Add a remote access policy using the SSL VPN remote access assistant
- Go to Remote access VPN > SSL VPN and click Assistant.
- Review the global settings and click Next. Note You can't change the SSL VPN global settings within the SSL VPN...
- Specify the settings: Name Description VPN name Enter a name to identify the connection. This is the name of your SSL...
Full Answer
What is a VPN remote access policy and how does it work?
By having an effective VPN remote access policy, you can reduce the risk of your organization’s network assets and support calls from end users. A VPN policy should be documented, and every user remotely connecting to the network should read and accept the terms of that policy.
How do I create a VPN policy in access control?
Create a rule in the Access Control Rule Base that handles with remote access connections. Go to Security Policies and right-click the cell in the VPN column. Select Specific VPN Communities.
How do I grant remote access to a VPN Server?
Select the Grant access. Grant access if the connection request matches this policy option. c. Under Type of network access server, select Remote Access Server (VPN-Dial up) from the drop-down. In the Routing and Remote Access MMC, right-click Ports, and then select Properties.
How do I configure the remote access VPN connection profile?
Configure the remote access VPN connection profile. Click Device, then click Setup Connection Profile in the Remote Access VPN group. (Click View Configuration if you already configured a profile). For existing connections, click Edit to modify the profile. Configure the connection profile settings:

How do I setup a VPN remote access?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
Why must you create a remote access policy for VPN?
By having an effective VPN remote access policy, you can reduce the risk of your organization's network assets and support calls from end users. A VPN policy should be documented, and every user remotely connecting to the network should read and accept the terms of that policy.
Does VPN allow remote access?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
How does remote access work with VPN?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What is the difference between remote access and a VPN?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
Which VPN is best for remote access?
Best Remote Access VPNs for business.Perimeter 81 – Best all-round business VPN.GoodAccess – Security Strategy Options.ExpressVPN – Lightning Fast VPN.Windscribe – VPN with Enterprise-Friendly Features.VyprVPN – Secure VPN with Business Packages.NordVPN – Security-first VPN.More items...•
Which is better VPN or RDP?
Security. Although both VPN and RDP are encrypted through internet connection, a VPN connection is less accessible to threats than a remote desktop connection. For this reason, VPN is often considered more secure than RDP.
Why is remote access important?
Remote access enables remote users to access files and other system resources on any devices or servers that are connected to the network at any time. This increases employee productivity and enables employees to better collaborate with colleagues around the world.
What is a VPN policy?
A VPN security policy is a policy that defines. just about everything that anyone would need to know about your VPN. It defines. things like who can use the VPN, what they can use it for, and what it is that. keeps them from using improperly or maliciously.
What is a remote access control policy?
Remote access policy is a document which outlines and defines acceptable methods of remotely connecting to the internal network. It is essential in large organization where networks are geographically dispersed and extend into insecure network locations such as public networks or unmanaged home networks.
How a remote access policy may be used and its purpose?
The purpose of a remote access policy is to outline the expectations of those users' behaviors while connecting to your network in an attempt to safeguard that network from viruses, threats or other security incidents.
What is the importance of remote access VPN?
Before the implementation of a remote-access VPN solution, it is imperative for organizations to define who can use the VPN, what it can be used for, and the security policies that prevent improper or malicious use.
What is IPsec remote access?
IPsec remote access offers customizability and versatility through modification of VPN client software. With APIs in IPsec software, organizations are able to control the function and appearance of the VPN client for applications and special case uses.
Why is remote access important?
Remote access VPN can be an attractive ground for hackers and malicious attackers, so an organization’s server must be protected by a security or network administrator. By having an effective VPN remote access policy, you can reduce the risk of your organization’s network assets and support calls from end users.
How to keep remote devices up to date?
The operating system of all remote devices must be kept up-to-date by applying patches as soon as they become available to download.
How to reduce exposure to corporate network security threats?
