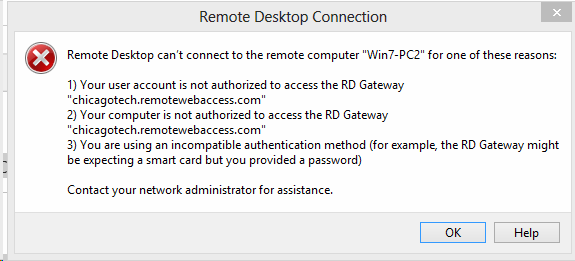
How to disable all remote connection to my computer?
- Open Control Panel.
- Click on System and Security. Source: Windows Central
- Under the "Windows Defender Firewall" section, click the Allow an app through Windows Firewall option. Source: Windows Central
- Click the Change settings button.
- Clear the Remote Assistance option. Source: Windows Central
- Click the OK button.
How to disable remote access in Windows 10?
To disable Remote Assistance on Windows 10, use these steps:
- Open Control Panel.
- Click on System and Security. …
- Under the “System” section, click the Allow remote access option. …
- Click the Remote tab.
- Under the “Remote Assistance” section, clear the Allow Remote Assistance connection to this computer option.
How do I turn off remote access in Windows 10?
Part 4: Disable Remote Desktop Service in Windows 10 with System Genius
- Get iSunshare System Genius downloaded and installed properly in your Windows 10 PC.
- Launch it and take the choice of System Service on the left menu column. Then it will display all the Windows services for you.
- Locate to Remote Desktop Service and click the Disable button to turn off this service on your PC.
How to remove remote access to computer?
Uninstall-Remote Access
- Syntax
- Description. The Unistall-RemoteAccess cmdlet uninstalls DirectAccess (DA) and VPN, both Remote Access (RA) VPN and site-to-site VPN.
- Examples. PS C:\>Uninstall-RemoteAccess Confirm If Remote Access is uninstalled, remote clients will not be able to connect to the corporate network via DirectAccess.
- Parameters. ...
- Inputs
- Outputs
How can you protect your computer when using remote access?
Basic Security Tips for Remote DesktopUse strong passwords. ... Use Two-factor authentication. ... Update your software. ... Restrict access using firewalls. ... Enable Network Level Authentication. ... Limit users who can log in using Remote Desktop. ... Set an account lockout policy.
Can someone remotely access my computer when it's off?
Without appropriate security software installed, such as anti-malware tools like Auslogics Anti-Malware, it is possible for hackers to access the computer remotely even if it is turned off.
How can I protect my PC from other users?
Keep your computer secure at homeUse a firewall. ... Keep all software up to date. ... Use antivirus software and keep it current. ... Make sure your passwords are well-chosen and protected. ... Don't open suspicious attachments or click unusual links in messages. ... Browse the web safely. ... Stay away from pirated material.More items...
How do you know if your PC is being monitored?
How to Check If Your Computer Is Being MonitoredLook for Suspicious Processes. Suspicious processes may indicate that your computer is being monitored. ... Run Antivirus Software. Antivirus software can reveal whether or not your computer is being monitored. ... Evaluate Ports. Another tip is to evaluate your network's ports.
What are the signs that your computer has been hacked?
How do I know that my computer is hacked?Frequent pop-up windows, especially the ones that encourage you to visit unusual sites, or download antivirus or other software.Changes to your home page.Mass emails being sent from your email account.Frequent crashes or unusually slow computer performance.More items...•
What would best prevent an unauthorized person from remotely accessing your computer?
It is essential to use a personal password for all your accounts to prevent unauthorized access. A user has to be more careful about this if they use a shared system. Apart from this, make sure to change passwords often. Use antivirus software.
How do you prevent other people from connecting to your network and accessing your data?
Turn Off File Sharing and Network DiscoveryIn Windows, this is under Control Panel > Network and Internet > Network and Sharing Center > Advanced Sharing Center. Turn off file sharing, printer sharing, public folder sharing, and network discovery.In Mac, go to System Preferences > Sharing and uncheck all boxes.
