- 1. Install Nmap Nmap is the tool most hackers use to conduct reconnaissance on a remote target. ...
- 2. Install TOR Tor is the most used software in the world to protect privacy while surfing the internet and sometimes to access the deep/dark web. ...
- 3. Install Proxychains ...
- 4. Start scanning anonymously
Full Answer
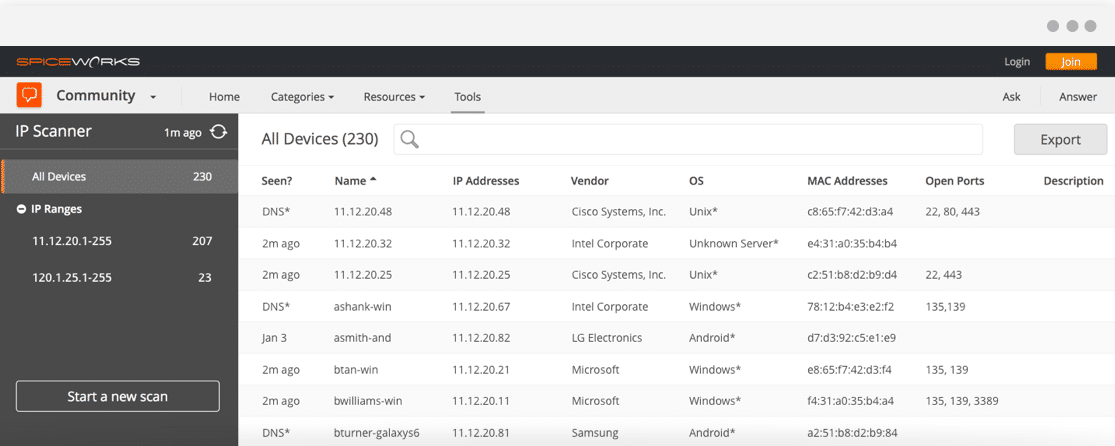
How do I scan for computers in the network?
Enter your range of IP addresses ("IP" button in the toolbar will help you to set the IP-address range of your network). 2. Click "Scan". Once the scanning process has been completed you will get a list of the computers in the network.
How to find the IP address of the camera being accessed?
HTTP://192.168.1.101 represents the IP address of the camera being accessed. Step 1. Find your camera’s IP address. If you don’t know its IP address, click here. Step 2. Open a web browser and type the IP address. Enter your login information. Step 3.
How can network scanning tools help you find IP addresses?
Not only can network scanning tools help you find IP addresses, but they can also provide extra information for monitoring, troubleshooting, and keeping your network running efficiently.
How to remotely access a computer with IP address?
For you to be able to successfully remote access a computer with IP address, it is great to know some of the basic concepts involving home networking. Most of the internet providers supply their subscribers with devices that combine the functionality of a router and modem in a single pack.
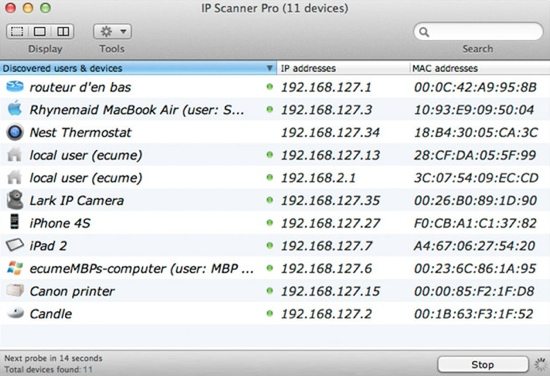
How do I find the IP address of a device remotely?
How to Find a Remote IP AddressClick "Start | All Programs | Accessories | Command Prompt" or click "Start," type "cmd.exe" and press "Enter."Type "ping
How do I find the IP address of a remote computer using command prompt?
Windows 7 Instructions: First, click on your Start Menu and type cmd in the search box and press enter. A black and white window will open where you will type ipconfig /all and press enter. There is a space between the command ipconfig and the switch of /all. Your ip address will be the IPv4 address.
How do I scan a network IP address?
On Windows or macOS type ipconfig or on Linux type ifconfig. Press return. Note down the subnet mask, the default gateway, and your own computer's IPv4 address. Enter the command arp -a to get a list of all other IP addresses active on your network.
How can I find the IP address of another computer?
How to Find All IP Addresses on a NetworkOpen the command prompt.Enter the command “ipconfig” for Mac or “ifconfig” on Linux. ... Next, input the command “arp -a”. ... Optional: Input the command “ping -t”.
How can I remotely access another computer using cmd?