Organizations must consider the following: 1. Avoid split tunneling.
Is encryption good for remote access?
Encryption is a major part of remote access security. Less secured protocols such as IPSEC6 and PPTP connections should be avoided if possible. Organizations should aim for the most secure encryption standards such as IPSEC (3DES) and 256-bit AES. SSL-backed VPN should be considered if it is compatible with company applications: in this case, a connection only allows access to individual ports, IP addresses and applications, which makes it more secure than standard connections that grant access to the whole network.
Is VPN security necessary for remote access?
Technologies required for preventing remote access abuse and mitigating threats such as spyware, viruses, and malware already exist in the security infrastructure of many enterprise networks. However, they are not integrated in a way that they can ensure remote access security, due to the way VPN traffic is encrypted. While additional security equipment may be installed and purchased to protect the VPN network, the most cost-effective solution would be to consider VPN gateways that offer application firewall and threat mitigation services as a built-in part of the VPN product.
What is VPN policy?
Policies for VPN remote access can be standardized. These policies “shore up” and prevent the use of rogue devices and access by non-authorized users , including the worker's family members or housemates. The policy also enforces proper email protocols to protect information from being sent through unsecured or untrusted sources, and also provides rules that limit or prohibit split tunnel configurations that allow mobile users to access both secure and unsecure networks simultaneously.
Why Is a Remote Access Policy Necessary?
The numerous types of mobile devices and the different ways to connect pose challenges for the IT department. Devices can include cell phones, tablets, laptops, and any other device a remote worker relies on to conduct business. They can be company owned and secured, personally owned and authorized by a Bring Your Own Device (BYOD) policy, or a combination. Each class of device has its own set of security challenges. According to the National Institute for Standards and Technology’s Guidelines for Managing the Security of Mobile Devices in the Enterprise, “…Security controls available for laptops today are quite different than those available for smartphones, tablets, and other mobile device types.” Since different devices demand different controls, the policy has to detail what is allowed, compliant, and secure. The policy should answer the following questions:
What Is Remote Access?
Remote access is any connection made to an organization's internal network and systems from an external source by a device or host. Remote locations can be almost anywhere in the world, from the employee’s home to an off-site office, hotels, transportation hubs, and cafes.
What Problems Arise Without a Remote Access Policy?
Therefore, consequences for misuse can also be clearly outlined to compel compliance and appropriate precautions for data use and access. Elements such as firewalls, connectivity guidelines, personal use restrictions, and antivirus updates can help IT prevent both malicious and accidental loss and disruption of corporate information assets. The remote access control policies also provide protections for confidentiality, intellectual property, and information compliance.
What percentage of people work remotely?
According to research conducted by Gallup, 43 percent of workers in the U.S. worked remotely at least some of the time in 2016. Remote workers report higher job satisfaction and flexibility, experience fewer distractions and interruptions, and are more productive. Companies experience less absenteeism, less stress on office accommodations, and realize greater employee retention. A recent New York Times article found that finance, insurance, real estate, and transportation were most likely to have and support remote work (retail and education were least likely candidates). The trend is only increasing: the 2016 Gallup poll also found that those who work remotely log more hours away from the office than was reported in their 2012 findings. Not only are people logging more hours, but remote workers are saving money when it comes to commuting costs and businesses are saving on office space expenses.
Why is remote access important?
Software organizations where development engineers need to connect across multiple locations, small organizations lacking office-space, and large, enterprise organizations all want to offer the most flexible work options in order to attract high-ranking candidates and reap the rewards of having such a policy.
What is unauthorized access policy?
Even if the employee provides their own equipment, laptop, or mobile device, the policy dictates and enforces the minimum-security requirements necessary. The policy can also provide determinations on who is allowed remote access, the level of access, and penalties for misuse.
How to install Remote Access Role in VPN?
On the VPN server, in Server Manager, select Manage and select Add Roles and Features. The Add Roles and Features Wizard opens. On the Before you begin page, select Next.
