WH-RAT – Remote Access Trojan Application
- Download and Install. This application is very easy to operate but first you have to download it through the given URL. ...
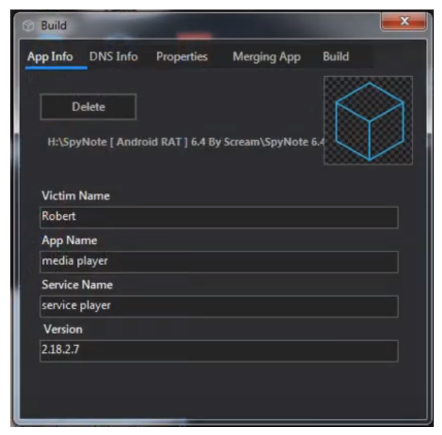
- Build RAT. Click “ Builder ” and choose the one for which you want to create the payload. ...
- File Manager. ...
- Execute Script. ...
- Remote Desktop. ...
- Remote Shell. ...
Full Answer
Is remote access Trojan illegal?
Law enforcement officials say that simply possessing a remote-access tool isn't illegal. In fact, remote-access tools are often used for IT support purposes in corporate environments.
How are remote access Trojans delivered?
A remote access Trojan (RAT) is a malware program that includes a back door for administrative control over the target computer. RATs are usually downloaded invisibly with a user-requested program -- such as a game -- or sent as an email attachment.
What are the variant of remote access Trojan?
There are a large number of Remote Access Trojans. Some are more well-known than others. SubSeven, Back Orifice, ProRat, Turkojan, and Poison-Ivy are established programs. Others, such as CyberGate, DarkComet, Optix, Shark, and VorteX Rat have a smaller distribution and utilization.
Which of the following is a remote Trojan?
Troya is a remote Trojan that works remotely for its creator.
How do I know if someone is accessing my computer remotely?
You can try any of these for confirmation.Way 1: Disconnect Your Computer From the Internet.Way 2. ... Way 3: Check Your Browser History on The Computer.Way 4: Check Recently Modified Files.Way 5: Check Your computer's Login Events.Way 6: Use the Task Manager to Detect Remote Access.Way 7: Check Your Firewall Settings.More items...•
Is TeamViewer a RAT?
The JS script then launches the malware, which installs a version of TeamViewer, a remote administration tool (RAT), modified by the attackers. As in earlier attacks, the attackers use a malicious DLL library to hide the graphical user interface in order to control the infected system without the user's knowledge.
Which is the best remote access Trojan?
Blackshades is a Trojan which is widely used by hackers to gain access to any system remotely. This tool frequently attacks the Windows-based operating system for access.
How would users recognize if ones computer is infected?
Signs of an infection include your computer acting strangely, glitching and running abnormally slow. Installing and routinely updating antivirus software can prevent virus and malware infections, as can following cautious best practices.
How can I remotely access another computer over the Internet?
You can set up remote access to your Mac, Windows, or Linux computer.On your computer, open Chrome.In the address bar, enter remotedesktop.google.com/access .Under “Set up Remote Access,” click Download .Follow the onscreen directions to download and install Chrome Remote Desktop.
What is a backdoor Trojan?
Backdoor malware is generally classified as a Trojan. A Trojan is a malicious computer program pretending to be something it's not for the purposes of delivering malware, stealing data, or opening up a backdoor on your system.
What do Trojan creators look for?
Explanation: Trojan creators do not look for securing victim's system with their programs, rather they create such trojans for stealing credit card and financial details as well as important documents and files.
What is a logic bomb virus?
A logic bomb is a malicious program that is triggered when a logical condition is met, such as after a number of transactions have been processed, or on a specific date (also called a time bomb). Malware such as worms often contain logic bombs, behaving in one manner, then changing tactics on a specific date and time.
What is a backdoor Trojan?
Backdoor malware is generally classified as a Trojan. A Trojan is a malicious computer program pretending to be something it's not for the purposes of delivering malware, stealing data, or opening up a backdoor on your system.
