The FBI recommends the following steps to better protect remote access:
- Use multi-factor authentication (MFA).
- Use strong passwords to protect Remote Desktop Protocol (RDP) credentials.
- Ensure antivirus, spam filters and firewalls are up to date and properly configured.
- Audit network configurations and isolate computer systems that cannot be updated.
- Use strong passwords. ...
- Update your software. ...
- Limit access using firewalls. ...
- Enable Network Level Verification. ...
- Limit users who can log in using remote desktop. ...
- Use two-factor authentication on highly sensitive systems.
How can I prevent remote access to my Windows PC?
Windows 8 and 7 Instructions
- Click the Start button and then Control Panel.
- Open System and Security.
- Choose System in the right panel.
- Select Remote Settings from the left pane to open the System Properties dialog box for the Remote tab.
- Click Don’t Allow Connections to This Computer and then click OK.
How to prevent someone from remote access Windows 10?
How to Block Remote Desktop Access Windows
- Open your control panel in Windows.
- In the search box on the top right, enter "Remote".
- Click on "Allow remote access to this computer" to open the Remote Access Settings.
- Uncheck the Checkbox "Allow remote support connections to this computer".
- Click "OK" and your computer will no longer accept remote desktop connections.
How do I turn off remote access in Windows 10?
Part 4: Disable Remote Desktop Service in Windows 10 with System Genius
- Get iSunshare System Genius downloaded and installed properly in your Windows 10 PC.
- Launch it and take the choice of System Service on the left menu column. Then it will display all the Windows services for you.
- Locate to Remote Desktop Service and click the Disable button to turn off this service on your PC.
How to disable remote access in Windows 10?
To disable Remote Assistance on Windows 10, use these steps:
- Open Control Panel.
- Click on System and Security. …
- Under the “System” section, click the Allow remote access option. …
- Click the Remote tab.
- Under the “Remote Assistance” section, clear the Allow Remote Assistance connection to this computer option.
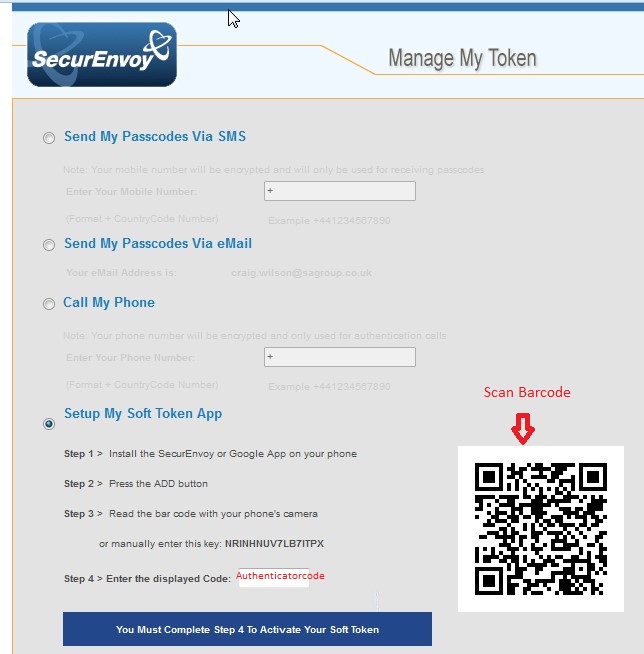
How do I protect my computer from remote access?
Open System and Security. Choose System in the right panel. Select Remote Settings from the left pane to open the System Properties dialog box for the Remote tab. Click Don't Allow Connections to This Computer and then click OK.