Use CMD to Access Another Computer Press the Windows key+r together to bring up Run, type "cmd" in the field, and press Enter. The command for the Remote Desktop connection app is "mstsc," which you use to launch the program. You are then prompted for the computer's name and your username.
Can you run ipconfig on a remote computer?
Using psexec, you can run ipconfig /all remotely on the remote machine and return the result to your local computer.
How to find IP address on network?
Or you can use a device connected to the network to ping the network and view the ARP tables. Done manually in this way, you have to do everything through the command line. Use the prompt “ipconfig” on Windows to get network settings, followed by “arp -a” to view IPs plus MAC addresses.
What is a network scanner?
This is another strong business-level contender for network scanner tools. MyLanViewer is an IP and network scanner, as well as a traceroute tool and network monitor. It uses a buddy-list style window to display all your network computers, including important technical information about each one. It can scan your network to monitor IPs and let you know when any details change.
What is IP address manager?
Instead of attempting to manually manage these aspects of your network, I recommend using an IP address manager (IPAM). These tools help you manage your IP addresses and troubleshoot problems, and they also help you find all the IP addresses of the devices on your network and determine the status of each one (dynamic, static, available, reserved, etc.). Some tools will also integrate with DNS and DHCP, and all of them will usually present data in a visual, interactive format. Many also allow you to save your network scanning results and present them in spreadsheets or reports.
What format does angry scan?
Angry IP Scanner maintained by angryziber. Angry IP Scanner can also produce reports in XML, CSV, and TXT format, which is useful for exporting data and other information within your business. It uses a multi-threaded scanning approach, which uses a separate scanning thread for each IP address.
What is a network topology mapper?
Looking for a combination network scanning and mapping tool? Network Topology Mapper is designed to use a unique, multi-layer discovery method using SNMP v1-v3, ICMP, WMI, CDP, VMware, Hyper-V, and more to create network diagrams with integrated OSI layer 2 and 3 topology data.
Is network scanning necessary?
Network scanning is a necessary task, but it can start off simple and rapidly become more complicated as your business gets larger. Manually finding IP addresses on your network is possible, but why do it yourself when there are so many tools to help you? Not only can network scanning tools help you find IP addresses, ...
Can you assign admin permissions to other admins?
You can easily assign management or control permissions to other admins or admin groups, allowing you to simply delegate tasks within IPAM rather than needing to use another tool. The console is centralized, allowing you to see all the relevant information in one place, reducing the potential for error.
How to scan for malware on Windows 10?
If you're using Windows 10, you can use the built-in scanning tools in Settings > Update & Security > Windows Security to check for rogue applications. If you're using a Mac, check out How to Scan a Mac for Malware to learn how to use Mac-based scanning tools.
How to install antivirus on another computer?
If you don't have an antivirus, download an installer on another computer and transfer it to your computer via USB. Install the antivirus and then run a scan with it.
How to know if malware has been removed?
Monitor your computer after removing any malware. If your antivirus and/or Anti-Malware found malicious programs, you may have successfully removed the infection, but you'll need to keep a close eye on your computer to ensure that the infection hasn't remained hidden.
What to do if your computer is compromised?
Change all of your passwords . If your computer was compromised, then there’s a possibility that all of your passwords have been recorded with a keylogger. If you’re sure the infection is gone, change the passwords for all of your various accounts. You should avoid using the same password for multiple services.
How to stop someone from accessing my computer?
This includes removing any Ethernet cables and turning off your Wi-Fi connections.
What to do if you can't get rid of intrusion?
If you're still experiencing intrusions, or are concerned that you may still be infected, the only way to be sure is to completely wipe your system and reinstall your operating system.
How to get rid of rootkits?
Download and run the Malwarebyte s Anti-Rootkit Beta. You can get this program for free from https://www.malwarebytes.com/antirootkit. This will detect and remove "rootkits," which are malicious programs that exist deep in your system files. The program will scan your computer, which may take a while to complete.
How to scan a network?
1. Enter your range of IP addresses ("IP" button in the toolbar will help you to set the IP-address range of your network). 2. Click "Scan". Once the scanning process has been completed you will get a list of the computers in the network.
What is advanced IP scanner?
Advanced IP Scanner is fast and free software for network scanning. It will allow you to quickly detect all network computers and obtain access to them. With a single click, you can turn a remote PC on and off, connect to it via Radmin, and much more.
What is RDP in computer?
RDP (Remote Desktop Protocol) developed by Microsoft provides a graphical interface that allows a user to work on another computer over a network connection. Allows you to connect to a selected computer via RDP. To perform this operation: Main menu - "Actions → RDP"; Shortcut menu - "RDP";
What command is used to trace a route to a remote computer?
Starts a terminal window with the tracert command to trace the route to the remote computer.
