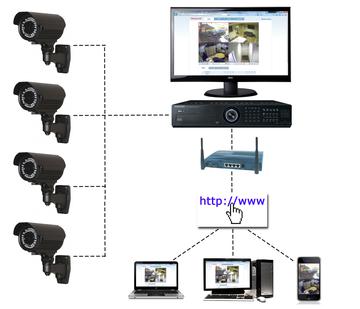
How do you build remote access software?
- 1. Strategize on offerings, pricing, etc. for the proposed remote work software You need to decide which user segments to serve. ...
- 2. Decide on the features to offer in a remote desktop access software ...
- 3. Plan the MVP (Minimum Viable Product) for your proposed remote desktop software ...
- 4. Planning to develop the key functionality of a remote work software application ...
Full Answer
What are the best remote access solutions for a secure work environment?
Top 3 Remote Access Solutions For A Secure Work Environment 1 Business or Enterprise-Level VPNs. Most organizations use a business VPN to allow employees or users to connect to the company’s network no matter where they are located. 2 Remote Desktop Software. ... 3 Cloudbric Remote Access Solution. ... 4 Conclusion. ...
How do I set up remote access?
Identify the network adapter topology that you want to use. Remote Access can be set up with any of the following topologies: With two network adapters: The Remote Access server is installed at the edge with one network adapter connected to the Internet and the other to the internal network.
How does remote access work with DirectAccess?
With one network adapter: The Remote Access server is installed behind a NAT device, and the single network adapter is connected to the internal network. DirectAccess uses IPv6 with IPsec to create a secure connection between DirectAccess client computers and the internal corporate network.
Why do you need remote desktop solutions?
Or a technician may need to access your device remotely to help you troubleshoot an issue. This is where remote desktop solutions can help. In these situations and more, remote PC access tools allow a person to gain access to a computer’s contents without needing to be physically present in front of it.

What is remote access plan?
It includes features that can let you manage your vehicle from your compatible smartphone and check certain aspects of your vehicle's health. With the Remote Access Plan, you can take charge of what's going on with your vehicle, even when you can't be there in person.
What are the three main types of remote connections?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
What should be included in a remote access policy?
What Should You Address in a Remote Access Policy?Standardized hardware and software, including firewalls and antivirus/antimalware programs.Data and network encryption standards.Information security and confidentiality.Email usage.Physical and virtual device security.Network connectivity, e.g., VPN access.More items...•
Which technology is used in remote access?
virtual private network (VPN) technologyRemote access software is usually accomplished using a virtual private network (VPN) technology. This type of method is more available compared to others since it is a more secure remote access software that connects the user and the enterprise's networks through an internet connection.
What are the two types of remote access server?
Remote Access Methods1- Remote Access Server: It's one server in organization network that it is the destination of all remote access connections.2- Remote Access Client: All computers that remote connect to network, called remote access client or remote computer.More items...•
What is remote GUI?
Remote GUI allows you to access your router's online settings, also known as the graphical user interface (GUI), through a WAN connection. To access your modem remotely, you will enter https:// followed by the modem IP in the URL field of a browser. 1.
How do I create a network security policy?
How To Develop & Implement A Network Security PlanArticle Navigation.Step 1: Understand Your Business Model.Step 2: Perform A Threat Assessment.Step 3: Develop IT Security Policies & Procedures.Step 4: Create A “Security-First” Company Culture.Step 5: Define Incident Response.Step 6: Implement Security Controls.More items...•
What security best practices are for connecting to remote systems?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
Why is remote access important?
With remote access, employees can safely work from any device, platform, or network at their home office or abroad. Remote desktop functions allow them to remotely access important files and share their screen for meetings and troubleshooting.
How many types of remote access are there?
Types of remote access: virtual private network. SaaS remote desktop tools. common remote service ports.
Which tool is used to connect a remote computer?
Comparison of Top Remote Desktop Access ToolsTool NameOS & DevicesOur RatingTeam ViewerWindows, Linux, iOS, & Android4.2/5VNC ConnectWindows, Mac, Linux, Raspberry Pi, iOS, Android4.2/5LogMeInWindows & Mac4.3/5GoToMyPCWindows & Mac4.2/58 more rows•Aug 7, 2022
What are the pros and cons of remote desktop access?
Advantages of Remote Access1) Flexible Access. ... 2) Flexible Set-Up and Costs. ... 3) Full Control on Authorization and Access. ... 4) Centralized Storage and Backups. ... 5) Shared Resources; Greater Efficiency and Collaboration. ... 1) Security Issues. ... 2) Version Problems and Data Liabilities. ... 3) Hardware Issues Still Need On-Site Work.More items...•
What types of connections are there?