Are PUPs malware?
Type and source of infection. Detections categorized as PUPs are not considered as malicious as other forms of malware, and may even be regarded by some as useful. Malwarebytes detects potentially unwanted programs for several reasons, including: They may have been installed without the user's consent.
What is data sending Trojan?
A data-sending Trojan is a kind of Trojan virus that relays sensitive information back to its owner. This type of Trojan can be used to retrieve sensitive data, including credit card information, email addresses, passwords, instant messaging contact lists, log files and so on.
Is a backdoor malware?
A backdoor is a malware type that negates normal authentication procedures to access a system. As a result, remote access is granted to resources within an application, such as databases and file servers, giving perpetrators the ability to remotely issue system commands and update malware.
What is RAT software?
RAT can also stand for remote administration tool, which is software giving a user full control of a tech device remotely. With it, the user can ac...
What’s the difference between the RAT computer virus and RAT software?
As for functions, there is no difference between the two. Yet, while remote administration tool is for legit usage, RAT connotes malicious and crim...
What are the popular remote access applications?
The common remote desktop tools include but are not limited to TeamViewer, AnyDesk, Chrome Remote Desktop, ConnectWise Control, Splashtop Business...
What Does A Remote Access Trojan Do?
Malware developers use Remote Access Trojan (RAT) tools to gain full access and control over a user’s computer, including mouse and keyboard control, file access, and network resources.
How Is A Remote Access Trojan Executed?
An attacker uses a Trojan to execute a program file on a system. Once the user attempts to open the file, the Trojan is executed, and some dangerous actions are taken. A remote access Trojan program uses a backdoor to control the target machine with administrative privileges.
Are Remote Access Trojans Illegal?
According to law enforcement officials, it is not illegal to possess a remote-access tool. IT support is often provided by remote-access tools in corporate environments. The use of such tools for illegal purposes is a different ballgame, never mind the purpose-built remote access Trojan that can be used.
Is It Illegal To Make A Trojan Virus?
Computer viruses, Trojan horses, and malware are not illegal. You may be held liable for damages caused by the virus if it spreads to other computers intentionally or by mistake.
Can Trojan Virus Be Detected?
By detecting suspicious activity inside your applications, the McAfee antivirus program can also identify new trojans, in addition to detecting known ones.
Is Trojan Virus Illegal?
A Trojan horse is downloaded onto a computer by its owner, and there is a secret program that is hidden on the computer, just like the Greek soldiers who snuck into Troy. The creation and distribution of trojan horse computer software is illegal, as is the management of a botnet and the use of computers for malicious purposes.
How to protect yourself from remote access trojans?
Just like protecting yourself from other network malware threats, for remote access trojan protection, in general, you need to avoid downloading unknown items; keep antimalware and firewall up to date, change your usernames and passwords regularly; (for administrative perspective) block unused ports, turn off unused services, and monitor outgoing traffic.
What is a RAT trojan?
RAT trojan is typically installed on a computer without its owner’s knowledge and often as a trojan horse or payload. For example, it is usually downloaded invisibly with an email attachment, torrent files, weblinks, or a user-desired program like a game. While targeted attacks by a motivated attacker may deceive desired targets into installing RAT ...
How does RAT malware work?
Once get into the victim’s machine, RAT malware will hide its harmful operations from either the victim or the antivirus or firewall and use the infected host to spread itself to other vulnerable computers to build a botnet.
How to check if my computer is safe?
Open the command prompt better as administrator, type “ system.ini ”, and press Enter. Then, a notepad will pop up showing you a few details of your system. Take a look at the drivers section, if it looks brief as what the below picture shows, you are safe. if there are some other odd characters, there may be some remote devices accessing your system via some of your network ports.
Is Sub 7 a trojan horse?
