i.e. .
Is Cisco 1841 compatible with Cisco 1841?
Those advanced IP Services are compatible with cisco 1841 routers..... current IOS is in specific to broadband which has some limited facilities..... for eg advip ios has much more features of IP SLA but broadband IOS has only IP SLA Responder feature.... Like this way you have many other differences mate....
Is Cisco Secure a partner of IBM?
This month, we're excited to bring awareness to a newly formed partnership between Cisco Secure and IBM. Securing today's dynamic enterprise applications is critical. With hybrid and multi-cloud adoption, traditional network-based security ran into limita... view more
Does Cisco IOS support SSH?
You will need an image that supports SSH (images with k9) Yes. Starting with Cisco IOS Software Release 12.4 (1), SSH is supported in all images with the following exceptions: IP Base without Crypto and Enterprise Base without Crypto. Use this command: Router (config)# crypto key generate rsa.
Objective
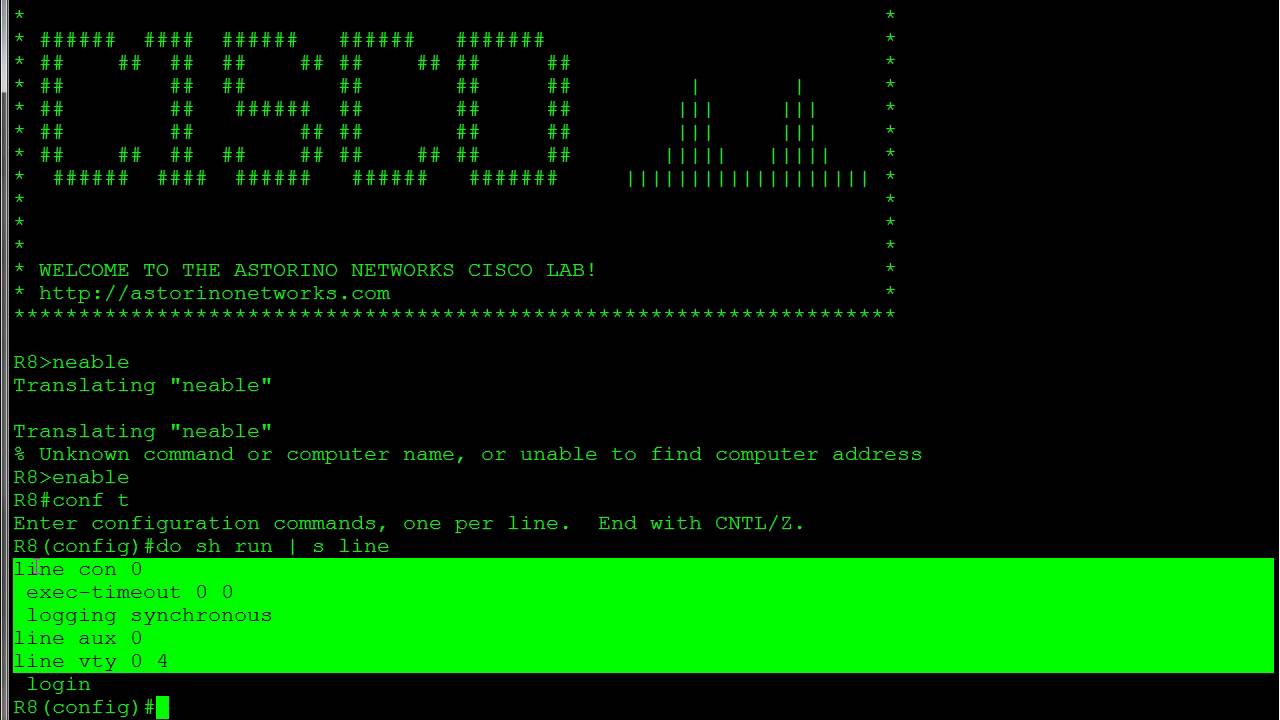
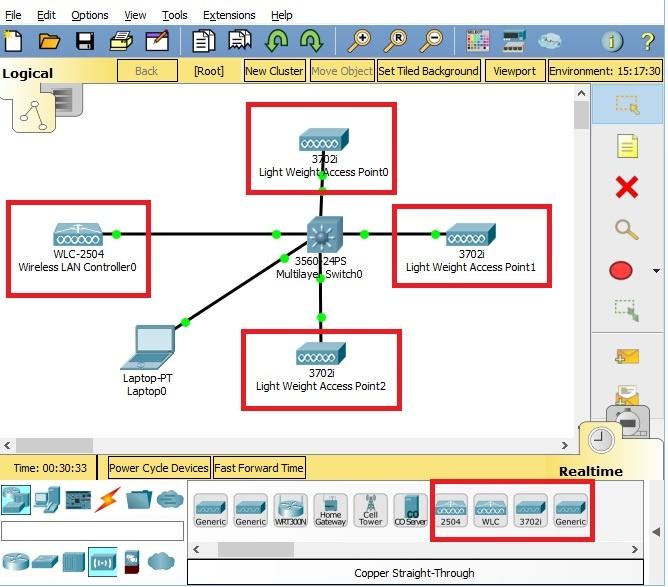
The objective of this lab is to configure the switch for remote management such that the laptop PC residing on a remote network be used to login and manage it via ssh . To accomplish this, the following will be done:
Implementation
The following configuration commands will the required to configure a Cisco switch for remote management. The commands used here a for the lab represented in the network topology used here. However, the solution can be achieved in many different ways.
Verification
To verify that I have configured the Cisco switch for remote management via ssh, I try to access the switch using the laptop on the network 192.168.0.0/24 using ssh. Remember that both the laptop and the switch are on different networks. See the result below.

Introduction
Prerequisites
- Requirements
The Cisco IOS image used must be a k9(crypto) image in order to support SSH. For example c3750e-universalk9-tar.122-35.SE5.taris a k9 (crypto) image. - Components Used
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command. The informati…
Test Authentication
- Authentication Test without SSH
First test the authentication without SSH to make sure that authentication works with the router Carter before you add SSH. Authentication can be with a local username and password or with an authentication, authorization, and accounting (AAA) server that runs TACACS+ or RADIUS. (Auth… - Authentication Test with SSH
