5 Steps to Secure Remote Access
- 1. Assume Hostile Threats Will Occur Laptops, wireless handheld devices and other portable digital gadgets are prone to loss or theft. ...
- 2. Develop Policy Defining Telework, Remote Access ...
- 3. Configure Remote Access Servers to Enforce Policies ...
- 4. Secure Telework Client Devices Against Common Threats ...
- 5. Employ Strong Encryption, User Authentication ...
- Use strong passwords.
- Use Two-factor authentication.
- Update your software.
- Restrict access using firewalls.
- Enable Network Level Authentication.
- Limit users who can log in using Remote Desktop.
What is the best remote access for PC?
What is the Best Remote Desktop Software?
- GoToMyPC. GoToMyPC is the best remote desktop software on this list. ...
- AnyDesk. AnyDesk is one of the most popular remote desktop software platforms, used by over 100 million users globally.
- LogMeIn. ...
- Parallels. ...
- Splashtop Business Access. ...
- Zoho Assist. ...
- ConnectWise Control. ...
- RemotePC. ...
- TeamViewer. ...
- Remote Utilities for Windows. ...
How do I find my Remote Desktop Connection?
You'll need this later.
- Make sure you have Windows 10 Pro. To check, go to Start > Settings > System > About and look for Edition . ...
- When you're ready, select Start > Settings > System > Remote Desktop, and turn on Enable Remote Desktop.
- Make note of the name of this PC under How to connect to this PC. You'll need this later.
How to set up windows for remote file access?
- Select Start.
- In your programs list, Expand Windows Accessories, then select Remote Desktop Connection. ...
- Enter your home computer's IP address, then select Connect.
- Enter your Home computer's username and password, then select OK.
- Your computer is not certified by a third party verification service. ...
Is rdweb secure?
Using Remote Web Access is fine but is less secure than a good VPN, especially if you don't take extra precautions to secure it, i.e. using an alternate server only for RWA, placing it in a DMZ, getting a valid 3rd party SSL cert, etc. Thanks for your feedback! This person is a verified professional.

Which method of remote access is the most secure?
Implement a Secure Connection for Remote Network AccessWired Connection: A wired connection is the most secure method for remote network access.Home Wi-Fi: The second most secure network connection is using a secured home Wi-Fi connection.More items...•
Is remote access security secure?
Yes. A robust cloud-based, highly secure remote access solution can provide unified protection for virtually all users against web-based threats — independent of a VPN connection.
What is the risk of remote access?
The overriding risk of remote access services and software is a hacker gaining deeper access to your organization, exposing you to a host of IT security threats. Once they gain privileged access to your system, it will be difficult to prevent data loss, prevent phishing, protect against ransomware, etc.
Which option creates a secure connection for remote workers?
The only way to secure your remote workforce is a secure VPN. Employees must connect from their laptops, desktops and mobile devices over a VPN connection. It's the secure, private method for virtually entering the corporate office, so to speak.
Is Google remote access secure?
Is Chrome Remote Desktop secure? While remote desktop software comes with inherent risks, Chrome Remote Desktop is safe and secure. Its remote sessions use AES computer encryption through a secure SSL connection, protecting your data while you remotely access your computer.
Is RDP more secure than VPN?
The essential difference when comparing VPNs and RDP is that a VPN doesn't provide your device with any additional functionality the way an RDP does. You're still using the same old device, only that its IP address has changed and it is now a whole lot more secure when accessing the Internet.
Why is RDP so insecure?
Weak user sign-in credentials. The problem is that the same password is often used for RDP remote logins as well. Companies do not typically manage these passwords to ensure their strength, and they often leave these remote connections open to brute force or credential stuffing attacks.
Should I give someone remote access to my computer?
Never allow access to someone who contacts you first. They use this as a pretense to convince you to let them access your computer. Once you have done so, they are free to run a virus or install malware on your computer.
What is the first thing that’s required to ensure smooth remote access via a VPN?
The first thing that’s required to ensure smooth remote access via a VPN is to plan out a comprehensive network security policy.
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
Why is IPSEC used?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
What are the implications of IPSec connections for corporations?
What are the implications of IPSec connections for corporations, considering the very nature of this connection? Well, your employee will only be able to access the network from a single, authorized device. Security is further boosted by the enforcement of antivirus and firewall policies.
What is IPSEC encryption?
IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect data flows between hosts and security gateways.
Why use two factor authentication for VPN?
Adopting two-factor authentication for remote access through VPN further boosts your network security. Now let’s take a look at why you should choose a particular VPN type as a secure connection methodology instead of the alternatives.
What is the line of defense for remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly.
How to unlock a user who has been locked out?
In order to manually unlock a user who has been locked out, go to Administrative Tools in the Start Menu and select Computer Management. In the Local Users and Groups setting, you can click on an individual user and restore their access by un-checking the Account is Disable box.
What is remote desktop?
Remote Desktop is a Windows service that allows users to connect to a host computer from a different location. This allows users to access information stored on a separate computer from any place that allows them to log on to the Remote Desktop application. This has many practical applications in business, but also opens up some obvious security ...
