
Industrial Control Systems Remote Access Protocol
- Overview. External parties may need to connect remotely to critical infrastructure control networks. ...
- Design principles. By default, there should be no communication between the vendor and the critical infrastructure control system.
- Implementation principles. ...
- Protocol. ...
- Further information. ...
- Contact details. ...
Full Answer
How to manage remote access to industrial control systems?
From the DMZ, after authentication, user-initiated remote access should follow a trusted path to the industrial control system—where the user will authenticate again, this time using the local identity and access management solution for the industrial control system. All remote access communications should be logged and monitored.
What are the protocols used in ICS?
These protocols were first designed for serial connection but, with time, have evolved to support and run on TCP/IP protocols over Ethernet networks. In a typical ICS system, the following protocols are widely used: RS-232 and RS-485, Modbus, DNP3, HART, TASE 2.0 and ICCP, CIP, PROFIBUS and PROFINET, FOUNDATION Fieldbus, BACnet and more.
How do you control ICS access on a network?
The first step in controlling ICS access is isolation. Organizations should segregate ICS and SCADA networks from the office network and the internet. We do this with technologies like VLANs, VxLANS and software-defined perimeters. When possible, physical separation is preferred.
Can I connect remotely to a control system?
Connecting remotely to a control system has some specific considerations. There is existing literature on the topic of remote access to control systems, such as international standard IEC 62443-4-1:2018 and advice from ICS-CERT. This publication is broken into three sections:
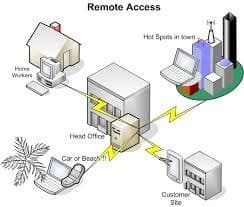
What is ICS protocol?
ICS is a generic term used to describe various control systems and their instrumentation, used for controlling and monitoring industrial processes. ICS basically integrates hardware, software and their network connectivity for running and supporting critical infrastructure.
What is remote access protocol?
A remote access protocol is responsible for managing the connection between a remote access server and a remote computer. It's necessary for desktop sharing and remote access for help desk activities.
What is ICS in cyber security?
ICS security is the area of concern involving the safeguarding of industrial control systems, the integrated hardware and software designed to monitor and control the operation of machinery and associated devices in industrial environments.
Which protocol is used for remote administration?
The Remote Desktop Protocol (RDP) is a protocol, or technical standard, for using a desktop computer remotely. Remote desktop software can use several different protocols, including RDP, Independent Computing Architecture (ICA), and virtual network computing (VNC), but RDP is the most commonly used protocol.
What are the three types of remote connections?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
Is RDP TCP or UDP?
Remote Desktop Protocol (RDP) is a Microsoft proprietary protocol that enables remote connections to other computers, typically over TCP port 3389. It provides network access for a remote user over an encrypted channel.
What are ICS devices?
What is an Industrial Control System (ICS)? ICS assets are the digital devices that are used in industrial processes. This includes all of the various components of critical infrastructure (power grid, water treatment, etc.), manufacturing, and similar applications. A number of different devices are classified as ICS.
Why is ICS security important?
NIST's Guide to Industrial Control Systems (ICS) Security helps industry strengthen the cybersecurity of its computer-controlled systems. These systems are used in industries such as utilities and manufacturing to automate or remotely control product production, handling or distribution.
What is ICS application?
Industrial control system (ICS) security focuses on ensuring the security and safe function of industrial control systems. This includes the hardware and software the system and its operators use.
What is the difference between SSH and RDP?
A Major Difference between RDP and SSH RDP and SSH are designed to provide two distinct solutions for connecting to remote computer systems. RDP furnishes users with a tool for managing remote connections via a GUI. SSH offers a Secure Shell and is used for text-based management of remote machines.
Who is more secure protocol for remote login?
While Remote Desktop is more secure than remote administration tools such as VNC that do not encrypt the entire session, any time Administrator access to a system is granted remotely there are risks. The following tips will help to secure Remote Desktop access to both desktops and servers that you support.