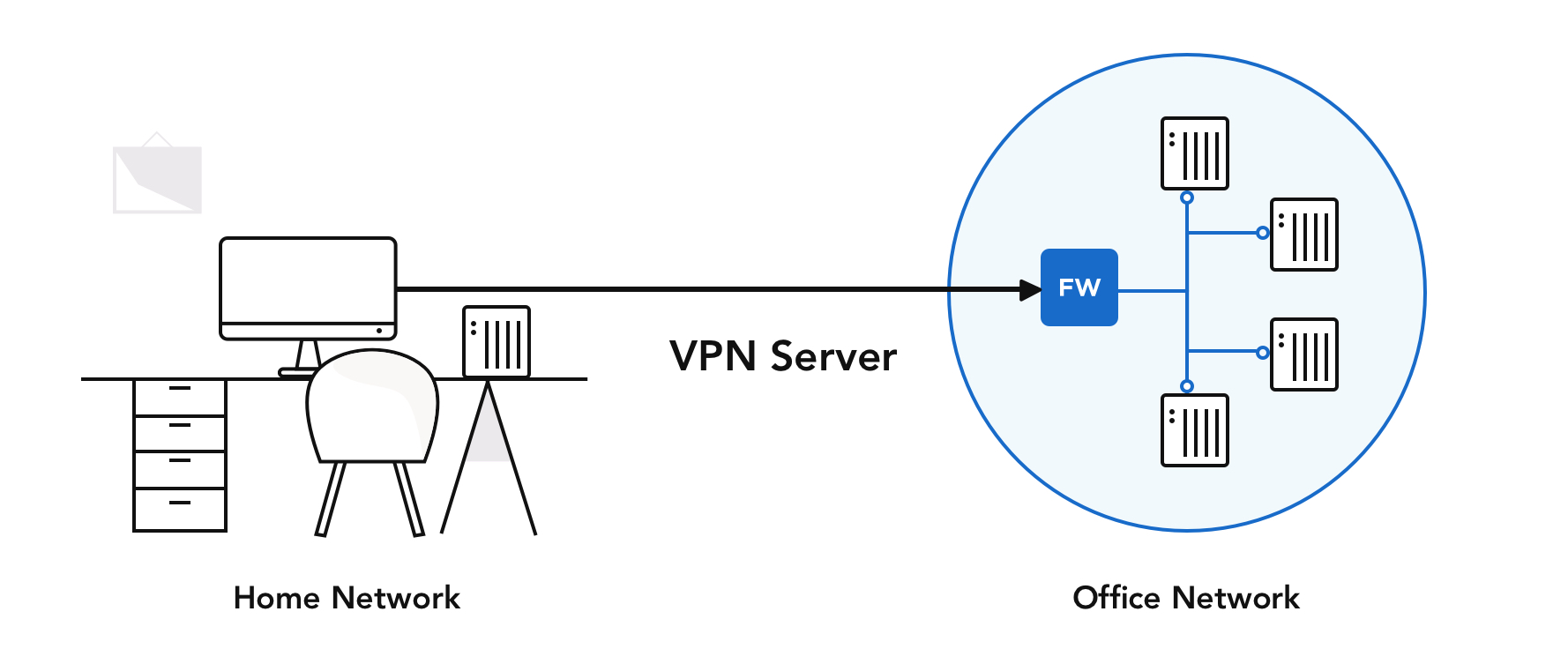
Can VPN stop remote access?
While having some similarities, VPN and remote desktop are functionally different things. A VPN will give you access to a network while remote desktop (or RDP) will give you control of an entire computer. If you want to have full control over a local computer from a remote location, VPN won't let you achieve that.
How do you protect remote users?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
What can we do in order to limit or prevent remote access?
Firewalls can be your first line of defense in network security by limiting those who have remote access. You should set up firewalls to restrict access using software or hardware or both. Update your software regularly. Make sure your software updates automatically so you're working with the latest security fixes.
What are some dangers of remote access?
Many remote access security risks abound, but below is a list of the ones that jump out.Lack of information. ... Password sharing. ... Software. ... Personal devices. ... Patching. ... Vulnerable backups. ... Device hygiene. ... Phishing attacks.
What is the difference between VPN and remote access?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
How can I tell if someone has remote access to my computer?
How to Know If Someone is Accessing My Computer Remotely?Way 1: Disconnect Your Computer From the Internet.Way 2. ... Way 3: Check Your Browser History on The Computer.Way 4: Check Recently Modified Files.Way 5: Check Your computer's Login Events.Way 6: Use the Task Manager to Detect Remote Access.More items...•
Can someone remotely access my computer without my knowledge?
There are two ways someone can access your computer without your consent. Either a family member or work college is physically logging in to your computer or phone when you are not around, or someone is accessing your computer remotely.
Can someone remotely access my computer when IT's off?
Without appropriate security software installed, such as anti-malware tools like Auslogics Anti-Malware, it is possible for hackers to access the computer remotely even if it is turned off.
Will a remote desktop work with VPN on?
To summarize, you can remotely connect to another PC using Remote Desktop from anywhere in the world with the help of a VPN and a router that has native support for VPN connections.
How does remote access work with VPN?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What are the disadvantages of using a VPN?
The 10 biggest VPN disadvantages are:A VPN won't give you complete anonymity: Read more.Your privacy isn't always guaranteed: Read more.Using a VPN is illegal in some countries: Read more.A safe, top-quality VPN will cost you money: Read more.VPNs almost always slow your connection speed: Read more.More items...•
Can I use RDP and VPN at the same time?
There's nothing wrong with VPN connection to the network then RDP to LAN while on the VPN. That's very common as it adds security. This person is a verified professional. Verify your account to enable IT peers to see that you are a professional.
What should security teams do if on-premises network and email security mechanisms are no longer available?
