
How does remote remote access work?
Remote access via the Internet makes use of a virtual private network (VPN) that provides a secure connection between two devices. Essentially, the VPN functions like a tunnel that keeps traffic private and uninterrupted. The VPN server acts as a gateway at the edge of the network, sending it to the right hosts within the network.
How does a VPN work on a router?
Before a remote user can actually send information, a router with VPN software encapsulates and encrypts the traffic. Then, using a variable set of routes based on available network paths, data packets are sent via the Internet to a receiving end.
What is the best VPN protocol?
OpenVPN is currently the most popular VPN protocol available to consumers. It typically uses either AES-256, a super high-level method of data encryption, or a Camellia encryption.
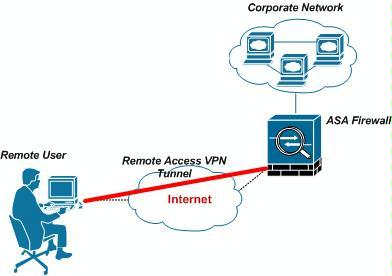
How to connect to a VPN?
2. When you’re in the “Add a VPN Connection” window, follow these steps: 1 For VPN provider, select the Windows (built-in) option and create a name you’ll remember as the VPN connection profile. You’ll need this information later, so choose something you can remember. 2 For VPN type, choose the kind of connection your VPN service provider uses. 3 For Type of sign-in info, select the sign-in info you will use to log in. 4 If this is at work, ask IT what kind of login you will need. 5 For home, simply enter your username and password details. Choose a strong password and avoid words or numbers that are easily accessible like your birthday.
Who uses VPNs?
Most corporations use a VPN to help guard their information as well as to promote communication and productivity with remote network access. Wherever employees are located, VPNs use a network of servers to allow them to remain connected and securely access information they may need off-site.
How do I set up a VPN on a Windows 10 computer?
Once you’ve created an account with a trusted VPN service provider, it’s time to set up your devices. Let’s talk about how to set up VPN on Windows 10. Here is a step-by-step guide for how to set up a VPN at home and work:
How does L2TP protect against hackers?
L2TP typically uses IPSec (Internet Protocol Security) to encrypt data.
Why is my VPN slow?
If you do find that your network is slowing down after you’ve set up your VPN, this could mean that your VPN server is too far away. It’s important to consider the locations of your provider’s servers to avoid speed issues. Many VPN providers have multiple locations in many countries. Be sure to pick one where you don't have to send your data around the world and back.
What happens when you use a VPN?
When you use a virtual protected network, your computer connects to a remote server while browsing on the internet. Instead of showing your device as connected to the public WiFi, your traffic reflects wherever your server is located - meaning your traffic (and the data traveling with it) are essentially rerouted to look like they’re coming from your VPN server’s location and not your own.
Why do we need VPN?
A VPN can be used to protect your data from insecure networks and guard it against unauthorized users. It uses encryption and a network of servers to secure your data and communications from outside interceptions. Each VPN service has a unique protocol for how they protect your data, which we’ll get into later.
What is pulse connect secure?
With Pulse Connect Secure (PCS), enterprises today can enable Zero Trust secure access to hybrid IT resources for an increasingly mobile workforce.
What is pulse secure?
Pulse Secure ensures your mobile workforce can reach applications and resources in the cloud and data center – for true hybrid IT access.
Does pulse have multiple logins?
With Pulse’s single, unified client, users safely and securely access applications. And, they don’t have to log in multiple times.
Is secure access a tall order?
In today’s environment with increasing remote and mobile workforces, more sophisticated and numerous malware and cloud migration happening at a rapid pace, enabling secure access is a tall order.