There are two possible types of connections: point-to-point and multipoint. A point-to-point connection provides a dedicated link between two devices.
How many types of remote access are there?
Types of remote access: virtual private network. SaaS remote desktop tools. common remote service ports.
What are the types of connections in network?
Generally there are two types of network connections: Peer-to-Peer and Network Shared environment.
What are the 4 types of networks?
A computer network is mainly of four types:LAN(Local Area Network)PAN(Personal Area Network)MAN(Metropolitan Area Network)WAN(Wide Area Network)
What is remote access server?
The Remote Access server acts as an IP-HTTPS listener and uses its server certificate to authenticate to IP-HTTPS clients. The IP-HTTPS name must be resolvable by DirectAccess clients that use public DNS servers.
What is direct access client?
DirectAccess clients attempt to reach the network location server to determine if they are on the internal network. Clients on the internal network must be able to resolve the name of the network location server, and they must be prevented from resolving the name when they are located on the Internet. To ensure that this occurs, by default, the FQDN of the network location server is added as an exemption rule to the NRPT. In addition, when you configure Remote Access, the following rules are created automatically:
What is DNS in DirectAccess?
DNS is used to resolve requests from DirectAccess client computers that are not located on the internal network. DirectAccess clients attempt to connect to the DirectAccess network location server to determine whether they are located on the Internet or on the corporate network.
How to use ISATAP?
To use ISATAP do the following: 1. Register the ISATAP name on a DNS server for each domain on which you want to enable ISATAP-based connectivity, so that the ISATAP name is resolvable by the internal DNS server to the internal IPv4 address of the Remote Access server. 2.
Why is ISATAP required?
ISATAP is required for remote management of DirectAccessclients, so that DirectAccess management servers can connect to DirectAccess clients located on the Internet . ISATAP is not required to support connections that are initiated by DirectAccess client computers to IPv4 resources on the corporate network.
Why do you need to add packet filters on a domain controller?
You need to add packet filters on the domain controller to prevent connectivity to the IP address of the Internet adapter.
Do you have to have a public IP address for DirectAccess?
Ensure that you do not have public IP addresses on the internal interface of the DirectAccess server. If you have public IP address on the internal interface, connectivity through ISATAP may fail.
What is remote access?
Depending on your needs, a remote access solution can allow employees or members of your organizations to securely access resources located in your private network or remotely connect to another physical computer.
What is remote desktop software?
The most popular remote desktop software out there is RDP (Remote Desktop Protocol), Microsoft’s free proprietary protocol that allows one user (i.e host machine) to fully control a remote computer through a network connection.
What happens if you hack a remote desktop?
Unfortunately, there are higher security risks associated with remote desktop software; if the connection is hijacked, a hacker can steal or delete important data or files on the computer, install spyware, and so much more.
Do VPNs need server and client side installation?
Both VPNs and remote access software like RDP require server- and client-side installation for the solution to work. This opens the gates to potential connection errors and untracked access.
What is a design scenario?
The "Design Scenario" series is where I showcase different network or security designs. Generally I will list a few requirements, go over the designs and discuss the pros and cons. I will try to steer away from specific configurations as the goal is always to try and be vendor neutral but I will usually provide config guides for reference and support material. I hope this provides you with an alternate way to look at a network engineering or a defense challenge. Feel free to share your thoughts or your own designs as well!
How to use 2 factor authentication?
The token application can be from an app on the computer, a cell phone, or a method like e-mail or SMS messaging. The application method is generally accepted vs SMS or e-mail as the more secure choice, however just having the second method at a minimum is good. These solutions can generally be deployed on-prem or from the cloud via APIs or similar mechanisms.
What are the advantages of a stand alone VPN?
How healthy the budget is might determine that. One of the advantages of purchasing a stand alone specialty VPN appliances is that ' typically ' they might have more flexibility when it comes to user policy and security settings. Some appliances also might have more robust client applications.
Is remote access part of a business continuity plan?
In general remote access should be a part of a business continuity plan. That alone could be the reason you justify deployment, which would mean you'd need to ensure there is some language about remote access and how the design works to meet the BC plan needs.
What Is Remote Access?
Remote access is any connection made to an organization's internal network and systems from an external source by a device or host. Remote locations can be almost anywhere in the world, from the employee’s home to an off-site office, hotels, transportation hubs, and cafes.
Why is remote access important?