In order to test authentication with SSH, you have to add to the previous statements in order to enable SSH on Carter and test SSH from the PC and UNIX stations. At this point, the show crypto key mypubkey rsacommand must show the generated key. After you add the SSH configuration, …
Optional Configuration Sets
- Prevent Non-SSH Connections
If you want to prevent non-SSH connections, add the transport input sshcommand under the lines to limit the router to SSH connections only. Straight (non-ssh) Telnets are refused. Test to ensure that non-SSH users cannot Telnet to the router "Carter". - Set Up an IOS Router or Switch as SSH Client
There are four steps required to enable SSH support on a Cisco IOS router: 1. Configure the hostname command. 2. Configure the DNS domain. 3. Generate the SSH key. 4. Enable SSH transport support for the vty. If you want to have one device act as an SSH client to the other, yo…
Debug and Show Commands
- Before you issue the debug commands described here, refer to Important Information on Debug Commands. Certain show commands are supported by the Output Interpreter Tool (registered to customers only), which allows you to view an analysis of showcommand output. 1. debug ip ssh Displays debug messages for SSH. 2. show ssh Displays the status of SSH server connectio…
Sample Debug Output
- Server Debug
Note: This is Solaris machine output.
Tips
- If your SSH configuration commands are rejected as illegal commands, you have not successfully generated a RSA key pair for your router. Ensure you have specified a host name and domain. Then use t...
- When you configure RSA key pairs, you can get these error messages:
- The number of allowable SSH connections is limited to the maximum number of vty configur…
- If your SSH configuration commands are rejected as illegal commands, you have not successfully generated a RSA key pair for your router. Ensure you have specified a host name and domain. Then use t...
- When you configure RSA key pairs, you can get these error messages:
- The number of allowable SSH connections is limited to the maximum number of vty configured for the router. Each SSH connection uses a vtyresource.
- SSH uses either local security or the security protocol configured through AAA on your router for user authentication. When you configure AAA, you must ensure that the console is not run under AAA....