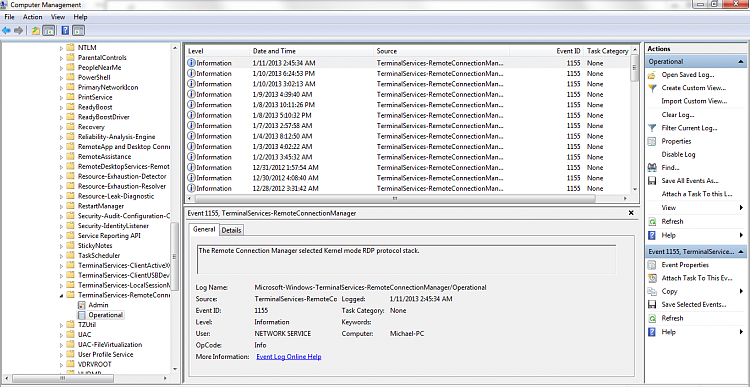
An effective way to find out the presence of a RAT is to analyze the startup entries. If you happen to find an unknown sort of entry in the list, chances are high that your PC is infected by a Remote Access Trojan. Analyze Running Processes; When there’s a Remote Access Trojan running in your computer, there will be corresponding process too.
Full Answer
What is a remote access trojan (RAT)?
What Is a RAT Virus? A remote access trojan (RAT), also called creepware, is a kind of malware that controls a system via a remote network connection. It infects the target computer through specially configured communication protocols and enables the attacker to gain unauthorized remote access to the victim.
Can desktop 1 detect remote access trojan?
Desktop 1 cannot be detected, but remote operations can be. There is no way they can do it. In theory, if they have access to your home ISP, they could see the inbound/outbound connections between your home PC and the server. 1. what is remote access trojan attack?
How do you know if your network has been compromised?
Keep in mind that these techniques require some level of expertise. People often say "Look at your network traffic", and then they go buy a tap, have a look in Wireshark and see lots of network traffic to various domains and IP addresses they cannot explain and then end up believing they must have been compromised.

Can a Trojan give remote access?
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
How are remote access Trojans delivered?
A remote access Trojan (RAT) is a malware program that includes a back door for administrative control over the target computer. RATs are usually downloaded invisibly with a user-requested program -- such as a game -- or sent as an email attachment.
What are the variant of remote access Trojan?
There are a large number of Remote Access Trojans. Some are more well-known than others. SubSeven, Back Orifice, ProRat, Turkojan, and Poison-Ivy are established programs. Others, such as CyberGate, DarkComet, Optix, Shark, and VorteX Rat have a smaller distribution and utilization.
Which of the following is a remote Trojan?
Troya is a remote Trojan that works remotely for its creator.
How do I know if someone is accessing my computer remotely?
Look for remote access programs in your list of running programs.VNC, RealVNC, TightVNC, UltraVNC, LogMeIn, GoToMyPC, and TeamViewer.Look for any programs that seem suspicious or that you don't recognize either. You can perform a web search for the process name if you aren't sure what a program is.
Is TeamViewer a RAT?
The JS script then launches the malware, which installs a version of TeamViewer, a remote administration tool (RAT), modified by the attackers. As in earlier attacks, the attackers use a malicious DLL library to hide the graphical user interface in order to control the infected system without the user's knowledge.
How would users recognize if ones computer is infected?
Signs of an infection include your computer acting strangely, glitching and running abnormally slow. Installing and routinely updating antivirus software can prevent virus and malware infections, as can following cautious best practices.
Which is the best remote access Trojan?
Blackshades is a Trojan which is widely used by hackers to gain access to any system remotely. This tool frequently attacks the Windows-based operating system for access.
Are PUPs malware?
Type and source of infection. Detections categorized as PUPs are not considered as malicious as other forms of malware, and may even be regarded by some as useful. Malwarebytes detects potentially unwanted programs for several reasons, including: They may have been installed without the user's consent.
What is the difference between a backdoor and a Trojan?
Once activated, a trojan can spy on your activities, steal sensitive data, and set up backdoor access to your machine. A backdoor is a specific type of trojan that aims to infect a system without the knowledge of the user.
What do Trojan creators look for?
Explanation: Trojan creators do not look for securing victim's system with their programs, rather they create such trojans for stealing credit card and financial details as well as important documents and files.
What is a logic bomb virus?