What is the best remote control software for Windows?
Radmin is one of the best remote control software for Windows, allowing you to work at a remote computer as if you were sitting right in front of it, using a standard graphical interface.
How to find the HTTP port number on a camera?
Go to SETTING > BASIC > Network > Information to find the HTTP port number used by the camera. The default is 80.
How to add a camera to a router?
Step 1. Log into your router’s management page (http://www.tp-link.us/faq-87.html). Go to Forwarding > Virtual Servers and click Add New. Step 2. Type the IP address and the port used by the camera in the corresponding field. For the Protocol, we recommend you select ALL.
What port is used for the camera?
Port 3333 can now be used by the camera.
Table of contents
Windows 10 does not come with Telnet pre-installed. Even DOS Command Prompt has also become secondary with PowerShell taking the center stage.
Install Telnet in Windows 10
If you are going strictly with a DOS based command then you are left with no option but to install telnet in Windows 10. To install Telnet, follow the instructions below:
Check whether the port is open or not using Command Prompt
Open Telnet using the three steps described above and issue the following command:
Check open port using PowerShell
Since Microsoft is pushing PowerShell and CMD has become a legacy system, we should be using PowerShell for most of our working. Let’s check whether a remote network port is open and listening or not.
How to pull IP address from unknown host?
To pull an IP address of an unknown host via ARP, start Wireshark and begin a session with the Wireshark capture filter set to arp, as shown above.
What is IP address?
An IP address is a unique identifier used to route traffic on the network layer of the OSI model. If you think of your local network as a neighborhood, a network address is analogous to a house number. When you know the IP address of a host, it’s possible to access and interact with it.
What are Wireshark and IP Addresses?
Wireshark is a network monitor and analyzer. It works below the packet level, capturing individual frames and presenting them to the user for inspection. Using Wireshark, you can watch network traffic in real-time, and look inside to see what data is moving across the wire.
What devices can Wireshark use to capture packets?
Wireshark captures packets through the network interface of the computer that it is installed on. It can run on Windows, Linux, macOS, FreeBSD, OpenBSD, Solaris, and Unix.
How to capture DHCP traffic?
To capture DHCP traffic, I like to start a new session with no capture filter and set the Wireshark display filter to udp.port==67 as shown above. Then wait for the unknown host to come online and request an IP address from your DHCP server.
What is ARP in Wireshark?
Address Resolution Protocol (ARP) requests can be used by Wireshark to get the IP address of an unknown host on your network. ARP is a broadcast request that’s meant to help the client machine map out the entire host network.
How to force every host to request a new IP address?
You can also force every host on your network to request a new IP address by setting the lease time to an hour or two and capturing network traffic. In this case, you’d want to browse through hostnames until you find the target client.
What is SCAN in Oracle?
Single Client Access Name (SCAN) is a feature used in Oracle Real Application Clusters environments that provides a single name for clients to access any Oracle Database running in a cluster. SCAN was first introduced with Oracle Real Application Clusters (RAC) 11g Release 2 as part of the Oracle Grid Infrastructure suite of products and was further enhanced with Oracle RAC 12c.
What is a scan listener?
During cluster configuration, several resources are created in the cluster for SCAN. For each of the 3 IP addresses that the SCAN resolves to, a SCAN VIP resource is created and a SCAN Listener is created. The SCAN Listener is dependent on the SCAN VIP and the 3 SCAN VIPs (along with their associated listeners) will be dispersed across the cluster.
What is the CMAN parameter in Oracle RAC?
If you use Oracle Connection Manager (CMAN) with your Oracle RAC Database, the REMOTE_LISTENER parameter for the Oracle RAC instances should include the CMAN server so that the CMAN server will receive load balancing related information and can therefore load balance connections across the available instances.
What does round robin DNS do?
Round-robin on DNS level allows for a connection request load balancing across SCAN listeners floating in the cluster. It is not required for SCAN to function as a whole and the absence of such a setup will not prevent the failover of a connection request to another SCAN listener, in case the first SCAN listener in the list is down.
Can scan be used in multiple configurations?
SCAN can be used in multiple configurations. This paper describes the recommended setup, which does not exclude other configurations, as long as you are aware of their implications. The following section discusse some less-common, configurations and will be updated over time as needed.
Can you scan on more than one subnet?
In order to use a SCAN on more than one subnet in the cluster, you must first enable the use of multiple subnets in the cluster, which in general is a post-installation task, including the following steps:
Can SCAN be set up to support more than one port?
For the purpose of allowing applications to maintain a distinguishable connect string on host / port level using one SCAN as the host or to enable port-based firewall configurations, SCAN can be set up to support more than one port for the same subnet.