What technology can prevent a hacker from using your computer when you don't have it?
Firewalls. A firewall is a software program or piece of hardware that blocks hackers from entering and using your computer. Hackers search the internet the way some telemarketers automatically dial random phone numbers.
Can a computer be hacked if it is in sleep mode?
A computer cannot be hacked “in” sleep mode, but it can be hacked either if the user resumes his or her computer to make it back into functioning under the power of the operating system or the hacker triggers a Wake-on-Lan (WOL).
Can someone log into your computer without you knowing?
There are two ways someone can access your computer without your consent. Either a family member or work college is physically logging in to your computer or phone when you are not around, or someone is accessing your computer remotely.
Community Q&A
Include your email address to get a message when this question is answered.
About This Article
wikiHow is a “wiki,” similar to Wikipedia, which means that many of our articles are co-written by multiple authors. To create this article, volunteer authors worked to edit and improve it over time. This article has been viewed 62,622 times.
How to protect your computer when using remote access?
Here are some steps you can take to help protect your computer and data while relying on remote access. Maintain strong passwords.
Why is remote access important?
Remote access software is helpful when you’re in a meeting at another office with your laptop — or telecommuting — and need an important file that’s on your office computer. Remote computer access can help you assist someone in your personal life who might be far away.
Why is it important to limit the number of users who can log in?
Remote computer access can help businesses, individuals, and families in a variety of ways. But it’s important to make remote access secure .
Is there a third party remote access program?
For instance, there are Windows-only and Mac-only programs if your computers and devices all use the same operating system.
Can hackers use RDP?
Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular. Remote desktop servers connect directly to the Internet when you forward ports on your router. Hackers and malware may be able to attack a weakness in those routers.
Can a single person's account be hacked?
A single person’s account can also be hacked and other alternatives are also not one hundred percent attack-proof. Moreover, TeamViewer is a necessity to many to provide remote tech support to their family without dealing with ports & IP addresses.
Can you run TeamViewer on RDP?
Many popular remote apps, including TeamViewer, have an option to run the app instead of installing. So if you want to remote control for just one time it’s wise to just run the app. If you are not using any app and instead using RDP, then remember to disable RDP access after you are done.
How to disable remote admin access?
Click or tap on the slider button to disable remote access. Remember, if you do need someone to occasionally do remote admin, they can always ask you, you can enable it, and then disable it when they’re done. Safer than just leaving this access open and available.
How to check if file sharing is good?
The easy way to check and see if all is good is to go into File Explorer and right-click on a folder. Like the Local Disk (C:) drive itself:
Does Windows 10 Home support remote desktop?
If you’ve got Windows 10 Home Edition, you’ll click and then see something like this: It might be a bit hard to read, but it says “ Your Home edition of Windows 10 doesn’t support Remote Desktop .”. Okay, that’s good. If you have the Pro version of Win10, however, you might find that it does support Remote Desktop and that it’s enabled!
What is remote desktop?
Remote Desktop is a Windows service that allows users to connect to a host computer from a different location. This allows users to access information stored on a separate computer from any place that allows them to log on to the Remote Desktop application. This has many practical applications in business, but also opens up some obvious security ...
How to limit users on a host computer?
Limit users who can log on to the host computer. Go to the host computer's system properties and select the Remote tab. If Remote Desktop is set up, the box that reads "Allow Users to Connect Remotely" should be checked. If not, check it now. Click the Select Remote Users button, and add which groups of users that can have access to the computer. ...
How to change scope of remote desktop?
In the Firewall options, select the Exceptions tab and highlight Remote Desktop. Click the edit button followed by the Change Scope button.
Can you use only certain IP addresses for remote desktop?
Allow only certain IP addresses to access the Remote Desktop. IP addresses are a unique series of numbers that identifies a computer, and through Windows it is possible to limit the Remote Desktop Connection to only known and trusted IP addresses. To do so, navigate to your Windows Firewall settings through the Windows Control Panel.