How to start remote access?
Select Start service to start Remote Access. In the Remote Access MMC, right-click the VPN server, then select Properties. In Properties, select the Security tab and do: a. Select Authentication provider and select RADIUS Authentication.
How to select a server from the server pool?
On the Select destination server page, select the Select a server from the server pool option. Under Server Pool, select the local computer and select Next. On the Select server roles page, in Roles, select Remote Access, then Next. On the Select features page, select Next. On the Remote Access page, select Next.
How many Ethernet adapters are needed for VPN?
Install two Ethernet network adapters in the physical server. If you are installing the VPN server on a VM, you must create two External virtual switches, one for each physical network adapter; and then create two virtual network adapters for the VM, with each network adapter connected to one virtual switch.
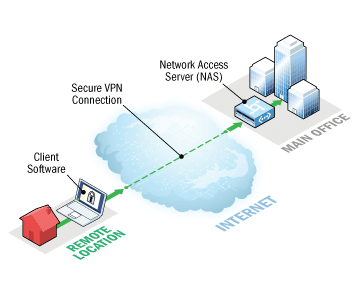
What is NAS in a network?
A NAS is a device that provides some level of access to a larger network. A NAS using a RADIUS infrastructure is also a RADIUS client, sending connection requests and accounting messages to a RADIUS server for authentication, authorization, and accounting. Review the setting for Accounting provider: Table 1.
Can you assign a VPN to a pool?
Additionally, configure the server to assign addresses to VPN clients from a static address pool. You can feasibly assign addresses from either a pool or a DHCP server; however, using a DHCP server adds complexity to the design and delivers minimal benefits.
Is RRAS a router or a server?
RRAS is designed to perform well as both a router and a remote access server because it supports a wide array of features. For the purposes of this deployment, you require only a small subset of these features: support for IKEv2 VPN connections and LAN routing.
Configuring Remote Access Policy
Configure Remote Access VPN policy in the Unified Access Control Policy Rule Base.
Defining Access Control Rules
Access control is a layer of security not connected with VPN. When there is a Remote Access Community, it does not mean that members of that community have free, automatic access to the network. Security rules have to be created in the Access Control Policy Rule Base blocking or allowing specific services.
Access Roles for Remote Access
For Security Gateways R80.10 and higher, create Access Roles for Remote Access and VPN Clients to include them in rules in the Access Control Rule Base. This applies to Mobile Access and IPsec clients. When an Access Role for a client is in the Source column of a rule, the rule applies to traffic that originates from that client.
Policy Definition for Remote Access
There must be a rule in the Security Policy Rule Base that grants remote users access to the LAN. Consider which services are allowed. Restrict those services that need to be restricted with an explicit rule in the Security Policy Rule Base.
Modifying Encryption Properties for Remote Access VPN
The encryption properties of the users participating in a Remote Access community are set by default. If you must modify the encryption algorithm, the data integrity method and/or the Diffie-Hellman group, you can either do this globally for all users or configure the properties per user.
Installing the Policy
Install the policy and instruct the users to create or update the site topology.
IPsec and IKE for Remote Access
For Remote users, the IKE settings are configured in Global Properties > Remote Access > VPN Authentication and Encryption.
What is remote access policy?
Remote access policies are an ordered set of rules that define how connections are either authorized or rejected. For each rule, there are one or more conditions, a set of profile settings, and a remote access permission setting. If a connection is authorized, the remote access policy profile specifies a set of connection restrictions. The dial-in properties of the user account also provide a set of restrictions. Where applicable, user account connection restrictions override the remote access policy profile connection restrictions.
How to delete VPN policy?
You can delete the other policies if you require only VPN connections to your ISA firewall. Right-click on Connections to other access servers, and click Delete. Repeat with Connections to Microsoft Routing and Remote Access server.
How does BAP work with ISDN?
