
To configure the infrastructure servers
- In the middle pane of the Remote Access Management console, in the Step 3 Infrastructure Servers area, click Configure.
- In the Infrastructure Server Setup Wizard, on the Network Location Server page, click the option that corresponds to the...
- If the network location server is on a remote web server, enter the URL, and then click Validate before you continue.
- If the network location server is on the Remote Access server, click Browse to locate the relevant certificate, and then...
- Click Finish.
Full Answer
What is the best remote access for PC?
What is the Best Remote Desktop Software?
- GoToMyPC. GoToMyPC is the best remote desktop software on this list. ...
- AnyDesk. AnyDesk is one of the most popular remote desktop software platforms, used by over 100 million users globally.
- LogMeIn. ...
- Parallels. ...
- Splashtop Business Access. ...
- Zoho Assist. ...
- ConnectWise Control. ...
- RemotePC. ...
- TeamViewer. ...
- Remote Utilities for Windows. ...
How do I find my Remote Desktop Connection?
You'll need this later.
- Make sure you have Windows 10 Pro. To check, go to Start > Settings > System > About and look for Edition . ...
- When you're ready, select Start > Settings > System > Remote Desktop, and turn on Enable Remote Desktop.
- Make note of the name of this PC under How to connect to this PC. You'll need this later.
How to set up windows for remote file access?
- Select Start.
- In your programs list, Expand Windows Accessories, then select Remote Desktop Connection. ...
- Enter your home computer's IP address, then select Connect.
- Enter your Home computer's username and password, then select OK.
- Your computer is not certified by a third party verification service. ...
Is rdweb secure?
Using Remote Web Access is fine but is less secure than a good VPN, especially if you don't take extra precautions to secure it, i.e. using an alternate server only for RWA, placing it in a DMZ, getting a valid 3rd party SSL cert, etc. Thanks for your feedback! This person is a verified professional.
How Do I Set Up Secure Remote Access?
Determine a security policy for your organization that includes which level of access certain groups/levels of employees will have and which level of account verification you want to enable or enforce. Here are the security features you can enable in Splashtop:
Why is remote access important?
Since remote access enables accessing a company device from anywhere in the world over the public Internet, security is an important consideration. Plus, if you’re using to remote access to provide support to your customers’ computers and devices, then you can potentially put your customers’ data at risk too whenever a security issue arises.
What is splashtop remote support?
Splashtop Remote Support: for MSPs and IT teams who want unattended remote access to their users’ computers to provide remote support. LEARN MORE | FREE TRIAL
Can you lock your remote computer's keyboard and mouse?
Lock the remote computer’s keyboard and mouse while in session. Lock the streamer settings using Splashtop admin credentials. In your Splashtop Account Settings, you can enable Two-step verification. In your Splashtop Account Team Settings, you can enable or disable the following features: In-session file transfer.
Is Splashtop Secure?
Yes, Splashtop’s remote access and remote support solutions are highly secure. All connections are protected with TLS and 256-bit AES encryption. Splashtop also comes with top security features including device authentication and two-factor authentication. Plus, Splashtop’s cutting-edge infrastructure provides a secure computing environment with advanced intrusion prevention and firewalls at multiple layers.
Can you share PrivX credentials?
So even when using shared accounts, the user cannot share any credentials to anyone else.
Can you restrict access to specific networks?
You can also restrict access to only to specific networks/target hosts when connecting from the PrivX GUI to websites. Login as self to web target is possible if the user provides own credentials for the web service. Again, optional session recording is possible. If needed, additional PrivX Extender component can be used to access Web targets (as well as SSH and RDP targets) in a private network or virtual private clouds (VPC).
What certificate is needed for remote access?
Remote Access requires an IP-HTTPS certificate to authenticate IP-HTTPS connections to the Remote Access server. There are three certificate options for the IP-HTTPS certificate:
When is a website created for remote access?
If the network location server website is located on the Remote Access server, a website will be created automatically when you configure Remote Access and it is bound to the server certificate that you provide.
How to join a remote server to a domain?
To join the Remote Access server to a domain. In Server Manager, click Local Server. In the details pane, click the link next to Computer name. In the System Properties dialog box, click the Computer Name tab, and then click Change.
How many Group Policy Objects are required for remote access?
To deploy Remote Access, you require a minimum of two Group Policy Objects. One Group Policy Object contains settings for the Remote Access server, and one contains settings for DirectAccess client computers. When you configure Remote Access, the wizard automatically creates the required Group Policy Objects.
What domain is Remote Access Server?
The Remote Access server and all DirectAccess client computers must be joined to an Active Directory domain . DirectAccess client computers must be a member of one of the following domain types:
How to add a new host in DNS?
In the left pane of the DNS Manager console, expand the forward lookup zone for your domain. Right-click the domain, and click New Host (A or AAAA).
When you use an internal CA to issue certificates, must you configure certificate templates for the IP-HTTPS certificate and?
When you use an internal CA to issue certificates, you must configure certificate templates for the IP-HTTPS certificate and the network location server website certificate.
How to open local security policy?
Go to the Start menu or open a Run prompt (Windows Key + R) and type “secpol.msc” to open the Local Security Policy menu.
How to change rules on firewall?
When Windows Firewall opens, click “Advanced Settings” on the left side of the window . Then right-click on “Inbound Rules” and choose “New Rule.”
How to see who is logging into my PC?