A logic bomb is a malicious program that is triggered when a logical condition is met, such as after a number of transactions have been processed, or on a specific date (also called a time bomb). Malware such as worms often contain logic bombs, behaving in one manner, then changing tactics on a specific date and time.
What is a backdoor Trojan?
Backdoor malware is generally classified as a Trojan. A Trojan is a malicious computer program pretending to be something it's not for the purposes of delivering malware, stealing data, or opening up a backdoor on your system.
What are RAT files?
A Remote Access Trojan, otherwise known as a RAT, is a type of spyware that allows a cybercriminal to take control of the computer or other device it's installed on. RATs are malicious software that constitute a major cybersecurity threat.
What is data sending Trojan?
A data-sending Trojan is a kind of Trojan virus that relays sensitive information back to its owner. This type of Trojan can be used to retrieve sensitive data, including credit card information, email addresses, passwords, instant messaging contact lists, log files and so on.
Is a backdoor malware?
A backdoor is a malware type that negates normal authentication procedures to access a system. As a result, remote access is granted to resources within an application, such as databases and file servers, giving perpetrators the ability to remotely issue system commands and update malware.
What is RAT software?
RAT can also stand for remote administration tool, which is software giving a user full control of a tech device remotely. With it, the user can ac...
What’s the difference between the RAT computer virus and RAT software?
As for functions, there is no difference between the two. Yet, while remote administration tool is for legit usage, RAT connotes malicious and crim...
What are the popular remote access applications?
The common remote desktop tools include but are not limited to TeamViewer, AnyDesk, Chrome Remote Desktop, ConnectWise Control, Splashtop Business...
What Does A Remote Access Trojan Do?
Malware developers use Remote Access Trojan (RAT) tools to gain full access and control over a user’s computer, including mouse and keyboard control, file access, and network resources.
How Is A Remote Access Trojan Executed?
An attacker uses a Trojan to execute a program file on a system. Once the user attempts to open the file, the Trojan is executed, and some dangerous actions are taken. A remote access Trojan program uses a backdoor to control the target machine with administrative privileges.
Can A Trojan Go Undetected?
Businesses and individuals alike are at risk from Trojan viruses. Malware can cause a variety of adverse effects from these subtle indicators, which are often undetected. Sensitive data and credentials can be accessed or special attacks and extortions can be carried out by these types of threats.
Can A Trojan Be Harmless?
Any malware that masquerades as a harmless file is called a Trojan horse.
What Is An Example Of A Trojan Virus?
A number of trojans are known to be malicious in government, including the Swiss MiniPanzer and MegaPanzer, as well as the German “state trojan” nicknamed R2D2. Governmentware in Germany exploits security gaps that are unknown to the general public and accesses smartphone data before it is encrypted.
Can Antivirus Detect A Rat?
RATs are not very effective against antivirus systems. It is not uncommon for computers and networks to be infected for years at a time. A RAT prevention system is rare because the RAT software can only be identified once it is installed on your computer. An intrusion detection system is the best way to deal with the RAT problem.
How Does Remote Access Trojan Works?
A Remote Access Trojan (RAT) infects a computer with a virus that gives cyberattackers unrestricted access to the data on the PC by using the victim’s access permissions. A RAT can include backdoors into the computer system, which can be used to create a botnet and spread to other devices as well.
How Do I Detect Remote Access?
The Admin tab is located at the top. The Action Log Viewer can be found in the Tools section . The Remote Control checkbox can be found under the Select Module Type section. You can click on the show button.
Are Remote Access Trojans Illegal?
According to law enforcement officials, it is not illegal to possess a remote-access tool. IT support is often provided by remote-access tools in corporate environments. The use of such tools for illegal purposes is a different ballgame, never mind the purpose-built remote access Trojan that can be used.
What Is The Purpose Of A Trojan Horse?
In general, a Trojan is designed to damage, disrupt, steal, or in general cause some other harm to your data or network.
Can Antivirus Detect Rat?
RATs are not very effective against antivirus systems. It is not uncommon for computers and networks to be infected for years at a time. A RAT prevention system is rare because the RAT software can only be identified once it is installed on your computer. An intrusion detection system is the best way to deal with the RAT problem.
What is Adwind malware?
Adwind is a paid malware platform that allows attackers to log keystrokes, steal passwords, capture webcam video, and more. Nasty stuff, for sure. Let’s break down what happened when the victim downloaded a so-called “important document” containing the Adwind RAT.
Is Threat Detection Report available for 2021?
