What happens if you give someone remote access to your computer?
This can be even worse than just conning you out of money, as undetected malware can allow hackers to steal your identity, including your passwords and financial information, over and over again, even if you get new passwords and account numbers.
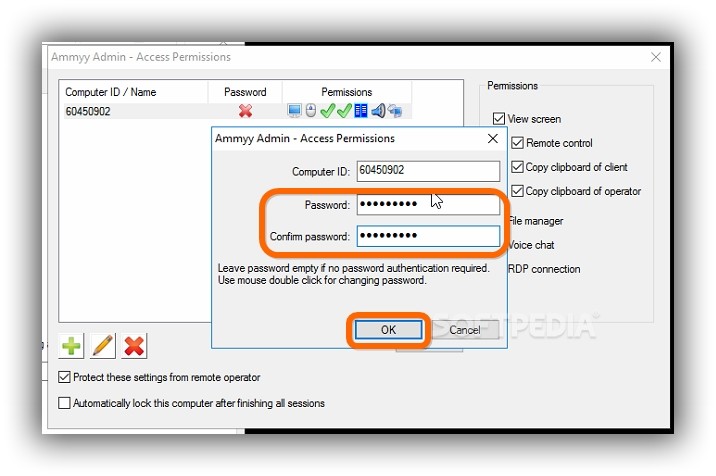
How do I stop someone from remote access to my computer?
Windows 10 InstructionsClick the Windows Start button and type "Allow Remote Access to your computer". ... Make sure "Allow Remote Assistance connections to this computer" is unchecked.Select "Don't allow remove connections to this computer" under the Remote Desktop section and then click OK.
Can someone remotely access my computer without my knowledge?
There are two ways someone can access your computer without your consent. Either a family member or work college is physically logging in to your computer or phone when you are not around, or someone is accessing your computer remotely.
How do you check if your laptop is being monitored?
How to Tell if Your Computer Is Being MonitoredMonitoring processes from Windows Task Manager. ... Monitoring Open Ports using netstat. ... Periodic Antivirus scans. ... Investigating Recent Files. ... Investigating Browser History. ... Auditing Login Event Viewer. ... Identifying Corporate Monitoring.
What does it mean when a computer technician is remotely accessing your computer?
When a technician is remotely accessing your computer, you may be able to see what they are doing. Often, remote access software will show the other person’s actions to you on the screen. In addition to being able to see, there may be some kind of communication between you and the technician. This could be in the form of a voice or a chatbox.
What to Do If Someone Wants to Access Your Computer?
If someone does want to access your computer and they have phoned you, there is a strong chance that this is a hoax .
Why Would You Want to Provide Remote Access?
There are several legitimate reasons to provide access to your computer. For instance, a remote desktop for Mac or PC can allow you to access files and folders stored on your computer when you are not near it.
What Are the Risks Involved in Giving Remote Access?
Before you let anyone else have remote access to your computer, you should, first of all, consider the risks .
How to protect your computer from cybercriminals?
You should ensure that you have both antivirus and firewall protection installed and that you keep this updated. Make sure that you download and install all updates to your operating system.
What are the benefits of remote access?
The other benefit of being able to provide remote access is that a technician can get into your machine and fix any software problems that you may have.
What to do if you receive an unsolicited call?
If the call is unsolicited, ask for some credentials or proof of identity before you proceed in downloading, installing, or setting up any remote access software.
How to gain remote access to a computer?
There are several ways a person can gain remote access. 1. The user downloads a virus through a file or pic of an unknown sender. 2. Through remote assistance ( this has to be verified by the owner of the computer first.
What is a link to a virus?
Any link to or advocacy of virus, spyware, malware, or phishing sites. Any other inappropriate content or behavior as defined by the Terms of Use or Code of Conduct. Any image, link, or discussion related to child pornography, child nudity, or other child abuse or exploitation.
What are threats in the community?
Threats include any threat of suicide, violence, or harm to another. Any content of an adult theme or inappropriate to a community web site. Any image, link, or discussion of nudity. Any behavior that is insulting, rude, vulgar, desecrating, or showing disrespect.
