- Enter the remote port number in the Source port field (e.g., 8080 ).
- Type the destination address and port number in the Destination field using the following format localhost:local_port (e.
- Once you verify that the information you entered is correct, click Add.
- Select Open to establish a remote SSH port-forward.
- Open the SSH terminal on your machine and run the following command: ssh your_username@host_ip_address. ...
- Type in your password and hit Enter. ...
- When you are connecting to a server for the very first time, it will ask you if you want to continue connecting.
How to enable SSH access?
- You should see an "active" status. If you don't, you may need to restart your system and try again.
- To stop SSH, enter systemctl stop sshd and you'll see an "inactive" tag.
- If you want SSH to automatically start whenever you reboot the system, enter: sudo systemctl enable sshd. Change "enable" to "disable" if you want to cancel the automatic setting.
How to use SSH to connect to a remote server?
Start the SSH server
- Open a browser on your technician PC and navigate to the URL of your Factory OS device.
- Once connected to Device Portal, navigate to the SSH tab in the left-hand pane. The SSH tab is at the bottom of the list.
- Select Enable SSH.
How do I Secure my SSH access?
- Use the built in VPN server on your Windows machine to additionally secure your traffic. ...
- Set client connection encryption level. ...
- Employ two-factor authentication using a third-party tool, such as Duo Security. ...
- Enforce firewall rules to limit exposure of open RDP ports to the Internet, especially if you are using the default RDP TCP port 3389. ...
How do I use SSH to Access MySQL remotely?
Perform the following steps to create an SSH tunnel to the MySQL server with PuTTY:
- Launch Putty and enter the IP Address of the server in the Host name (or IP address) field:
- Under the Connection menu, expand SSH and select Tunnels. ...
- Go back to the Session page to save the settings so that you do not need to enter them again. ...
- Select the saved session and log in to the remote server by clicking on the Open button. ...
How do I set up SSH remotely?
How to setup SSH keysStep 1: Generate SSH Keys. Open the terminal on your local machine. ... Step 2: Name your SSH keys. ... Step 3: Enter a passphrase (optional) ... Step 4: Move the public key to the remote machine. ... Step 5: Test your connection.
How do I SSH into a device?
ConnectOpen a Command prompt window on your technician PC.Connect to the device: To connect using a username and password: cmd Copy. ssh user@192. 168. ... Enter the password for your user if you're connecting with a username and password, or if you configured your key to require a password.
How do I SSH to another computer?
2:043:52How to use SSH (to connect to another computer) - YouTubeYouTubeStart of suggested clipEnd of suggested clipSo we can open up the command prompt and go SSH storm cloud so this is the username that you'reMoreSo we can open up the command prompt and go SSH storm cloud so this is the username that you're logging in with at the IP address you know one six eight dot zero dot 200 in my case.
How does SSH connection work?
So, here's how SSH works in Linux, Mac, etcClient contacts server to initiate a connection.The server responds by sending the client a public cryptography key.The server negotiates parameters and opens a secure channel for the client.The user, through their client, logs into the server.
What does SSH stand for?
Secure ShellSSH, also known as Secure Shell or Secure Socket Shell, is a network protocol that gives users, particularly system administrators, a secure way to access a computer over an unsecured network.
Can you SSH into a device on a different network?
Yes, it is absolutely possible. You typically use port forwarding for that (for different residential routers, the way you do port forwarding may vary).
How do I enable SSH on Windows?
Install OpenSSH for WindowsOpen Settings, select Apps, then select Optional Features.Scan the list to see if the OpenSSH is already installed. If not, at the top of the page, select Add a feature, then: Find OpenSSH Client, then select Install. Find OpenSSH Server, then select Install.
How can I remotely access a server by IP address?
Remote Desktop to Your Server From a Local Windows ComputerClick the Start button.Click Run...Type “mstsc” and press the Enter key.Next to Computer: type in the IP address of your server.Click Connect.If all goes well, you will see the Windows login prompt.
Can you SSH into any device?
You are now able to SSH into any machine with the server-side application on it, provided that you have the necessary privileges to gain access, as well as the hostname or IP address.
Can you SSH into a phone?
SSH lets you completely control your Android over WiFi. You can issue commands like ls, mkdir, find, etc. Though, to take full advantage of this, you'll have to be familiar with the terminal command. Moreover, SSH lets you transfer files securely to your Android device.