Enter Bandwidth Allocation Protocol (BAP). BAP adds features to PPP and Multilink to monitor the connection requirements and to adjust accordingly . If our ISDN link does not need the bandwidth provided through two B-channels, BAP will drop one of the two connections, based on our configuration settings. If the bandwidth requirements increase and the single B-channel in use cannot provide sufficient bandwidth, BAP will connect the second B-channel to double our bandwidth capabilities. This same configuration could include two analog phone lines at each end of the connection as opposed to the 2B+D ISDN configuration for Multilink. In order to take advantage of the capabilities of BAP, the remote access client and server must support BAP and have it enabled.
How to enable EAP authentication?
Follow these steps to enable EAP authentication:#N#1.#N#Select Start | Administrative Tools | Internet Authentication Service.#N#2.#N#The IAS management console is displayed. Click to highlight Remote Access Policies in the left column.#N#3.#N#In the right column, select Connections to Microsoft Routing and Remote Access Server .#N#4.#N#Select Action | Properties from the menu, or right-click and select Properties from the context menu. #N#5.#N#The Properties dialog box is displayed. Click the Edit Profile button .#N#6.#N#The Edit Dial-in Profile dialog box is displayed. Select the Authentication tab.#N#7.#N#The authentication methods supported by IAS are displayed, as shown in Figure 5.14. You can enable or disable the non-EAP authentication methods here. You can also change the order in which the selected EAP types are negotiated by moving them up or down in the list, using the Move Up and Move Down buttons.#N#Sign in to download full-size image#N#Figure 5.14. Authentication Methods#N#8.#N#Click the EAP Methods button. A list of the currently enabled EAP types is displayed.#N#9.#N#Click Add and select MD5-Challenge from the list.#N#10.#N#Click OK, then click OK in the EAP types list.#N#11.#N#Click OK to exit the Edit Profile dialog box.#N#12.#N#Click OK to exit the Properties dialog box.
How to enable EAP on IAS?
To enable EAP authentication on an IAS server, you create a Remote Access Policy that allows EAP authentication, or you modify an existing policy. Exercise 5.07 demonstrates how to modify a policy to allow the use of MD5 CHAP authentication through EAP.
What is VPN quarantine in Windows 2003?
A new feature that comes with a new set of utilities for Windows Server 2003 is Network Access Quarantine Control. Using either the Connection Manager Administration Kit (CMAK) or the Windows Deployment and Resource Kits, administrators can configure special policies that restrict VPN client access using a quarantine mode until the client system is either brought into compliance with corporate VPN client specifications or determined to already be in accordance with specifications. This is a new feature for Windows Server 2003 that will help to increase network security.
What is PPP protocol?
The official implementation, as used by Microsoft, comes from RFP 1990. Capabilities were added and subsequent modifications to the standard were made leading up to PPP as it exists today. In 1994, a documented standard was proposed for “The PPP Multilink Protocol” in RFC 1717. At the time, other proposals existed to combine streams of data at the bit level (basically a hardware solution). This proposal described a software-based solution for the need to combine multiple streams of data into one. This solution was well-suited to the twin bearer channels of ISDN (2B+D).
How should VPN usage be monitored?
Monitoring. Remote access and VPN usage should be logged and monitored in a central database and reviewed regularly to detect anomalies and make changes to remote access privileges.
What is remote access in a company name?
Remote access is defined as any connection to [COMPANY NAME]’s internal network from a location outside of any affiliated company offices.
How long do remote users have to log in?
Remote access must be logged in a central database and kept for a period of at least 30 days. Access logs must be reviewed regularly.
Why is remote access important?
Today, every organization should have a robust remote access policy that provides employees with clear direction on how to connect securely when at home or on the road. As remote work opportunities increase and travel remains a big part of corporate life, it’s more important than ever for organizations to ensure their employees have a secure means of accessing critical corporate data from any location.