How to change scope of remote desktop?
In the Firewall options, select the Exceptions tab and highlight Remote Desktop. Click the edit button followed by the Change Scope button.
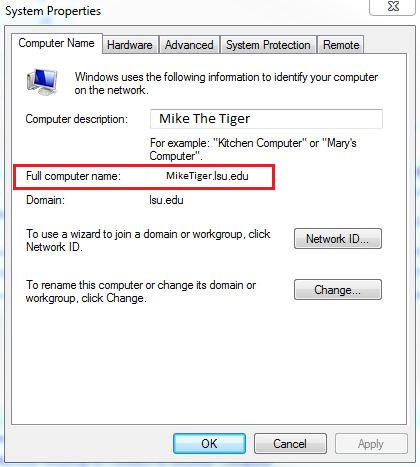
How to limit users on a host computer?
Limit users who can log on to the host computer. Go to the host computer's system properties and select the Remote tab. If Remote Desktop is set up, the box that reads "Allow Users to Connect Remotely" should be checked. If not, check it now. Click the Select Remote Users button, and add which groups of users that can have access to the computer. ...
Can you allow admin access to host computer?
In most versions of Windows, this will still allow users in the administrator group to access the host computer. If you want to change that, go to the Run box in your Windows Start Menu and enter
Can you use only certain IP addresses for remote desktop?
Allow only certain IP addresses to access the Remote Desktop. IP addresses are a unique series of numbers that identifies a computer, and through Windows it is possible to limit the Remote Desktop Connection to only known and trusted IP addresses. To do so, navigate to your Windows Firewall settings through the Windows Control Panel.
Why is remote access important?
It is essential for these individuals to have safe, anytime, anywhere access to corporate networks and services.
What are the risks of remote access?
Many potential risks accompany vendor remote access —from introducing malware into your systems to technical and business dangers.
What percentage of Verizon network intrusions exploited weak or stolen credentials?
According to Verizon’s Data Breach Investigation Report, “76 percent of network intrusions exploited weak or stolen credentials.” Since vendors don’t need constant access to your network, they often use one remote access tool license and share generic logins and passwords across technicians. This makes the credentials easy for hackers to guess. What’s more, the vendor’s ex-employees often retain remote access to your systems.
Why add layered authentication through MFA?
Add layered authentication through MFA to reduce account sharing among third parties. Some of the most significant data breaches of the last decade, like Target and Home Depot, could have been stopped with this simple step.
What happens if you give access to an outsider?
Recognize that granting system access to an outsider lowers your security level to that of the external provider. If they lack strong security controls, they become your weakest link. If a hacker compromises their system, that partner can become a backdoor into your environment .
Where should a server be placed?
Because of this, NIST recommends; in most cases, that a server should be placed at an enterprise's network perimeter so it serves as a single point of entry to the network and enforces the remote work security policy before any remote access traffic is permitted into the enterprise's internal networks.
Can compromised servers be used to eavesdrop?
The National Institute of Standards and Technology (NIST) advises that compromised servers could be wielded to eavesdrop on and manipulate remote access communications. They can also provide a starting point for attacking other hosts within your organization.
How to open local security policy?
Go to the Start menu or open a Run prompt (Windows Key + R) and type “secpol.msc” to open the Local Security Policy menu.
How to change rules on firewall?
When Windows Firewall opens, click “Advanced Settings” on the left side of the window . Then right-click on “Inbound Rules” and choose “New Rule.”
How to see who is logging into my PC?
If you’re wondering how you can keep track of who is logging into your PC (and from where), you can open up Event Viewer to see.
Is network level authentication necessary?
It’s not a necessity to require Network Level Authentication, but doing so makes your computer more secure by protecting you from Man in the Middle attacks . Systems even as old as Windows XP can connect to hosts with Network Level Authentication, so there’s no reason not to use it.
Is remote desktop secure?
How to Enable and Secure Remote Desktop on Windows. While there are many alternatives, Microsoft’s Remote Desktop is a perfectly viable option for accessing other computers, but it has to be properly secured. After recommended security measures are in place, Remote Desktop is a powerful tool for geeks to use and lets you avoid installing third ...
How can information security managers mitigate external security threats?
Information security managers can mitigate external security threats by encrypting data to protect the confidentiality and integrity of communications and authenticating endpoints to verify identities.
What is telework security policy?
A telework security policy should define the form of remote access, types of telework devices allowed to use each form of remote access and the type of access each type of employee or contractor is granted. NIST also suggests the policy should cover how the organization's remote access servers are administered and how policies in those servers are ...
Do teleworkers have to have the same security?
Teleworkers' PCs, laptops and handhelds should have the same local security controls as client devices for non-telework employees. For instance, remote devices should receive the same application and security devices as those found in government facilities. They should employ antivirus software and personal firewalls.
How secure is remote desktop?
How secure is Windows Remote Desktop? Remote Desktop sessions operate over an encrypted channel, preventing anyone from viewing your session by listening on the network. However, there is a vulnerability in the method used to encrypt sessions in earlier versions of RDP.
How to restrict access to remote desktop?