How do I SSH into my Samsung phone?
Connecting to an Android device over SSHInitial Setup. Install Android App Termux from APKPure or AppStore. ... Install and run SSH Server. Next, run the following commands inside the Termux using the on device keyboard to type. ... Connect to SSH Server. ... Stop SSH Server. ... Troubleshooting. ... Reference.
How do I SSH into my phone using Raspberry Pi?
0:282:11How to SSH to your Raspberry Pi from your mobile phone - YouTubeYouTubeStart of suggested clipEnd of suggested clipAnd set up the services that i want to have access to when i'm not on the local network opening theMoreAnd set up the services that i want to have access to when i'm not on the local network opening the remoted app i select my raspberry pi. And select the ssh service and click connect.
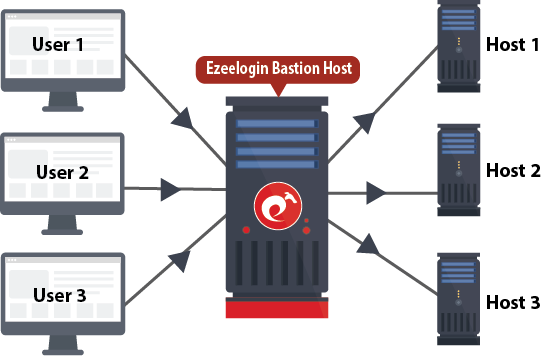
Can you share PrivX credentials?
So even when using shared accounts, the user cannot share any credentials to anyone else.
Can you restrict access to specific networks?
You can also restrict access to only to specific networks/target hosts when connecting from the PrivX GUI to websites. Login as self to web target is possible if the user provides own credentials for the web service. Again, optional session recording is possible. If needed, additional PrivX Extender component can be used to access Web targets (as well as SSH and RDP targets) in a private network or virtual private clouds (VPC).
What is SSH in a network?
Secure Shell (SSH) is a protocol which provides a secure remote access connection to network devices. Communication between the client and server is encrypted in both SSH version 1 and SSH version 2. Implement SSH version 2 when possible because it uses a more enhanced security encryption algorithm. This document discusses how to configure and ...
What is SSH authentication?
SSH uses either local security or the security protocol that is configured through AAA on your router for user authentication. When you configure AAA, you must ensure that the console is not running under AAA by applying a keyword in the global configuration mode to disable AAA on the console.
How to prevent non-SSH connections?
If you want to prevent non-SSH connections, add the transport input ssh command under the lines to limit the router to SSH connections only . Straight (non-SSH) Telnets are refused.
How many steps are required to enable SSH on Cisco router?
There are four steps required to enable SSH support on a Cisco IOS router:
What does show ssh mean?
show ssh âDisplays the status of SSH server connections.
What happens if you reject SSH?
If your SSH configuration commands are rejected as illegal commands, you have not successfully generated a RSA key pair for your router. Make sure you have specified a host name and domain. Then use the crypto key generate rsa command to generate an RSA key pair and enable the SSH server.
Why isn't the connect button enabled?
The Connect button is not enabled if you do not enter the host name and username. This screenshot shows that the login banner is displayed when Secure Shell connects to the router. Then, the login banner password prompt displays. The PuTTY client does not require the username to initiate the SSH connection to the router.
What is SSH config?
Enter SSH config, which is a per-user configuration file for SSH communication. Create a new file: ~/.ssh/config and open it for editing:
What happens if you remove the keys from ssh-agent?
But if you remove the keys from ssh-agent with ssh-add -D or restart your computer, you will be prompted for password again when you try to use SSH. Turns out there's one more hoop to jump through. Open your SSH config file by running nano ~/.ssh/config and add the following:
Can you use a different SSH key?
Managing SSH keys can become cumbersome as soon as you need to use a second key. Traditionally , you would use ssh-add to store your keys to ssh-agent, typing in the password for each key.
Can you enter a password every time you initialize an SSH connection?
The last piece of the puzzle is managing passwords. It can get very tedious entering a password every time you initialize an SSH connection. To get around this, we can use the password management software that comes with macOS and various Linux distributions.
Can you use multiple SSH keys?