How does remote administration work?
Instead, it requires remote access software to be downloaded and installed on both the local and remote computers. Once the software is installed, the local computer can access the remote computer and perform several tasks like running applications, managing updates, and even handling administrative tasks.
What is the significance of SSH protocol?
SSH or Secure Shell is a network communication protocol that enables two computers to communicate (c.f http or hypertext transfer protocol, which is the protocol used to transfer hypertext such as web pages) and share data.
What is the PPP Point to Point Protocol and how does it work?
Point-to-Point Protocol (PPP) is a TCP/IP protocol that is used to connect one computer system to another. Computers use PPP to communicate over the telephone network or the Internet. A PPP connection exists when two systems physically connect through a telephone line. You can use PPP to connect one system to another.
Which of the following protocol is used by remote login?
Notes: Telnet is a protocol used to log in to remote computers. terminals over the Internet or a TCP/IP computer network.
Which of the remote is a secure remote access protocol?
Most Secure Remote Access Protocol | Remote Desktop (RDP)
What protocols are used in ICS?
In a typical ICS system, the following protocols are widely used: RS-232 and RS-485, Modbus, DNP3, HART, TASE 2.0 and ICCP, CIP, PROFIBUS and PROFINET, FOUNDATION Fieldbus, BACnet and more.
What is ICS system?
ICS systems get data from remote sensors and send commands to the machinery for the appropriate actions to take.
What is the difference between ICS and IT?
On the other hand, ICS systems focus more on detecting, monitoring and controlling physical equipment and processes using sensors, actuators, controllers, PLC (Programmable Logic Controllers), PCD (Process Control Dynamics), BAS (Building Automation System) and more. Thus, IT and ICS systems are altogether different and pose their own challenges in terms of maintenance, security and operations.
What is the oldest serial communication protocol?
Modbus: Modbus is the oldest and most widely deployed serial communication protocol. It is open-source and freely distributed and can be built by anyone into their equipment.
How many slaves are there in a Modbus network?
Modbus is a request-response protocol and operates at the application layer of the OSI model. In a typical Modbus network, there are 247 slaves and one master. Master/slave is a communication model in which one device (master) controls other devices (slaves).
What is ICS in industrial?
ICS is a generic term used to describe various control systems and their instrumentation, used for controlling and monitoring industrial processes. ICS basically integrates hardware, software and their network connectivity for running and supporting critical infrastructure. ICS systems get data from remote sensors and send commands to the machinery for the appropriate actions to take.
What are the security concerns of Modbus?
Modbus has several security concerns – lack of authentication, lack of encryption, lack of message checksum and lack of broadcast suppression.
Is remote access to OT commonplace?
Remote access to OT systems is now commonplace, especially driven by industry 4.0 applications, although it is not unique to these cases. Increasingly more companies are contracting out the development, assembly and commissioning of new machines that require remote access, so that the supplier can provide the technical support agreed upon in the contract. For clients, these accesses are an entry point to their network, so they should seek to make them as secure as possible and only use them when strictly necessary.
Is remote access to control systems secure?
As discussed above, there are various ways to remotely access control systems. Some are more secure than others, but, at the same time, they are more difficult to implement and deploy. We must always start from the premise that direct remote access to control systems is not recommended in all good practice guides and regulations, since external networks are considered insecure environments. Therefore, any measure taken will be beneficial to the security of the organization.
Is remote access necessary in OT?
The remote accesses in OT are increasingly frequent and necessary, however, we must not forget that they are devices with a far lower levels of security than what we find in IT environments, so it is essential to carry out the appropriate work in order to increase their cybersecurity levels.
What are remote access requirements?
Remote access requirements should be determined, including what IP addresses, what communication types, and what processes can be monitored. All others should be disabled by default. Remote access including process control should be limited as much as possible.
What is remote access?