If you’re wondering how you can keep track of who is logging into your PC (and from where), you can open up Event Viewer to see.
Is network level authentication necessary?
It’s not a necessity to require Network Level Authentication, but doing so makes your computer more secure by protecting you from Man in the Middle attacks . Systems even as old as Windows XP can connect to hosts with Network Level Authentication, so there’s no reason not to use it.
Is remote desktop secure?
How to Enable and Secure Remote Desktop on Windows. While there are many alternatives, Microsoft’s Remote Desktop is a perfectly viable option for accessing other computers, but it has to be properly secured. After recommended security measures are in place, Remote Desktop is a powerful tool for geeks to use and lets you avoid installing third ...
Why don't companies allow remote work?
For various reasons, some employers discourage or don’t allow remote work. Manufacturers may feel it’s unfair to let operational staff work remotely when plant and warehouse workers have to come in. The office environment is naturally conducive to building friendships, fostering teamwork and encouraging collaboration.
What is VPN in remote office?
VPN – Virtual Private Network – You can restrict access so that employees must exclusively connect through a VPN, providing a direct, encrypted connection between their remote device and the main office server. This is a way to offer full, but secure access to remote employees. Be prescriptive about which VPN tools employees use.
Why is remote work important?
Remote work gives you a lot more flexibility to balance work and home life. You no longer have to commute, saving time and money. Remote work can also eliminate regular office distractions, making you more productive.
What to do if your company works with sensitive information?
If your company works with sensitive information, you want to be especially careful in setting up remote access. You’ll want to limit access, printing or downloading for records like:
Can you work remotely and in office?
One of the easiest ways is to allow employees to work from home. Obviously, working remotely and in-office are not the same. You don’t have the same fluid interactions between employees as when they’re within walking distance from each other. Paperwork and contracts can’t be passed around.
Is working remotely challenging?
Working remotely can be challenging for everyone at first. Don’t get discouraged.
Can you wipe a remote device in Office 365?
Microsoft Office 365 and other IT vendors have software available that enables employers to wipe remote devices in the case equipment is lost or stolen.
How to change scope of remote desktop?
In the Firewall options, select the Exceptions tab and highlight Remote Desktop. Click the edit button followed by the Change Scope button.
What is remote desktop?
Remote Desktop is a Windows service that allows users to connect to a host computer from a different location. This allows users to access information stored on a separate computer from any place that allows them to log on to the Remote Desktop application. This has many practical applications in business, but also opens up some obvious security ...
How to limit users on a host computer?
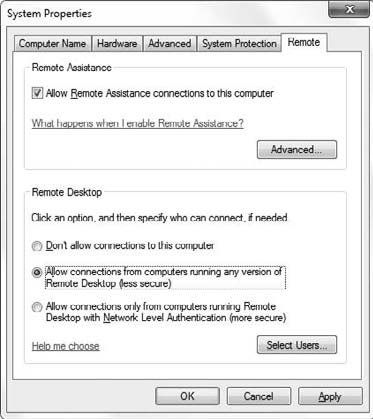
Limit users who can log on to the host computer. Go to the host computer's system properties and select the Remote tab. If Remote Desktop is set up, the box that reads "Allow Users to Connect Remotely" should be checked. If not, check it now. Click the Select Remote Users button, and add which groups of users that can have access to the computer. ...
How to unlock a user who has been locked out?
In order to manually unlock a user who has been locked out, go to Administrative Tools in the Start Menu and select Computer Management. In the Local Users and Groups setting, you can click on an individual user and restore their access by un-checking the Account is Disable box.
Can you allow admin access to host computer?
In most versions of Windows, this will still allow users in the administrator group to access the host computer. If you want to change that, go to the Run box in your Windows Start Menu and enter
Can you use only certain IP addresses for remote desktop?
Allow only certain IP addresses to access the Remote Desktop. IP addresses are a unique series of numbers that identifies a computer, and through Windows it is possible to limit the Remote Desktop Connection to only known and trusted IP addresses. To do so, navigate to your Windows Firewall settings through the Windows Control Panel.
What to do if you don't have Azure?
If you don't have an Azure subscription, create an account. An Azure Active Directory tenant associated with your subscription, either synchronized with an on-premises directory or a cloud-only directory. If needed, create an Azure Active Directory tenant or associate an Azure subscription with your account.
Can RD be deployed into managed domain?
With RD deployed into the managed domain, you can manage and use the service as you would with an on-premises AD DS domain.
Can a VM be deployed into a subnet?
Make sure that VMs are deployed into a workloads subnet of your Azure AD DS virtual network, then join the VMs to managed domain. For more information, see how to create and join a Windows Server VM to a managed domain.
What is the first thing that’s required to ensure smooth remote access via a VPN?
The first thing that’s required to ensure smooth remote access via a VPN is to plan out a comprehensive network security policy.
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
Why is IPSEC used?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
What are the implications of IPSec connections for corporations?
What are the implications of IPSec connections for corporations, considering the very nature of this connection? Well, your employee will only be able to access the network from a single, authorized device. Security is further boosted by the enforcement of antivirus and firewall policies.
What is IPSEC encryption?
IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect data flows between hosts and security gateways.
Why use two factor authentication for VPN?
Adopting two-factor authentication for remote access through VPN further boosts your network security. Now let’s take a look at why you should choose a particular VPN type as a secure connection methodology instead of the alternatives.
What is the line of defense for remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly.
