What is VPN on Cisco router?
How to verify that authentication proxy is successfully configured on the router?
What command to use to verify PPTP?
What is Cisco IOS firewall proxy?
What is the radiusserverkey command?
What is authentication proxy?
How to display user authentication entries?
See 4 more
About this website
How do I setup a VPN remote access?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
How do I connect my Cisco router to a VPN?
6:3815:11How to Setup a Cisco Router VPN (Site-to-Site) - YouTubeYouTubeStart of suggested clipEnd of suggested clipPre share and now we need to identify our. Key itself. So we'll type crypto AIESEC imp key is VPNMorePre share and now we need to identify our. Key itself. So we'll type crypto AIESEC imp key is VPN key and this is just a text string but it has to match on both ends of the connection.
What is Cisco remote access VPN?
This allows remote users to connect to the ASA and access the remote network through an IPsec encrypted tunnel. The remote user requires the Cisco VPN client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network.
Does VPN allow remote access?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
How do I setup a Cisco VPN server?
Steps for setting up a VPNStep 1: Line up key VPN components. ... Step 2: Prep devices. ... Step 3: Download and install VPN clients. ... Step 4: Find a setup tutorial. ... Step 5: Log in to the VPN. ... Step 6: Choose VPN protocols. ... Step 7: Troubleshoot. ... Step 8: Fine-tune the connection.
Where is Cisco VPN client configuration file?
Resolution:Operating SystemLocationWindows 8%ProgramData%\Cisco\Cisco AnyConnect Secure Mobility Client\ProfileWindows 10%ProgramData%\Cisco\Cisco AnyConnect Secure Mobility Client\ProfileMac OS X/opt/cisco/anyconnect/profileLinux/opt/cisco/anyconnect/profile3 more rows•Apr 27, 2022
Why is my Cisco VPN not connecting?
Solution: Try unplugging your network cable and reinserting it. If this does not work, you may have a link issue. The Network Access Manager may not be able to determine the correct link state of your adapter. Check the Connection Properties of your Network Interface Card (NIC) driver.
Is Cisco VPN client free?
Cisco AnyConnect is a free, easy to use, and worthwhile VPN client for Microsoft Windows computers. It's secure and doesn't require a lot of maintenance.
How much does Cisco VPN cost?
OverviewAdditional DetailsPrice:$102.00MSRP:$150.53Mfr Part #:ASA-AC-E-5515=SHI Part #:254045704 more rows
What is the difference between VPN and remote access?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
Which VPN is best for remote access?
Best Remote Access VPNs for business.Perimeter 81 – Best all-round business VPN.GoodAccess – Security Strategy Options.ExpressVPN – Lightning Fast VPN.Windscribe – VPN with Enterprise-Friendly Features.VyprVPN – Secure VPN with Business Packages.NordVPN – Security-first VPN.More items...•
How do I connect VPN outside of network?
How does it work?Download your firewall's VPN client software - usually available for free from the vendors website (SonicWall, Checkpoint, WatchGuard, Meraki, etc).Install the software.Enter your organisation's public IP address.Enter your username and password and connect.
How does Cisco AnyConnect VPN Work?
Remote and mobile users use the Cisco AnyConnect Secure VPN client to establish VPN sessions with the adaptive security appliance. The adaptive security appliance sends web traffic to the Web Security appliance along with information identifying the user by IP address and user name.
How can I use VPN?
Open your phone's Settings app.Tap Network & internet. VPN. If you can't find it, search for "VPN." If you still can't find it, get help from your device manufacturer.Tap the VPN you want.Enter your username and password.Tap Connect. If you use a VPN app, the app opens.
How do I change the IP address on a Cisco AnyConnect router?
If you are in ASDM, go to Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Client Profiles, highlight the client profile you have and click the “Edit” button. Update the hostname to be the domain name and update the host address to be the new IP address and click OK.
Is Cisco AnyConnect an SSL VPN?