Use firewalls (both software and hardware where available) to restrict access to remote desktop listening ports (default is TCP 3389). Using an RDP Gateway is highly recommended for restricting RDP access to desktops and servers (see discussion below). As an alternative to support off-campus connectivity, you can use the campus VPN software to get a campus IP address and add the campus VPN network address pool to your RDP firewall exception rule. Visit our page for more information on the campus VPN service.
What is RDP gateway?
It provides a way to tightly restrict access to Remote Desktop ports while supporting remote connections through a single "Gateway" server. When using an RD Gateway server, all Remote Desktop services on your desktop and workstations should be restricted to only allow access only from the RD Gateway. The RD Gateway server listens for Remote Desktop requests over HTTPS (port 443) and connects the client to the Remote Desktop service on the target machine.
Why is RDP gateway important?
By enforcing the use of an RDP gateway, you also get a third level of auditing that is easier to read than combing through the domain controller logins and is separate from the target machine so it is not subject to tampering. This type of log can make it much easier to monitor how and when RDP is being used across all the devices in your environment.
What to do if remote desktop is not used?
If Remote Desktop is not used for system administration, remove all administrative access via RDP, and only allow user accounts requiring RDP service. For Departments that manage many machines remotely remove the local Administrator account from RDP access at and add a technical group instead.
How to check if you need authentication for remote connection?
To check you may look at Group Policy setting Require user authentication for remote connections by using Network Level Authentication found at ComputerPoliciesWindows ComponentsRemote Desktop ServicesRemote Desktop Session HostSecurity. This Group Policy setting must be enabled on the server running the Remote Desktop Session Host role.
Why is Remote Desktop better than 3rd party?
One advantage of using Remote Desktop rather than 3rd party remote admin tools is that components are updated automatically with the latest security fixes in the standard Microsoft patch cycle. Make sure you are running the latest versions of both the client and server software by enabling and auditing automatic Microsoft Updates. If you are using Remote Desktop clients on other platforms, make sure they are still supported and that you have the latest versions. Older versions may not support high encryption and may have other security flaws.
How to secure RDP?
Ananth: There are some built-in, no-cost defenses that can secure RDP. These include: 1 Patching: Keep servers especially up to date. 2 Complex passwords: Also use two-factor authentication, and implement lockout policies. 3 Default port: Change the default port used by RDP from 3389 to something else via the Registry. 4 Windows firewall: Use the built-in Windows firewall to restrict RDP sessions by IP address. 5 Network Level Authentication (NLA): Enable NLA, which is non-default on older versions. 6 Limit RDP access: Limit RDP access to a specific user group. Don't allow any domain admin to access RDP. 7 Tunnel RDP access: Tunnel access via IPSec or Secure Shell (SSH).
What are some built-in, no-cost defenses that can secure RDP?
Ananth: There are some built-in, no-cost defenses that can secure RDP. These include: Patching: Keep servers especially up to date. Complex passwords: Also use two-factor authentication, and implement lockout policies. Default port: Change the default port used by RDP from 3389 to something else via the Registry.
What is the RDP vulnerability?
Most notably, 2019 gave rise to a vulnerability known as BlueKeep that could allow cybercriminals to remotely take over a connected PC that's not properly patched.
What is RDP brute forcing?
Ananth: One common tactic is RDP brute-forcing, where attackers automate many login attempts using common credentials, hoping one hits. The second involves exploiting a software vulnerability to gain control of an RDP server. For instance, attackers could exploit BlueKeep ( CVE-2019-0708) to gain complete control of a managed service provider's (MSP) unpatched RDP servers.
What firewall is used to restrict RDP sessions?
Windows firewall: Use the built-in Windows firewall to restrict RDP sessions by IP address.
How many systems are exposed to the internet via RDP?
Web crawlers like shodan.io make it easy for attackers to quickly identify vulnerable public-facing machines. Worldwide, more than two million systems are exposed to the internet via RDP, of which more than 500,000 are in the US.
Can RDP be placed on the internet?
Some major organizations place RDP directly on the internet, but most (hopefully) are doing this unknowingly. Checking on this is pretty simple; just fire up your favorite internet-wide scanner and look at all the RDP instances directly exposed. Ananth: There are some built-in, no-cost defenses that can secure RDP.
How can my staff work from home and access the company network?
As with most things IT-related, the best solution for you depends on your organization’s priorities: security, flexibility, and ease of use.
Firstly, what is a VPN?
A Virtual Private Network (VPN) is the name given to a secure connection from one device to another, usually over an insecure network like the Internet. You may also hear the term “tunnel”, but this is a broader class of connection that doesn’t always provide any security.
What types of VPN are there?
There are two main types of VPN technology in use: IPsec and SSL/TLS. We’ll look at both types here from the viewpoint of your organization’s priorities.
Which type of VPN should I use?
The type of VPN you use will depend on your organizational priorities and may include a mix of both.
How can I deploy VPNs without overloading my IS team?
We recognize that for many companies, despite the advantages of deploying a VPN solution for your remote workforce, it may be too complicated or time-consuming, especially if your IS team has other priorities.