Software organizations where development engineers need to connect across multiple locations, small organizations lacking office-space, and large, enterprise organizations all want to offer the most flexible work options in order to attract high-ranking candidates and reap the rewards of having such a policy.
Why Is a Remote Access Policy Necessary?
The numerous types of mobile devices and the different ways to connect pose challenges for the IT department. Devices can include cell phones, tablets, laptops, and any other device a remote worker relies on to conduct business. They can be company owned and secured, personally owned and authorized by a Bring Your Own Device (BYOD) policy, or a combination. Each class of device has its own set of security challenges. According to the National Institute for Standards and Technology’s Guidelines for Managing the Security of Mobile Devices in the Enterprise, “…Security controls available for laptops today are quite different than those available for smartphones, tablets, and other mobile device types.” Since different devices demand different controls, the policy has to detail what is allowed, compliant, and secure. The policy should answer the following questions:
What Problems Arise Without a Remote Access Policy?
Therefore, consequences for misuse can also be clearly outlined to compel compliance and appropriate precautions for data use and access. Elements such as firewalls, connectivity guidelines, personal use restrictions, and antivirus updates can help IT prevent both malicious and accidental loss and disruption of corporate information assets. The remote access control policies also provide protections for confidentiality, intellectual property, and information compliance.
What is telecommuting?
“Telecommuting,” a term coined in the 1970s, has experienced explosive growth in today’s era of mobile connectivity. Now called distributed offices, remote work, telework, mobile work, smart work, and work shifting, many people are finding flexibility and increased productivity conducting business away from a centralized office environment. Researchers have long studied the benefits of remote work - from the successes that remote work had on traffic reduction during the 1984 Los Angeles Olympics to the 2016 findings by a Gallup survey on the increased hours for remote work.
What percentage of people work remotely?
According to research conducted by Gallup, 43 percent of workers in the U.S. worked remotely at least some of the time in 2016. Remote workers report higher job satisfaction and flexibility, experience fewer distractions and interruptions, and are more productive. Companies experience less absenteeism, less stress on office accommodations, and realize greater employee retention. A recent New York Times article found that finance, insurance, real estate, and transportation were most likely to have and support remote work (retail and education were least likely candidates). The trend is only increasing: the 2016 Gallup poll also found that those who work remotely log more hours away from the office than was reported in their 2012 findings. Not only are people logging more hours, but remote workers are saving money when it comes to commuting costs and businesses are saving on office space expenses.
What is unauthorized access policy?
Even if the employee provides their own equipment, laptop, or mobile device, the policy dictates and enforces the minimum-security requirements necessary. The policy can also provide determinations on who is allowed remote access, the level of access, and penalties for misuse.
What is an attended remote access solution?
Attended remote access solutions require an authorized individual to be physically present with the machine you are trying to remotely connect to, to grant access. It’s typically used to provide remote support, enabling customer support technicians to provide direct and immediate support.
What is remote access?
Remote access might also be leveraged to provide support to customers.
How to remote access a PC with Solarwinds?
To remote access a PC with SolarWinds DRS and DRE, you first need to invite a remote host to join an attended or unattended session. With Dameware tools, you can connect with and troubleshoot user machines both inside and outside your network. If the connection is outside the firewall, you will connect with the end user via an unattended or attended Internet Session. To achieve this, you need to configure the Dameware Internet Proxy.
Why use a built in ticketing system?
For companies using remote access to provide support, a built-in ticketing system can significantly improve your team’s efficiency. A built-in or integrated ticketing system will allow you to track user requests without leaving your remote desktop solution’s console. This centralizes your support operations and can provide other benefits, including linking correspondence logs with tickets to create a searchable history of prior support requests and client information.
What is remote desktop?
A remote desktop solution allows you to access your PC, its files, and its applications from another device, via internet connection. Remote desktop software achieves this by streaming a visual, real-time feed of the computer you’re trying to access. Some remote desktop tools allow you to establish these remote connections from your smartphone, tablet, or even across a data network.
Why use unattended remote access?
For companies using unattended remote access software to provide support, unattended remote access allows them to deliver intermittent support services and perform maintenance activities on devices. A help desk team is likely to use it to provide immediate support and leverage it to manage infrastructure. This usually involves installing updates and troubleshooting non-critical issues.
Why is remote access important?
Unattended remote access is ideal for individuals and companies hoping to increase productivity, flexibility, and efficiency by enabling them to access PCs remotely—even when the device is unattended. For instance, it might be used by a company employee to connect to their office desktop, so they have access to all necessary files and accounts even when working from home on another device.