Cisco SSL AnyConnect VPN is a real trend these days – it allows remote users to access enterprise networks from anywhere on the Internet through an SSL VPN gateway using a web browser. During the establishment of the SSL VPN with the gateway, the client downloads and installs the AnyConnect VPN client from VPN gateway.
Cisco IOS VPN Configuration Guide - Cisco
Bias-Free Language. The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality.
How to enable the Cisco VPN Client on Windows 10
Cisco's VPN Client v5 is not officially supported on Windows 10--but what if you rely on the software to communicate remotely to business resources? Here's a workaround to help you out.
How to configure Cisco IOS Remote Access IPSEC VPN - NAT OVERLOAD
crypto isakmp client configuration group VPNGROUP key secret dns 8.8.8.8 pool VPNRAPOOL acl VPN_SPLIT Step 4. Create a the address Pool and the access-list used for traffic encryption
Why is VPN better than other methods of remote communication?
Communication with a VPN connection provides a higher level of security compared to other methods of remote communication, keeping private networks closed to people who don’t have authorized access.
How to get a VPN up and running?
The simplest way to get your VPN up and running is to install clients from your VPN provider. However, they may not offer software for every platform you need, such as Windows, iOS, and Android. Even if they don't, it's better to install what they offer first and then confirm that your VPN account is operating correctly.
Why is my VPN connection so slow?
Slow connection speeds. If you're using a VPN client that provides free VPN service, your connection speed may be slow, as these providers do not usually offer high-speed connections. Consider whether the speed is sufficient for business needs.
How to fix VPN not working?
Usually, your VPN provider's client will start working right away. But if that's not the case, try these steps: 1 Shut down and reopen the client and try rebooting your device. 2 If you have any other VPN software running, make sure you're disconnected, then close it down.
What is the oldest VPN protocol?
Point-to-Point Tunneling Protocol is one of the oldest VPN protocols. But it is becoming less widely used since there are faster and more secure protocols available.
What is VPN in business?
Businesses often use VPN connections because they're a more secure way to help employees remotely access private company networks, even when they're working outside the office. The VPN lets remote devices, like laptops, ...
What to do if VPN doesn't work?
If, for some reason, your VPN provider doesn't offer software for the devices your business uses, check the provider's website for guides on manual setup. Hopefully, you'll find the documentation you need. If you don't, search for other providers' setup guides that use the same devices.
What is the simplest way to connect to the Internet?
The simplest connectivity to the Internet is to use a single device to provide the connectivity and firewall function to the Internet. With everything being in a single device, it is easy to address translation and termination of the VPN tunnels. Complexity arises when you need to add extra Cisco 7200 series routers to the network. This normally leads people into building a network where the corporate network touches the Internet through a network called the DMZ, or demilitarized zone.
How does IPSec work?
In IPSec tunnel mode, the entire original IP datagram is encrypted, and it becomes the payload in a new IP packet. This mode allows a network device, such as a router, to act as an IPSec proxy. That is, the router performs encryption on behalf of the hosts. The source router encrypts packets and forwards them along the IPSec tunnel. The destination router decrypts the original IP datagram and forwards it on to the destination system. Tunnel mode protects against traffic analysis; with tunnel mode, an attacker can only determine the tunnel endpoints and not the true source and destination of the packets passing through the tunnel, even if they are the same as the tunnel endpoints.
What is IPSEC security?
IPSec is a framework of open standards, developed by the Internet Engineering Task Force (IETF), that provides data confidentiality, data integrity, and data authentication between participating peers. IPSec provides these security services at the IP layer; it uses IKE to handle negotiation of protocols and algorithms based on local policy, and to generate the encryption and authentication keys to be used by IPSec. IPSec can be used to protect one or more data flows between a pair of hosts, between a pair of security Cisco 7200 series routers, or between a security Cisco 7200 series router and a host.
What is Cisco IOS firewall?