How to stop someone from accessing my computer?
This includes removing any Ethernet cables and turning off your Wi-Fi connections.
How to install antivirus on another computer?
If you don't have an antivirus, download an installer on another computer and transfer it to your computer via USB. Install the antivirus and then run a scan with it.
What to do if your computer is compromised?
Change all of your passwords . If your computer was compromised, then there’s a possibility that all of your passwords have been recorded with a keylogger. If you’re sure the infection is gone, change the passwords for all of your various accounts. You should avoid using the same password for multiple services.
Why is public Wi-Fi so dangerous?
Try to avoid public Wi-Fi spots. Public Wi-Fi spots are risky because you have zero control over the network. You can't know if someone else using the spot is monitoring traffic to and from your computer. By doing this, they could gain access to your open browser session or worse. You can mitigate this risk by using a VPN whenever you are connected to a public Wi-Fi spot, which will encrypt your transfers.
What to do if you can't get rid of intrusion?
If you're still experiencing intrusions, or are concerned that you may still be infected, the only way to be sure is to completely wipe your system and reinstall your operating system.
Why does my computer turn on without my input?
If your computer appears to turn on without your input when you're not using it, it is likely waking from Sleep mode to install updates .
How to find out what is running on my computer?
Open your Task Manager or Activity Monitor. These utilities can help you determine what is currently running on your computer.
How to connect to another computer remotely?
To open Remote Desktop: Press the Windows key on the keyboard and type remote into the Search bar. Click Remote Desktop Connection.
How to select users to connect to a PC remotely?
To select specific users who can connect to the PC remotely, click Select users that can remotely access this PC and make your selection (s). Open Remote Desktop Connection on the computer making the connection. Now you'll need to go back to the PC you want to use to connect to the other PC.
How to log in to TeamViewer?
Enter the password from the remote PC and click Log On. This is the password on the "Allow Remote Control" screen on the remote computer. Or, if you created a password earlier for unattended access, you can enter that instead. Either will work to sign in. Once the password is accepted, the contents of the screen will appear in the TeamViewer window.
How to create a free TeamViewer account?
Create or sign in to a TeamViewer account. To create a new account, select Create a free TeamViewer account, fill out the form, and click Next. To sign in to an existing account, select I already have a TeamViewer account and sign in.
How to get remote to search bar?
Press the Windows key on the keyboard and type remote into the Search bar.
Where is the Connect button in TeamViewer?
Click Connect on the computer making the connection. It's at the top-right corner of TeamViewer.
Can you add a contact without a TeamViewer account?
You can also proceed without an account by selecting I don't want to create a TeamViewer account now. You won't be able to add this computer and password to your contacts, however.
What to do if you're not 100% sure your computer is safe?
If you're not 100% confident that the compromised machine is clean, it may be wise to do this from a different machine and log back in once you're sure the compromised system is safe. With your passwords changed, log out of every instance of your accounts.
How to get your computer back to 100% safe?
One sure way to take care of any nasty activity is to wipe your hard drive and reinstall your operating system. Completely blowing it all away is the only sure method to get your machine back to being 100% safe. This does mean, however, that all of your files will be lost.
How to protect your router from hackers?
There are some weak points that almost everyone is vulnerable to, so get familiar with them. Having Universal Plug and Play (UPnP) enabled on your router can leave it vulnerable for certain types of attack, and be sure to turn off Wi-Fi Protected Setup (WPS) on your router as well. Additionally, using weak passwords and browsing insecure web sites are all things that can make gaining access to your machine easy. Make sure you keep everything up to date: browsers, antivirus applications, and your OS. If you're not sure you have the basics covered well enough, check out our online security checklist.
How to get rid of malware on my computer?
Make sure your antivirus and anti-malware is up to date and disconnect from the internet if you haven't already. Enable your virus protection software if it's disabled, and run a full system scan. You should have separate antivirus and anti-malware applications on your machine, and you should run full system scans with both. Sometimes one can catch something that the other won't, and you want to be as thorough as possible.