What is the purpose of the Company Name policy?
The intent of this policy is to establish guidelines specifically pertaining to remote access to [COMPANY NAME]’s internal network. Preventing unauthorized access to company data from insecure networks is of utmost importance to [COMPANY NAME]. This policy is designed to ensure remote and/or traveling employees have the ability to securely connect to the corporate network without fear of threat and to provide the Company with an additional means of monitoring and controlling access to the internal network.
What to do if your connection is compromised?
If you believe your connection may have been compromised, please immediately report the incident to [RELEVANT CONTACT].
Is multifactor authentication required for VPN?
And to make it even stronger, we recommend multi-factor authentication as a requirement for VPN access. Restricted use. Remote access privileges shouldn’t be given out in the office like candy, but rather on an as-needed basis.
What is remote access VPN?
In remote access VPN, you might want users on the remote networks to access the Internet through your device. However, because the remote users are entering your device on the same interface that faces the Internet (the outside interface), you need to bounce Internet traffic right back out of the outside interface. This technique is sometimes called hair pinning.
Where does remote access VPN problem originate?
Remote access VPN connection issues can originate in the client or in the Firepower Threat Defense device configuration. The following topics cover the main troubleshooting problems you might encounter.
How to view VPN configuration?
Click Device, then click View Configuration in the Site-to-Site VPN group.
How to use a VPN on a computer?
Step 1. Using a web browser, open https://ravpn-address , where ravpn-address is the IP address or hostname of the outside interface on which you are allowing VPN connections. You identify this interface when you configure the remote access VPN. The system prompts the user to log in. Step 2.
How to complete a VPN connection?
To complete a VPN connection, your users must install the AnyConnect client software. You can use your existing software distribution methods to install the software directly. Or, you can have users install the AnyConnect client directly from the Firepower Threat Defense device.
What is AnyConnect client profile?
AnyConnect client profiles are downloaded to clients along with the AnyConnect client software. These profiles define many client-related options, such as auto connect on startup and auto reconnect, and whether the end user is allowed to change the option from the AnyConnect client preferences and advanced settings.
How long is a VPN idle?
Idle Timeout —The length of time, in minutes, that the VPN connection can be idle before it is automatically closed, from 1-35791394. The default is 30 minutes. Browser Proxy During VPN Sessions —Whether proxies are used during a VPN session for Internet Explorer web browsers on Windows client devices.
What is SSTP in VPN?
SSTP is a Microsoft proprietary SSL-based solution that can penetrate firewalls since most firewalls open the outbound TCP port that 443 SSL uses. OpenVPN. OpenVPN is a SSL-based solution that can penetrate firewalls since most firewalls open the outbound TCP port that 443 SSL uses. IKEv2 VPN.
Is TLS 1.1 supported by Azure VPN?
Starting July 1, 2018, support is being removed for TLS 1.0 and 1.1 from Azure VPN Gateway. VPN Gateway will support only TLS 1.2. To maintain support, see the updates to enable support for TLS1.2.
Does Radius support OpenVPN?
RADIUS authentication is supported for the OpenVPN protocol only through PowerShell.
Does Azure support P2S VPN?
Azure supports Windows, Mac, and Linux for P2S VPN.
Does VPN reestablish automatically?
By default, the client computer will not reestablish the VPN connection automatically.
Do you need a VPN for a resource manager?
Yes. For the Resource Manager deployment model , you must have a RouteBased VPN type for your gateway. For the classic deployment model, you need a dynamic gateway. We do not support Point-to-Site for static routing VPN gateways or PolicyBased VPN gateways.
Can a point to site client connect to a VNet?
Yes, Point-to-Site client connections to a virtual network gateway that is deployed in a VNet which is peered with other VNets may have access to other peered VNets. Point-to-Site clients will be able to connect to peered VNets as long as the peered VNets are using the UseRemoteGateway / AllowGatewayTransit features.