All 2021 Threat Detection Report content is fully available through this website. If you prefer to download a PDF, just fill out this form and let us know what email to send it to.
Do you need administrator privileges to write files to AppData?
Since AppData is owned by the user, an attacker doesn’t need to have Administrator privileges in order to write files there. In addition, many legitimate applications launch processes from AppData, so the file location alone isn’t likely to raise many red flags to defenders.
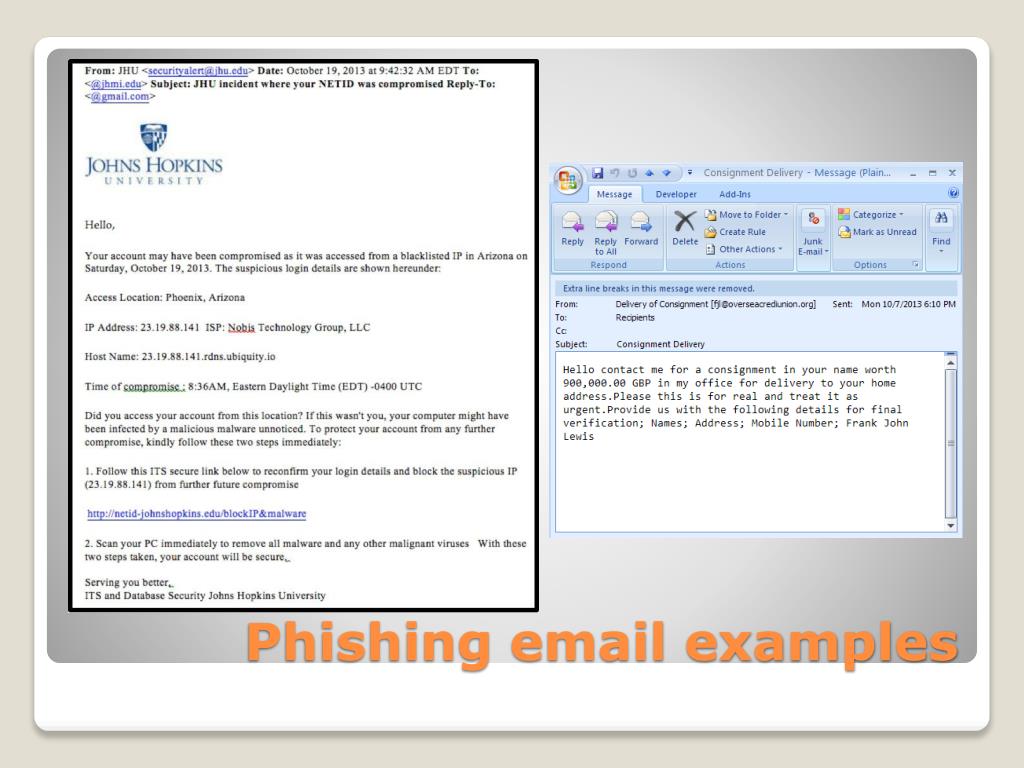
How to protect your computer from phishing?
As mentioned above, you can't. What you can is follow best practices, that are repeated over and over again by security experts: 1 Keep your system up-to-date 2 Don't install software from untrustworthy sources 3 Use a password manager 4 Make backups on an external device 5 Don't click on links in phishing emails and don't answer them.
What is information security stack exchange?
Information Security Stack Exchange is a question and answer site for information security professionals. It only takes a minute to sign up.
Does 100% security exist?
A 100% does not exist in security. You could scan for known RATs, and you could try and actively found the type of bugs RATs exploit, that’s about it.
What is a link to a virus?
Any link to or advocacy of virus, spyware, malware, or phishing sites. Any other inappropriate content or behavior as defined by the Terms of Use or Code of Conduct. Any image, link, or discussion related to child pornography, child nudity, or other child abuse or exploitation.
Is WTSapi32.dll legit?
Did you look up any of these file names on Bing or Google? Per TechNet and the Microsoft Community, WTSapi32.dll, RasMan, wtsapi32.dll and Netjoin.dll are all legit Windows files. I'm guessing the same with the other files, which is probably why Security Essentials is not detecting them as Trojans. Hope this helps!
How are Remote Access Trojans Useful to Hackers?