What to do if you found one piece of malware?
A malware scanner like Malwarebytes can find the executables and scripts , but there could be a browser plugin or extension that will keep downloading it. Everything is a suspect. Take a close look at all of the little things you've downloaded and installed, and remove anything that looks suspicious.
How to be safe on public Wi-Fi?
Be wary of public Wi-Fi. Once you connect to a network that has other people on it, there's no guarantee of safety. Chances of an attack are low, but it only takes once for someone snooping to get something useful. If you must use a public Wi-Fi service, Blake recommends using a VPN to ensure that no one can snoop on your traffic. We can show the many reasons to start using a VPN, and recommend the most popular VPN service provider around here. Remember, just because a Wi-Fi network has a password doesn't mean it's secure—if there are other people on it, you need to stay safe. We've talked about the safety of public Wi-Fi networks before.
How to make yourself vulnerable?
Make sure you have your firewall configured properly. Blake points out that this is the easiest way to make yourself vulnerable. A misconfigured firewall leaves dangerous ports open and can make your computer visible to anyone on the internet. Once it's running, check that it's doing its job properly. The How-To Geek recommends port scanning your router at ShieldsUP!, a web site that tests your router for vulnerabilities. If there are open or exploitable ports, the site will notify you. Otherwise, you're all clear.
How to protect your computer when using remote access?
Here are some steps you can take to help protect your computer and data while relying on remote access. Maintain strong passwords.
What is remote computer access?
Many people take their laptops with them to do things like finish a business presentation while waiting for a flight at the airport. But a lot of those laptops may not have bigger, important files on them. You might leave those files at work or at home on your desktop computer.
How to protect remote desktop from hackers?
Use a secure Virtual Private Network (VPN). If you set up a VPN, your remote desktop server won’t be connected directly to the internet. It will only be exposed on your local network, which could leave it less vulnerable to hackers.
How to protect your network from remote access?
You should set up firewalls to restrict access using software or hardware or both.
What is remote access software?
Remote computer access software lets you access networks and computers remotely. It can enable file sharing. It’s like having a remote control for a computer or system that isn’t near you. You’ll be able to remotely download files and applications from your desktop or another person’s computer onto your laptop or your cell phone. Remote access also gives you control over that remote device
Why is it important to limit the number of users who can log in?
Remote computer access can help businesses, individuals, and families in a variety of ways. But it’s important to make remote access secure .
Why is it important to lock your computer?
Set up an account lockout policy. To help guard against hackers implementing brute-force attacks with automated password-guessing tools, it’s important to set your computer to lock your accounts when someone enters an incorrect password a set number of times.
How to remotely connect to a computer?
You can start a remote connection from those computers by clicking Start, typing “remote,” and then choosing the “Remote Desktop Connection” result. Just type in the name or IP address ...
How to access someone's computer?
How to access someone’s computer using Remote Desktop Connection. Windows Remote Desktop Connections allows you to connect to a Windows-based PC via the internet or a network. When you are connected using a Remote Desktop Connection, you can see the host computer’s desktop and access its files and folders as if you were sitting in front ...
How to access remote desktop in Windows 7?
In Windows 7, you can also launch the Remote Desktop Connection client from the Start Menu. Click “All Programs” and navigate to the Accessories group. There, click the Remote Desktop Connection shortcut. You can also use the search to find and open the Remote Desktop Connection client.
How to open Remote Desktop Connection?
If you are using Windows 10, you can launch the Remote Desktop Connection client from the Start Menu. Open the Start Menu and scroll through the apps list until you find the folder called Windows Accessories. Click on the Remote Desktop Connection to open it. You can also use Cortana’s search box from the taskbar.
Where is Remote Desktop Connection on Windows 8.1?
If you are using Windows 8.1, you can open the Remote Desktop Connection from the Start screen. Go to the Apps view, look for the Remote Desktop Connection client and click or tap its name to launch it. You should find it in the “Windows Accessories” folder.