Cisco IOS software provides an extensive set of security features with which you can configure a simple or elaborate firewall, according to your particular requirements. When you configure Cisco IOS firewall features on your Cisco router, you turn your router into an effective, robust firewall.
Where is NAT configured?
NAT is configured on the router at the border of a stub domain (referred to as the inside network) and a public network such as the Internet (referred to as the outside network ). NAT translates the internal local addresses to globally unique IP addresses before sending packets to the outside network.
Do IKE policies require companion configuration?
Depending on which authentication method you specify in your IKE policies, you need to complete an additional companion configuration before IKE and IPSec can successfully use the IKE policies.
Does Cisco 7200 support intrusion detection?
Note Although Cisco 7200 series routers support intrusion detection features, intrusion detection configuration procedures are not explained in this guide. For detailed information on intrusion detection, refer to the Intrusion Detection Planning Guide.
What is Cisco Easy VPN?
The Cisco Easy VPN client feature eliminates much of the tedious configuration work by implementing the Cisco Unity Client protocol. This protocol allows most VPN parameters, such as internal IP addresses, internal subnet masks, DHCP server addresses, WINS server addresses, and split-tunneling flags, to be defined at a VPN server, such as a Cisco VPN 3000 series concentrator that is acting as an IPSec server.
What are the two types of VPNs?
Two types of VPNs are supported—site-to-site and remote access. Site-to-site VPNs are used to connect branch offices to corporate offices, for example. Remote access VPNs are used by remote clients to log in to a corporate network. The example in this chapter illustrates the configuration of a remote access VPN that uses ...
What is a Cisco 870 router?
The Cisco 870 series routers support the creation of Virtual Private Networks (VPNs). Cisco routers and other broadband devices provide high-performance connections to the Internet, but many applications also require the security of VPN connections which perform a high level of authentication and which encrypt the data between two particular ...
Does Cisco 850 support VPN?
Note The material in this chapter does not apply to Cisco 850 series routers. Cisco 850 series routers do not support Cisco Easy VPN.
Can you negotiate with a peer in a security association?
Note With manually established security associations, there is no negotiation with the peer , and both sides must specify the same transform set.
Does Cisco Easy VPN support multiple destinations?
Note The Cisco Easy VPN client feature supports configuration of only one destination peer. If your application requires creation of multiple VPN tunnels, you must manually configure the IPSec VPN and Network Address Translation/Peer Address Translation (NAT/PAT) parameters on both the client and the server.
What is the advantage of Easy VPN?
The main advantage of Easy VPN is that IPSec policies are centrally managed on the server (Head end router providing IPSec feature) and are pushed to client devices. This policy push is known as Mode Configuration. This requires minimum configuration on the end-user side. The IPSec policies can be configured on a RADIUS server and then downloaded to an Easy VPN server, further reducing configuration required on the Easy VPN server.
What is the command ezvpn-author group radius?
In this configuration the command ‘aaa authorization network ezvpn-author group radius’ tells us that the configuration for Easy VPN group (policies) must be downloaded from a RADIUS server.
How many group policies do you need to configure a Radius server?
Let us be more specific about the requirement so that we can configure our RADIUS server. In our requirement we need to create two group policies:
What is a remote control policy?
Controlling policy for remote access through a RADIUS server is only a single example among multiple available. There is lot that can be achieved with a RADIUS server and AAA protocol. This not only helps in centralizing everything but helps you strengthen your security posture. If a policy needs to be updated, the time it takes to propagate the updated policies is greatly reduced. This could result in lowering operational costs in the long run.
Can two groups of remote users connect to the corporate network?
Now we are required to allow two sets or groups of remote users to connect to the corporate network. Each set must be assigned a different IP address. Most important, the remote users of one group should not be allowed to connect using the profile of the other group, because each group has a unique set of policies for accessing the corporate network.
Can you add a static route dynamically?