Remote access is a relatively new capability for industrial control systems —one that comes with specific engineering and financial benefits. However, when considering new remote access connections, organizations need to involve the necessary stakeholders to make security and reliability-based decisions.
Do not enable remote access?
First and foremost, do not enable remote access by default. This is not a strict anti-remote access stance— rather a pro-engineering discussion. Because remote access is a “gate” through the (hopefully robust) perimeter and moat and walls of your fort, you want to make sure it is secure. This requires multiple stakeholders to be involved, including OT security, IT security, engineering, vendors, and any maintenance support teams. It is not something that is easily pre-packaged and it is never a “set it and forget it” capability.
Why is remote access important?
Secure remote access is a necessity to keep productivity high and to quickly address operational issues, but it also can create a low cost, easy entry point for hackers. Blue Ridge Networks has designed a secure remote access solution that is comptaible with ICS/OT environments and supports both the enterprise and operational user. When this solution is in place, secure remote access to the OT environment is completely isolated and contained. This allows organizations to securely manage authorized connections between users and devices from one point to another through end-to-end encrypted tunnels — without establishing or configuring complex, time-consuming protocols. The solution eliminates endpoint vulnerability and cloaks devices, making them invisible and inaccessible to unauthorized systems.
Can you ban remote access?
Many organizations have continued to prohibit remote access for third parties entirely, requiring individuals to exclusively access ICS during on-site visits. For example, within the telecommunications industry, switch equipment vendors have abandoned ICS remote access and retreated to conducting maintenance checks on premise. Banning remote access does eliminate some potential security risks, but can be prohibitive in critical alarm situations that indicate hazardous conditions or failure modes. In many instances, field sites may be separated by miles.
How to control ICS access?
The first step in controlling ICS access is isolation. Organizations should segregate ICS and SCADA networks from the office network and the internet. We do this with technologies like VLANs, VxLANS and software-defined perimeters. When possible, physical separation is preferred.
What is ICS infrastructure?
ICS infrastructure manages our national critical infrastructure and manufacturing processes. When ICS is compromised, services that continue the healthy operation of the country are subject to interruption.
What is risk based authentication?
Risk-based authentication helps ensure the continued trust levels of authenticated entities (Olzak, 2018). It includes continuous monitoring of the behavior of the user/device and the device state. If the state changes too far from baselines, additional authentication is required.
What is SCADA system?
Industrial controls systems (ICS) and supervisory control and data acquisition (SCADA) systems (a subset of ICS) manage our critical national infrastructure. Controlling logical access to these systems is not easy, given their often-distributed nature and the large number of employee and support roles needing access.
What is a logical access control?
Logical access control must address how these roles access resources, what resources what they can see, what accessed resources can see each other, the risk of user/device context during sessions and other considerations.
Is strong authentication required for ICS?
Access to ICS should include strong authentication. Strong authentication includes at least two authentication factors. However, this is not enough today. We must ensure that user/device contexts continue to meet a level of trust we expect when accessing critical infrastructure. This is particularly true for remote users.
Is access control included in zero-trust?
All of the access controls above are included in emerging zero-trust network solutions. In zero-trust, we trust nothing and no one. For ICS, this is the way we should look at access control.
What is remote access protocol?
A remote access protocol is responsible for managing the connection between a remote access server and a remote computer. It’s necessary for desktop sharing and remote access for help desk activities. The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), ...
What is PPP protocol?
PPP is a remote access protocol that allows you to implement TCP/IP. It establishes a connection via point-to-point links (i.e., dedicated leased lines and dial-up). PPP is used most often for remote connections to LANs and ISPs. PPP utilizes the Link Control Protocol (LCP), which tests the link between client and PPP host ...
How to use PPTP?
To use PPTP, you’ll have to set up a PPP session between the server and the client, usually over the internet. Once the session is established, you’ll create a second dial-up session. This dial-up session will use PPTP to dial through the existing PPP session.
What is PPTP in a network?