Typically, Sub 7 allows undetected and unauthorized access. So, it is usually regarded as a trojan horse by the security industry. Sub7 worked on the Windows 9x and Windows NT family of OSes, up to and including Windows 8.1. Sub7 has not been maintained since 2014. 4.
Can a RAT remote access trojan be used on a computer?
Since RAT remote access trojan will probably utilize the legitimate apps on your computer, you’d better upgrade those apps to their latest versions. Those programs include your browsers, chat apps, games, email servers, video/audio/photo/screenshot tools, work applications…
What Is The Best Trojan Remote Access?
Hackers commonly use Blackshades to gain remote access to computers. Windows-based operating systems are frequently targeted by this tool. The Trojan has infected 500,000 systems worldwide until now.
Where Are Remote Access Trojans Used?
Malware developers use Remote Access Trojan (RAT) tools to gain full access and control over a user’s computer, including mouse and keyboard control, file access, and network resources.
What Can You Do With A Remote Access Tool?
The remote access programs and tools (sometimes called RATs) allow remote access and manipulation of systems from another location. All types of users can use remote access programs to access files and data on remote computers, and many of them are legitimate tools.
What Is Trojan Ddos?
An infected computer is used to launch a DoS attack from a pre-defined address using this type of malicious program. The malicious user infects a number of computers with this type of Trojan in advance (for example, as part of a mass spam mailing) in order to conduct a successful DoS attack.
What Is The Purpose Of A Trojan Horse?
In general, a Trojan is designed to damage, disrupt, steal, or in general cause some other harm to your data or network.
How are Remote Access Trojans Useful to Hackers?
Attackers using remote control malware cut power to 80,000 people by remotely accessing a computer authenticated into SCADA (supervisor y control and data acquisition) machines that controlled the country’s utility infrastructure. RAT software made it possible for the attacker to access sensitive resources through bypassing the authenticated user's elevated privileges on the network. Having access to critical machines that control city resources and infrastructure is one of the biggest dangers of RAT malware.
Why do attackers use remote devices?
Instead of storing the content on their own servers and cloud devices, attackers use targeted stolen devices so that they can avoid having accounts and servers shut down for illegal content.
How to install a RAT?
An attacker must convince the user to install a RAT either by downloading malicious software from the web or running an executable from a malicious email attachment or message. RATs can also be installed using macros in Microsoft Word or Excel documents. When a user allows the macro to run on a device, the macro silently downloads RAT malware and installs it. With the RAT installed, an attacker can now remotely control the desktop, including mouse movement, mouse clicks, camera controls, keyboard actions, and any configured peripherals.
What is remote control software?
Legitimate remote-control software exists to enable an administrator to control a device remotely. For example, administrators use Remote Desktop Protocol (RDP) configured on a Windows server to remotely manage a system physically located at another site such as a data center. Physical access to the data center isn’t available to administrators, so RDP gives them access to configure the server and manage it for corporate productivity.
What happens if you remove the internet from your computer?
Removing the Internet connection from the device disables remote access to your system by an attacker. After the device can no longer connect to the Internet, use your installed anti-malware program to remove it from local storage and memory. Unless you have monitoring configured on your computer, you won't know which data and files transferred to an attacker. You should always change passwords across all accounts, especially financial accounts, after removing malware from your system.
How are Remote Access Trojans Useful to Hackers?
Attackers using remote control malware cut power to 80,000 people by remotely accessing a computer authenticated into SCADA (supervisor y control and data acquisition) machines that controlled the country’s utility infrastructure. RAT software made it possible for the attacker to access sensitive resources through bypassing the authenticated user's elevated privileges on the network. Having access to critical machines that control city resources and infrastructure is one of the biggest dangers of RAT malware.
Why do attackers use remote devices?
Instead of storing the content on their own servers and cloud devices, attackers use targeted stolen devices so that they can avoid having accounts and servers shut down for illegal content.
How to install a RAT?