Recommendation: If some on-premises network and email security mechanisms are no longer available, security teams should double down on educating users to identify phishing attempts and to choose strong, unique passwords, encouraging the use of a password manager. They should also implement client certificates and multi-factor authentication in order to prevent attackers from gaining access through unsecured devices.
Why is it important to enforce access based on user identity?
Recommendation: It’s critical that companies enforce access based on user identity, allowing specific groups access to only what they need to get their jobs done, and expanding access from there on an as-needed basis.
What is XDR in security?
Recommendation: Rather than invest in point solutions, consider security platforms that maximize integration between systems, limiting the amount of switching between tools and providing visibility into all data – including remote user activity. Extended detection and response (XDR) not only protects endpoints, but also applies analytics across all your data to find threats like unusual access or lateral movement, and simplifies investigations by stitching together data and identifying the root cause.
What are the risks of using a VPN?
Here are five top security risks that teams must deal with, as well as technology and user education best practices to keep users and data safe: 1. Weak remote access policies. Once attackers get access to a virtual private network (VPN), they can often penetrate the rest of the network like a hot knife through butter.
Why do companies use VPNs?
Historically, many companies deployed VPNs primarily for technical people needing access to critical technology assets. Not so much the case anymore – VPNs are often encouraged for all users as a more secure connection than home or public networks.
What Is A Remote Access Trojan (RAT)?
A remote access trojan (RAT) is a type of malware that enables backdoor administrative control over the targeted computer.
Are You Prepared To Stop A RAT?
Businesses must educate their employees on the dangers of malware infections, and as GI Joe used to say, “knowing is half the battle.”
How to check for unwanted programs?
Check for any new Firewall rules, check for any unwanted apps by going to Control Panel > Uninstall a Program. If you want to achieve paranoid level checks, Regshot, for auditing registry & Windows built in file auditor are also there at your disposal.
What to do if something fishy happened to my PC?
If you suspect something fishy has happened to your PC in your absence, a system wide anti-virus scan should be carried out. An intruder, if failed in finding anything useful, may install a keylogger or worse, ransomware. Even if Windows Defender gives a clean chit, which it does many times, a second scan should be done using some of the popular free anti-virus programs.
Do passwords need to be stored in browsers?
This habit will cost you, if you become victim of such attacks. An alternative is to use password manager (though they are also not immune to attacks), which is advisable, but if you absolutely don’t want to get out of your old habit , a master password gives one more layer of protection.
Can you run TeamViewer on RDP?
Many popular remote apps, including TeamViewer, have an option to run the app instead of installing. So if you want to remote control for just one time it’s wise to just run the app. If you are not using any app and instead using RDP, then remember to disable RDP access after you are done.
What is remote access?
Remote access is a common tool of any IT professionals. If you ever had your computer fixed, you probably had a technician access your machine from a remote location. They can take control of your PC using software created for this specific function.
What is the best way to protect against RATs?
While Windows Defender is a fantastic security software, modern RATs can easily slip past its protection especially when it is not updated. Install a specialized anti-malware program, such as MalwareFox. It allows you to have peace of mind with its real-time protection. Additionally, if you suspect that your machine is infected, its deep scanning function will root out anything hiding in your computer.`
How do RATs gain access to a computer?
It can gain remote access to the victim’s computer through specially configured communication protocols that allow the malware to go unnoticed. The backdoor access provides virtually complete access to the machine such as change settings, monitor the user’s behavior, use the computer’s Internet connection, browse and copy files, and even access to other computers in the victim’s network.
How to tell if a RAT is hiding in your computer?
Determining if a RAT is hiding in your computer is difficult as it does not exhibit the usual symptoms of a malware infection. However, ensuring that you only access legitimate and trustworthy websites is an excellent first step. Make sure that you have proper layers of protection especially if you regularly download files online or use torrent.
How do RATs spy on people?
Moreover, RATs can spy on victims by discreetly activating a computer’s webcam or microphone . It is especially dangerous when a computer is connected to various home gadgets such as home security systems, CCTV cameras, and more. It can escalate to a dangerous situation when the victim’s computer is used to conduct illegal activities, download illicit files, and conduct criminal transactions using your identity.
How to avoid RAT malware?
Fortunately, it is quite easy to avoid RAT malware. Avoid downloading files from untrustworthy sources. A good indicator of a legitimate website is the HTTPS in the URL. Moreover, do not download attachments from emails with unfamiliar sources. Do not torrent files unless you are certain that the source is clean as well.
Can a RAT hack a machine?
The ability to monitor and gather information from anyone without their knowledge certainly opens them for identity theft, bank account infiltration, and more. Unfortunately, this is very possible using a RAT.