Attackers using remote control malware cut power to 80,000 people by remotely accessing a computer authenticated into SCADA (supervisor y control and data acquisition) machines that controlled the country’s utility infrastructure. RAT software made it possible for the attacker to access sensitive resources through bypassing the authenticated user's elevated privileges on the network. Having access to critical machines that control city resources and infrastructure is one of the biggest dangers of RAT malware.
Why do attackers use remote devices?
Instead of storing the content on their own servers and cloud devices, attackers use targeted stolen devices so that they can avoid having accounts and servers shut down for illegal content.
How to install a RAT?
An attacker must convince the user to install a RAT either by downloading malicious software from the web or running an executable from a malicious email attachment or message. RATs can also be installed using macros in Microsoft Word or Excel documents. When a user allows the macro to run on a device, the macro silently downloads RAT malware and installs it. With the RAT installed, an attacker can now remotely control the desktop, including mouse movement, mouse clicks, camera controls, keyboard actions, and any configured peripherals.
What happens if you don't see malware in Task Manager?
If you don’t see any potential malware in Task Manager, you could still have a RAT that an author programmed to avoid detection. Good anti-malware applications detect most of the common RATs in the wild. Any zero-day malware remains undetected until the user updates their anti-malware software, so it’s important to keep your anti-malware and antivirus software updated. Vendors for these programs publish updates frequently as new malware is found in the wild.
What is remote control software?
Legitimate remote-control software exists to enable an administrator to control a device remotely. For example, administrators use Remote Desktop Protocol (RDP) configured on a Windows server to remotely manage a system physically located at another site such as a data centre. Physical access to the data centre isn’t available to administrators, so RDP gives them access to configure the server and manage it for corporate productivity.
What happens if you remove the internet from your computer?
Removing the Internet connection from the device disables remote access to your system by an attacker. After the device can no longer connect to the Internet, use your installed anti-malware program to remove it from local storage and memory. Unless you have monitoring configured on your computer, you won't know which data and files transferred to an attacker. You should always change passwords across all accounts, especially financial accounts, after removing malware from your system.
Can malware writers name processes?
For most applications and processes, you can identify any suspicious content in this window, but malware writers name processes to make them look official. If you find any suspicious executables and processes, search online to determine if the process could be a RAT or other type of malware.
How are Remote Access Trojans Useful to Hackers?
Attackers using remote control malware cut power to 80,000 people by remotely accessing a computer authenticated into SCADA (supervisor y control and data acquisition) machines that controlled the country’s utility infrastructure. RAT software made it possible for the attacker to access sensitive resources through bypassing the authenticated user's elevated privileges on the network. Having access to critical machines that control city resources and infrastructure is one of the biggest dangers of RAT malware.
Why do attackers use remote devices?
Instead of storing the content on their own servers and cloud devices, attackers use targeted stolen devices so that they can avoid having accounts and servers shut down for illegal content.
How to install a RAT?
An attacker must convince the user to install a RAT either by downloading malicious software from the web or running an executable from a malicious email attachment or message. RATs can also be installed using macros in Microsoft Word or Excel documents. When a user allows the macro to run on a device, the macro silently downloads RAT malware and installs it. With the RAT installed, an attacker can now remotely control the desktop, including mouse movement, mouse clicks, camera controls, keyboard actions, and any configured peripherals.
What happens if you don't see malware in Task Manager?
If you don’t see any potential malware in Task Manager, you could still have a RAT that an author programmed to avoid detection. Good anti-malware applications detect most of the common RATs in the wild. Any zero-day malware remains undetected until the user updates their anti-malware software, so it’s important to keep your anti-malware and antivirus software updated. Vendors for these programs publish updates frequently as new malware is found in the wild.
What is remote control software?
Legitimate remote-control software exists to enable an administrator to control a device remotely. For example, administrators use Remote Desktop Protocol (RDP) configured on a Windows server to remotely manage a system physically located at another site such as a data center. Physical access to the data center isn’t available to administrators, so RDP gives them access to configure the server and manage it for corporate productivity.
What happens if you remove the internet from your computer?
Removing the Internet connection from the device disables remote access to your system by an attacker. After the device can no longer connect to the Internet, use your installed anti-malware program to remove it from local storage and memory. Unless you have monitoring configured on your computer, you won't know which data and files transferred to an attacker. You should always change passwords across all accounts, especially financial accounts, after removing malware from your system.
Can malware writers name processes?
For most applications and processes, you can identify any suspicious content in this window, but malware writers name processes to make them look official. If you find any suspicious executables and processes, search online to determine if the process could be a RAT or other type of malware.