An attacker must convince the user to install a RAT either by downloading malicious software from the web or running an executable from a malicious email attachment or message. RATs can also be installed using macros in Microsoft Word or Excel documents. When a user allows the macro to run on a device, the macro silently downloads RAT malware and installs it. With the RAT installed, an attacker can now remotely control the desktop, including mouse movement, mouse clicks, camera controls, keyboard actions, and any configured peripherals.
What is remote control software?
Legitimate remote-control software exists to enable an administrator to control a device remotely. For example, administrators use Remote Desktop Protocol (RDP) configured on a Windows server to remotely manage a system physically located at another site such as a data centre. Physical access to the data centre isn’t available to administrators, so RDP gives them access to configure the server and manage it for corporate productivity.
What happens if you remove the internet from your computer?
Removing the Internet connection from the device disables remote access to your system by an attacker. After the device can no longer connect to the Internet, use your installed anti-malware program to remove it from local storage and memory. Unless you have monitoring configured on your computer, you won't know which data and files transferred to an attacker. You should always change passwords across all accounts, especially financial accounts, after removing malware from your system.
What is intrusion detection?
Intrusion detection systems are important tools for blocking software intrusion that can evade detection by antivirus software and firewall utilities. The SolarWinds Security Event Manager is a Host-based Intrusion Detection System. However, there is a section of the tool that works as a Network-based Intrusion Detection System. This is the Snort Log Analyzer. You can read more about Snort below, however, you should know here that it is a widely used packet sniffer. By employing Snort as a data collector to feed into the Snort Log Analyzer, you get both real-time and historic data analysis out of the Security Event Manager.
Can a hacker use your internet address?
The hacker might also be using your internet address as a front for illegal activities, impersonating you, and attacking other computers. Viruses downloaded through RAT will infect other computers, while also causing damage to your system by erasing or encryption essential software.
Can antivirus be used to get rid of a RAT?
Antivirus systems don’t do very well against RATs. Often the infection of a computer or network goes undetected for years. The obfuscation methods used by parallel programs to cloak the RAT procedures make them very difficult to spot. Persistence modules that use rootkit techniques mean that RATs are very difficult to get rid of. Sometimes, the only solution to rid your computer of a RAT is to wipe out all of your software and reinstall the operating system.
Can a Remote Access Trojan be installed to BIOS?
Access to the BIOS has been known to the world’s hackers since 2015. Many believe that the NSA was planting RATs and trackers on BIOS even earlier.
What Does A Remote Access Trojan Do?
Malware developers use Remote Access Trojan (RAT) tools to gain full access and control over a user’s computer, including mouse and keyboard control, file access, and network resources.
How Is A Remote Access Trojan Executed?
An attacker uses a Trojan to execute a program file on a system. Once the user attempts to open the file, the Trojan is executed, and some dangerous actions are taken. A remote access Trojan program uses a backdoor to control the target machine with administrative privileges.
How Do I Scan My Computer For Trojans?
You can remove malicious software from Microsoft Windows by downloading and running the program…
Can You Get A Virus From Remote Access?
Viruses and malware are not always detected by remote access software solutions. The hacker could easily install malware on your business’s servers and spread to all machines in your office if your home or work PC has been infected and you are using it remotely to access your office network.
How Do I Remove Trojans From My Computer?
The best way to remove trojans is to install and use a reputable antivirus program. In order to detect, isolate and remove trojan signatures, effective antivirus programs search for valid trust and app behavior as well as trojan signatures in files.
Can Windows Defender Remove Trojans?
Microsoft Defender, which was first introduced with Windows XP, is a free antimalware program that protects Windows users from viruses, malware, and other harmful programs. Windows 10 users can use it to detect and remove Trojan horses.
What Is An Example Of A Trojan Virus?
A number of trojans are known to be malicious in government, including the Swiss MiniPanzer and MegaPanzer, as well as the German “state trojan” nicknamed R2D2. Governmentware in Germany exploits security gaps that are unknown to the general public and accesses smartphone data before it is encrypted.