PPTP is a remote access protocol, based on PPP, created by Microsoft. It’s used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network.
What is solarwinds take control?
SolarWinds Take Control offers remote access for help desks, desktop sharing, and privileged access management capabilities. It was designed to help IT server providers support their customers in a fast and intuitive way, on almost any platform. Take Control gives you access to deep diagnostics through a user-friendly dashboard and it’s able to connect to devices in just a few seconds.
What is take control?
Take Control was created to suit your technicians’ workflows and designed to let you hit the ground running. No training or experience is required, making the process of providing remote support less of a headache. You also have the option of configuring the tool to suit your needs—you can even adopt personalized branding, which helps your customers keep your business top-of-mind.
What is managed services provider?
As a managed services provider (MSP), you likely already work with remote access protocols on a daily basis. But learning how to best explain the various types of remote access protocols and their advantages and disadvantages to customers is critical in helping them understand your decisions—and why they should trust you and your services.

Design Principles
- 1. By default, there should be no communication between the vendor and the critical infrastructure control system.
- 2. Networks should be segmented and segregated. Details on the application of segmentation and segregation can be found in the ACSC’s Implementing Network Segmentation and Segregationpublication. I...
- 1. By default, there should be no communication between the vendor and the critical infrastructure control system.
- 2. Networks should be segmented and segregated. Details on the application of segmentation and segregation can be found in the ACSC’s Implementing Network Segmentation and Segregationpublication. I...
- 3. There must be other processes and procedures in place before this protocol is used. These processes include:
- 4. Multi-factor authentication should be used. Two-factor authentication should be used at a minimum. Details, including why this is needed, can be found in the ACSC’s Implementing Multi-Factor Aut...
Implementation Principles
- 1. There should be no connection directly from the vendor to the control equipment. There should be at least one hop through a device controlled and managed by the critical infrastructure owner fir...
- 2. The connection between the control network and any external device should be physically disconnected when the protocol is not being used. Ideally this would mean removal of a phys…
- 1. There should be no connection directly from the vendor to the control equipment. There should be at least one hop through a device controlled and managed by the critical infrastructure owner fir...
- 2. The connection between the control network and any external device should be physically disconnected when the protocol is not being used. Ideally this would mean removal of a physical cable, how...
- 3. Ensure there is a warning on the control system operator’s machines when the connection to the remote vendor is established.
- 4. VPNs should be configured as tightly as possible, for example locked to specific IP addresses through firewalls.
Protocol
- 1. Ensure procedures discussed in Design Principle 2, such as a method to disconnect the control system from the internet quickly, are known and in place.
- 2. Obtain approval for the connection from the relevant senior officer in the critical infrastructure company.
Further Information
- The Information Security Manual is a cyber security framework that organisations can apply to protect their systems and data from cyber threats. The advice in the Strategies to Mitigate Cyber Security Incidents, along with its Essential Eight, complements this framework.
Contact Details
- If you have any questions regarding this guidance you can write to usor call us on 1300 CYBER1 (1300 292 371).
Components of Ics
It Versus Ics
- IT systems basically focuses on the development, maintenance and use of computer systems, software and networks for the processing and sharing of data. On the other hand, ICS systems focus more on detecting, monitoring and controlling physical equipment and processes using sensors, actuators, controllers, PLC (Programmable Logic Controllers), PCD (Process Control Dy…
Communication Protocols Used in Ics Systems
- As described above, due to ICS being different from IT systems in many aspects, traditional IT protocols cannot be used in ICS systems. All the systems, interfaces and instruments in an ICS system use different protocols for real-time communication and data transfer. These protocols were first designed for serial connection but, with time, have evo...
Conclusion
- ICS and SCADA systemshave been on the market since the 1970s, but not much development has taken place in this field. This is due to the higher cost and risk involved. These systems need urgent attention, since security was not given much priority while these systems were being developed. Also, due to high risk and lack of exposure, maintaining and providing security to the…
Sources