You can also instruct the device to add a static route dynamically for the connecting remote clients. In this example we have achieved it with the command ‘reverse-route’.
Is Cisco router a VPN?
Since this is client server architecture in which we have a Cisco router as an Easy VPN Server, performing the responsibility of a server, the client end responsibility is fulfilled by:
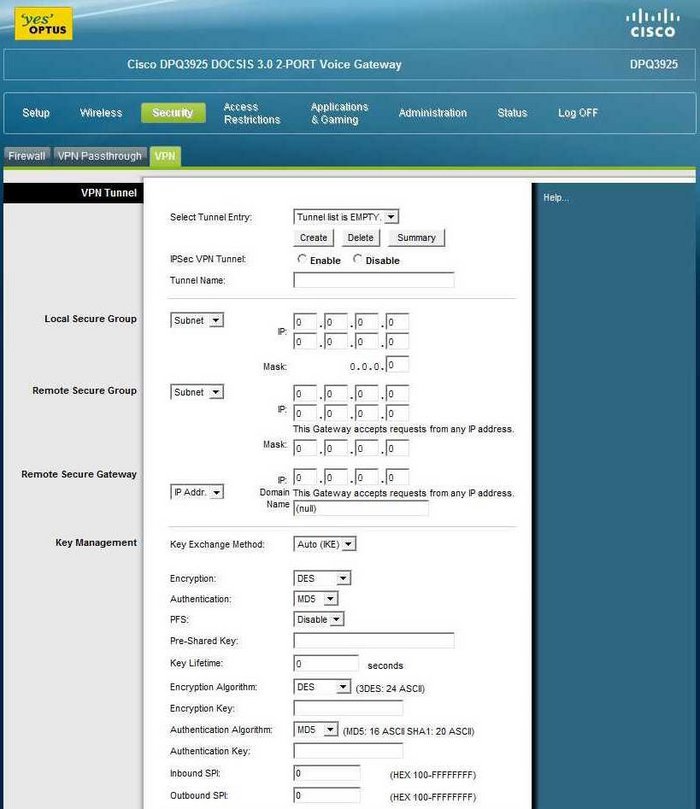
What is VPN on Cisco router?
This chapter explains the basic tasks for configuring an IP-based, remote access Virtual Private Network (VPN) on a Cisco 7200 series router. In the remote access VPN business scenario, a remote user running VPN client software on a PC establishes a connection to the headquarters Cisco 7200 series router.
How to verify that authentication proxy is successfully configured on the router?
To verify that the authentication proxy is successfully configured on the router, ask a user to initiate an HTTP connection through the router. The user must have authentication and authorization configured at the AAA server. If the user authentication is successful, the firewall completes the HTTP connection for the user. If the authentication is unsuccessful, check the access list and the AAA server configurations.
What command to use to verify PPTP?
After you complete a connection, enter the show vpdn tunnel command or the show vpdn session command to verify your PPTP and MPPE configuration.The following example contains typical output:
What is Cisco IOS firewall proxy?
Using the Cisco IOS firewall authentication proxy feature , network administrators can apply specific security policies on a per-user basis. Users can be identified and authorized on the basis of their per-user policy, and access privileges tailored on an individual basis are possible, in contrast with general policy applied across multiple users.
What is the radiusserverkey command?
Sets the authentication and encryption key for communications between the router and the AAA server. For RADIUS servers use the radiusserverkey command.
What is authentication proxy?
With the authentication proxy feature, users can log into the network or access the Internet via HTTP, and their specific access profiles are automatically retrieved and applied from an authentication server. The user profiles are active only when there is active traffic from the authenticated users.
How to display user authentication entries?
Display the user authentication entries using the show ip auth-proxy cache command in privileged EXEC mode. The authentication proxy cache lists the host IP address, the source port number, the timeout value for the authentication proxy, and the state of the connection. If the authentication proxy state is HTTP_ESTAB, the user authentication was successful.