For example, you might be using one SSH key pair for working on your company's internal projects, but you might be using a different key for accessing a client's servers. On top of that, you might be using a different key pair for accessing your own private server.
Does host add keys to agent?
Host * AddKeysToAgent yes UseKeychain yes. With that, whenever you run ssh it will look for keys in Keychain Access. If it finds one, you will no longer be prompted for a password. Keys will also automatically be added to ssh-agent every time you restart your machine. Now that you know the basics of creating new SSH keys ...
What is SSH remoting?
SSH remoting lets you do basic PowerShell session remoting between Windows and Linux computers. SSH remoting creates a PowerShell host process on the target computer as an SSH subsystem. Eventually we'll implement a general hosting model, similar to WinRM, to support endpoint configuration and JEA.
What is SSH in PowerShell?
SSH is now available for Linux and Windows platforms and allows true multiplatform PowerShell remoting. WinRM provides a robust hosting model for PowerShell remote sessions.
How to tell if PowerShell supports SSH?
You can confirm that PowerShell has SSH remoting support by listing the New-PSSession parameter sets. You'll notice there are parameter set names that begin with SSH. Those parameter sets include SSH parameters.
How to create a remote session?
To create a remote session, you specify the target computer with the HostName parameter and provide the user name with UserName. When running the cmdlets interactively, you're prompted for a password. You can also use SSH key authentication using a private key file with the KeyFilePath parameter. Creating keys for SSH authentication varies by platform.
Where is OpenSSH installed?
Add the path where OpenSSH is installed to your Path environment variable. For example, C:Program FilesOpenSSH. This entry allows for the ssh.exe to be found.
Where is the PowerShell executable located?
The default location of the PowerShell executable is /usr/local/bin/pwsh. The location can vary depending on how you installed PowerShell.
Does SSH use multifactor authentication?
PowerShell remoting over SSH relies on the authentication exchange between the SSH client and SSH service and doesn't implement any authentication schemes itself. The result is that any configured authentication schemes including multi-factor authentication are handled by SSH and independent of PowerShell. For example, you can configure the SSH service to require public key authentication and a one-time password for added security. Configuration of multi-factor authentication is outside the scope of this documentation. Refer to documentation for SSH on how to correctly configure multi-factor authentication and validate it works outside of PowerShell before attempting to use it with PowerShell remoting.
How does SSH authentication work?
How SSH key authentication works. SSH public key authentication works with an asymmetric pair of generated encryption keys. The public key is shared with Azure DevOps and used to verify the initial ssh connection. The private key is kept safe and secure on your system.
What happens when you register a new SSH key?
A: Whenever you register a new SSH Key with Azure DevOps Services, you will receive an email notification informing you that a new SSH key has been added to your account.
Can you configure multiple keys for SSH?
A: Generally, if you configure multiple keys for an SSH client and connect to an SSH server, the client can try the keys one at a time until the server accepts one.
Can you change SSH key in Azure DevOps?
Once saved, you cannot change the key. You can delete the key or create a new entry for another key. There are no restrictions on how many keys you can add to your user profile. Also note that SSH keys stored in Azure DevOps expire after five years.
Does Fedora Linux support SSH?
A: Some Linux distributions, such as Fedora Linux, have crypto policies that require stronger SSH signature algorithms than Azure DevOps supports (as of January 2021). There's an open feature request to add this support.
What is remote SSH?
The Remote - SSH extension is used to connect to SSH hosts.
How to add SSH key to VM?
In the previous step, you generated an SSH key pair. Select Use existing public key in the dropdown for SSH public key source so that you can use the public key you just generated. Take the public key and paste it into your VM setup, by copying the entire contents of the id_rsa.pub in the SSH public key.
How to get started with OpenSSH?
To get started, you need to have done the following steps: Install an OpenSSH compatible SSH client (PuTTY is not supported). Install Visual Studio Code. Have an Azure subscription ( If you don't have an Azure subscription, create a free account before you begin).
What is remote status bar?
The Remote Status bar item can quickly show you in which context VS Code is running (local or remote) and clicking on the item will bring up the Remote - SSH commands.
How to access a port on a remote machine?
To be able to access a port on the remote machine that may not be publicly exposed, you need to establish a connection or a tunnel between a port on your local machine and the server. With the app still running, open the SSH Explorer and find the Forwarded Ports view.
Can you connect Visual Studio code to SSH?