What is the line of defense for remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly.
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
Why is IPSec VPN important?
IPSec VPN connections are also important for an employee who needs widespread access to the company’s network. A word of warning: If you are using IPSec VPN for remote access, but you are not deploying Internet Key Exchange (IKE, certificates) as an authentication method, the connection will be vulnerable.
Why is IPSEC used?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
What is IPSEC protocol?
IPSec: IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect data flows between hosts and security gateways. The unique feature of IPSec is that it operates at the Network Layer of the Open Systems Interconnection (OSI) protocol model.
What do people use in an office?
Most, if not all, of the day-to-day tasks performed in offices today rely heavily on technology, mainly computers, laptops , tablets & smart devices. As the world and the global economy become increasingly interconnected, members of the staff too are required to go mobile. Sometimes, the need arises to work from home or somewhere away from the office, plus, a lot of companies have more than one office, in different parts of the world, and that requires them to have secure communications and exchange of data between offices.
Should a company use IPSEC VPN?
A company should go for IPSec VPN remote access if it has a strong networking department with the ability to configure each employee’s hardware device individually (installing client software, enforcing security policies etc.).
How to secure RDP?
Ananth: There are some built-in, no-cost defenses that can secure RDP. These include: 1 Patching: Keep servers especially up to date. 2 Complex passwords: Also use two-factor authentication, and implement lockout policies. 3 Default port: Change the default port used by RDP from 3389 to something else via the Registry. 4 Windows firewall: Use the built-in Windows firewall to restrict RDP sessions by IP address. 5 Network Level Authentication (NLA): Enable NLA, which is non-default on older versions. 6 Limit RDP access: Limit RDP access to a specific user group. Don't allow any domain admin to access RDP. 7 Tunnel RDP access: Tunnel access via IPSec or Secure Shell (SSH).
What are some built-in, no-cost defenses that can secure RDP?
Ananth: There are some built-in, no-cost defenses that can secure RDP. These include: Patching: Keep servers especially up to date. Complex passwords: Also use two-factor authentication, and implement lockout policies. Default port: Change the default port used by RDP from 3389 to something else via the Registry.
What is the RDP vulnerability?
Most notably, 2019 gave rise to a vulnerability known as BlueKeep that could allow cybercriminals to remotely take over a connected PC that's not properly patched.
How many systems are exposed to the internet via RDP?
Web crawlers like shodan.io make it easy for attackers to quickly identify vulnerable public-facing machines. Worldwide, more than two million systems are exposed to the internet via RDP, of which more than 500,000 are in the US.
Do all RDP instances need a VPN?
Gamblin: Without many exceptions, all RDP instances should require multiple levels of access and authentication controls. This would include the use of a VPN to access an RDP instance and requiring a second factor (like Duo) for authentication.
Can RDP be placed on the internet?
Some major organizations place RDP directly on the internet, but most (hopefully) are doing this unknowingly. Checking on this is pretty simple; just fire up your favorite internet-wide scanner and look at all the RDP instances directly exposed. Ananth: There are some built-in, no-cost defenses that can secure RDP.
How to remotely access a PC?
On the device you want to connect to, select Start and then click the Settings icon on the left. Select the System group followed by the Remote Desktop item. Use the slider to enable Remote Desktop.
How to remotely connect to Windows 10?
Windows 10 Fall Creator Update (1709) or later 1 On the device you want to connect to, select Start and then click the Settings icon on the left. 2 Select the System group followed by the Remote Desktop item. 3 Use the slider to enable Remote Desktop. 4 It is also recommended to keep the PC awake and discoverable to facilitate connections. Click Show settings to enable. 5 As needed, add users who can connect remotely by clicking Select users that can remotely access this PC .#N#Members of the Administrators group automatically have access. 6 Make note of the name of this PC under How to connect to this PC. You'll need this to configure the clients.