You get the full development experience of Visual Studio Code connected over SSH.
Can you use a PuttyGen key in a VM?
We strongly recommend using key-based authentication (if you use a username/password, you'll be prompted to enter your credentials more than once by the extension). If you're on Windows and have already created keys using PuttyGen, you can reuse them.
What is SSH in Visual Studio?
The Visual Studio Code Remote - SSH extension allows you to open a remote folder on any remote machine, virtual machine, or container with a running SSH server and take full advantage of VS Code's feature set. Once connected to a server, you can interact with files and folders anywhere on the remote filesystem.
How to close remote connection in VS Code?
To close the connection when you finish editing files on the remote host, choose File > Close Remote Connection to disconnect from the host. The default configuration does not include a keyboard shortcut for this command. You can also simply exit VS Code to close the remote connection.
What is localforward in SSH?
If you have ports that you always want to forward, you can use the LocalForward directive in the same SSH config file you use to remember hosts and advanced settings .
Which is better: rsync or sshfs?
If you need to use an application that bulk reads/write to many files at once (like a local source control tool), rsync is a better choice.
How to change the port of a tunnel?
Right-click the tunnel you want to modify, and select Change Local Port in the context menu.
How to forward a port in Remote Explorer?
Once you are connected to a host, if you want to temporarily forward a new port for the duration of the session, select Forward a Port from the Command Palette ( F1, Ctrl+Shift+P) or click on the Forward New Port icon in the Remote Explorer after selecting it from the Activity Bar.
How to see which host you are connected to?
You can always refer to the Status bar to see which host you are connected to. Clicking on the Status bar item will provide a list of remote commands while you are connected. You can then open any folder or workspace on the remote machine using File > Open... or File > Open Workspace... just as you would locally!

Introduction
Prerequisites
- Requirements
The Cisco IOS image used must be a k9(crypto) image in order to support SSH. For example c3750e-universalk9-tar.122-35.SE5.taris a k9 (crypto) image. - Components Used
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command. The informati…
Test Authentication
- Authentication Test without SSH
First test the authentication without SSH to make sure that authentication works with the router Carter before you add SSH. Authentication can be with a local username and password or with an authentication, authorization, and accounting (AAA) server that runs TACACS+ or RADIUS. (Auth… - Authentication Test with SSH
In order to test authentication with SSH, you have to add to the previous statements in order to enable SSH on Carter and test SSH from the PC and UNIX stations. At this point, the show crypto key mypubkey rsacommand must show the generated key. After you add the SSH configuration, …
Optional Configuration Sets
- Prevent Non-SSH Connections
If you want to prevent non-SSH connections, add the transport input sshcommand under the lines to limit the router to SSH connections only. Straight (non-ssh) Telnets are refused. Test to ensure that non-SSH users cannot Telnet to the router "Carter". - Set Up an IOS Router or Switch as SSH Client
There are four steps required to enable SSH support on a Cisco IOS router: 1. Configure the hostname command. 2. Configure the DNS domain. 3. Generate the SSH key. 4. Enable SSH transport support for the vty. If you want to have one device act as an SSH client to the other, yo…
Debug and Show Commands
- Before you issue the debug commands described here, refer to Important Information on Debug Commands. Certain show commands are supported by the Output Interpreter Tool (registered to customers only), which allows you to view an analysis of showcommand output. 1. debug ip ssh Displays debug messages for SSH. 2. show ssh Displays the status of SSH server connectio…
Sample Debug Output
- Server Debug
Note: This is Solaris machine output.
Tips
- If your SSH configuration commands are rejected as illegal commands, you have not successfully generated a RSA key pair for your router. Ensure you have specified a host name and domain. Then use t...
- When you configure RSA key pairs, you can get these error messages:
- The number of allowable SSH connections is limited to the maximum number of vty configur…
- If your SSH configuration commands are rejected as illegal commands, you have not successfully generated a RSA key pair for your router. Ensure you have specified a host name and domain. Then use t...
- When you configure RSA key pairs, you can get these error messages:
- The number of allowable SSH connections is limited to the maximum number of vty configured for the router. Each SSH connection uses a vtyresource.
- SSH uses either local security or the security protocol configured through AAA on your router for user authentication. When you configure AAA, you must ensure that the console is not run under AAA....